-
-
[原创]ios-dumpdecrypted砸壳
-
发表于:
2020-12-27 15:12
77161
-
fa6K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6K6N6r3g2X3j5h3&6W2M7%4y4W2M7W2)9J5c8X3c8#2L8i4m8V1k6h3y4J5P5i4m8@1k6h3c8Q4x3V1k6S2M7X3y4Z5K9i4k6W2i4K6u0r3L8h3q4K6N6r3g2J5i4K6u0W2P5X3W2H3
复制到iPhone /var/mobile/ 目录下
可以使用ssh连接到手机
我直接使用了 Terminal 手机命令工具
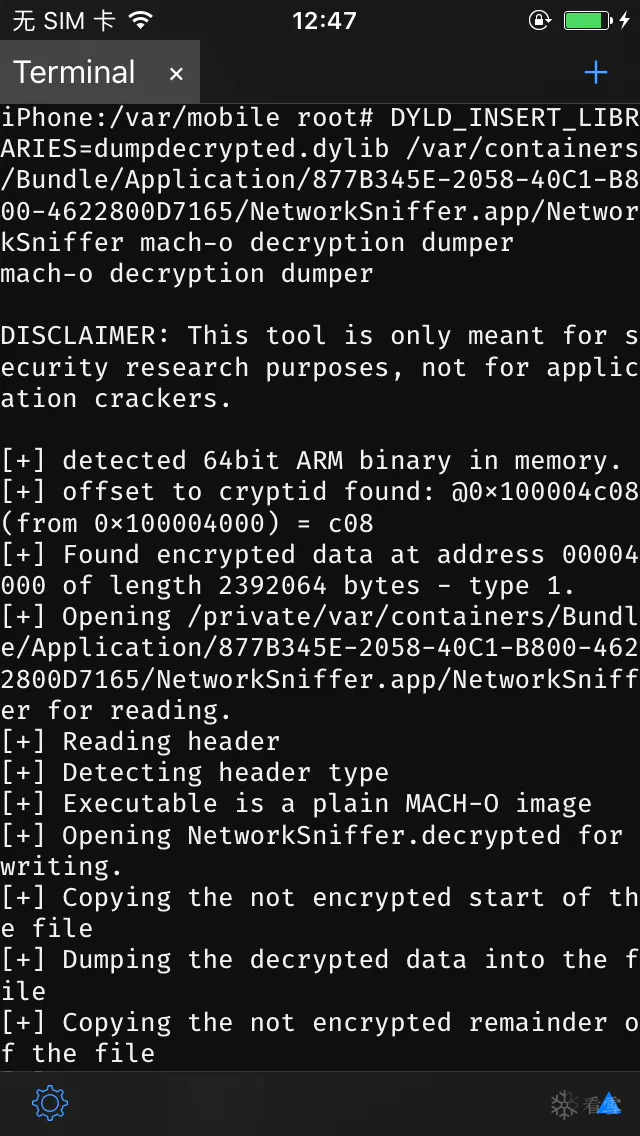
砸壳成功输出目录为命令执行当前目录 生成 目标二进制文件.decrypted
删除后缀名.decrypted 命令 chmod -R 777 二进制文件
查壳 otool -l 二进制文件 | grep crypt 结果为 0 成功脱壳
这样一般是由于 dumpdecrypted.dylib 没有进行签名导致的,我们需要对它进行签名
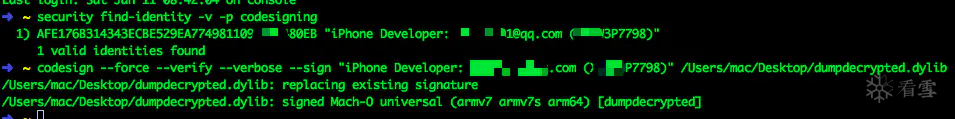
之前一直使用简书记录:d77K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2B7K9h3q4F1M7$3S2#2i4K6u0W2j5$3!0E0i4K6u0r3M7q4)9J5c8X3q4X3x3K6j5K6x3$3y4W2y4X3b7#2z5b7`.`.
DYLD_INSERT_LIBRARIES=dumpdecrypted.dylib /var/containers/Bundle/Application/877B345E-2058-40C1-B800-4622800D7165/NetworkSniffer.app/NetworkSniffer mach-o decryption dumper
DYLD_INSERT_LIBRARIES=dumpdecrypted.dylib /var/containers/Bundle/Application/877B345E-2058-40C1-B800-4622800D7165/NetworkSniffer.app/NetworkSniffer mach-o decryption dumper
DYLD_INSERT_LIBRARIES=dumpdecrypted.dylib /var/containers/Bundle/Application/877B345E-2058-40C1-B800-4622800D7165/NetworkSniffer.app/NetworkSniffer mach-o decryption dumper
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课