-
-
[原创]挖矿病毒通过Flash漏洞传播 火绒用户无需升级即可防御
-
发表于: 2018-4-24 17:59 1724
-
4月24日,火绒安全团队发出警报,病毒团伙利用Adobe Flash漏洞传播挖矿病毒。病毒团伙将挖矿程序植入到游戏下载站“52pk”中(82cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6e0f1J5M7r3E0Q4x3X3g2U0L8$3#2Q4c8f1k6Q4b7V1y4Q4z5o6W2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7V1c8Q4z5e0y4Q4c8e0N6Q4z5e0c8Q4b7e0S2Q4c8e0k6Q4z5o6S2Q4b7U0N6Q4c8e0S2Q4b7f1g2Q4b7V1k6Q4c8e0W2Q4z5e0N6Q4b7f1g2Q4c8e0S2Q4b7f1k6Q4b7e0g2Q4c8e0N6Q4b7V1c8Q4z5e0q4Q4c8e0N6Q4b7f1u0Q4z5e0W2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7U0S2Q4b7e0k6Q4c8e0k6Q4b7f1k6Q4z5e0u0Q4c8e0W2Q4b7e0q4Q4b7U0g2Q4c8e0W2Q4z5f1c8Q4b7e0u0Q4c8e0g2Q4b7U0q4Q4z5e0g2Q4c8e0N6Q4b7e0c8Q4b7V1q4Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0k6Q4z5e0N6Q4b7e0m8Q4c8e0W2Q4z5f1y4Q4z5o6m8Q4c8e0c8Q4b7V1u0Q4b7V1u0Q4c8e0c8Q4b7V1c8Q4z5e0g2Q4c8e0k6Q4z5e0y4Q4z5p5c8Q4c8e0c8Q4b7V1c8Q4z5f1y4Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0k6Q4z5p5y4Q4z5e0k6Q4c8e0N6Q4z5f1k6Q4b7V1k6Q4c8e0N6Q4b7e0S2Q4z5p5u0Q4c8e0g2Q4b7V1q4Q4z5p5k6Q4c8e0c8Q4b7V1g2Q4b7V1k6Q4c8e0c8Q4b7V1y4Q4z5f1q4Q4c8e0N6Q4b7f1u0Q4z5p5u0Q4c8e0g2Q4z5p5c8Q4b7U0y4Q4c8e0S2Q4b7V1k6Q4z5e0m8Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5o6S2Q4b7e0W2Q4c8e0N6Q4z5e0c8Q4b7e0S2Q4c8e0N6Q4z5e0c8Q