-
-
[原创]非常规破解网络验证
-
发表于:
2013-10-8 15:26
3680
-
原文来自Tracy'Blog——
75eK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4m8#2M7Y4m8D9k6i4u0G2j5#2)9J5k6h3y4G2L8b7`.`.
上网时,突然有人找我说要破解一软件,看了下,是俊亚的一款收费软件。
用OD跟踪了个把小时,没有实质性的进展,不过,也大概知道了验证的思路,改了些地方,想暴力破解掉,可发现没那么简单,于是,暂时休息休息。知道它用的是网络验证,那么,服务端在哪呢?
换工具,对程序抓包,找到url(
43eK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4S2^5P5s2S2^5i4K6u0W2k6Y4y4B7P5i4u0B7i4K6u0W2j5$3!0E0i4K6u0r3k6$3c8&6i4K6u0r3K9r3I4V1i4K6g2X3M7i4g2W2M7Y4W2Q4x3X3g2S2M7%4m8Q4c8f1k6Q4b7V1y4Q4z5o6W2Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5p5g2Q4b7V1u0Q4c8e0N6Q4z5f1y4Q4z5p5u0Q4c8e0c8Q4b7V1q4Q4z5o6k6Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4x3V1y4Q4c8e0S2Q4b7V1k6Q4z5e0c8Q4c8e0g2Q4z5f1u0Q4z5f1g2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4z5e0S2Q4b7f1k6Q4c8e0c8Q4b7U0S2Q4z5o6m8Q4c8e0g2Q4b7e0c8Q4b7e0N6Q4c8e0g2Q4b7e0m8Q4z5o6k6Q4c8e0N6Q4b7V1u0Q4z5o6c8Q4c8e0g2Q4z5e0m8Q4z5o6S2Q4c8e0k6Q4z5e0g2Q4b7U0m8Q4c8e0g2Q4b7f1c8Q4z5e0N6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7U0W2Q4z5f1k6Q4c8e0g2Q4b7U0m8Q4b7U0q4Q4c8e0k6Q4z5e0S2Q4b7f1k6Q4c8e0S2Q4b7f1k6Q4b7U0c8Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0N6Q4b7e0S2Q4z5p5u0Q4c8e0g2Q4b7V1q4Q4z5p5k6Q4c8e0W2Q4z5f1y4Q4z5o6m8Q4c8e0S2Q4b7e0k6Q4z5o6q4Q4c8e0S2Q4b7e0N6Q4b7e0y4Q4c8e0g2Q4b7f1k6Q4z5o6k6Q4c8e0S2Q4b7V1k6Q4z5e0W2Q4c8e0c8Q4b7U0S2Q4b7f1q4Q4c8e0S2Q4b7V1k6Q4z5e0c8Q4c8e0g2Q4z5f1u0Q4z5f1g2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4z5e0g2Q4b7U0m8Q4c8e0k6Q4z5p5c8Q4b7f1g2Q4c8e0k6Q4z5f1c8Q4b7e0g2Q4c8e0S2Q4b7V1k6Q4z5f1u0Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0g2Q4z5o6S2Q4b7e0c8Q4c8e0k6Q4z5e0k6Q4b7f1c8Q4c8e0c8Q4b7V1u0Q4z5p5g2Q4c8e0S2Q4z5o6m8Q4z5p5y4Q4c8e0W2Q4b7f1q4Q4z5p5y4Q4c8e0S2Q4b7f1k6Q4z5o6q4Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0g2Q4z5p5k6Q4b7e0k6Q4c8e0g2Q4b7e0c8Q4z5e0k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5f1y4Q4b7e0S2Q4c8e0k6Q4b7U0y4Q4b7e0S2Q4c8e0g2Q4z5o6k6Q4z5p5y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8e0W2Q4z5e0c8Q4z5e0W2Q4c8e0S2Q4b7f1k6Q4b7f1k6Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4z5e0N6Q4b7U0k6Q4c8e0g2Q4z5o6m8Q4z5e0W2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7V1y4Q4b7U0W2Q4c8e0g2Q4z5o6N6Q4b7V1q4Q4c8e0g2Q4b7e0k6Q4z5o6u0Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0g2Q4b7f1k6Q4b7U0W2Q4c8e0S2Q4b7f1k6Q4z5f1c8Q4c8e0k6Q4b7e0q4Q4z5o6k6Q4c8e0y4Q4z5o6m8Q4z5o6t1`.
可在程序中是没有这些个字符的,开始猜测可能是以unicode存放在程序中的,可看到那一大堆组合的数字之后,觉得,返回的这些个信息应该也是从服务端传递过来的。于是再用OD下recvfrom断点,跟踪了一下,证实了我的猜想。
回头看看那个url,一级级的目录进行浏览,结果发现,
07cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4S2^5P5s2S2^5i4K6u0W2k6Y4y4B7P5i4u0B7i4K6u0W2j5$3!0E0i4K6u0r3k6$3c8&6i4@1f1%4i4K6W2n7i4@1t1@1i4@1f1$3i4K6S2q4i4@1p5#2i4@1f1#2i4@1u0o6i4@1t1&6i4@1f1#2i4K6R3%4i4@1u0m8i4@1f1%4i4@1u0p5i4K6V1I4i4@1f1%4i4@1q4n7i4K6V1&6i4@1f1#2i4K6V1H3i4K6S2q4i4@1f1#2i4K6S2r3i4@1t1H3i4@1f1%4i4K6V1&6i4@1u0n7i4@1f1&6i4K6V1&6i4K6R3$3i4@1f1%4i4K6V1#2i4K6S2o6i4@1f1&6i4K6W2p5i4@1p5J5i4@1f1@1i4@1u0m8i4K6R3$3i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1%4i4K6R3@1i4@1t1$3i4@1f1#2i4K6V1H3i4K6S2q4i4@1f1#2i4K6R3$3i4K6S2p5i4@1f1$3i4K6R3&6i4K6V1K6i4@1f1#2i4@1u0o6i4K6R3H3K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4S2^5P5s2S2^5i4K6u0W2k6Y4y4B7P5i4u0B7i4K6u0W2j5$3!0E0i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1%4i4K6W2o6i4K6S2n7i4@1f1#2i4K6R3^5i4@1t1H3i4@1f1@1i4@1t1^5i4K6R3H3i4@1f1@1i4@1t1^5i4@1q4m8i4@1f1^5i4@1q4q4i4@1u0q4i4@1f1^5i4@1q4q4i4@1p5I4i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1$3i4K6S2o6i4@1u0m8i4@1f1%4i4@1t1J5i4@1u0q4i4@1f1%4i4@1u0q4i4K6S2q4i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1%4i4@1u0p5i4K6V1I4i4@1f1%4i4@1q4n7i4K6V1&6i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1@1i4@1t1^5i4K6S2p5i4@1f1^5i4@1u0r3i4K6R3%4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1@1i4@1t1^5i4K6R3H3i4@1f1%4i4K6W2o6i4K6S2n7i4@1f1#2i4@1t1H3i4@1t1I4i4@1f1%4i4K6W2r3i4@1p5#2i4@1f1&6i4K6R3I4i4K6V1K6i4@1f1$3i4K6V1^5i4@1q4r3i4@1f1@1i4@1t1^5i4@1q4m8i4@1f1#2i4@1t1I4i4K6V1#2i4@1f1%4i4@1p5@1i4@1u0m8i4@1f1&6i4@1p5I4i4@1t1#2i4@1f1&6i4K6W2p5i4@1p5J5i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4@1t1&6i4@1t1$3i4@1f1$3i4@1t1J5i4@1p5I4i4@1f1$3i4K6W2o6i4K6R3&6i4@1f1@1i4@1u0n7i4@1u0n7i4@1f1@1i4@1u0p5i4K6V1#2i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1#2i4@1q4q4i4K6W2q4i4@1f1^5i4@1t1@1i4@1p5^5i4@1f1$3i4K6R3H3i4@1p5%4i4@1f1#2i4K6R3$3i4K