-
-
[推荐]看雪.纽盾 KCTF 2019 Q3 | 第八题点评及解题思路
-
发表于: 2019-10-8 13:49 1898
-
稷下三贤者培养了许多极具天分的弟子,孙膑是其中佼佼者之一。这个天才少年将兵法与机关术巧妙地结合在一起。孙膑的成果令师兄庞涓感到威胁,甚至当众诋毁他。一次,孙膑在调查遗迹的途中遭遇狂暴的魔种。被追赶时摔下山崖,埋入一片废墟中。田忌发现好友失踪闯入废墟,试图解救孙膑。不幸的是,触动机关,田忌被卷入黑暗的漩涡。造成事故的巧合并非偶然。庞涓精心策划的完美报复实现了。后来孙膑被救出,保住了生命,代价则是双腿和好友田忌。田忌,一定还在某个地方活着,孙膑坚信。就像噩梦的夜晚,田忌焦急呼唤着他名字一样,现在轮到他以机关术的力量,重新打开无边无垠的时空之门,将最好的朋友带回家。

题目简介
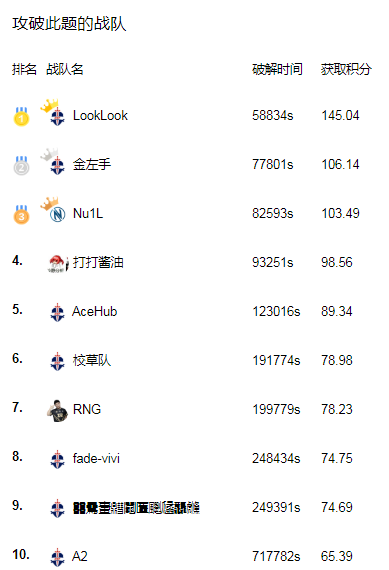
看雪评委crownless点评
出题团队简介
下面是团队简介:
某安全公司实习生,目前正在学习逆向和木马分析,希望能从各位大佬身上学习并提升自己。
设计思路
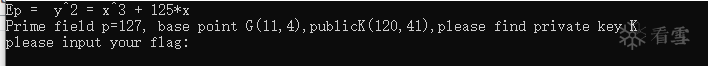

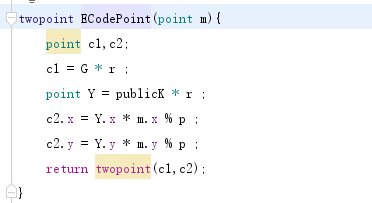
公钥K = 基点G * 私钥k
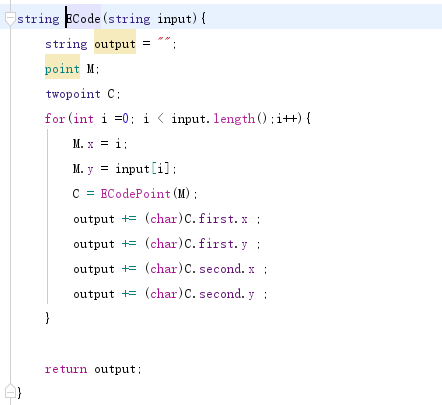
mov byte ptr ss:[ebp-5],0 mov eax, dword ptr fs:[0x30] mov al, byte ptr [eax + 2] mov byte ptr [ebp - 5], al movzx eax, byte ptr [ebp - 5]

解题思路

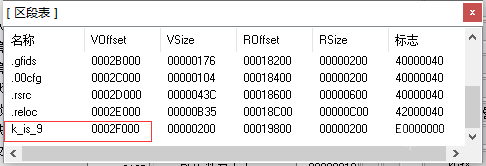
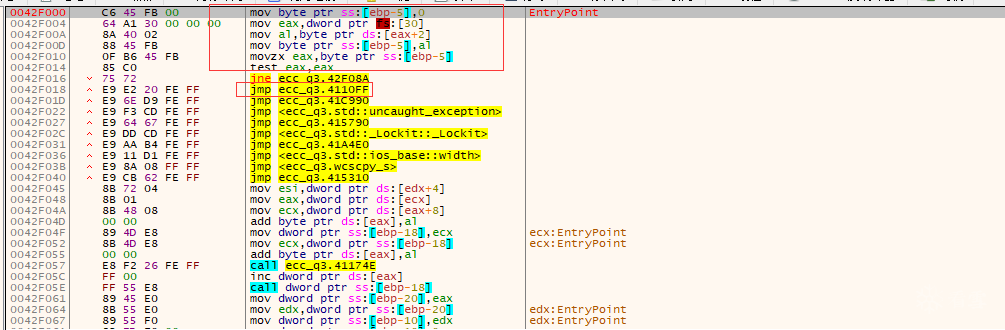
初步分析程序
k_is_9:0042F000 start proc near k_is_9:0042F000 mov byte ptr [ebp-5], 0 k_is_9:0042F004 mov eax, large fs:30h k_is_9:0042F00A mov al, [eax+2] k_is_9:0042F00D mov [ebp-5], al k_is_9:0042F010 movzx eax, byte ptr [ebp-5] k_is_9:0042F014 test eax, eax k_is_9:0042F016 k_is_9:0042F016 loc_42F016: ; CODE XREF: start:loc_42F08A↓j k_is_9:0042F016 jnz short loc_42F08A k_is_9:0042F018 jmp sub_4110FF
int __usercall keyFunc@<eax>(int a1@<xmm0>)
{
int v1; // edx
int v2; // eax
int v3; // eax
int v4; // ecx
int v5; // eax
int v6; // eax
int v7; // ecx
int v8; // eax
int v9; // eax
int v10; // ecx
_DWORD *v11; // eax
int v12; // eax
int v13; // ecx
void *v14; // edx
int v16; // [esp-1Ch] [ebp-1F8h]
int v17; // [esp-8h] [ebp-1E4h]
void *v18; // [esp-4h] [ebp-1E0h]
char v19; // [esp+0h] [ebp-1DCh]
struc_String *keyString_1; // [esp+10h] [ebp-1CCh]
struc_String *keyString; // [esp+14h] [ebp-1C8h]