4b7e0S2Q4c8e0k6Q4z5o6S2Q4b7U0N6Q4c8e0N6Q4z5e0c8Q4b7U0g2Q4c8e0S2Q4z5o6c8Q4z5e0q4Q4c8e0u0Q4z5o6m8Q4z5f1y4Q4c8e0k6Q4z5p5y4Q4z5e0k6Q4c8e0N6Q4z5f1k6Q4b7V1k6Q4c8e0u0Q4z5o6m8Q4z5f1c8Q4x3U0S2Q4c8e0W2Q4z5e0N6Q4b7e0S2Q4c8e0N6Q4b7V1c8Q4z5e0N6Q4c8e0g2Q4b7U0S2Q4z5o6q4Q4x3U0W2Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0N6Q4z5o6W2Q4b7U0W2Q4c8e0g2Q4z5o6S2Q4b7f1u0Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4z5e0S2Q4b7f1k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0S2Q4b7f1k6Q4b7e0g2Q4c8e0N6Q4z5e0N6Q4z5o6g2Q4c8e0k6Q4b7f1k6Q4z5e0u0Q4c8e0c8Q4b7V1c8Q4b7V1k6Q4c8e0N6Q4z5e0c8Q4b7e0S2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0u0Q4z5o6m8Q4z5f1y4Q4c8e0g2Q4z5o6g2Q4z5p5c8Q4c8e0k6Q4z5f1c8Q4z5o6m8Q4c8e0u0Q4z5o6m8Q4z5f1c8Q4c8e0k6Q4z5p5q4Q4z5o6m8Q4c8e0k6Q4z5f1y4Q4b7f1k6Q4c8e0N6Q4z5f1u0Q4b7U0S2Q4c8e0k6Q4b7f1k6Q4z5e0c8Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0g2Q4b7V1g2Q4z5o6m8Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0N6Q4b7f1g2Q4z5o6m8Q4c8e0g2Q4z5p5c8Q4z5e0g2Q4c8e0N6Q4b7f1k6Q4b7e0q4Q4c8e0k6Q4z5e0c8Q4b7U0W2Q4c8e0k6Q4z5e0k6Q4z5o6N6Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8e0g2Q4z5e0y4Q4z5o6S2Q4c8e0g2Q4b7U0S2Q4z5p5y4Q4c8e0k6Q4z5f1y4Q4z5o6W2Q4c8e0S2Q4b7V1g2Q4z5o6y4Q4c8e0g