6R3#2i4@1f1#2i4@1q4q4i4@1t1&6i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1@1i4@1t1&6i4K6W2r3i4@1f1#2i4@1t1H3i4@1t1I4i4@1f1$3i4K6V1^5i4@1q4r3i4@1f1^5i4@1q4r3i4@1t1@1i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1%4i4K6V1@1i4@1p5^5i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1$3i4K6V1^5i4@1q4r3i4@1f1@1i4@1t1^5i4K6R3H3i4@1f1@1i4@1t1^5i4@1q4m8i4@1f1^5i4@1t1%4i4K6W2r3i4@1f1^5i4K6R3%4i4@1q4m8i4@1f1#2i4@1t1%4i4@1t1I4i4@1f1^5i4@1u0p5i4@1q4r3i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1&6i4@1q4m8i4K6S2o6i4@1f1^5i4@1q4r3i4K6R3I4i4@1f1$3i4@1q4r3i4@1q4n7i4@1f1$3i4K6V1%4i4@1p5H3i4@1f1#2i4K6R3#2i4@1t1K6i4@1f1%4i4@1t1K6i4@1u0n7i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1%4i4@1u0p5i4K6V1I4i4@1f1%4i4@1q4n7i4K6V1&6i4@1f1@1i4@1u0p5i4K6W2o6i4@1f1@1i4@1t1^5i4@1u0m8i4@1f1$3i4K6V1^5i4@1u0q4i4@1f1%4i4@1p5@1i4@1u0m8i4@1f1K6i4K6R3H3i4K6R3J5
回到登陆界面,

找到的唯一有用的信息是“梦幻账号管理系统”,百度谷歌一番,没任何收获,于是,回到那个设计精美的页面,找到一些关键词,搜了下,把源代码下下来,结果发现,整个网站,就只有几个html页面。于是,从网站端下手,有点困难了。就先放放吧。改天再看。
第二天再次打开网址,发现页面换了,页面换了也就是说换了一套展示的系统。看了下,是网趣网上购物系统。于是立马网上down下源代码。心想才放上去的网站,肯定登陆用户名密码都没改的,网站后接admin,用默认的admin/admin,直接就进去了。
然后,破解的思路就是:拿下网站,找到验证的asp程序,改掉,在本地搭建服务器,本地hosts文件中添加一条记录,使网站指向127.0.0.1。
于是,提权吧。后台转悠了半天,没发现啥可用的,于是,来分析下几个上传文件的地方的源代码。
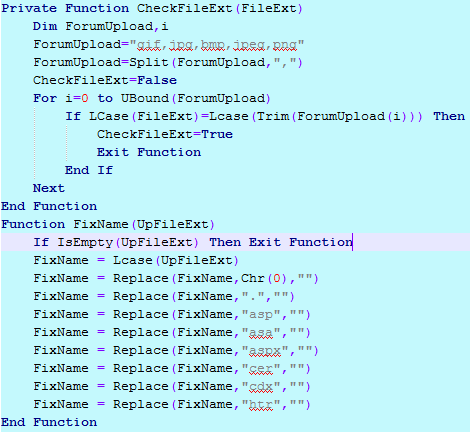
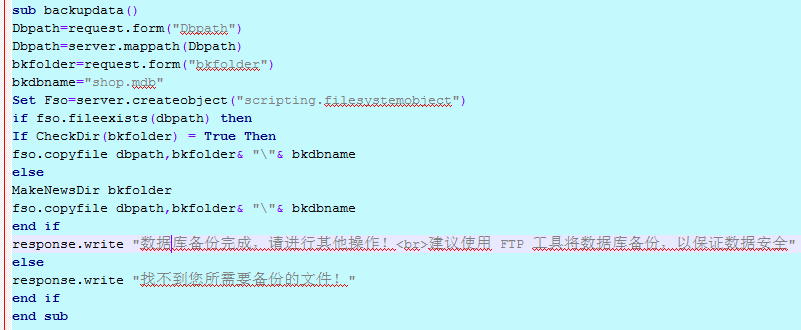
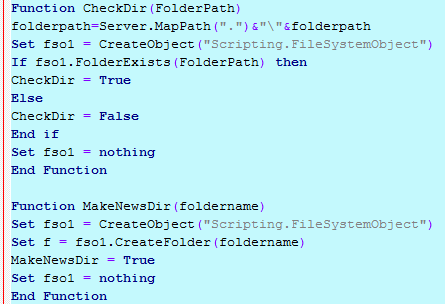
可以看出,只允许上传几种常见的图片文件,而如果发现了asp等网页文件后缀的字符串,则直接清除掉再存放文件。于是,试了下构造特定的asaspp等后缀上传,结果发现还是不能直接上传webshell。
后来,想了下一些博客,常用的都有一个database备份的页面,而且,不会放在菜单栏上。于是,找了找,发现,这套系统也有一个backdata.asp的文件。
直接访问,发现能够实现对特定的文件进行备份。
可以看出,我们把webshell改成jpg的后缀,上传得到返回地址,而后再用这个备份功能,把文件备份为asp格式,就可以得到我们的webshell了。
可是,我们做完这一些之后访问url得到一个404错误。那,问题在哪呢?
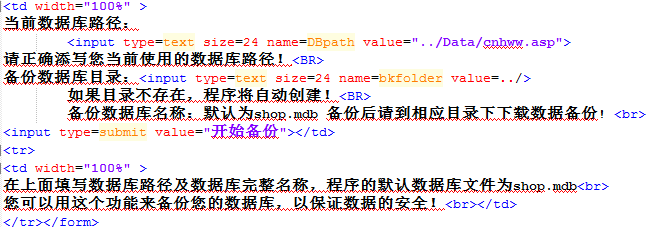
哦,从这里可以看出我们输入的文件名,不是文件名,而是一个文件夹名。而我们要备份的那个jpg文件,会保存到我们输入的文件夹名下的shop.mdb。
瞬间,想到的就是iis的解析漏洞,输入1.asp作为文件夹,然后访问:xxxx.xxxx.com/1.asp/shop.mdb。能够直接把shop.mdb中的内容以asp格式访问。
就这样,小马可以使用了,再把大马放上去~~~
行,就写到这把,好几个月前的事了,只是一个思路的记录。也没环境去截那么多图了。
[培训]科锐逆向工程师培训第53期2025年7月8日开班!