-
-
BTS Pentesting Lab XSS 分析(1)
-
发表于: 2014-9-4 17:02 2255
-
跨站脚本攻击漏洞分析
一、环境准备
1)XAMPP安装
2)下载BTS lab btslab.zip,BTS pentesting lab 包解压缩,放置于~\xampp\htdocs文件夹内
3)在xampp中启动apache,访问2bcK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4G2j5$3q4D9K9r3!0K6N6q4)9J5c8X3u0@1M7$3I4S2j5W2)9J5c8Y4y4W2N6s2g2H3i4K6u0W2M7r3S2H3
二、XSS分析
1)reflected xss 1 分析
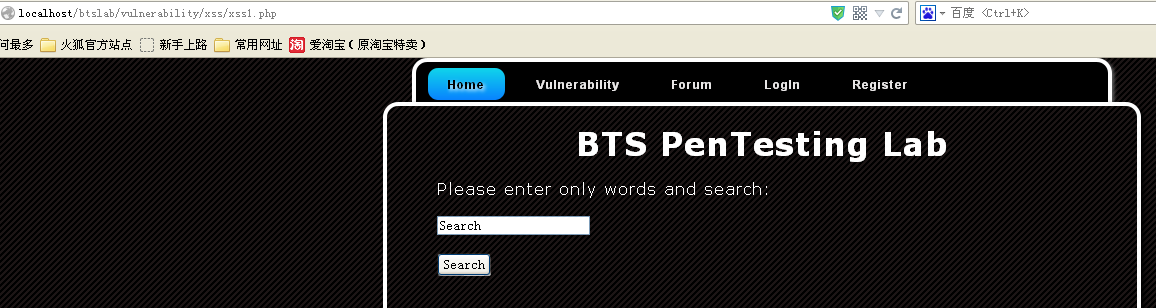
一个搜索框,那试试<script>alert(1)</script> ,ok,弹框
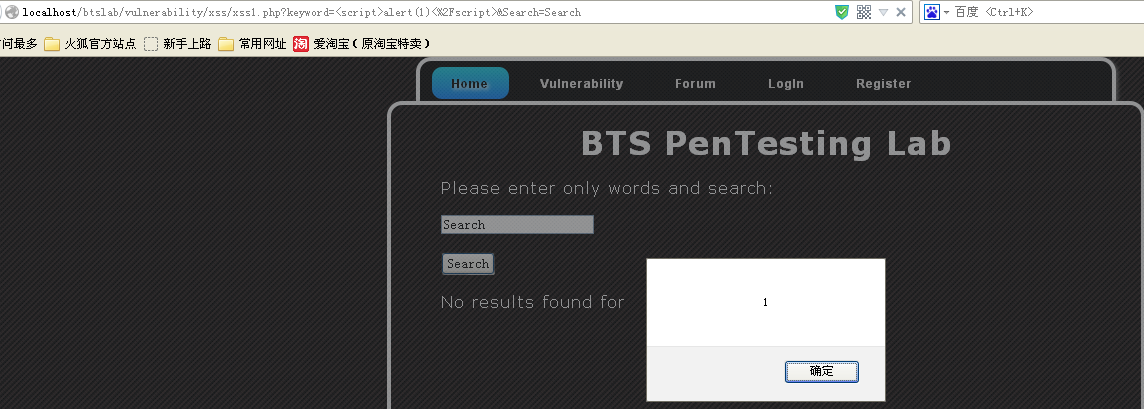
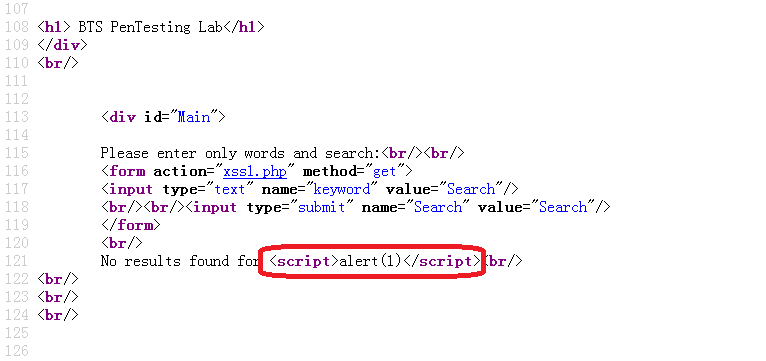
查看源代码,发现输入的搜索内容,没有转码直接显示:
2)reflected xss 2分析
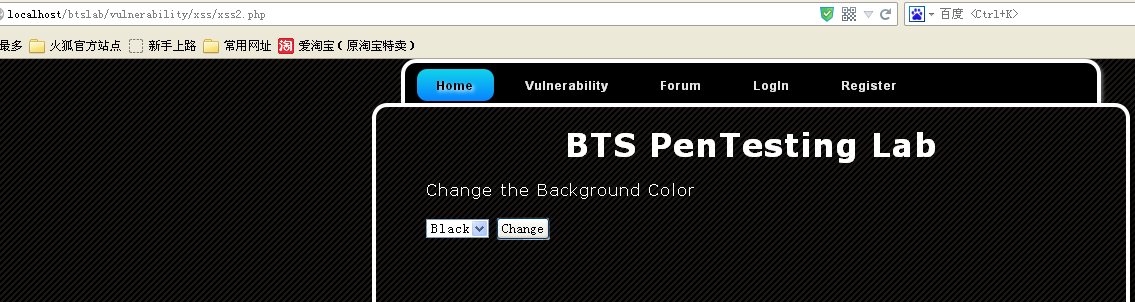
一个选择框,是不是可以修改提交的选择框的内容,导致xss呢?
随便选择一个看看是GET方式提交选择框内容还是POST?(GET可以在地址栏修改,POST就借助Live HTTP header插件),ok,GET方式提交:562K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4G2j5$3q4D9K9r3!0K6N6q4)9J5c8X3u0@1M7$3I4S2j5W2)9J5c8Y4k6#2L8r3&6W2M7X3q4T1K9h3I4A6N6s2W2Q4x3V1k6^5M7%4y4Q4x3V1k6^5M7%4x3J5i4K6u0W2M7r3S2H3i4K6y4r3j5$3I4J5i4K6y4p5%23000&Change=Change。
先试试<script>alert(1)</script>看有啥反应?提交290K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4G2j5$3q4D9K9r3!0K6N6q4)9J5c8X3u0@1M7$3I4S2j5W2)9J5c8Y4k6#2L8r3&6W2M7X3q4T1K9h3I4A6N6s2W2Q4x3V1k6^5M7%4y4Q4x3V1k6^5M7%4x3J5i4K6u0W2M7r3S2H3i4K6y4r3j5$3I4J5i4K6y4p5<script>alert(1)</script>&Change=Change,没啥反应,查看下源代码:
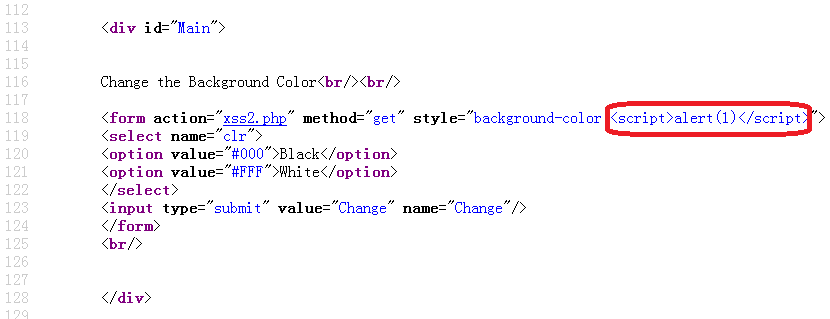
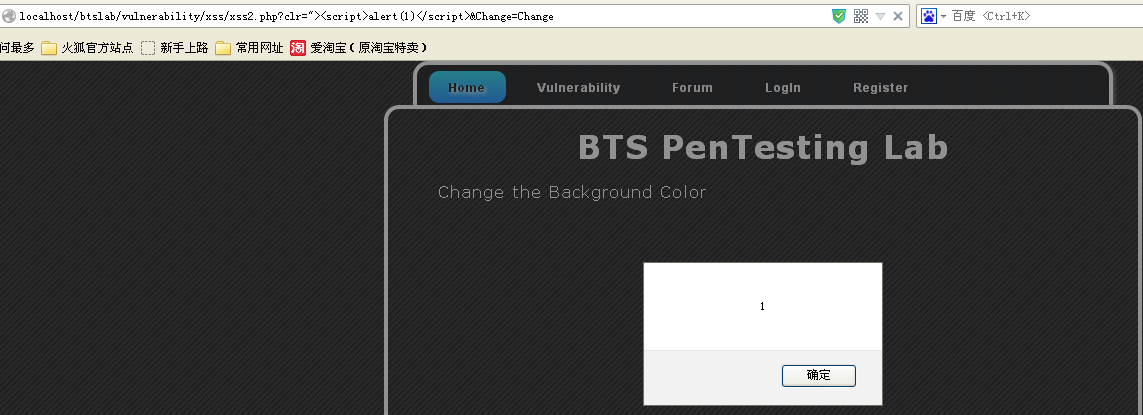
没有转码写入style属性中,那闭合双引号会成啥样?提交1faK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4G2j5$3q4D9K9r3!0K6N6q4)9J5c8X3u0@1M7$3I4S2j5W2)9J5c8Y4k6#2L8r3&6W2M7X3q4T1K9h3I4A6N6s2W2Q4x3V1k6^5M7%4y4Q4x3V1k6^5M7%4x3J5i4K6u0W2M7r3S2H3i4K6y4r3j5$3I4J5i4K6y4p5”><script>alert(1)</script>&Change=Change,弹出框
3)reflected xss 3分析
又是一个搜索框,那再按照1)中的试试,发现没有弹框,看看源码发现进行了转码,分别试试单引号,双引号,<,>等发现都转码了,貌似搜索框不好使,那咋办![]() ,仔细看看发现chanlenge3颜色不同,貌似有链接存在,点击发现地址栏中出现:829K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4G2j5$3q4D9K9r3!0K6N6q4)9J5c8X3u0@1M7$3I4S2j5W2)9J5c8Y4k6#2L8r3&6W2M7X3q4T1K9h3I4A6N6s2W2Q4x3V1k6^5M7%4y4Q4x3V1k6^5M7%4x3K6i4K6u0W2M7r3S2H3i4K6y4r3N6q4)9K6c8s2c8A6N6r3I4W2 ,这个地址可能存在xss,试试?修改为:254K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4G2j5$3q4D9K9r3!0K6N6q4)9J5c8X3u0@1M7$3I4S2j5W2)9J5c8Y4k6#2L8r3&6W2M7X3q4T1K9h3I4A6N6s2W2Q4x3V1k6^5M7%4y4Q4x3V1k6^5M7%4x3K6i4K6u0W2M7r3S2H3i4K6y4r3N6q4)9K6c8q4)9J5y4X3I4@1i4K6y4n7M7$3y4J5K9i4m8@1i4K6t1$3k6%4c8Q4x3@1u0S2L8r3g2J5N6q4)9J5z5o6q4Q4x3U0W2Q4x3U0k6D9N6q4)9K6b7W2)9J5c8Y4y4U0M7X3W2H3N6q4)9J5y4X3N6@1i4K6y4n7i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1$3i4K6S2r3i4K6V1H3i4@1f1@1i4@1u0m8i4@1p5@1i4@1f1$3i4@1t1J5i4@1p5I4i4@1f1#2i4K6S2r3i4K6S2p5i4@1f1#2i4@1u0m8i4K6V1@1i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1$3i4K6W2r3i4@1p5#2i4@1f1%4i4K6W2o6i4K6S2n7i4@1f1$3i4@1u0m8i4K6V1H3i4@1f1%4i4@1p5H3i4K6R3I4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4K6S2r3i4K6V1I4i4@1f1%4i4K6S2q4i4@1t1H3i4@1g2r3i4@1u0o6i4K6W2m8
,仔细看看发现chanlenge3颜色不同,貌似有链接存在,点击发现地址栏中出现:829K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4G2j5$3q4D9K9r3!0K6N6q4)9J5c8X3u0@1M7$3I4S2j5W2)9J5c8Y4k6#2L8r3&6W2M7X3q4T1K9h3I4A6N6s2W2Q4x3V1k6^5M7%4y4Q4x3V1k6^5M7%4x3K6i4K6u0W2M7r3S2H3i4K6y4r3N6q4)9K6c8s2c8A6N6r3I4W2 ,这个地址可能存在xss,试试?修改为:254K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3I4G2j5$3q4D9K9r3!0K6N6q4)9J5c8X3u0@1M7$3I4S2j5W2)9J5c8Y4k6#2L8r3&6W2M7X3q4T1K9h3I4A6N6s2W2Q4x3V1k6^5M7%4y4Q4x3V1k6^5M7%4x3K6i4K6u0W2M7r3S2H3i4K6y4r3N6q4)9K6c8q4)9J5y4X3I4@1i4K6y4n7M7$3y4J5K9i4m8@1i4K6t1$3k6%4c8Q4x3@1u0S2L8r3g2J5N6q4)9J5z5o6q4Q4x3U0W2Q4x3U0k6D9N6q4)9K6b7W2)9J5c8Y4y4U0M7X3W2H3N6q4)9J5y4X3N6@1i4K6y4n7i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1$3i4K6S2r3i4K6V1H3i4@1f1@1i4@1u0m8i4@1p5@1i4@1f1$3i4@1t1J5i4@1p5I4i4@1f1#2i4K6S2r3i4K6S2p5i4@1f1#2i4@1u0m8i4K6V1@1i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1$3i4K6W2r3i4@1p5#2i4@1f1%4i4K6W2o6i4K6S2n7i4@1f1$3i4@1u0m8i4K6V1H3i4@1f1%4i4@1p5H3i4K6R3I4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4K6S2r3i4K6V1I4i4@1f1%4i4K6S2q4i4@1t1H3i4@1g2r3i4@1u0o6i4K6W2m8
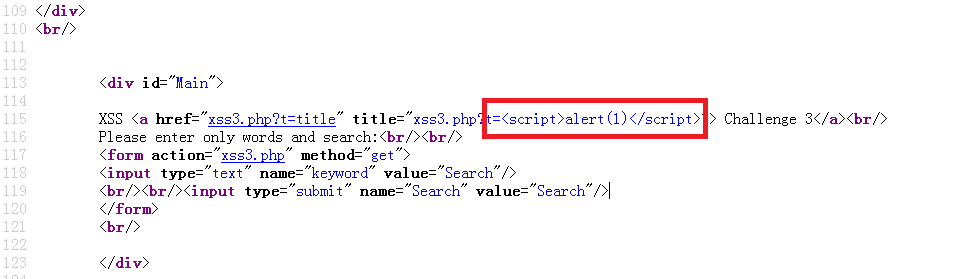
没有转码,直接写入title属性中,那试试闭合双引号:?t=”><script>alert(1)</script>,ok,弹框了
参考文献:
[1]0e8K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3u0J5k6h3q4C8N6r3S2W2M7$3g2U0N6i4u0A6N6s2W2Q4x3X3g2U0L8$3#2Q4x3V1j5J5x3o6p5K6i4K6u0r3x3e0u0Q4x3V1k6T1N6s2y4Q4x3X3c8H3k6h3&6@1k6i4y4@1K9h3&6Y4i4K6u0V1L8r3q4T1i4K6u0V1N6Y4g2D9L8X3g2J5j5h3u0D9k6g2)9J5k6s2N6W2j5W2)9J5k6h3S2@1L8h3I4Q4c8f1k6Q4b7V1y4Q4z5o6S2Q4c8e0g2Q4z5p5k6Q4b7f1k6Q4c8e0S2Q4z5o6y4Q4b7V1c8Q4c8e0W2Q4z5f1y4Q4z5o6m8Q4c8e0S2Q4b7e0k6Q4z5o6q4Q4c8e0g2Q4z5o6N6Q4b7V1q4Q4c8e0g2Q4z5p5g2Q4b7V1u0Q4c8e0k6Q4z5o6W2Q4z5p5c8Q4c8e0S2Q4z5o6y4Q4b7V1c8Q4c8e0N6Q4z5f1y4Q4z5p5u0Q4c8e0g2Q4z5o6S2Q4b7U0l9`.![]() )
)
[2]653K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2G2N6$3q4K6M7q4)9J5k6h3!0J5k6#2)9J5c8X3W2F1k6r3g2^5i4K6u0W2M7r3S2H3i4K6u0r3h3q4y4e0i4K6g2X3c8X3W2D9N6r3g2J5i4K6g2X3c8i4k6S2M7$3W2G2L8W2)9#2k6V1y4Z5k6h3q4@1i4K6g2X3f1$3S2W2k6i4b7`.

