-
-
8月4日安全资讯分享~
-
发表于: 2020-8-4 10:54 2349
-
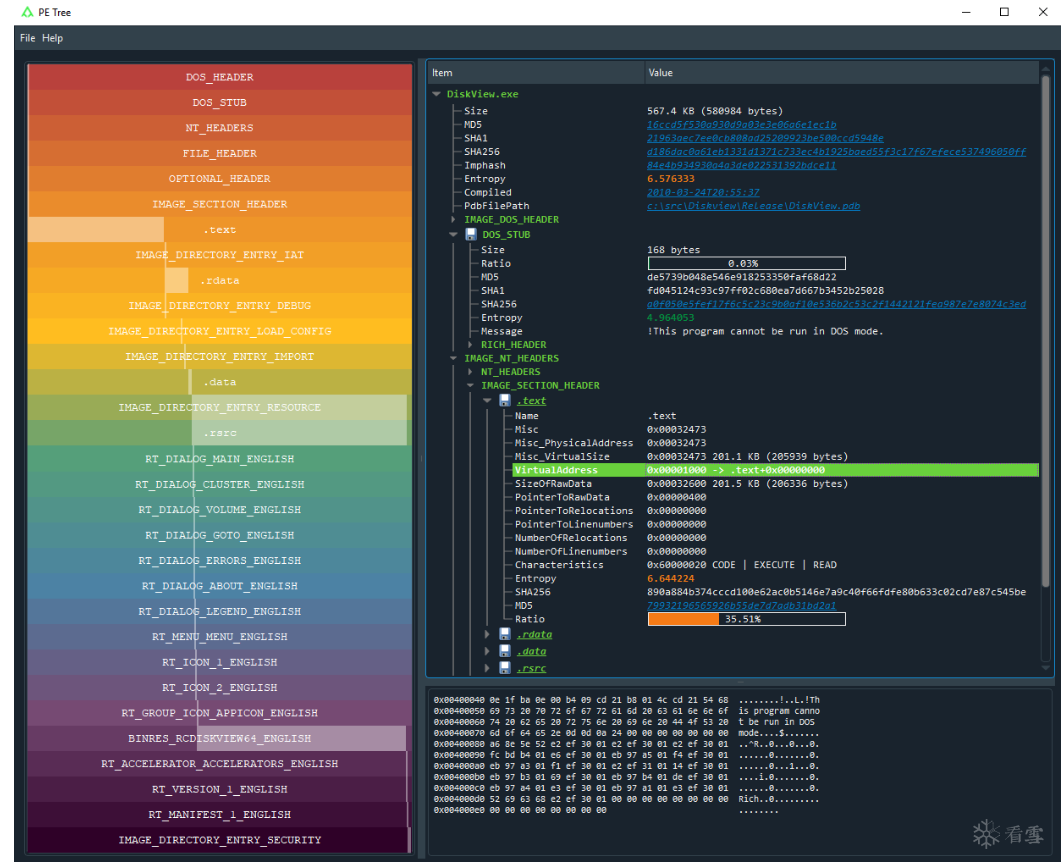
PE Tree 一款用于辅助逆向分析PE的开源工具
eaaK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6T1L8r3q4U0K9$3u0W2M7Y4u0&6i4K6u0r3M7r3g2Q4y4h3k6@1M7X3g2W2
如何通过flutter进行SSL Pinning绕过
21cK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0k6h3c8A6N6h3#2Q4x3X3g2U0L8$3#2Q4x3V1k6Q4y4o6m8H3N6$3^5H3M7$3g2U0i4K6u0r3k6X3I4#2N6s2c8W2M7X3q4H3M7q4)9J5k6s2m8W2L8X3g2@1M7X3q4@1K9h3!0F1i4K6u0V1N6r3g2K6N6r3W2F1k6#2)9J5k6r3q4F1L8%4c8Z5k6i4u0Q4x3X3c8%4j5i4W2Q4x3X3c8@1L8#2)9J5k6r3u0&6M7r3q4K6M7#2)9J5k6s2y4K6L8q4)9J5k6s2m8A6L8X3&6A6L8X3N6Q4x3X3c8X3y4o6f1H3k6o6q4S2y4o6l9%4j5U0b7`.
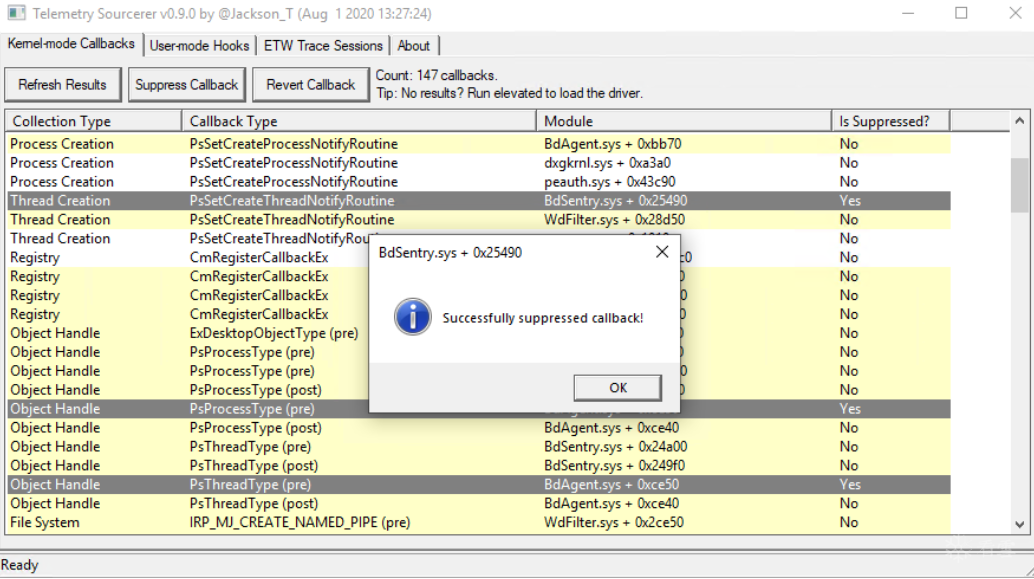
红队开源工具TelemetrySourcerer可以枚举和禁用AV/EDR
748K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6B7N6r3S2#2M7X3q4A6M7$3q4E0P5g2)9J5c8W2c8W2L8r3g2E0k6i4c8J5P5g2y4G2N6i4u0U0k6i4u0W2M7R3`.`.
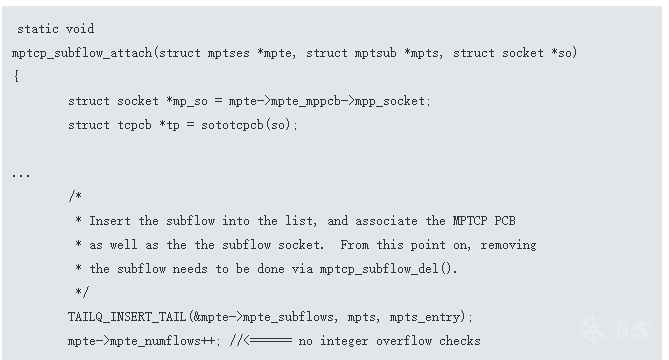
盘古对MPTCP整数溢出概要分析
909K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2M7r3q4F1k6%4g2Q4x3X3g2A6L8#2)9J5c8W2)9K6c8Y4m8Q4x3@1b7J5x3e0x3`.
具有多个C2协议的powershell bot分析
915K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6A6M7$3y4Q4x3X3g2K6j5h3&6K6i4K6u0W2k6h3c8#2i4K6u0r3k6r3W2S2M7Y4W2Q4x3V1j5J5y4U0b7J5x3l9`.`.
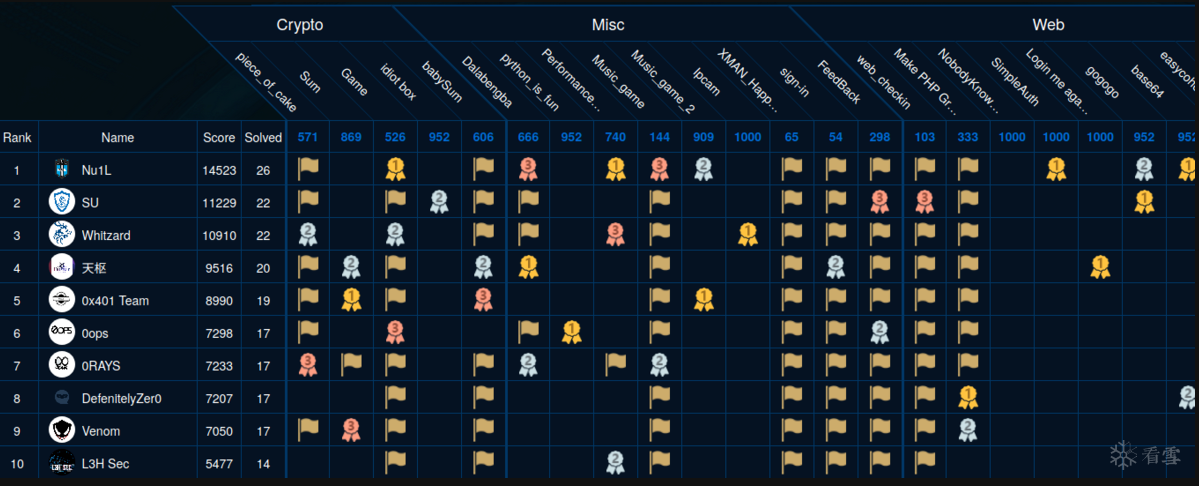
WMCTF 2020 Writeup
7a4K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6H3N6s2u0Q4x3X3c8&6N6h3c8S2K9g2)9J5k6h3S2S2N6r3g2F1j5h3u0D9L8$3N6Q4x3X3g2U0L8$3#2Q4x3V1k6W2L8Y4c8J5P5g2)9J5c8U0t1H3x3U0m8Q4x3V1j5H3z5q4)9J5c8U0l9K6i4K6u0r3x3e0t1H3x3e0f1K6
开源的协议封装工具Mistica
992K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6u0L8X3y4A6k6r3g2p5K9h3N6A6N6r3q4D9i4K6u0r3e0h3W2K6N6r3W2U0j5b7`.`.

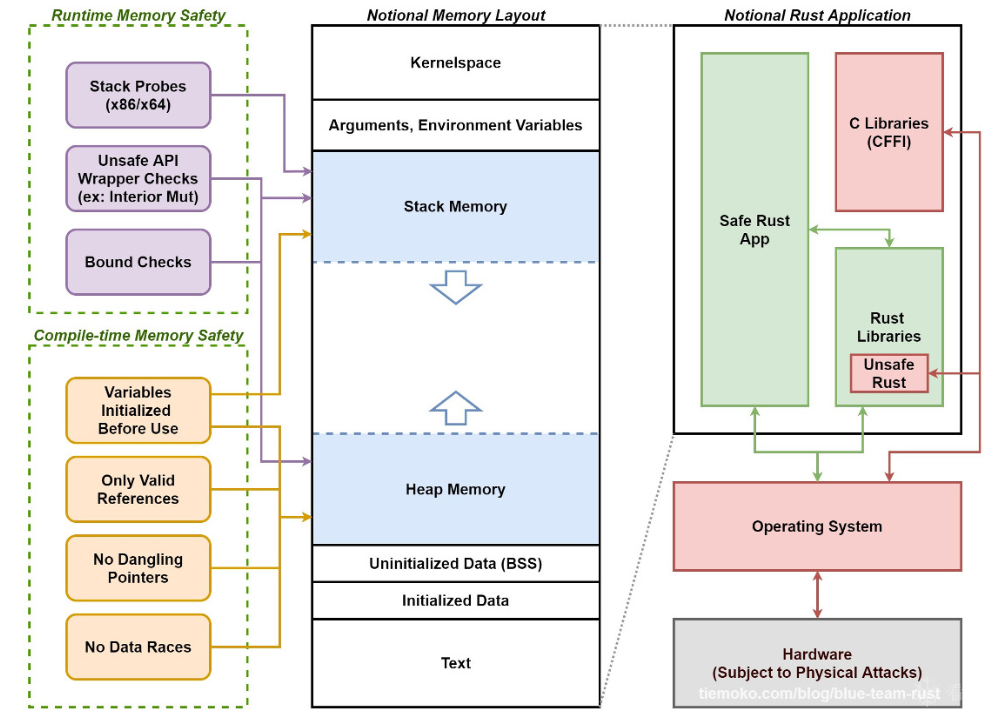
从蓝队角度介绍内存安全
474K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6@1K9h3g2E0L8$3E0G2i4K6u0W2j5$3!0E0i4K6u0r3j5X3I4G2k6#2)9J5c8X3u0D9N6h3g2Q4x3X3c8@1k6h3q4E0i4K6u0V1M7Y4g2K6N6q4)9J5c8R3`.`.
分享资料主要来源于玄武日推,sec.today 欢迎大家讨论,翻译,复现分享~
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
赞赏
- [推荐] [小活动] 庆祝建党,发帖送书送T恤 5042
- [原创] 分享一份恶意代码分析方向的基础技能表 22864
- [分享]分享一些平时在进行恶意代码分析时常用的网站 12459
- [原创]南亚APT组织"蔓灵花"历史攻击活动浅析(上) 7410

