-
-
[转帖]How To Reverse Engineer RC4 Crypto For Malware Analysis
-
发表于: 2021-1-24 05:59 1986
-
How To Reverse Engineer RC4 Crypto For Malware Analysis
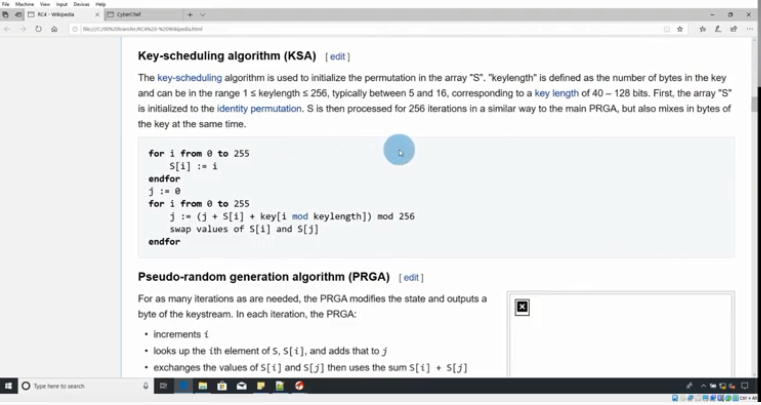
In this video, we will learn how to identify, extract the cryptographic key, and dynamically verify RC4 cryptography commonly used in malware. We’ll cover the theory and then walk through several examples to demonstrate the concepts.
RC4 crypto is one of the most widely used algorithms malware uses to obfuscate it’s high valued data like url strings and other IOCs. Learning to deal with this capability is a key requirement to advance your malware analysis skills.
Download the malware samples at 486K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0j5h3I4K6K9r3q4J5k6g2)9J5k6h3y4G2L8b7`.`. to review in your own analysis lab:
1. Example 1: 221cbb3df05e346187af129aa128af44c002945955b2f98f1a77b911b636e4db
2. Example 2: 6652588e445d7dca9f68c260d4b471ebabfcd044084837ccd3d0eeb53eb45288
3. Example 3: 58e923ff158fb5aecd293b7a0e0d305296110b83c6e270786edcc4fea1c8
View our in-person and on-demand malware analysis training
e4bK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6m8c8@1c8o6M7$3g2J5N6X3W2U0k6i4y4Q4x3X3g2U0L8$3#2Q4x3V1k6@1M7X3q4A6L8X3W2F1k6#2)9J5c8R3`.`.
Follow me on Twitter for reverse engineering tips and resources
1c9K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6@1N6$3W2@1N6r3g2J5i4K6u0W2j5$3!0E0i4K6u0r3b7f1N6p5b7%4y4W2M7Y4k6A6j5$3g2K6
Get resources to help with learning malware analysis
7f9K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2&6L8%4g2@1N6h3u0W2i4K6u0W2j5$3!0E0i4K6u0r3M7X3g2V1K9i4u0W2j5%4c8Q4x3@1k6J5k6h3c8A6M7W2)9#2k6Y4c8G2K9$3g2F1i4K6y4p5f1g2g2r3c8V1I4g2K9s2q4S2x3X3c8E0k6g2k6n7g2$3c8C8c8W2N6i4K9X3x3I4g2$3#2@1P5q4g2*7k6s2u0z5c8g2f1@1j5X3A6m8P5X3x3I4f1Y4k6K9x3%4S2n7f1e0y4v1N6r3x3H3N6s2c8K9g2h3c8f1g2f1c8z5d9g2A6B7K9o6g2z5c8%4m8K6h3o6y4G2x3#2q4D9e0Y4y4d9L8r3H3@1h3h3I4h3d9h3y4o6x3h3S2e0g2q4j5@1j5@1c8v1x3#2f1H3y4g2N6W2L8g2k6Z5g2h3E0C8N6#2k6q4K9r3E0f1c8%4m8X3g2f1c8Y4x3#2g2s2M7p5!0e0c8p5&6%4k6h3&6d9f1f1&6C8M7o6m8K9x3U0R3I4g2p5g2H3N6g2q4h3g2V1u0V1x3g2A6t1f1#2M7I4K9#2u0q4N6K6q4i4b7K6q4^5f1@1S2H3K9q4q4f1h3X3q4T1c8r3H3I4j5e0y4d9d9#2N6s2h3e0g2i4c8U0W2o6j5h3I4D9h3q4y4g2K9o6m8V1h3r3c8z5f1#2q4Q4x3U0f1K6c8q4)9J5y4e0y4p5i4K6t1$3j5h3#2H3i4K6y4n7M7g2)9K6c8r3S2@1N6s2m8K6i4K6t1#2x3@1q4Q4x3U0f1J5c8W2)9J5y4e0u0r3j5h3N6V1j5%4y4W2M7Y4k6A6j5$3g2K6i4K6u0W2j5$3!0E0i4K6t1#2x3V1k6T1L8r3!0Y4i4K6t1#2x3V1k6J5k6i4y4G2N6i4u0U0k6i4y4Q4x3X3c8X3L8%4u0Q4x3X3c8D9k6h3q4J5L8X3W2F1k6#2)9J5k6r3#2S2L8s2N6S2M7X3g2Q4x3X3c8S2L8X3q4D9P5i4y4A6M7#2)9J5y4e0u0r3i4K6t1$3j5h3#2H3i4K6y4n7k6i4k6W2L8Y4c8Q4x3@1c8$3K9h3c8W2L8#2)9#2k6X3c8W2M7$3y4J5K9i4m8@1K9h3!0F1i4K6t1$3j5h3#2H3i4K6y4n7N6W2)9K6c8q4)9J5k6p5g2c8d9$3W2u0j5V1!0x3c8h3x3`.
283K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2&6L8%4g2@1N6h3u0W2i4K6u0W2j5$3!0E0i4K6u0r3N6$3q4@1j5$3S2Q4x3@1k6$3i4K6y4p5i4K6u0V1c8g2q4w2K9f1W2T1e0@1I4q4j5#2)9J5y4X3q4E0M7q4)9K6b7X3k6W2j5i4c8#2M7X3g2Q4x3@1c8&6L8%4g2@1N6g2)9J5k6h3u0W2