int v22; // [esp+18h] [ebp-1C4h]
char goalBuf[56]; // [esp+20h] [ebp-1BCh]
char v24; // [esp+58h] [ebp-184h]
int v25; // [esp+60h] [ebp-17Ch]
char v26; // [esp+6Ch] [ebp-170h]
char v27; // [esp+7Fh] [ebp-15Dh]
struc_String sting; // [esp+88h] [ebp-154h]
int *v29; // [esp+ACh] [ebp-130h]
int v30; // [esp+B8h] [ebp-124h]
int v31; // [esp+BCh] [ebp-120h]
struc_String goalString; // [esp+188h] [ebp-54h]
struc_String keyStringFromInput; // [esp+1ACh] [ebp-30h]
int v34; // [esp+1CCh] [ebp-10h]
int v35; // [esp+1D8h] [ebp-4h]
int savedregs; // [esp+1DCh] [ebp+0h]
G1.x = 11;
G1.y = 4;
v30 = j_timesPiont((struc_Point *)a1, &G1, times);
v31 = v1;
G2.x = v30;
G2.y = v1;
sub_4113B6((int)&keyStringFromInput, a1, byte_4252C2);
v35 = 0;
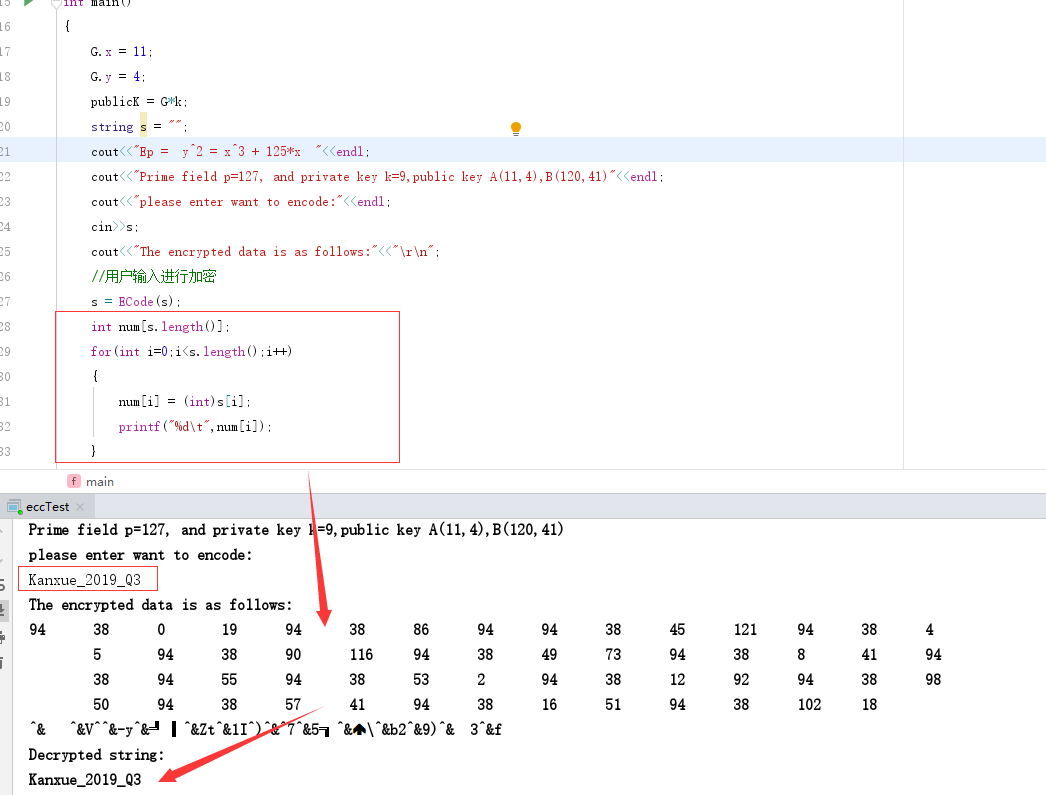
v2 = sub_411802(std::cout, "Ep = y^2 = x^3 + 125*x ");
v3 = std::basic_ostream<char,std::char_traits<char>>::operator<<(v2, sub_411159);
j_asmFun(v4, &v19 == &v19, v3, a1);
v5 = sub_411802(std::cout, "Prime field p=127,base point G(11,4),publicK(120,41) please find private key k");
v6 = std::basic_ostream<char,std::char_traits<char>>::operator<<(v5, sub_411159);
j_asmFun(v7, &v19 == &v19, v6, a1);
v8 = sub_411802(std::cout, "input your flag:");
v9 = std::basic_ostream<char,std::char_traits<char>>::operator<<(v8, sub_411159);
j_asmFun(v10, &v19 == &v19, v9, a1);
getInput(a1, std::cin, &keyStringFromInput); // 获取输入
v29 = &v16;
v22 = sub_411447(&v16, a1, &keyStringFromInput);
keyString = (struc_String *)calcuKey(a1, (int)&sting);// 根据输入生成key
keyString_1 = keyString;
stringCopy(&keyStringFromInput, a1, keyString);
releaseString(&sting, a1);
goalBuf[0] = 0x5E; //目标结果字串
goalBuf[1] = 0x26;
goalBuf[2] = 0;
goalBuf[3] = 0x13;
goalBuf[4] = 94;
goalBuf[5] = 38;
goalBuf[6] = 86;
goalBuf[7] = 94;
goalBuf[8] = 94;
goalBuf[9] = 38;
goalBuf[10] = 45;
goalBuf[11] = 121;
goalBuf[12] = 94;
goalBuf[13] = 38;
goalBuf[14] = 4;
goalBuf[15] = 5;
goalBuf[16] = 94;
goalBuf[17] = 38;
goalBuf[18] = 90;
goalBuf[19] = 116;
goalBuf[20] = 94;
goalBuf[21] = 38;
goalBuf[22] = 49;
goalBuf[23] = 73;
goalBuf[24] = 94;
goalBuf[25] = 38;
goalBuf[26] = 8;
goalBuf[27] = 41;
goalBuf[28] = 94;
goalBuf[29] = 38;
goalBuf[30] = 94;
goalBuf[31] = 55;
goalBuf[32] = 94;
goalBuf[33] = 38;
goalBuf[34] = 53;
goalBuf[35] = 2;
goalBuf[36] = 94;
goalBuf[37] = 38;
goalBuf[38] = 12;
goalBuf[39] = 92;
goalBuf[40] = 94;
goalBuf[41] = 38;
goalBuf[42] = 98;
goalBuf[43] = 50;
goalBuf[44] = 94;
goalBuf[45] = 38;
goalBuf[46] = 57;
goalBuf[47] = 41;
goalBuf[48] = 94;
goalBuf[49] = 38;
goalBuf[50] = 16;
goalBuf[51] = 51;
goalBuf[52] = 94;
goalBuf[53] = 38;
goalBuf[54] = 102;
goalBuf[55] = 18;
v18 = j_getThis_0((int)&v27);
v11 = sub_4112C1(&v26, (int)goalBuf, (int)&v24);
createString(&goalString, a1, *v11, v11[1], (int)v18);
if ( stringCmp((int)&keyStringFromInput, a1, (int)&goalString) )// key 验证
sub_41186B("try again", v19);
else
sub_41186B("Congratulations~~", v19);
v12 = system("pause");
j_asmFun(v13, &v19 == &v19, v12, a1);
v25 = 0;
releaseString(&goalString, a1);
v35 = -1;
releaseString(&keyStringFromInput, a1);
v18 = v14;
v17 = v25;
sub_411677((int)&savedregs, (int)&dword_41BC54);
return j_asmFun((unsigned int)&savedregs ^ v34, 1, v17, a1);
}分析核心的key生成函数
for ( i = 0; ; ++i )
{
len = getInpuKeyLen((int)sting, a1); // 获取key长度
if ( i >= len )
break;
index = i;
oneKey = *(char *)getKeyByIndex((int)sting, a1, i);
pointPair_1 = (struc_PointPair *)timesPiontByOneKey(a1, &pointPair, index, oneKey);
