-
-
[原创]第四题:西部乐园 唐僧流解题
-
发表于: 2019-12-17 16:59 4956
-
唐师傅去西天取经,佛祖布置了81个作业,唐师傅没有孙长老的法力,不能biu~一下拿到Key,只能吃了一亏,又上了一当,一个一个坑踩。

双击 ConsoleApplication1.exe,看到是个
Console程序:

容易来到sub_1400020A0():

驱动里面,只有一个分发函数sub_1400020A0():

调试的时候驱动入口处有个坑
_security_cookie
== 0x2B992DDFA232i64
,会蓝屏,windbg改掉判断时RCX的值;
__int64 _security_init_cookie()
{
__int64 result; // rax
if ( !_security_cookie || _security_cookie == 0x2B992DDFA232i64 ) // 坑
__fastfail(6u);
result = ~_security_cookie;
qword_140003078 = ~_security_cookie;
return result;
}
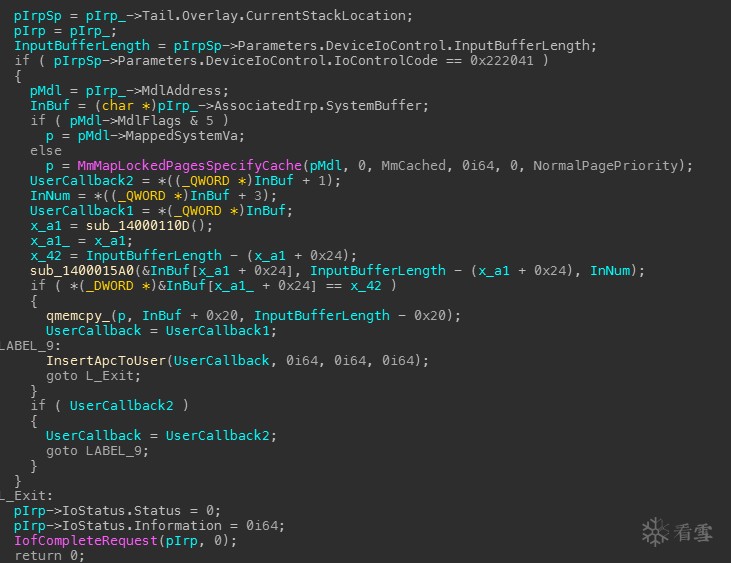
来到分发函数,
重点语句是:
sub_1400015A0(&InBuf[x_a1 + 0x24], InputBufferLength - (x_a1 + 0x24), InNum);
if ( *(_DWORD *)&InBuf[x_a1_ + 0x24] == x_42 ) // 判断是否成功
{
qmemcpy_(p, InBuf + 0x20, InputBufferLength - 0x20);
UserCallback = UserCallback1;
LABEL_9:
InsertApcToUser(UserCallback, 0i64, 0i64, 0i64); // 插APC让应用层弹框
goto L_Exit;
}
把
sub_1400015A0扒出来,从windbg拿到当时的输入数据与长度:
#include <stdio.h>
#include <windows.h>
char InBuf[] = {
0x50, 0xf8, 0x31, 0x00, 0x00, 0x00, 0x00, 0x00, 0x50, 0x20, 0x0b, 0x3f, 0x01, 0x00, 0x00, 0x00,
0xc8, 0x06, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x91, 0x5f, 0x01, 0x00, 0x00, 0x00, 0x00, 0x00,
0xeb, 0x18, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x08, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x60, 0x6b, 0x0b, 0x3f, 0x01, 0x00, 0x00, 0x00, 0x55, 0x48, 0x8b, 0xec, 0xe8, 0x01,
0x00, 0x00, 0x00, 0x90, 0x48, 0x8b, 0xc4, 0x48, 0xc7, 0xc1, 0x10, 0x00, 0x00, 0x00, 0x48, 0x33,
0xd2, 0x48, 0xf7, 0xf1, 0x83, 0xfa, 0x00, 0x75, 0x17, 0x48, 0x8b, 0x04, 0x24, 0x48, 0x89, 0x44,
0x24, 0xf8, 0x48, 0x8b, 0x44, 0x24, 0x08, 0x48, 0x89, 0x04, 0x24, 0x48, 0x8d, 0x64, 0x24, 0xf8,
0x48, 0x8b, 0x0c, 0x24, 0x48, 0x8b, 0x51, 0xdf, 0x48, 0x83, 0xfa, 0x00, 0x74, 0x04, 0x48, 0x89,
0x55, 0x08, 0x48, 0x8b, 0x51, 0xe7, 0x48, 0x83, 0xfa, 0x00, 0x48, 0xba, 0x2d, 0x7f, 0x6c, 0x43,
0xf6, 0x7f, 0x00, 0x00, 0x48, 0xb8, 0xce, 0x7f, 0x6c, 0x43, 0xf6, 0x7f, 0x00, 0x00, 0x9c, 0x48,
0x2b, 0xc2, 0x9d, 0x74, 0x17, 0x48, 0x8d, 0x51, 0xdd, 0x48, 0x8d, 0x14, 0x10, 0x48, 0x8b, 0x41,
0xe7, 0x48, 0x8d, 0x04, 0x10, 0x48, 0x8b, 0x49, 0xef, 0x51, 0xff, 0xd0, 0x48, 0x8b, 0xe5, 0x5d,
0xc3, 0x00, 0x00, 0x00, 0x00, 0xe8, 0x59, 0x0d, 0x6d, 0x80, 0x3c, 0xa2, 0x78, 0x15, 0x87, 0x16,
0x16, 0x07, 0x26, 0x68, 0x55, 0x7f, 0x12, 0xf1, 0xef, 0xf9, 0xa1, 0x9c, 0xe8, 0xea, 0x9c, 0x90,
0xf4, 0x9f, 0x3a, 0xa8, 0x8c, 0x27, 0x47, 0x79, 0xf6, 0xdc, 0x20, 0x7f, 0x86, 0xed, 0x34, 0x7e,
0xf7, 0x1c, 0x55, 0x6b, 0xf6, 0xef, 0xf2, 0x2a, 0x7a, 0xf0, 0x44, 0x50, 0x8a, 0x9b, 0xe1, 0xc4,
0xe1, 0x45, 0x90, 0x2b, 0x0e, 0xcf, 0xaf, 0xff, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00};
__int16 __fastcall sub_1400015A0(BYTE *a1, int a2, int InNum)
{
ULONG v3; // rax
int i; // er10
int v6; // esi
__int32 v7; // r11
unsigned __int8 v8; // al
__int32 v9; // r8
__int16 v10; // di
unsigned __int16 v11; // dx
i = InNum - 1;
if ( InNum - 1 >= 0 )
{
v6 = a2 - 1;
do
{
v7 = i % (signed int)a2;
if ( i % (signed int)a2 )
{
v8 = a1[v7 - 1];
v9 = i % (signed int)a2;
}
else
{
v8 = a1[a2 - 1];
v9 = 0i64;
}
if ( (DWORD)v7 == v6 )
v10 = (unsigned __int8)*a1 + ((unsigned __int8)a1[v9] << 8);
else
v10 = *(WORD *)&a1[v9];
v11 = v10 + v8;
//LOWORD(v3) = v11 >> 8;
v3 = v11 >> 8;
a1[v9] = HIBYTE(v11);
if ( (DWORD)v7 == v6 )
*a1 = v11;
else
a1[v9 + 1] = v11;
--i;
}
while ( i >= 0 );
}
return (signed __int16)v3;
}
int main()
{
ULONG x_a1 = 0xa1;
ULONG InputBufferLength = 0x107;
for (ULONG i = 90000; i <= 96000; i++)
{
char t[400];
memcpy(t, InBuf, sizeof(InBuf));
sub_1400015A0((BYTE *)&t[x_a1 + 0x24], InputBufferLength - (x_a1 + 0x24), i);
if ( *(DWORD *)&t[x_a1 + 0x24] == 0x42 )
{
printf("find Key : %d\n", i);
getchar();
break;
}
}
return 0;
}-End-
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
最后于 2019-12-17 17:11
被囧囧编辑
,原因:
赞赏
他的文章
- [原创]Arm thumb Cortex-M0 opcode 解析 3680
- IO完成端口原理 2678
- 代码角度看SSL握手过程 13695
- 给Internet Download Manager打补丁 5997
- [原创]分析X绒hrdevmon.sys,突破U盘访问控制,摄像头保护原理 9950
赞赏
雪币:
留言:

