-
-
[转帖]SharpEDRChecker
-
发表于: 2021-1-28 05:32 2109
-
SharpEDRChecker
Checks Running Processes, Process Metadata, DLLs Loaded Into Your Current Process And The Each DLLs Metadata, Common Inst all Directories,
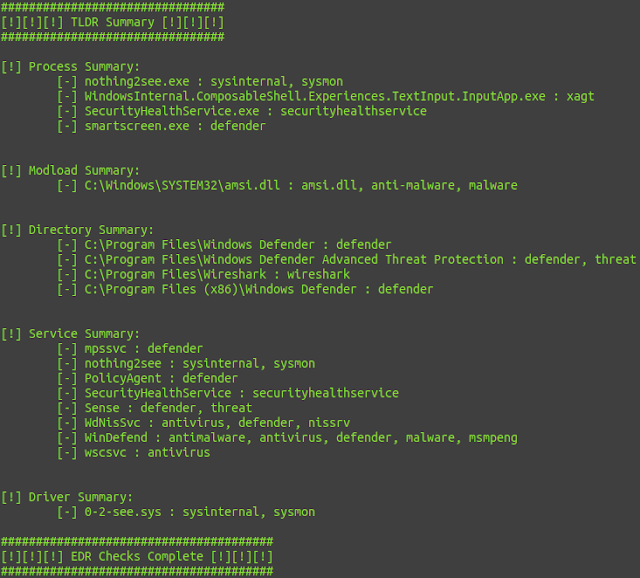
Installed Services And Each Service Binaries Metadata, Installed Drivers And Each Drivers Metadata, All For The Presence Of Known Defensive Products Such As AV's, EDR's And Logging Tools
New and improved C# Implementation of Invoke-EDRChecker. Checks running processes, process metadata, Dlls loaded into your current process and each DLLs metadata, common install directories, installed services and each service binaries metadata, installed drivers and each drivers metadata, all for the presence of known defensive products such as AV's, EDR's and logging tools. Catches hidden EDRs as well via its metadata checks, more info in a blog post coming soon.
This binary can be loaded into your C2 server by loading the module then running it. Note: this binary is now included in PoshC2 so no need to manually add it.
03cK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2C8K9i4c8H3L8r3!0A6N6q4)9J5k6h3y4G2L8g2)9J5c8U0t1H3x3U0q4Q4x3V1j5H3x3g2)9J5c8Y4y4Z5j5i4u0H3k6h3c8J5j5$3S2W2j5$3E0W2M7W2)9J5k6r3y4Z5k6h3y4C8M7#2)9J5k6s2u0#2L8X3&6A6L8X3N6Q4x3X3g2Z5N6r3#2D9