copyPoint_1(&pointPair_2, a1, pointPair_1);
j_addZuobiao2Buf_0(a1, (struc_String *)&resultStr, pointPair_2.p1_x);
j_addZuobiao2Buf_0(a1, (struc_String *)&resultStr, pointPair_2.p1_y);
j_addZuobiao2Buf_0(a1, (struc_String *)&resultStr, pointPair_2.p2_x);
j_addZuobiao2Buf_0(a1, (struc_String *)&resultStr, pointPair_2.p2_y);
}int __usercall timesPiontByOneKey_0@<eax>(struc_Point *a1@<xmm0>, struc_PointPair *result, int index, int onekey)
{
int y1AfterTimes; // edx
int y2AfterTimes; // edx
struc_Point p1; // [esp+100h] [ebp-20h]
struc_Point p2; // [esp+110h] [ebp-10h]
int v9; // [esp+11Ch] [ebp-4h]
int savedregs; // [esp+120h] [ebp+0h]
p2.x = j_timesPiont(a1, &G1, 17); // G1(11,4)->(0x5e,0x26)
p2.y = y1AfterTimes;
p1.x = index * j_timesPiont(a1, &G2, 17) % 127;// G2(14,91)->(0x56,0x5A)
p1.y = onekey * y2AfterTimes % 127;
copyPoint(result, (int)a1, (int)&p2, (int)&p1);
sub_411677((int)&savedregs, (int)&dword_417788);
return j_asmFun((unsigned int)&savedregs ^ v9, 1, (int)result, (int)a1);
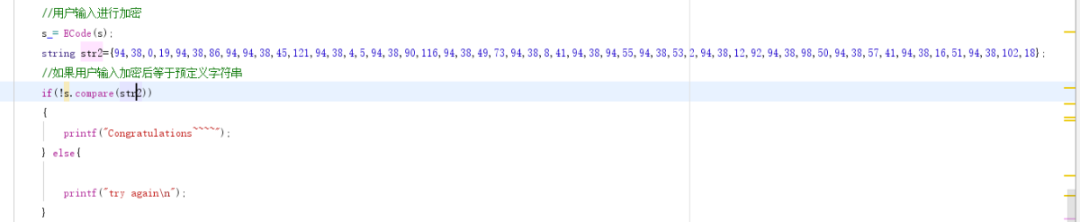
}createString(&goalString, a1, *v11, v11[1], (int)v18);
if ( stringCmp((int)&keyStringFromInput, a1, (int)&goalString) )// key 验证
sub_41186B("try again", v19);
else
sub_41186B("Congratulations~~", v19);逆向输入
public class Q3CTF8 {
static char [] result1 = {0x13,0x5E,0x79,0x05,0x74,0x49,0x29,0x37,0x02,0x5C,0x32,0x29,0x33,0x12};
static char key;
public static void main(String[] args)
{
for(int k = 0;k<result1.length;k++)
{
key = result1[k];
for(int i =0;i<0xff;i++)
{
if(i*0x5A%127==key)
{
System.out.printf("%c",i);
break;
}
}
}
}
} - End -
合作伙伴