2Q4b7e0c8Q4b7e0N6Q4c8e0k6Q4z5e0c8Q4b7U0W2Q4c8e0S2Q4b7V1k6Q4z5f1u0Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7U0N6Q4b7U0u0Q4c8e0N6Q4b7V1u0Q4z5p5k6Q4c8e0k6Q4z5f1y4Q4z5o6W2Q4c8e0c8Q4b7V1q4Q4z5o6k6Q4c8e0g2Q4z5f1u0Q4b7V1c8Q4c8e0g2Q4b7e0c8Q4z5e0k6Q4c8e0k6Q4b7U0N6Q4b7U0N6Q4c8e0k6Q4b7U0N6Q4z5o6k6Q4c8e0g2Q4z5e0W2Q4b7e0S2Q4c8e0g2Q4z5o6g2Q4z5p5c8Q4c8e0k6Q4z5f1c8Q4z5o6m8Q4c8e0k6Q4z5p5q4Q4z5o6m8Q4c8e0k6Q4z5f1y4Q4b7f1k6Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0W2Q4z5f1u0Q4z5p5k6Q4c8e0g2Q4b7V1c8Q4b7e0u0Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5f1y4Q4b7e0S2Q4c8e0c8Q4b7U0S2Q4z5o6m8Q4c8e0g2Q4b7f1g2Q4z5f1q4Q4c8e0N6Q4b7e0S2Q4z5p5u0Q4c8e0g2Q4b7V1q4Q4b7e0k6Q4c8e0c8Q4b7U0S2Q4z5p5q4Q4c8e0k6Q4z5p5k6Q4z5e0m8Q4c8e0g2Q4z5p5c8Q4z5o6N6Q4c8e0c8Q4b7V1q4Q4z5o6k6Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0S2Q4b7V1c8Q4b7f1k6Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8e0g2Q4b7f1k6Q4b7U0W2Q4c8e0g2Q4z5o6g2Q4b7U0k6Q4c8e0k6Q4z5f1k6Q4b7e0g2Q4c8e0k6Q4z5f1c8Q4z5o6m8Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0W2Q4z5e0N6Q4b7e0S2Q4c8e0k6Q4b7e0N6Q4z5f1u0Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0u0Q4z5o6m8Q4z5f1y4Q4c8e0N6Q4z5o6q4Q4b7f1u0Q4c8e0N6Q4b7V1u0Q4z5e0u0Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0S2Q4b7V1c8Q4b7f1k6Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8e0u0Q4z5o6m8Q4z5f1c8Q4c8e0k6Q4z5e0N6Q4b7e0m8Q4c8e0W2Q4z5f1y4Q4z5o6m8Q4c8e0g2Q4z5p5c8Q4z5o6N6Q4c8e0N6Q4b7V1q4Q4b7e0N6Q4c8e0g2Q4z5p5c8Q4b7U0y4Q4c8e0g2Q4z5p5k6Q4b7f1k6Q4c8e0W2Q4z5e0S2Q4b7U0u0Q4c8e0g2Q4b7V1g2Q4b7e0q4Q4c8e0S2Q4b7f1k6Q4b7e0g2Q4c8e0N6Q4z5e0N6Q4z5o6g2Q4c8e0k6Q4b7f1k6Q4z5e0u0Q4c8e0y4Q4z5o6m8Q4z5o6t1`.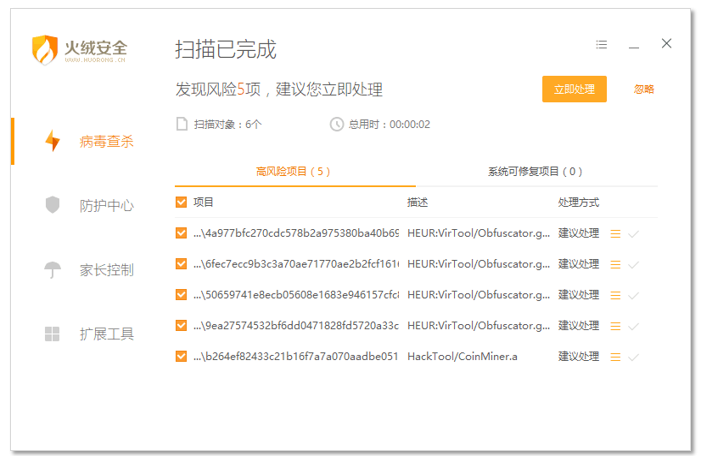
通过我们对该样本的分析,我们发现虽然样本来源为国内,但是其所使用的混淆技术已经具备一些简单的混淆器特征,如:使用无效参数调用系统API、利用系统API影响原始镜像加载流程等。用于解密原始镜像数据的代码数据被存放在资源“YBNHVXA”中,病毒没有使用资源相关的API读取数据而是直接通过硬地址进行数据读取。资源数据,如下图所示:
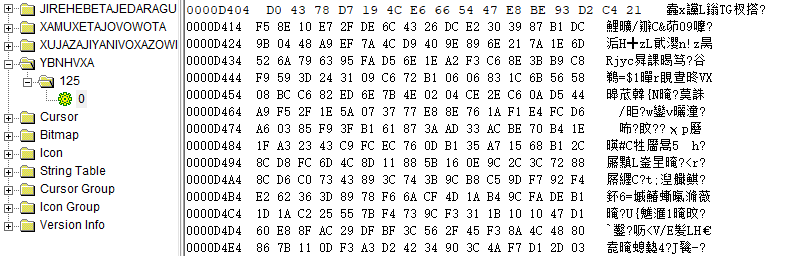
病毒资源
相关代码如下图所示:
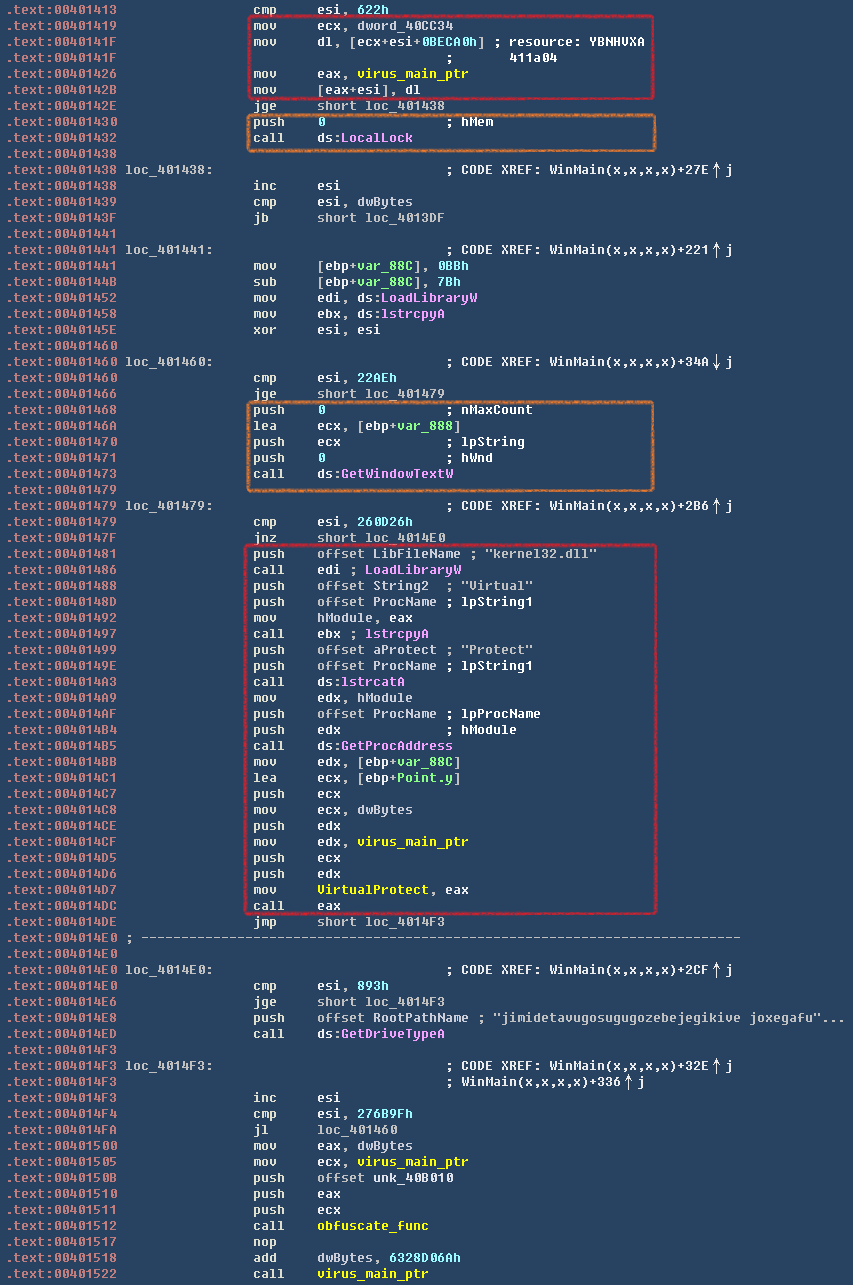
获取解密代码
在主要病毒逻辑代码中被插入了大量的无效函数调用,参数全部都为0。如果虚拟机引擎未对这些API进行模拟,则会无法解密出原始镜像数据。虽然该病毒所使用的混淆手法极为简单,但也已经具备了混淆器对抗虚拟机引擎的一些技术特点,可能将来国内病毒与安全软件的对抗方式也会以混淆器为主。相关代码如下图所示:
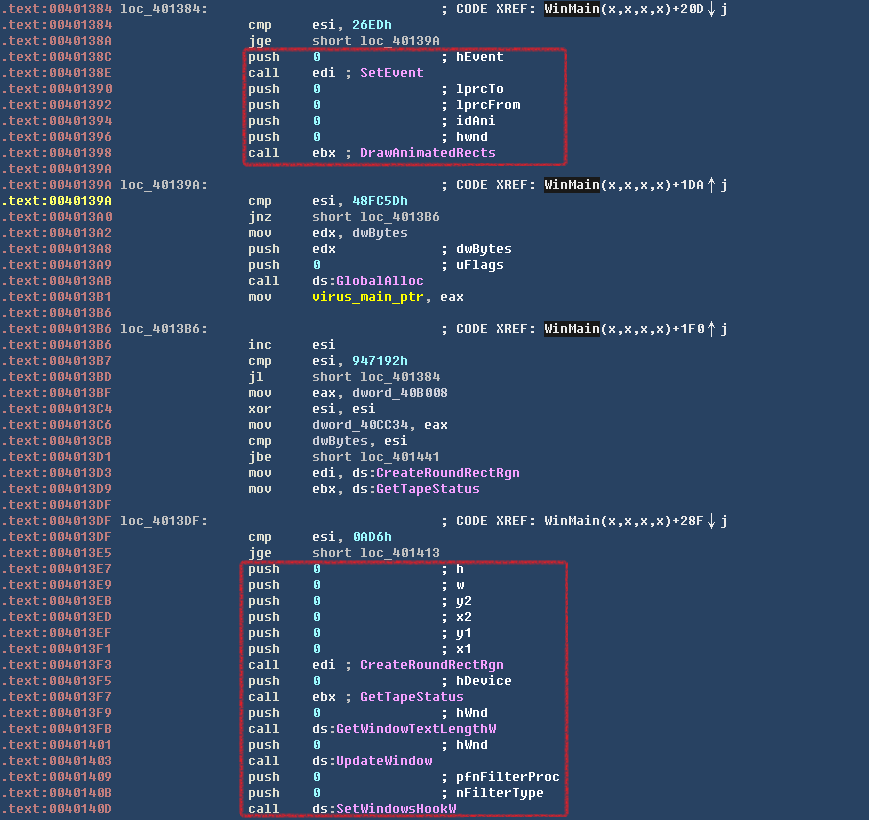
混淆代码
该病毒在火绒虚拟行为沙盒中的运行行为,如下图所示:
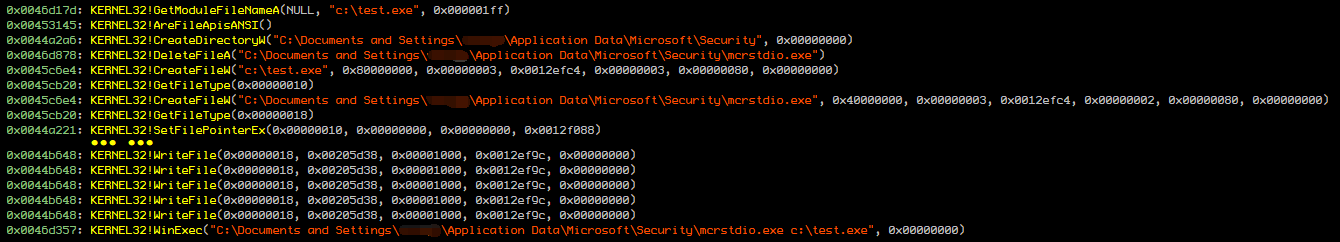
虚拟行为沙盒中的病毒行为
在混淆代码运行完成后,最终执行的恶意代码会挖取门罗币,矿工相关信息如下图所示:
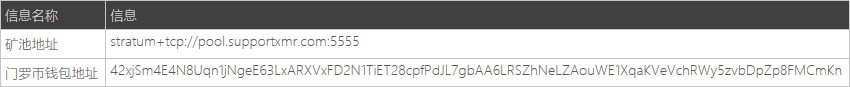
矿工信息
通过对门罗币钱包地址的查询,我们可以看到当前为该钱包地址进行挖矿的矿工情况,截止到此时矿工总数为483。如下图所述:

门罗币钱包情况
附录
文中涉及样本SHA256:

[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课

