#include "windows.h"
#include "tchar.h"
#pragma comment(lib, "urlmon.lib")
#define DEF_URL (L"933K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3u0S2K9h3c8#2i4K6u0W2j5$3!0E0i4K6u0r3K9h3&6V1k6i4S2Q4x3X3g2Z5N6r3#2D9")
#define DEF_FILE_NAME (L"index.html")
HMODULE g_hMod = NULL;
DWORD WINAPI ThreadProc(LPVOID lParam)
{
TCHAR szPath[_MAX_PATH] = {0,};
if( !GetModuleFileName( g_hMod, szPath, MAX_PATH ) )
return FALSE;
TCHAR *p = _tcsrchr( szPath, '\\' );
if( !p )
return FALSE;
_tcscpy_s(p+1, _MAX_PATH, DEF_FILE_NAME);
URLDownloadToFile(NULL, DEF_URL, szPath, 0, NULL);
return 0;
}
BOOL WINAPI DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpvReserved)
{
HANDLE hThread = NULL;
g_hMod = (HMODULE)hinstDLL;
switch( fdwReason )
{
case DLL_PROCESS_ATTACH :
OutputDebugString(L"<myhack.dll> Injection!!!");
hThread = CreateThread(NULL, 0, ThreadProc, NULL, 0, NULL);
CloseHandle(hThread);
break;
}
return TRUE;
}
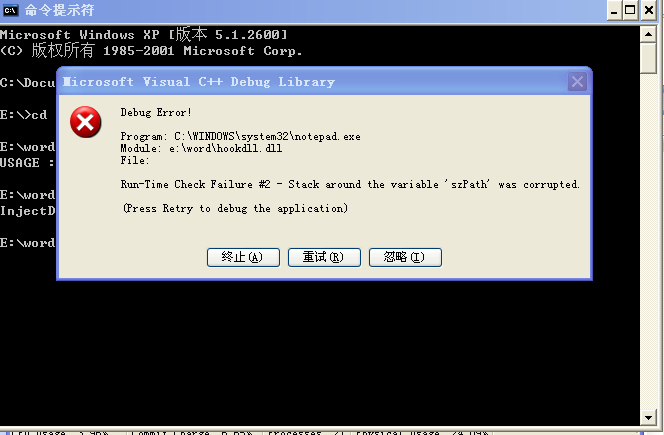
报错截图
我用od调试后发现,他提供的dll和我用他的源码(vs2008)生成的DLL汇编代码不一样。
这是他提供的DLL ThreadProc函数汇编代码
10001000 55 PUSH EBP
10001001 8BEC MOV EBP,ESP
10001003 81EC 0C020000 SUB ESP,20C
10001009 A1 00900010 MOV EAX,DWORD PTR DS:[10009000]
1000100E 33C5 XOR EAX,EBP
10001010 8945 FC MOV DWORD PTR SS:[EBP-4],EAX
10001013 33C0 XOR EAX,EAX
10001015 68 06020000 PUSH 206
1000101A 50 PUSH EAX
1000101B 8D8D F6FDFFFF LEA ECX,DWORD PTR SS:[EBP-20A]
10001021 51 PUSH ECX
10001022 66:8985 F4FDFFFF MOV WORD PTR SS:[EBP-20C],AX
10001029 E8 821A0000 CALL myhack.10002AB0
1000102E A1 70A70010 MOV EAX,DWORD PTR DS:[1000A770]
10001033 83C4 0C ADD ESP,0C
10001036 68 04010000 PUSH 104
1000103B 8D95 F4FDFFFF LEA EDX,DWORD PTR SS:[EBP-20C]
10001041 52 PUSH EDX
10001042 50 PUSH EAX
10001043 FF15 04600010 CALL DWORD PTR DS:[<&KERNEL32.GetModuleF>; kernel32.GetModuleFileNameW
10001049 85C0 TEST EAX,EAX
1000104B 74 43 JE SHORT myhack.10001090
1000104D 8D8D F4FDFFFF LEA ECX,DWORD PTR SS:[EBP-20C]
10001053 6A 5C PUSH 5C
10001055 51 PUSH ECX
10001056 E8 A5000000 CALL myhack.10001100
1000105B 83C4 08 ADD ESP,8
1000105E 85C0 TEST EAX,EAX
10001060 74 2E JE SHORT myhack.10001090
10001062 68 1C780010 PUSH myhack.1000781C ; UNICODE "index.html"
10001067 83C0 02 ADD EAX,2
1000106A 68 04010000 PUSH 104
1000106F 50 PUSH EAX
10001070 E8 B9000000 CALL myhack.1000112E
10001075 83C4 0C ADD ESP,0C
10001078 6A 00 PUSH 0
1000107A 6A 00 PUSH 0
1000107C 8D95 F4FDFFFF LEA EDX,DWORD PTR SS:[EBP-20C]
10001082 52 PUSH EDX
10001083 68 38780010 PUSH myhack.10007838 ; UNICODE "9ddK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3&6S2N6X3g2J5i4K6u0W2j5$3!0E0i4K6u0r3K9h3&6V1k6i4S2Q4x3X3g2Z5N6r3#2D9"
10001088 6A 00 PUSH 0
1000108A FF15 EC600010 CALL DWORD PTR DS:[<&urlmon.URLDownloadT>; urlmon.URLDownloadToFileW
10001090 8B4D FC MOV ECX,DWORD PTR SS:[EBP-4]
10001093 33CD XOR ECX,EBP
10001095 33C0 XOR EAX,EAX
10001097 E8 55000000 CALL myhack.100010F1
1000109C 8BE5 MOV ESP,EBP
1000109E 5D POP EBP
1000109F C2 0400 RETN 4
这是他提供的源码 (vs2008生成)ThreadProc函数汇编代码
10011370 55 PUSH EBP
10011371 8BEC MOV EBP,ESP
10011373 81EC E0020000 SUB ESP,2E0
10011379 53 PUSH EBX
1001137A 56 PUSH ESI
1001137B 57 PUSH EDI
1001137C 8DBD 20FDFFFF LEA EDI,DWORD PTR SS:[EBP-2E0]
10011382 B9 B8000000 MOV ECX,0B8
10011387 B8 CCCCCCCC MOV EAX,CCCCCCCC
1001138C F3:AB REP STOS DWORD PTR ES:[EDI]
1001138E A1 00700110 MOV EAX,DWORD PTR DS:[10017000]
10011393 33C5 XOR EAX,EBP
10011395 8945 FC MOV DWORD PTR SS:[EBP-4],EAX
10011398 33C0 XOR EAX,EAX
1001139A 66:8985 F0FDFFFF MOV WORD PTR SS:[EBP-210],AX
100113A1 68 06020000 PUSH 206
100113A6 6A 00 PUSH 0
100113A8 8D85 F2FDFFFF LEA EAX,DWORD PTR SS:[EBP-20E]
100113AE 50 PUSH EAX
100113AF E8 C4FCFFFF CALL hookdll.10011078
100113B4 83C4 0C ADD ESP,0C
100113B7 8BF4 MOV ESI,ESP
100113B9 68 04010000 PUSH 104
100113BE 8D85 F0FDFFFF LEA EAX,DWORD PTR SS:[EBP-210]
100113C4 50 PUSH EAX
100113C5 8B0D 38710110 MOV ECX,DWORD PTR DS:[10017138]
100113CB 51 PUSH ECX
100113CC FF15 C8810110 CALL DWORD PTR DS:[<&KERNEL32.GetModuleF>; kernel32.GetModuleFileNameW
100113D2 3BF4 CMP ESI,ESP
100113D4 E8 58FDFFFF CALL hookdll.10011131
100113D9 85C0 TEST EAX,EAX
100113DB 75 04 JNZ SHORT hookdll.100113E1
100113DD 33C0 XOR EAX,EAX
100113DF EB 63 JMP SHORT hookdll.10011444
100113E1 6A 5C PUSH 5C
100113E3 8D85 F0FDFFFF LEA EAX,DWORD PTR SS:[EBP-210]
100113E9 50 PUSH EAX
100113EA E8 C0FCFFFF CALL hookdll.100110AF
100113EF 83C4 08 ADD ESP,8
100113F2 8985 E4FDFFFF MOV DWORD PTR SS:[EBP-21C],EAX
100113F8 83BD E4FDFFFF 00 CMP DWORD PTR SS:[EBP-21C],0
100113FF 75 04 JNZ SHORT hookdll.10011405
10011401 33C0 XOR EAX,EAX
10011403 EB 3F JMP SHORT hookdll.10011444
10011405 8BF4 MOV ESI,ESP
10011407 68 94550110 PUSH hookdll.10015594 ; UNICODE "index.html"
1001140C 68 04010000 PUSH 104
10011411 8B85 E4FDFFFF MOV EAX,DWORD PTR SS:[EBP-21C]
10011417 83C0 02 ADD EAX,2
1001141A 50 PUSH EAX
1001141B FF15 CC820110 CALL DWORD PTR DS:[<&MSVCR90D.wcscpy_s>]
10011421 83C4 0C ADD ESP,0C
10011424 3BF4 CMP ESI,ESP
10011426 E8 06FDFFFF CALL hookdll.10011131
1001142B 6A 00 PUSH 0
1001142D 6A 00 PUSH 0
1001142F 8D85 F0FDFFFF LEA EAX,DWORD PTR SS:[EBP-210]
10011435 50 PUSH EAX
10011436 68 40550110 PUSH hookdll.10015540 ; UNICODE "aa6K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2Z5j5h3)9I4x3U0y4Q4x3X3g2U0L8$3#2Q4x3V1k6A6L8X3c8W2P5q4)9J5k6h3S2@1L8h3H3`."
1001143B 6A 00 PUSH 0
1001143D E8 2CFCFFFF CALL hookdll.1001106E
10011442 33C0 XOR EAX,EAX
10011444 52 PUSH EDX
10011445 8BCD MOV ECX,EBP
10011447 50 PUSH EAX
10011448 8D15 78140110 LEA EDX,DWORD PTR DS:[10011478]
1001144E E8 39FCFFFF CALL hookdll.1001108C
10011453 58 POP EAX
10011454 5A POP EDX
10011455 5F POP EDI
10011456 5E POP ESI
10011457 5B POP EBX
10011458 8B4D FC MOV ECX,DWORD PTR SS:[EBP-4]
1001145B 33CD XOR ECX,EBP
1001145D E8 B2FBFFFF CALL hookdll.10011014
10011462 81C4 E0020000 ADD ESP,2E0
10011468 3BEC CMP EBP,ESP
1001146A E8 C2FCFFFF CALL hookdll.10011131
1001146F 8BE5 MOV ESP,EBP
10011471 5D POP EBP
10011472 C2 0400 RETN 4
用OD调试发现问题就出在两段代码上
这是他提供的DLL文件
函数开头把10009000处的数据取出后和EBP xor 值放入栈中
10001000 55 PUSH EBP
10001001 8BEC MOV EBP,ESP
10001003 81EC 0C020000 SUB ESP,20C
10001009 A1 00900010 MOV EAX,DWORD PTR DS:[10009000]
1000100E 33C5 XOR EAX,EBP
10001010 8945 FC MOV DWORD PTR SS:[EBP-4],EAX
取出EBP-4 的值 和EBP XOR 调用CALL myhack.100010F1验证
10001090 8B4D FC MOV ECX,DWORD PTR SS:[EBP-4]
10001093 33CD XOR ECX,EBP
10001095 33C0 XOR EAX,EAX
10001097 E8 55000000 CALL myhack.100010F1
以上代码能正确验证栈
而VS2008生成的
1001141B FF15 CC820110 CALL DWORD PTR DS:[<&MSVCR90D.wcscpy_s>]函数里调用
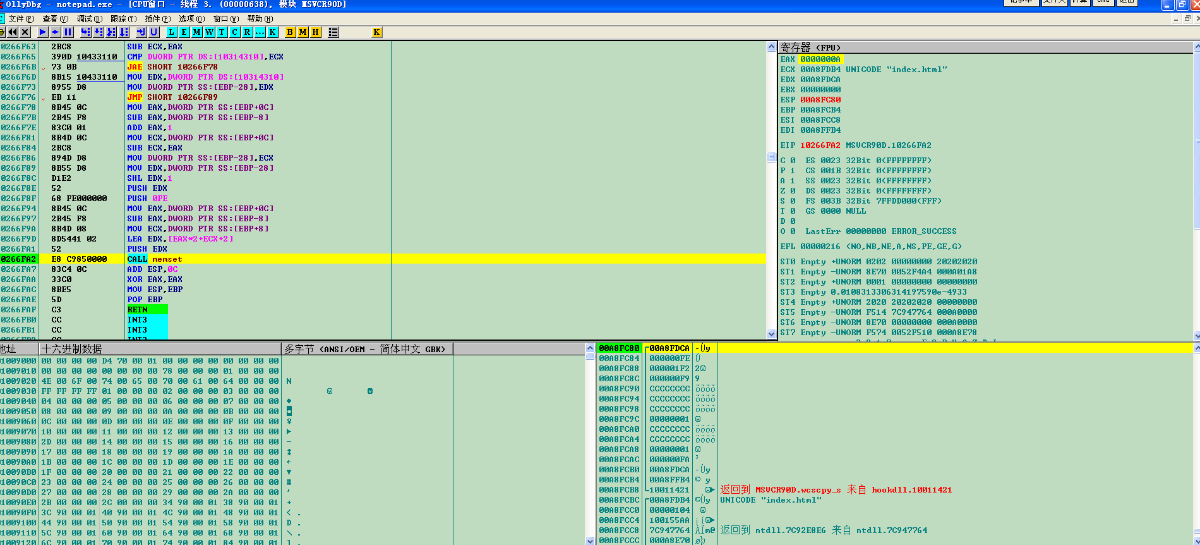
call memset函数把堆栈中的数据更改了以至于验证不过去程序报错
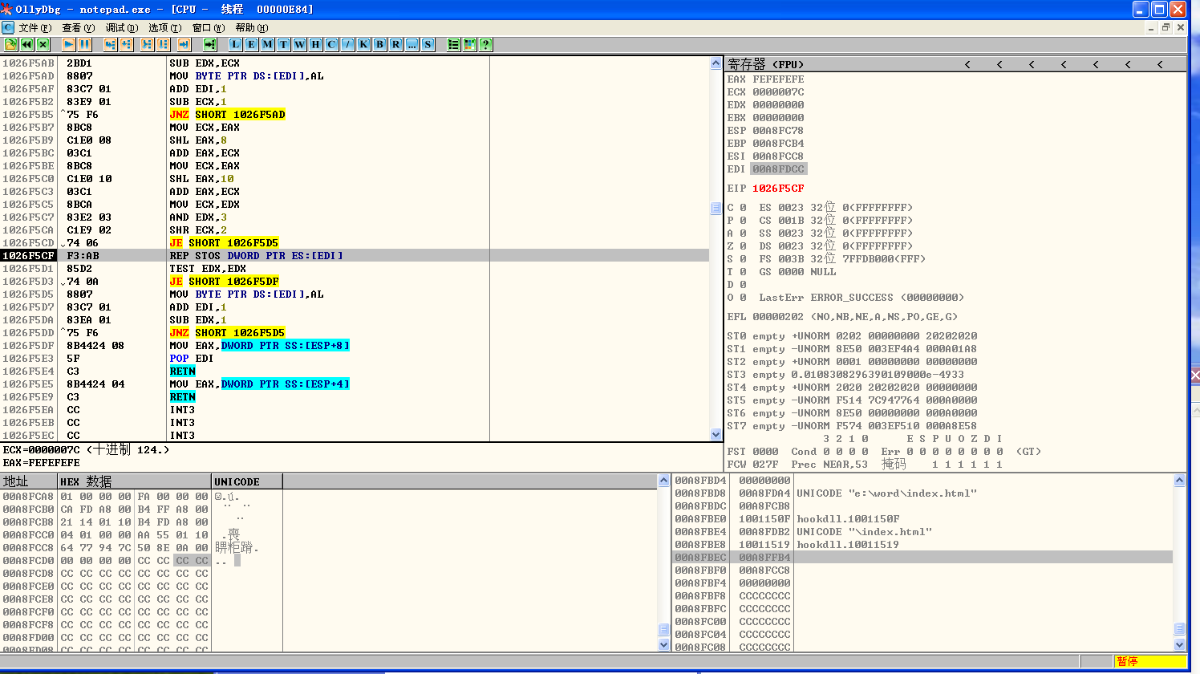
更改堆栈的指令 覆盖范围 00A8FDCC-00A8FFBC把要验证的值给覆盖了
求大神解惑是程序源码的问题还是VS2008编译器的问题????
问题在 _tcscpy_s(p+1, _MAX_PATH, DEF_FILE_NAME);函数的第二个参数,第二个参数为整个数组剩余的元素个数,该参数可以小于数组的实际数目但不能大于数组的实际数目。不然 _tcscpy_s()函数调用memset函数填充数组时会照成栈溢出把要验证的值给覆盖掉。
[培训]科锐逆向工程师培训第53期2025年7月8日开班!