上海纽盾科技股份有限公司(c8fK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3&6W2N6$3c8G2L8W2)9J5k6h3&6W2N6q4!0q4c8W2!0n7b7#2)9^5z5g2!0q4y4W2)9^5z5q4)9&6x3q4!0q4y4#2!0m8b7W2)9^5b7W2!0q4y4q4!0n7b7g2)9^5c8e0t1H3x3o6W2Q4c8e0g2Q4b7U0W2Q4b7U0c8Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0k6Q4z5e0S2Q4b7f1k6Q4c8e0c8Q4b7U0S2Q4z5o6m8Q4c8e0g2Q4b7f1g2Q4b7U0k6Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0u0Q4z5o6m8Q4z5f1y4Q4c8e0N6Q4b7V1c8Q4z5e0q4Q4c8e0N6Q4b7V1u0Q4z5f1y4Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0u0Q4z5o6m8Q4z5f1c8Q4c8e0c8Q4b7U0S2Q4b7V1q4Q4c8e0c8Q4b7U0S2Q4b7V1u0Q4c8e0S2Q4b7V1c8Q4b7U0c8Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0u0Q4z5o6m8Q4z5f1y4Q4c8e0N6Q4b7e0N6Q4z5e0q4Q4c8e0k6Q4z5p5q4Q4z5o6m8Q4c8e0k6Q4b7V1q4Q4z5e0m8Q4c8e0S2Q4z5o6N6Q4b7f1q4Q4c8e0N6Q4z5e0c8Q4z5f1k6Q4c8e0k6Q4b7U0c8Q4b7V1u0Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0N6Q4b7V1q4Q4b7V1c8Q4c8e0N6Q4z5f1u0Q4b7V1g2Q4c8e0k6Q4z5f1y4Q4z5p5c8Q4c8e0g2Q4z5p5q4Q4b7e0q4Q4c8e0N6Q4b7e0c8Q4b7V1g2Q4c8e0c8Q4b7V1y4Q4z5f1q4Q4c8e0u0Q4z5o6m8Q4z5f1c8Q4c8e0c8Q4b7U0S2Q4b7V1q4Q4c8e0k6Q4b7e0m8Q4b7U0S2Q4c8e0g2Q4b7V1k6Q4z5o6y4Q4c8e0N6Q4b7V1u0Q4z5p5k6Q4c8e0S2Q4z5e0m8Q4b7e0g2Q4c8e0N6Q4z5e0m8Q4z5o6k6Q4c8e0g2Q4b7V1k6Q4b7U0g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0N6Q4b7V1c8Q4z5e0q4Q4c8e0N6Q4b7V1u0Q4z5f1y4Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0c8Q4b7V1q4Q4b7e0N6Q4c8e0g2Q4z5e0y4Q4z5o6q4Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0N6Q4b7e0m8Q4z5e0c8Q4c8e0g2Q4z5p5k6Q4z5e0q4Q4c8e0y4Q4z5o6m8Q4z5o6q4Q4c8e0N6Q4z5e0c8Q4z5f1k6Q4c8e0c8Q4b7V1q4Q4b7e0N6Q4c8e0y4Q4z5o6m8Q4z5o6q4Q4c8e0W2Q4z5e0c8Q4z5o6m8Q4c8e0g2Q4z5e0c8Q4b7f1g2Q4c8e0y4Q4z5o6m8Q4z5o6q4Q4c8e0g2Q4z5e0c8Q4b7f1g2Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8e0k6Q4z5f1y4Q4z5p5c8Q4c8e0g2Q4z5p5q4Q4b7e0q4Q4c8e0c8Q4b7U0S2Q4z5p5g2Q4c8e0N6Q4z5f1u0Q4b7U0S2Q4c8e0g2Q4z5o6g2Q4b7U0y4Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0k6Q4z5f1y4Q4z5p5c8Q4c8e0g2Q4z5p5q4Q4b7e0q4Q4c8e0c8Q4b7U0S2Q4b7V1q4Q4c8e0c8Q4b7U0S2Q4z5o6m8Q4c8e0c8Q4b7V1c8Q4z5e0y4Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0c8Q4b7U0S2Q4z5e0y4Q4c8e0c8Q4b7U0S2Q4z5f1q4Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0g2Q4z5o6g2Q4b7f1y4Q4c8e0g2Q4z5p5k6Q4b7U0S2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0S2Q4z5o6N6Q4b7U0c8Q4c8e0g2Q4z5p5q4Q4z5f1u0Q4c8e0c8Q4b7V1q4Q4z5p5g2Q4c8e0c8Q4b7U0S2Q4b7V1q4Q4c8e0k6Q4z5e0g2Q4b7U0m8Q4c8e0g2Q4b7f1c8Q4z5e0N6Q4c8e0g2Q4z5p5y4Q4z5e0k6Q4c8e0k6Q4z5e0N6Q4b7U0k6Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0S2Q4z5o6y4Q4z5p5y4Q4c8e0k6Q4z5e0W2Q4b7f1k6Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0N6Q4z5e0c8Q4b7e0S2Q4c8e0k6Q4z5o6S2Q4b7U0N6Q4c8e0k6Q4z5p5k6Q4z5e0m8Q4c8e0c8Q4b7V1g2Q4z5f1u0Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0c8Q4b7V1q4Q4b7e0N6Q4c8e0g2Q4z5e0y4Q4z5o6q4Q4c8e0y4Q4z5o6m8Q4z5o6q4Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0k6Q4z5f1y4Q4z5p5c8Q4c8e0g2Q4z5p5q4Q4b7e0q4Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0g2Q4z5p5k6Q4z5p5q4Q4c8e0N6Q4b7f1c8Q4z5o6W2Q4c8e0N6Q4b7V1q4Q4b7e0N6Q4c8e0c8Q4b7V1k6Q4z5f1c8Q4c8e0k6Q4z5p5q4Q4b7e0c8Q4c8e0N6Q4b7f1c8Q4z5o6W2Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0S2Q4b7e0N6Q4b7e0y4Q4c8e0g2Q4z5o6k6Q4b7U0y4Q4c8e0k6Q4z5e0k6Q4b7U0W2Q4c8e0k6Q4b7e0q4Q4z5o6S2Q4c8e0y4Q4z5o6m8Q4z5o6t1`.
原文链接:166K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0M7q4)9J5k6i4N6W2K9i4S2A6L8W2)9J5k6i4q4I4i4K6u0W2j5$3!0E0i4K6u0r3M7#2)9J5c8X3c8F1c8V1A6X3g2i4j5H3z5g2)9#2k6U0m8r3K9p5E0T1h3s2k6Y4N6$3E0$3f1b7`.`.
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课

