-
-
[原创][分享]为记事本添加置顶/透明/打开HOSTS文件功能
-
发表于:
2014-7-25 16:42
7973
-
[原创][分享]为记事本添加置顶/透明/打开HOSTS文件功能
本人菜鸟,今天闲来无事,很久没发文章了,论坛的学业已经荒废,重新来练习下,不对之处请谅解,欢迎提出好的建议。
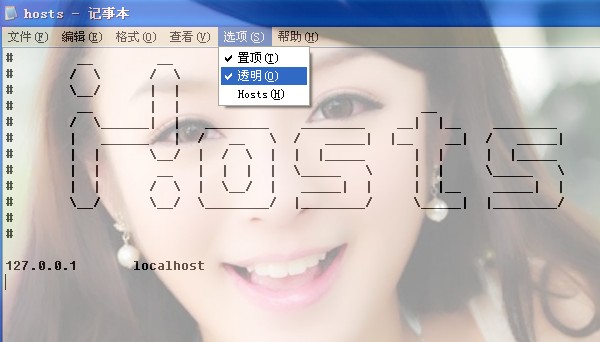
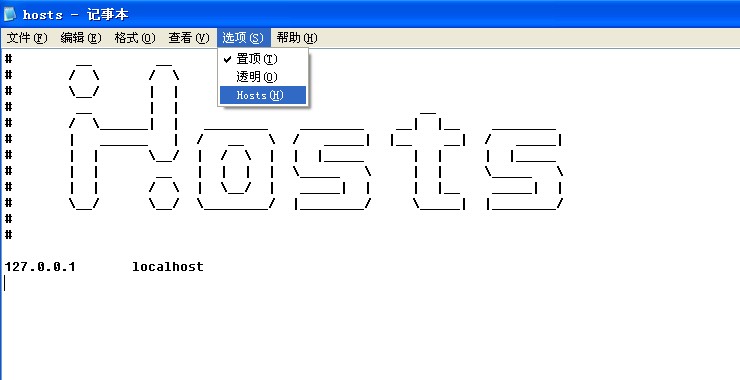
为记事本添加 /置顶/透明/Hosts/ 功能
源文件:WINXP 记事本 NotePad.exe
要实现我们的功能需要一些函数,SetWindowPos、SetLayeredWindowAttributes、GetSystemDirectoryW
经过查看模块调用发现没有这三个函数,发现有GetModuleHandle、GetProcAddress这两个函数,
有了他们事情就好办了;免得我们去增加需要的函数,其他用到的函数如下:
GetWindowLongW、SetWindowLongW、GetMenu、GetSubMenu、CheckMenuItem、CreateFileW、lstrcatw
CALL DWORD PTR DS:[0x10010CC] ;GetModuleHandle
CALL DWORD PTR DS:[0x1001110] ;GetProcAddress
CALL DWORD PTR DS:[0x1001264] ;GetMenu
CALL DWORD PTR DS:[0x1001260] ;GetSubMenu
CALL DWORD PTR DS:[0x1001248] ;CheckMenuItem
CALL DWORD PTR DS:[0x1001270] ;GetWindowLongW
CALL DWORD PTR DS:[0x100126C] ;SetWindowLongW
CALL DWORD PTR DS:[0x1001104] ;CreateFileW
CALL DWORD PTR DS:[0x1001118] ;lstrcatw
第一步:先给程序增加菜单
用资源编辑器打开文件,增加菜单项,置顶 - 118 、透明 - 119 、Hosts - 120
第二步:查找消息处理地址
用OD加载记事本,查询所有模块间的调用,找到RegisterClassExW F2下断,F9运行程序程序会断下.
01004550 |. FF15 D0110001 CALL DWORD PTR DS:[<&USER32.RegisterClas>; \RegisterClassExW
看堆栈框如下:
0007FDE8 0006FDF0 \pWndClassEx = 0007FDF0 ;注册窗口类的结构定义,在堆栈中中查看
0007FDEC 77D19D69 user32.LoadCursorW
0007FDF0 00000030
0007FDF4 00000000
0007FDF8 01003429 NotePad_.01003429 ;窗口过程地址 //右键 反汇编窗口跟随 来到过程入口
0007FDFC 00000000
0007FE00 00000000
0007FE04 01000000 NotePad_.01000000 ;所属实例
0007FE08 052807AB
0007FE0C 00010013
0007FE10 00000006
0007FE14 00000001
0007FE18 01009020 UNICODE "Notepad"
来到过程入口,我们下翻来到WM_COMMAND消息分支:
010038C7 |> \3B3D 38980001 CMP EDI,DWORD PTR DS:[0x1009838] ; Case 111 (WM_COMMAND) of switch 01003434
010038CD |. 75 4C JNZ SHORT NotePad.0100391B
…………………………………………省略……………………………………………………
01003916 |.^ E9 A2FBFFFF JMP NotePad.010034BD
0100391B |> 57 PUSH EDI
0100391C |. FF75 10 PUSH [ARG.3]
0100391F |. FF75 08 PUSH [ARG.1]
01003922 |. E8 60F2FFFF CALL NotePad.01002B87 ;// 进入此过程 - 判断菜单消息
进入过程后,来到10032C6这里是菜单 关于 的判断地方。0x41 = 65 菜单关于的ID=65,我们加入远程跳转跳至自己的代码处,
需要5个字节,修改010032C6这里,修改会覆盖5字节记下源代码以备还原;
010032C6 |> \83FF 41 CMP EDI,0x41 ;// 改为 JMP 01013053
010032C9 |. 74 76 JE SHORT NotePad.01003341
第三步:找空白空间存放自己的常量字符串代码,代码段的后边有空白地址,我们把代码放到01008748处,修改如下:
01008748 . 53 65 74 57 6>ASCII "SetWindowPos",0
01008755 00 DB 00
01008756 . 53 65 74 4C 6>ASCII "SetLayeredWindow"
01008766 . 41 74 74 72 6>ASCII "Attributes",0
01008771 00 DB 00
01008772 . 47 65 74 53 7>ASCII "GetSystemDirecto"
01008782 . 72 79 57 00 ASCII "ryW",0
01008786 00 DB 00
01008787 . 5C00 6400 720>UNICODE "\drivers"
01008797 . 5C00 6500 740>UNICODE "\etc\hos"
010087A7 . 7400 7300 000>UNICODE "ts",0
改完后保存下。
第四步:增加资源段大小,我们的代码需要1C0H的空间,我们增加200H就够了,用16进制工具在文件尾
增加200H的空间;然后修改.rsrc段的虚拟和物理大小,各增加200H,最后修改段属性为可执行。
第五步:增加我们的代码;
CTRL+G来到1013000处,即我们自己加的空间。写上如下代码:
01013000 55 PUSH EBP
01013001 8BEC MOV EBP,ESP
01013003 FF75 0C PUSH DWORD PTR SS:[EBP+0xC]
01013006 FF15 CC100001 CALL DWORD PTR DS:[<&KERNEL32.GetModuleH>; kernel32.GetModuleHandleA
0101300C FF75 08 PUSH DWORD PTR SS:[EBP+0x8]
0101300F 50 PUSH EAX
01013010 FF15 10110001 CALL DWORD PTR DS:[<&KERNEL32.GetProcAdd>; kernel32.GetProcAddress
01013016 C9 LEAVE
01013017 C2 0800 RETN 0x8
0101301A 90 NOP
0101301B 90 NOP
0101301C 90 NOP
0101301D 90 NOP
0101301E 90 NOP
0101301F 55 PUSH EBP
01013020 8BEC MOV EBP,ESP
01013022 FF35 30980001 PUSH DWORD PTR DS:[0x1009830]
01013028 FF15 64120001 CALL DWORD PTR DS:[<&USER32.GetMenu>] ; user32.GetMenu
0101302E 6A 04 PUSH 0x4
01013030 50 PUSH EAX
01013031 FF15 60120001 CALL DWORD PTR DS:[<&USER32.GetSubMenu>] ; user32.GetSubMenu
01013037 3E:837D 0C 00 CMP DWORD PTR DS:[EBP+0xC],0x0
0101303C 74 04 JE SHORT 1116.01013042
0101303E 6A 08 PUSH 0x8
01013040 EB 02 JMP SHORT 1116.01013044
01013042 6A 00 PUSH 0x0
01013044 FF75 08 PUSH DWORD PTR SS:[EBP+0x8]
01013047 50 PUSH EAX
01013048 FF15 48120001 CALL DWORD PTR DS:[<&USER32.CheckMenuIte>; user32.CheckMenuItem
0101304E C9 LEAVE
0101304F C2 0800 RETN 0x8
01013052 90 NOP
01013053 60 PUSHAD
01013054 E8 0F000000 CALL 1116.01013068
01013059 61 POPAD
0101305A 83FF 41 CMP EDI,0x41
0101305D - 0F84 DE02FFFF JE 1116.01003341
01013063 - E9 6302FFFF JMP 1116.010032CB
01013068 83FF 76 CMP EDI,0x76
0101306B 74 11 JE SHORT 1116.0101307E
0101306D 83FF 77 CMP EDI,0x77
01013070 74 5F JE SHORT 1116.010130D1
01013072 83FF 78 CMP EDI,0x78
01013075 0F84 D4000000 JE 1116.0101314F
0101307B C3 RETN
0101307C 90 NOP
0101307D 90 NOP
0101307E 68 3C870001 PUSH 1116.0100873C ; ASCII "USER32.dll"
01013083 68 48870001 PUSH 1116.01008748 ; ASCII "SetWindowPos"
01013088 E8 73FFFFFF CALL 1116.01013000
0101308D 6A 13 PUSH 0x13
0101308F 6A 00 PUSH 0x0
01013091 6A 00 PUSH 0x0
01013093 6A 00 PUSH 0x0
01013095 6A 00 PUSH 0x0
01013097 833D 2C980001 0>CMP DWORD PTR DS:[0x100982C],0x0
0101309E 74 0E JE SHORT 1116.010130AE
010130A0 C705 2C980001 0>MOV DWORD PTR DS:[0x100982C],0x0
010130AA 6A FE PUSH -0x2
010130AC EB 0C JMP SHORT 1116.010130BA
010130AE C705 2C980001 0>MOV DWORD PTR DS:[0x100982C],0x1
010130B8 6A FF PUSH -0x1
010130BA FF35 30980001 PUSH DWORD PTR DS:[0x1009830]
010130C0 FFD0 CALL EAX
010130C2 FF35 2C980001 PUSH DWORD PTR DS:[0x100982C]
010130C8 6A 76 PUSH 0x76
010130CA E8 50FFFFFF CALL 1116.0101301F
010130CF C3 RETN
010130D0 90 NOP
010130D1 6A EC PUSH -0x14
010130D3 FF35 30980001 PUSH DWORD PTR DS:[0x1009830]
010130D9 FF15 70120001 CALL DWORD PTR DS:[<&USER32.GetWindowLon>; user32.GetWindowLongW
010130DF 833D 28980001 0>CMP DWORD PTR DS:[0x1009828],0x0
010130E6 74 11 JE SHORT 1116.010130F9
010130E8 C705 28980001 0>MOV DWORD PTR DS:[0x1009828],0x0
010130F2 25 FFFFF7FF AND EAX,0xFFF7FFFF
010130F7 EB 0F JMP SHORT 1116.01013108
010130F9 C705 28980001 0>MOV DWORD PTR DS:[0x1009828],0x1
01013103 0D 00000800 OR EAX,0x80000
01013108 50 PUSH EAX
01013109 6A EC PUSH -0x14
0101310B FF35 30980001 PUSH DWORD PTR DS:[0x1009830]
01013111 FF15 6C120001 CALL DWORD PTR DS:[<&USER32.SetWindowLon>; user32.SetWindowLongW
01013117 833D 28980001 0>CMP DWORD PTR DS:[0x1009828],0x0
0101311E 74 20 JE SHORT 1116.01013140
01013120 68 3C870001 PUSH 1116.0100873C ; ASCII "USER32.dll"
01013125 68 56870001 PUSH 1116.01008756 ; ASCII "SetLayeredWindowAttributes"
0101312A E8 D1FEFFFF CALL 1116.01013000
0101312F 6A 02 PUSH 0x2
01013131 68 96000000 PUSH 0x96
01013136 6A 00 PUSH 0x0
01013138 FF35 30980001 PUSH DWORD PTR DS:[0x1009830]
0101313E FFD0 CALL EAX
01013140 FF35 28980001 PUSH DWORD PTR DS:[0x1009828]
01013146 6A 77 PUSH 0x77
01013148 E8 D2FEFFFF CALL 1116.0101301F
0101314D C3 RETN
0101314E 90 NOP
0101314F 68 EC800001 PUSH 1116.010080EC ; ASCII "KERNEL32.dll"
01013154 68 72870001 PUSH 1116.01008772 ; ASCII "GetSystemDirectoryW"
01013159 E8 A2FEFFFF CALL 1116.01013000
0101315E 68 00010000 PUSH 0x100
01013163 68 00950001 PUSH 1116.01009500
01013168 FFD0 CALL EAX
0101316A 68 87870001 PUSH 1116.01008787 ; UNICODE "\drivers\etc\hosts"
0101316F 68 00950001 PUSH 1116.01009500
01013174 FF15 18110001 CALL DWORD PTR DS:[<&KERNEL32.lstrcatW>] ; kernel32.lstrcatW
0101317A 6A 00 PUSH 0x0
0101317C 68 80000000 PUSH 0x80
01013181 6A 03 PUSH 0x3
01013183 6A 00 PUSH 0x0
01013185 6A 03 PUSH 0x3
01013187 68 00000080 PUSH 0x80000000
0101318C 68 00950001 PUSH 1116.01009500
01013191 FF15 04110001 CALL DWORD PTR DS:[<&KERNEL32.CreateFile>; kernel32.CreateFileW
01013197 FF35 30900001 PUSH DWORD PTR DS:[0x1009030]
0101319D A3 80A40001 MOV DWORD PTR DS:[0x100A480],EAX
010131A2 68 00950001 PUSH 1116.01009500
010131A7 E8 CD1FFFFF CALL 1116.01005179
010131AC - E9 16FCFEFF JMP 1116.01002DC7
010131B1 90 NOP
改完后保存,就可以测试程序了。
文件下载 NotePad_diy.rar
NotePad_diy.rar
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课