-
-
[原创]关于WhiteHat Wargame RE005的分析
-
发表于: 2015-7-28 22:54 11530
-
cm来源: 93fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4j5i4u0Y4j5h3#2W2i4K6u0W2N6$3S2A6N6r3g2Z5j5i4c8Q4x3X3g2$3L8W2)9J5c8R3`.`.
网站里的re005, 这个cm对大牛来说太小菜了,大牛们就飘过吧...
拿到cm,先用PEiD查壳:
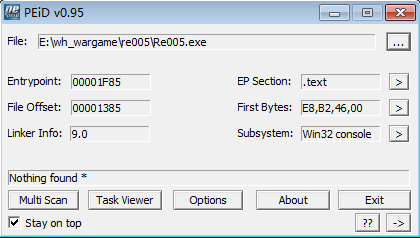
Nothing found...没办法,接下来先运行试试,随便打个字符串:
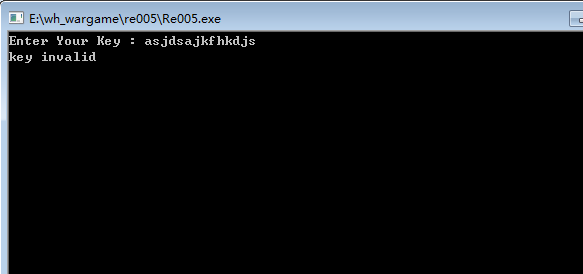
写了key invalid.直接用od跟上,本想先查一下字符串,可发现程序里没有”key invalid”的提示,猜测应该是字符串被加密了。没办法,只好单步了。
单步后跟到一个关键点:
00011000 > $ 55 push ebp 00011001 . 8BEC mov ebp, esp 00011003 . 83EC 0C sub esp, 0xC 00011006 . 53 push ebx 00011007 . 56 push esi 00011008 . 8935 002D0200 mov dword ptr [0x22D00], esi ; record current TickCount 0001100E . FF15 00E00100 call dword ptr [<&KERNEL32.GetTickCou>; [GetTickCount 00011014 . A3 FC2C0200 mov dword ptr [0x22CFC], eax ; anti-dbg 00011019 . 0FB605 1A2D02>movzx eax, byte ptr [0x22D1A] 00011020 . 50 push eax 00011021 . E8 DE090000 call <operator_new_uint> ; operator new (uint) 00011026 . 68 F4010000 push 0x1F4 ; (initial cpu selection) 0001102B . 8BD8 mov ebx, eax 0001102D . 6A 00 push 0x0 0001102F . 68 202D0200 push 00022D20 00011034 . 895D F4 mov dword ptr [ebp-0xC], ebx 00011037 . E8 94600000 call <memset> ; memset
00011550 >/$ 55 push ebp 00011551 |. 8BEC mov ebp, esp 00011553 |. 83EC 0C sub esp, 0xC 00011556 |. 53 push ebx 00011557 |. 56 push esi 00011558 |. 57 push edi 00011559 |. 68 44210200 push 00022144 0001155E |. 68 20030000 push 0x320 00011563 |. E8 98080000 call 00011E00 00011568 |. 8B1D 08E00100 mov ebx, dword ptr [<&KERNEL32.LoadL>; kernel32.LoadLibraryA 0001156E |. 83C4 08 add esp, 0x8 00011571 |. 68 90FE0100 push 0001FE90 ; /user32.dll 00011576 |. 8BF0 mov esi, eax ; | 00011578 |. FFD3 call ebx ; \LoadLibraryA 0001157A |. 8B3D 0CE00100 mov edi, dword ptr [<&KERNEL32.GetPr>; kernel32.GetProcAddress 00011580 |. 68 9CFE0100 push 0001FE9C ; /messageboxa 00011585 |. 50 push eax ; |hModule 00011586 |. FFD7 call edi ; \GetProcAddress ...
0001104B . B9 11000000 mov ecx, 0x11 00011050 > 3088 9C200200 xor byte ptr [eax+0x2209C], cl 00011056 . 40 inc eax 00011057 . 3BC1 cmp eax, ecx 00011059 .^ 7C F5 jl short 00011050 ; decrypt 0001105B . 68 9C200200 push 0002209C ; Enter Your Key : 00011060 . 68 8CFE0100 push 0001FE8C ; %s 00011065 . E8 080B0000 call <_printf> ...
00011078 . 85C0 test eax, eax 0001107A . 78 02 js short 0001107E 0001107C . 79 00 jns short 0001107E ...
0001107E > \8B48 04 mov ecx, dword ptr [eax+0x4] 00011081 . 6A 00 push 0x0 00011083 . 6A 00 push 0x0 00011085 . 6A 00 push 0x0 00011087 . 68 D0170100 push <thread_routine_1> 0001108C . 6A 00 push 0x0 0001108E . 6A 00 push 0x0 00011090 . FFD1 call ecx ; CreateThread
.text:00401819 xor eax, eax .text:0040181B pop ecx .text:0040181C call ebp ; GetTickCount .text:0040181E sub eax, Start_TickCount .text:00401824 cmp eax, 50h .text:00401827 jge short loc_401850 ; CurrentTickCount-StartTickCount>=80
.text:00401832 mov byte ptr [edi], 0E8h .text:00401836 mov esi, FuncStruct .text:0040183C mov eax, 0FFFFFFFFh .text:00401841 sub eax, edi .text:00401843 sub eax, 4 .text:00401846 db 3Eh .text:00401846 add eax, [esi+30h] .text:0040184A db 3Eh .text:0040184A mov [edi+1], eax .text:0040184E jmp short loc_40185A
.text:0040185A lea esi, ImageBaseOriginalByte .text:00401860 mov edi, ImageBase .text:00401866 add edi, 3 .text:00401869 xor ecx, ecx .text:0040186B mov cl, xor_1_7_1E .text:00401871 xor eax, eax .text:00401873 .text:00401873 loc_401873: ; CODE XREF: ThreadRoutine_2+AB j .text:00401873 db 3Eh .text:00401873 mov al, [edi] .text:00401876 db 3Eh .text:00401876 mov [esi], al .text:00401879 inc edi .text:0040187A inc esi .text:0040187B loop loc_401873 .text:0040187D xor ecx, ecx .text:0040187F mov cl, xor_1_90_97 .text:00401885 xor eax, eax .text:00401887 lea esi, ImageBaseOriginalByte_2 .text:0040188D .text:0040188D loc_40188D: ; CODE XREF: ThreadRoutine_2+C5 j .text:0040188D db 3Eh .text:0040188D mov al, [edi] .text:00401890 db 3Eh .text:00401890 mov [esi], al .text:00401893 inc edi .text:00401894 inc esi .text:00401895 loop loc_40188D .text:00401897 lea esi, ImageBaseOriginalByte_3 .text:0040189D xor ecx, ecx .text:0040189F mov ecx, 0Bh
00011092 . 68 80310200 push 00023180
00011097 . 68 78FE0100 push 0001FE78 ; %500[^\n]s
0001109C . E8 F4090000 call <_scanf> ; read from stdin
000110A1 . B8 80310200 mov eax, 00023180
000110A6 . 83C4 08 add esp, 0x8
000110A9 . 8D50 01 lea edx, dword ptr [eax+0x1]
000110AC . 8D6424 00 lea esp, dword ptr [esp]
000110B0 > 8A08 mov cl, byte ptr [eax]
000110B2 . 40 inc eax
000110B3 . 84C9 test cl, cl
000110B5 .^ 75 F9 jnz short 000110B0
000110B7 . 2BC2 sub eax, edx ; eax = string length
000110B9 . 0FB615 1A2D02>movzx edx, byte ptr [0x22D1A]
000110C0 . 8D4C12 06 lea ecx, dword ptr [edx+edx+0x6]
000110C4 . 3BC1 cmp eax, ecx
000110C6 . A3 042D0200 mov dword ptr [0x22D04], eax ; string length must >= 20
000110CB . 0F8C A4020000 jl 00011375
000110D1 . 6A 05 push 0x5
000110D3 . 68 84FE0100 push 0001FE84 ; flag{
000110D8 . 68 80310200 push 00023180
000110DD . E8 D0090000 call <_strncmp> ; string must begin with "FLAG{"
000110E2 . 83C4 0C add esp, 0xC
000110E5 . 85C0 test eax, eax
000110E7 . 0F85 88020000 jnz 00011375 ; jmp to failure
000110ED . A1 042D0200 mov eax, dword ptr [0x22D04]
000110F2 . 80B8 7F310200>cmp byte ptr [eax+0x2317F], 0x7D ; string ends with '}'
000110F9 . 0F85 76020000 jnz 00011375
000110FF . 0FB60D 1A2D02>movzx ecx, byte ptr [0x22D1A]
00011106 . 8D5409 06 lea edx, dword ptr [ecx+ecx+0x6]
0001110A . 8BF0 mov esi, eax
0001110C . 2BF2 sub esi, edx
0001110E . 83FE 16 cmp esi, 0x16 ; string length must = 42
010B114A > \03C9 add ecx, ecx 010B114C . 2BC1 sub eax, ecx 010B114E . 83E8 06 sub eax, 0x6 010B1151 . 50 push eax 010B1152 . 8D81 85310C01 lea eax, dword ptr [ecx+0x10C3185] 010B1158 . 50 push eax 010B1159 . 68 78330C01 push 010C3378 010B115E . E8 8D620000 call <memcpy> 010B1163 . 68 78330C01 push 010C3378 010B1168 . E8 53020000 call <StrToHex> 010B116D . 83C4 10 add esp, 0x10 010B1170 . A3 0C2D0C01 mov dword ptr [0x10C2D0C], eax 010B1175 . 85C0 test eax, eax 010B1177 . 75 14 jnz short 010B118D
赞赏记录
参与人
雪币
留言
时间
飘零丶
为你点赞~
2024-5-31 05:22
shinratensei
为你点赞~
2024-5-31 05:16
PLEBFE
为你点赞~
2022-7-27 02:43
赞赏
赞赏
雪币:
留言:


