-
-
[原创]RCTF bloker_vm 侧信道爆破解法
-
发表于: 2024-6-14 19:56 2552
-
看了https://bbs.kanxue.com/thread-281796.htm#msg_header_h3_8 想着找题练练手QAQ
通过字符串可以找到主逻辑 程序有反调试 但是在主逻辑里没看着 用ida attach 即可起调试
通过对比输入与最终的字符串可以确定是单字节加密
校验逻辑应该在这
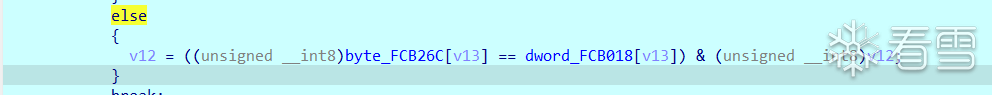
尝试使用侧信道爆破
但是这里是用侧信道爆破发现结果都是相同的 尝试patch二进制文件让其能够泄露一定的信息
如果校验发现不相同则直接让他跳出循环


脚本如下:
js脚本如下:
运行结果如下
的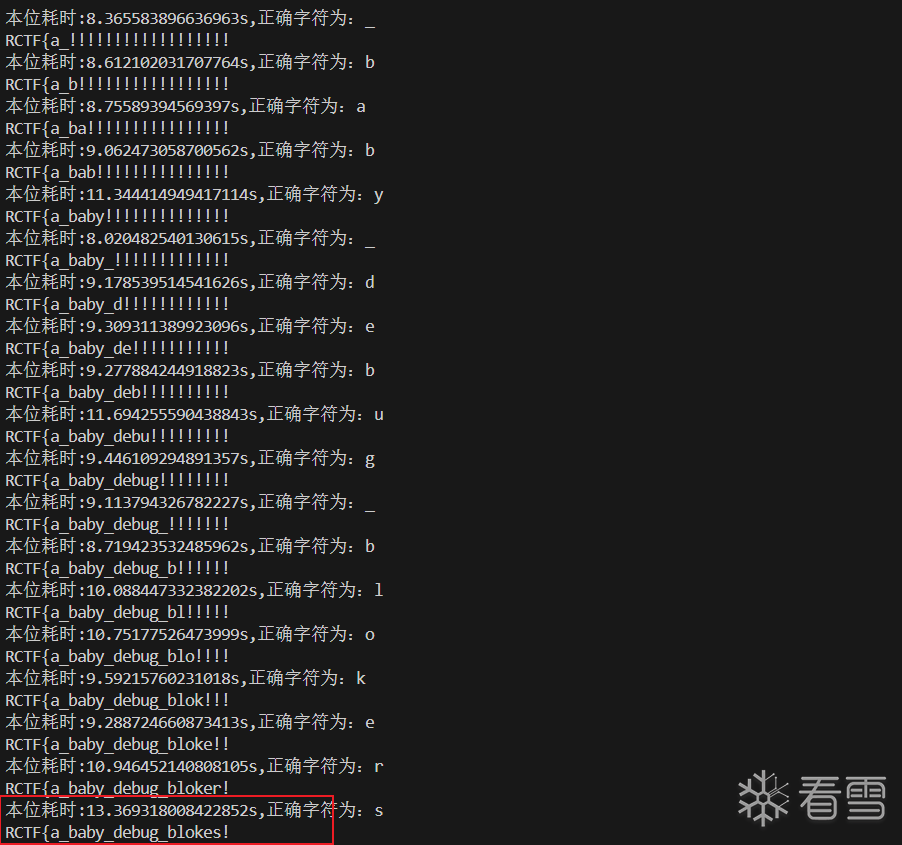
最终flag:RCTF{a_baby_debug_blokes}
import subprocessimport fridaimport sysimport win32apiimport win32con number = 0flaglen = 43filename = "bloker_vm.exe"# flag{O1SC_VM_1s_h4rd_to_r3v3rs3_#a78abffaa#}flag = bytearray(b'!'*25)jscode = open("blockvm.js", "rb").read().decode()new_number = 0 result = 0def brute(F): def on_message(message, data): global result if message['type'] == 'send': result = message['payload'] # print(result) else: print(message) process = subprocess.Popen(filename, stdin=subprocess.PIPE, stdout=subprocess.PIPE, stderr=subprocess.PIPE, universal_newlines=True) session = frida.attach(filename) script = session.create_script(jscode) script.on('message', on_message) script.load() process.stdin.write(F.decode()) #print(F.decode()) output, error = process.communicate() #print(output,error) #print(f"number:{result}") process.terminate() return resultimport time count = 0 new_number = brute(flag)number = new_numbert = time.time()st = t while count < flaglen: number = brute(flag) # print(flag.decode()) if number != new_number: print(f"本位耗时:{time.time()-t}s,正确字符为:{chr(flag[count])}") t = time.time() print(flag.decode()) new_number = number count += 1 else: flag[count] += 1 while(flag[count] > 127): flag[count] = 33 count -= 1 flag[count] += 1print(flag.decode())print(f"总耗时{time.time()-st}")import subprocessimport fridaimport sysimport win32apiimport win32con number = 0flaglen = 43filename = "bloker_vm.exe"# flag{O1SC_VM_1s_h4rd_to_r3v3rs3_#a78abffaa#}flag = bytearray(b'!'*25)jscode = open("blockvm.js", "rb").read().decode()new_number = 0 result = 0def brute(F): def on_message(message, data): global result if message['type'] == 'send': result = message['payload'] # print(result) else: print(message) process = subprocess.Popen(filename, stdin=subprocess.PIPE, stdout=subprocess.PIPE, stderr=subprocess.PIPE, universal_newlines=True) session = frida.attach(filename) script = session.create_script(jscode) script.on('message', on_message) script.load() process.stdin.write(F.decode()) #print(F.decode()) output, error = process.communicate() #print(output,error) #print(f"number:{result}") process.terminate() return result赞赏
他的文章
- [原创] LLVM NEW PASS Learning Notes 4672
- [原创]Branch2Call 一种基于LLVM的混淆 9293
- [原创]强网杯MINIRE 12919
- [原创]第七届强网拟态RE WP 14087
- [原创] 2 1640
赞赏
雪币:
留言:

