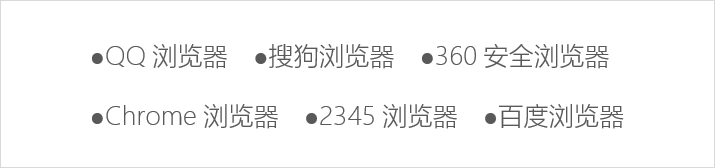
一、 概述
日前,火绒安全团队截获后门病毒“Humpler”。该病毒伪装成多款小工具(如:老板键、屏幕亮度调节等),正通过2345软件大全等多个知名下载站进行传播。病毒入侵电脑后,会劫持QQ、360、搜狗等(市面上所有主流)浏览器首页。并且该后门病毒还在不断更新恶意代码,不排除未来会向用户电脑派发更具威胁性病毒的可能性。
Humpler病毒伪装成“老板键”、“屏幕亮度调节”等多款小工具。当用户在2345软件大全(原多特下载站)、非凡、PC6等下载站下载并运行上述小工具后,病毒将侵入电脑。随即弹出弹窗,询问是否“愿意支持”该软件,如果用户选择“支持”,病毒会立即劫持浏览器首页。但即使用户选择拒绝,病毒仍会在一天之后劫持用户的浏览器首页。也就是说,无论用户选择愿意与否,被感染电脑浏览器首页都会被劫持。
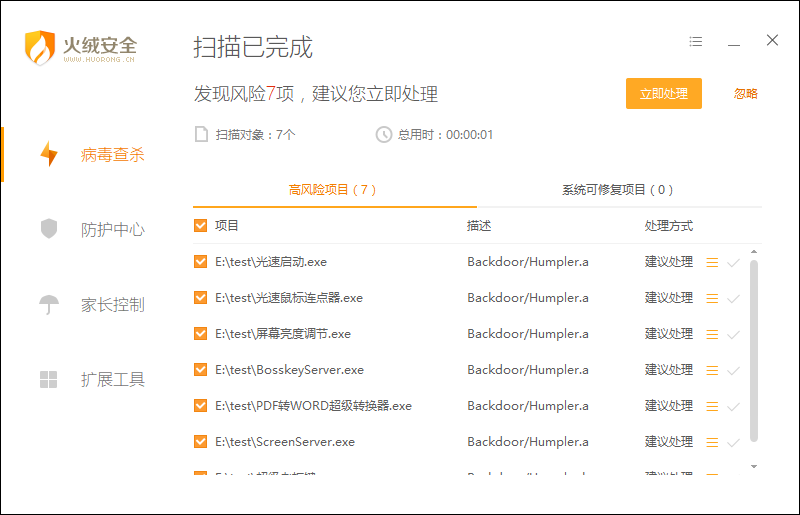
“火绒安全软件”最新版即可拦截并查杀该病毒。我们看到这些小工具在下载站中的排名靠前,极易吸引用户点击下载。建议近期在上述下载站下载过软件的用户,尽快使用“火绒安全软件”对电脑进行查杀。
二、 样本分析
近期,火绒截获到一批后门病毒样本,病毒会将自己伪装成小工具(如:超级老板键、超级变声器、屏幕亮度调节等),并会通过2345软件大全、非凡下载站、PC6下载站等多个软件下载站进行传播。病毒会通过C&C服务器获取最终恶意代码,恶意代码执行后,表面会询问用户是否“愿意支持”软件后进行首页锁定。但在第二天用户再次启动该程序时,不论用户是否选择“愿意支持”都会强行劫持浏览器首页。而且为了躲避安全厂商查杀,现阶段被下发的病毒模块为PE头被简化过的模块数据。截至到目前,被下发的病毒模块数据依然在持续更新,我们不排除病毒将来会下发其他病毒模块的可能性。下载站下载页面,如下图所示:
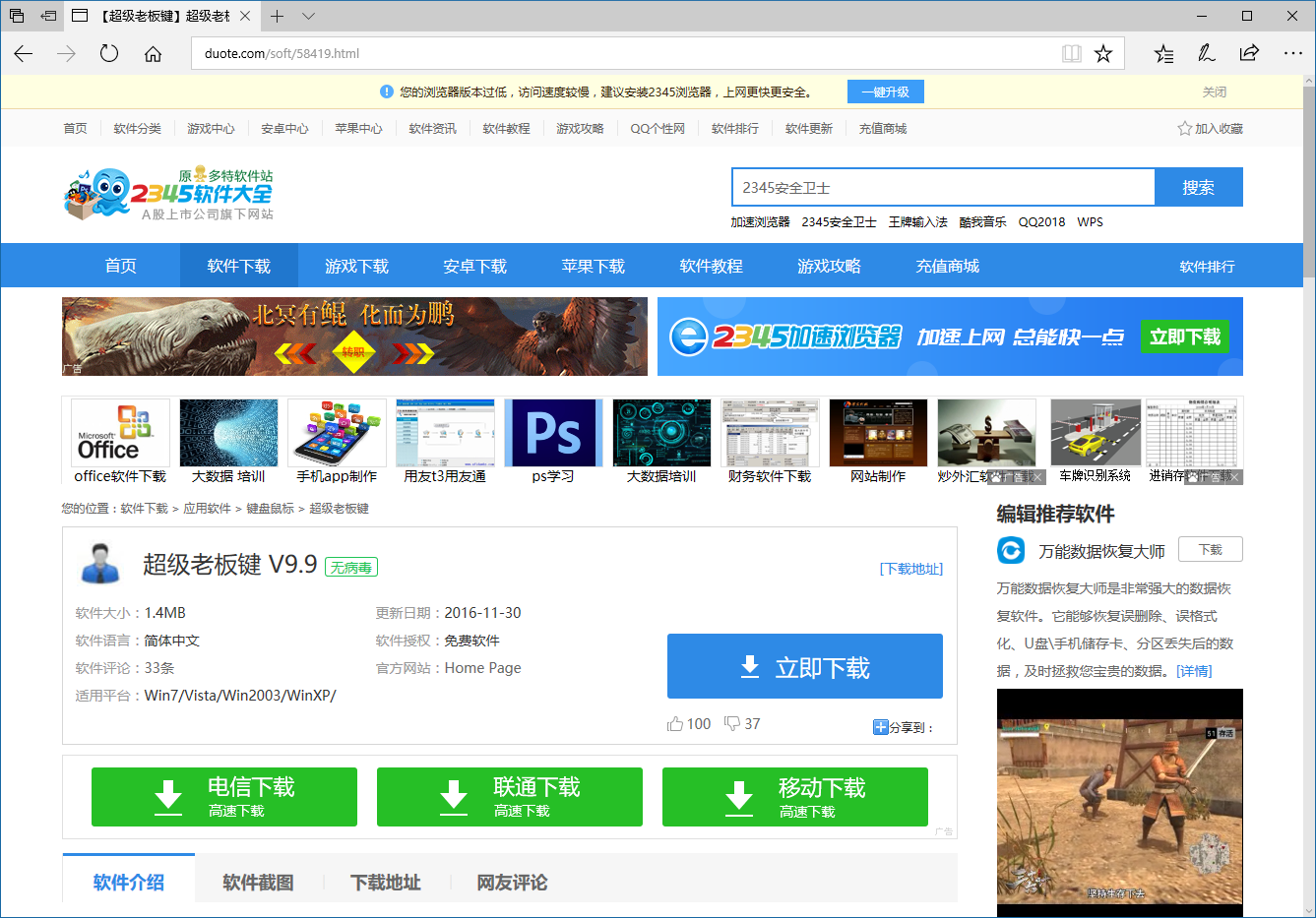
软件下载页面
我们以超级老板键为例,病毒代码执行后会与C&C服务器(c4eK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3u0S2K9h3c8#2i4K6u0V1K9r3!0E0k6g2)9J5k6h3y4G2L8g2!0q4y4g2)9&6x3W2)9^5b7%4N6%4N6#2)9J5k6e0u0C8x3Y4g2Q4x3X3g2U0L8$3#2Q4c8f1k6Q4b7V1y4Q4z5o6W2Q4c8e0S2Q4b7V1k6Q4z5f1u0Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0W2Q4z5o6m8Q4z5f1q4Q4c8e0S2Q4b7f1g2Q4b7f1k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0S2Q4b7f1k6Q4b7U0N6Q4c8e0k6Q4b7U0q4Q4z5o6u0Q4c8e0S2Q4b7V1k6Q4z5f1y4Q4c8e0N6Q4b7e0S2Q4z5p5u0Q4c8e0k6Q4z5o6q4Q4b7U0k6Q4c8e0k6Q4z5o6c8Q4z5p5k6Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8e0S2Q4z5o6N6Q4b7U0y4Q4c8e0k6Q4z5f1y4Q4b7f1y4Q4c8e0g2Q4z5f1y4Q4b7U0m8Q4c8e0S2Q4b7V1k6Q4z5f1u0Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0k6Q4z5o6W2Q4b7e0N6Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0N6Q4z5e0N6Q4z5o6g2Q4c8e0k6Q4b7f1k6Q4z5e0u0Q4c8e0W2Q4z5o6m8Q4b7V1u0Q4c8e0S2Q4b7V1g2Q4z5e0q4Q4c8e0N6Q4z5f1u0Q4b7U0S2Q4c8e0g2Q4z5o6g2Q4b7U0y4Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8e0c8Q4b7V1y4Q4z5f1q4Q4c8e0g2Q4b7e0c8Q4b7U0W2Q4c8e0k6Q4z5f1c8Q4z5o6u0Q4c8e0g2Q4z5f1y4Q4b7e0S2Q4c8e0S2Q4b7V1c8Q4b7f1k6Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8e0g2Q4z5p5q4Q4z5f1k6Q4c8e0S2Q4z5o6y4Q4b7V1c8Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8e0c8Q4b7U0S2Q4b7f1c8Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5f1y4Q4b7e0S2Q4c8e0N6Q4z5p5u0Q4b7f1y4Q4c8e0N6Q4b7f1u0Q4z5p5u0Q4c8e0N6Q4b7V1q4Q4b7V1k6Q4c8e0N6Q4b7e0S2Q4z5p5u0Q4c8e0c8Q4b7U0S2Q4b7f1c8Q4c8e0k6Q4z5o6W2Q4b7e0N6Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0N6Q4z5e0N6Q4z5o6g2Q4c8e0k6Q4b7f1k6Q4z5e0u0Q4c8e0W2Q4z5o6m8Q4b7V1u0Q4c8e0S2Q4b7V1g2Q4z5e0q4Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0N6Q4z5f1u0Q4b7U0S2Q4c8e0g2Q4z5o6g2Q4b7U0y4Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7e0k6Q4z5o6u0Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0g2Q4z5f1u0Q4b7V1g2Q4c8e0k6Q4z5o6W2Q4z5o6m8Q4c8e0N6Q4b7e0c8Q4b7V1q4Q4c8f1k6Q4b7V1y4Q4z5f1p5`.
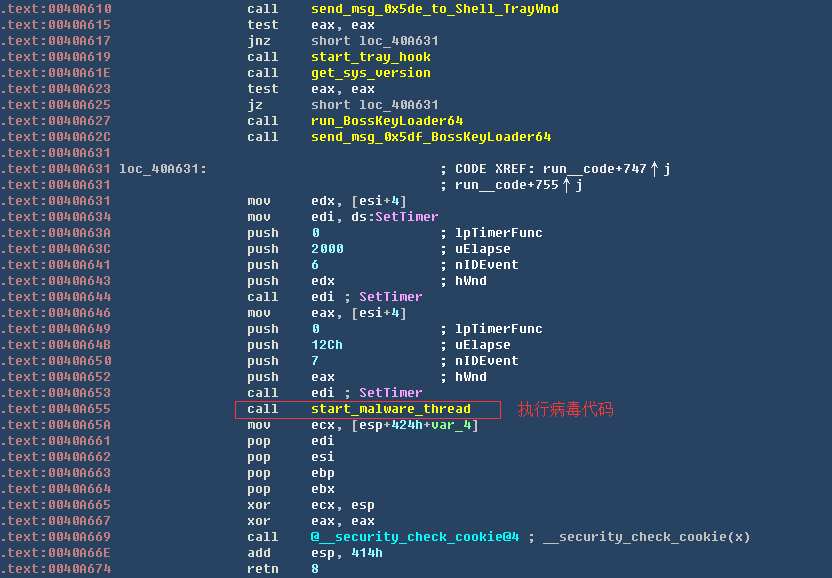
病毒代码位置
病毒首先会通过访问64dK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3u0S2K9h3c8#2i4K6u0W2j5$3!0E0i4@1f1$3i4@1p5K6i4K6R3H3i4@1f1$3i4@1t1#2i4K6S2n7i4@1f1#2i4@1u0p5i4K6V1K6i4@1f1#2i4K6R3&6i4K6S2p5i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1%4i4@1u0p5i4K6V1I4i4@1f1%4i4@1u0n7i4K6W2o6i4@1f1%4i4K6S2m8i4@1t1$3i4@1f1$3i4K6R3H3i4K6R3I4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4@1p5$3i4K6R3J5i4@1f1$3i4K6W2q4i4K6W2o6i4@1f1$3i4K6V1%4i4@1p5H3i4@1f1$3i4@1t1K6i4K6V1#2i4@1f1$3i4@1q4p5i4@1p5K6i4@1f1#2i4@1t1^5i4@1t1^5i4@1f1^5i4K6R3I4i4K6V1@1i4@1f1%4i4@1u0p5i4K6V1I4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4K6R3^5i4K6V1&6i4@1f1@1i4@1t1^5i4K6S2p5i4@1f1@1i4@1u0o6i4K6W2m8i4@1f1^5i4@1u0r3i4K6V1H3i4@1f1^5i4@1p5I4i4K6S2o6i4@1f1%4i4K6V1%4i4K6R3#2i4@1f1$3i4@1q4r3i4K6V1J5i4@1f1$3i4@1t1#2i4K6R3I4i4@1f1%4i4@1p5^5i4K6S2n7i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1#2i4@1p5$3i4K6R3J5i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1#2i4K6W2n7i4@1u0q4i4@1f1$3i4K6R3&6i4K6R3H3i4@1f1%4i4@1p5@1i4@1u0m8i4@1g2r3i4@1u0o6i4K6W2m8

检测当前网络状态
在网络状态正常的情况下,病毒首先会解密出用于请求远程恶意代码的相关代码,并进行执行。如下图所示:
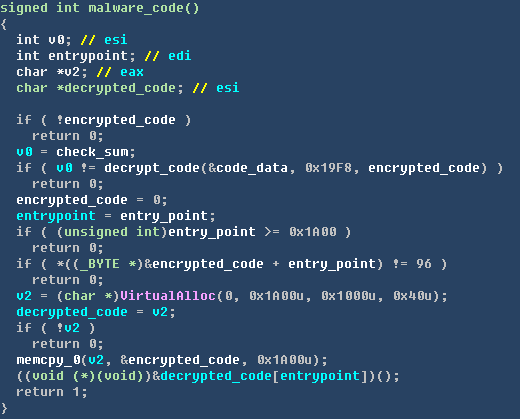
解密执行代码逻辑
在上述解密后代码运行时,会通过检查软件断点的方式检测调试器。相关代码,如下图所示:
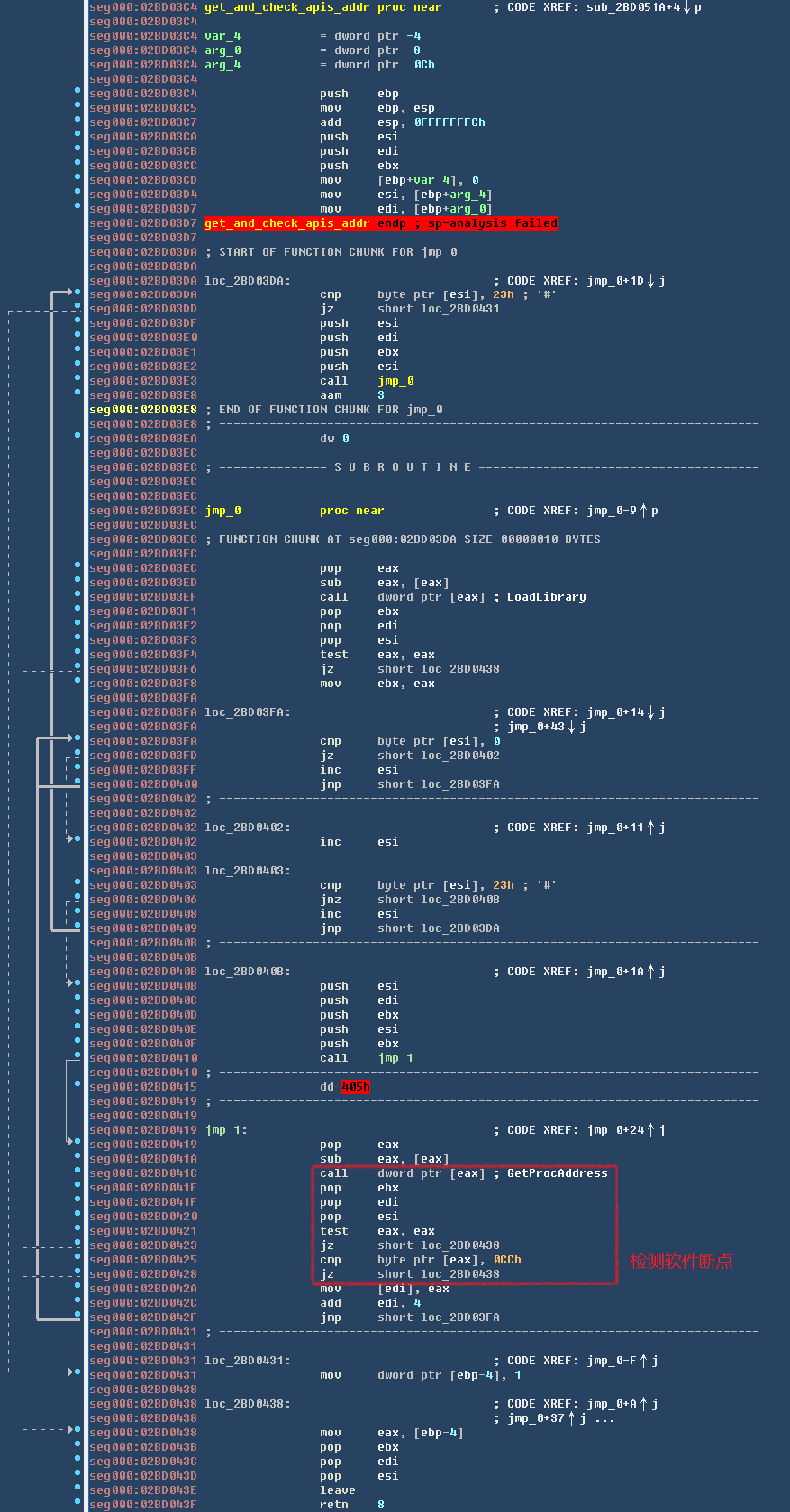
检测调试器代码
解密后的病毒代码,首先会访问C&C服务器地址(hxxp://0b7K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3u0S2K9h3c8#2i4K6u0V1K9r3!0E0k6g2)9J5k6h3y4G2L8g2)9J5c8X3u0G2M7%4y4C8k6i4W2Q4x3V1k6U0K9r3g2U0K9%4g2H3k6r3q4@1k6g2)9J5k6i4c8^5N6q4!0q4c8W2!0n7b7#2)9^5z5g2!0q4z5q4)9^5c8g2!0n7y4#2!0q4y4g2)9^5c8W2)9&6y4W2!0q4y4W2)9^5x3g2!0n7y4W2!0q4y4W2)9^5y4q4)9^5c8W2!0q4y4q4!0n7b7W2!0m8x3#2!0q4y4#2!0m8x3q4)9^5x3g2!0q4y4q4!0n7z5q4)9^5b7W2!0q4z5q4!0n7c8q4!0n7c8q4!0q4y4g2)9&6b7#2!0n7x3q4!0q4y4g2)9&6c8q4)9^5x3q4!0q4x3#2)9^5x3q4)9^5x3W2!0q4y4W2)9&6b7#2)9^5x3q4!0q4y4#2!0n7b7W2)9^5z5q4!0q4y4q4!0n7b7#2)9&6b7g2!0q4z5g2)9^5x3q4)9&6b7g2!0q4z5q4!0n7c8W2)9^5y4#2!0q4z5q4!0m8c8g2!0n7c8W2!0q4z5g2)9&6y4#2!0m8c8f1y4Q4x3U0k6S2L8i4m8Q4x3@1u0o6i4@1f1$3i4K6W2o6i4K6S2p5i4@1f1#2i4K6S2m8i4@1p5I4i4@1f1#2i4K6V1&6i4@1p5^5i4@1g2r3i4@1u0o6i4K6R3^5K9s2S2^5M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6e0u0C8x3Y4g2Q4x3X3g2U0L8$3#2Q4x3V1k6H3L8s2g2Y4K9h3&6Q4x3V1k6T1L8%4y4K6K9$3g2&6i4K6u0r3j5X3!0K6M7$3E0W2P5i4g2H3k6r3q4@1k6g2)9J5k6h3c8S2N6q4!0q4c8W2!0n7b7#2)9^5z5g2!0q4z5q4)9^5c8g2!0n7y4#2!0q4y4g2)9^5c8W2)9&6y4W2!0q4y4g2)9^5z5q4!0n7x3q4!0q4z5q4!0n7c8W2)9&6b7#2!0q4y4#2!0m8z5q4)9^5b7W2!0q4y4W2)9^5x3g2!0n7y4W2!0q4y4W2)9^5y4q4)9^5c8W2!0q4y4q4!0n7b7W2!0m8x3#2!0q4y4#2!0m8x3q4)9^5x3g2!0q4y4g2)9^5z5q4!0n7x3q4!0q4y4g2)9^5y4W2)9^5y4g2!0q4y4g2!0m8c8q4)9&6z5q4!0q4y4q4!0n7z5q4!0m8c8q4!0q4y4g2)9^5b7g2!0m8x3q4!0q4z5q4!0n7c8q4!0n7c8q4!0q4y4g2!0n7z5g2!0n7y4W2!0q4y4W2)9^5z5g2!0m8y4#2!0q4z5q4!0m8x3g2)9^5b7#2!0q4x3#2)9^5x3q4)9^5x3W2!0q4y4W2)9&6b7#2)9^5x3q4!0q4y4#2!0n7b7W2)9^5z5q4!0q4z5q4!0m8c8W2!0n7y4#2!0q4y4W2!0n7x3g2)9^5x3W2!0q4y4g2)9^5z5q4!0n7x3q4!0q4y4#2)9&6b7g2)9^5y4q4!0q4y4W2)9^5x3g2!0n7y4W2!0q4y4W2)9^5y4q4)9^5c8W2!0q4y4q4!0n7b7W2!0m8x3#2!0q4y4#2!0m8x3q4)9^5x3g2!0q4c8W2!0n7b7#2)9^5b7#2!0q4y4W2)9&6z5q4!0m8c8W2!0q4y4q4!0n7z5q4)9^5x3q4!0q4y4q4!0n7z5q4!0m8b7g2m8q4i4@1f1#2i4@1p5@1i4@1t1@1i4@1f1^5i4@1p5J5i4@1q4n7i4@1f1%4i4@1t1J5i4@1u0q4i4@1f1%4i4@1q4q4i4K6R3H3i4@1f1^5i4@1u0r3i4K6R3%4i4@1f1%4i4K6W2m8i4K6R3@1f1p5g2Q4c8e0k6Q4z5e0k6Q4z5o6N6Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0N6Q4z5e0N6Q4z5o6g2Q4c8e0k6Q4b7f1k6Q4z5e0u0Q4c8e0g2Q4z5f1y4Q4b7e0S2Q4c8e0S2Q4z5p5g2Q4b7U0N6Q4c8e0g2Q4z5p5k6Q4z5e0k6Q4c8e0g2Q4z5o6S2Q4b7U0m8Q4c8e0k6Q4z5o6q4Q4b7U0k6Q4c8e0k6Q4z5o6c8Q4z5p5k6Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8e0c8Q4b7V1y4Q4z5f1q4Q4c8e0W2Q4z5o6m8Q4z5f1q4Q4c8e0S2Q4b7V1k6Q4z5o6N6Q4c8e0S2Q4z5e0W2Q4z5f1q4Q4c8e0k6Q4z5p5u0Q4z5f1k6Q4c8e0k6Q4z5e0S2Q4b7e0m8Q4c8e0g2Q4b7U0m8Q4z5o6c8Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4z5e0k6Q4b7U0W2Q4c8e0g2Q4b7V1y4Q4z5p5k6Q4c8e0g2Q4b7U0m8Q4z5o6k6Q4c8e0k6Q4z5o6q4Q4b7U0k6Q4c8e0k6Q4z5o6c8Q4z5p5k6Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8e0g2Q4z5p5q4Q4b7e0m8Q4c8e0S2Q4b7V1c8Q4b7V1c8Q4c8e0g2Q4z5o6S2Q4b7U0m8Q4c8e0g2Q4z5o6k6Q4z5o6g2Q4c8e0g2Q4b7f1c8Q4z5e0S2Q4c8e0c8Q4b7U0S2Q4b7f1c8Q4c8e0S2Q4b7V1k6Q4z5f1u0Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0k6Q4z5o6W2Q4b7e0N6Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0c8Q4b7U0W2Q4z5p5u0Q4c8e0k6Q4z5o6W2Q4z5o6m8Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0W2Q4z5o6m8Q4z5f1q4Q4c8e0S2Q4b7V1k6Q4z5o6N6o6i4K6t1$3j5h3#2H3i4K6y4n7b7#2!0q4y4W2)9&6b7#2)9^5c8q4!0q4y4g2)9^5b7g2!0m8x3g2!0q4y4g2)9&6z5g2!0m8z5q4!0q4y4q4!0n7z5q4)9^5b7W2!0q4y4g2)9^5c8W2)9&6x3g2!0q4y4#2!0n7x3W2!0n7c8g2!0q4y4#2!0m8c8g2)9^5x3q4!0q4y4#2)9&6b7g2)9^5y4q4m8q4i4@1f1&6i4K6V1#2i4K6W2o6i4@1f1#2i4K6R3K6i4K6S2r3i4@1f1$3i4K6V1#2i4@1t1H3i4@1f1$3i4K6S2p5i4@1q4q4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1^5i4K6R3H3i4K6S2o6i4@1f1@1i4@1t1^5i4K6S2p5i4@1f1$3i4K6V1^5i4@1q4r3i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1#2i4K6S2r3i4K6V1I4i4@1f1#2i4@1q4q4i4K6S2o6i4@1f1$3i4K6V1#2i4@1t1@1i4@1f1%4i4K6W2m8i4K6R3@1f1p5g2Q4c8e0W2Q4z5e0g2Q4z5f1y4Q4c8e0g2Q4z5o6y4Q4z5p5k6Q4c8e0k6Q4z5e0k6Q4z5o6N6Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7U0S2Q4b7V1u0Q4c8e0S2Q4b7e0k6Q4z5o6q4Q4c8e0k6Q4z5e0S2Q4b7f1k6Q4c8e0c8Q4b7U0S2Q4b7V1q4Q4c8e0c8Q4b7V1q4Q4z5o6k6Q4c8e0g2Q4b7f1k6Q4b7U0W2Q4c8e0k6Q4z5p5q4Q4z5e0N6Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0g2Q4z5p5g2Q4z5o6u0Q4c8e0g2Q4z5e0g2Q4z5o6k6Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4z5f1k6Q4b7e0g2Q4c8e0k6Q4z5f1c8Q4z5o6m8Q4c8e0g2Q4z5e0u0Q4z5p5y4Q4c8e0g2Q4b7f1g2Q4z5o6W2Q4c8e0g2Q4z5o6g2Q4b7e0S2Q4c8e0N6Q4b7e0m8Q4z5e0c8Q4c8e0N6Q4b7e0W2Q4b7U0k6Q4c8e0c8Q4b7V1q4Q4b7V1q4Q4c8e0g2Q4z5e0q4Q4z5e0S2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0W2Q4z5o6m8Q4z5o6k6Q4c8e0g2Q4z5e0m8Q4z5e0q4Q4c8e0g2Q4z5o6S2Q4z5o6k6Q4c8e0k6Q4z5f1g2Q4z5e0m8Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0k6Q4z5o6q4Q4b7U0k6Q4c8e0k6Q4z5o6c8Q4z5p5k6Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8e0k6Q4z5o6W2Q4b7e0N6Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7V1y4Q4z5f1q4Q4c8e0g2Q4b7V1y4Q4b7U0W2Q4c8e0g2Q4z5o6N6Q4b7V1q4Q4c8e0N6Q4b7f1q4Q4z5e0N6Q4c8e0g2Q4z5p5k6Q4b7e0y4Q4c8e0S2Q4b7f1k6Q4b7e0u0Q4c8e0W2Q4z5e0N6Q4b7f1g2Q4c8e0N6Q4z5e0c8Q4b7e0S2Q4c8e0k6Q4z5o6S2Q4b7U0N6Q4c8e0k6Q4z5e0S2Q4b7f1k6Q4c8e0g2Q4z5e0m8Q4b7e0k6Q4c8e0u0Q4z5o6m8Q4z5f1y4Q4c8e0k6Q4z5o6c8Q4b7V1k6Q4c8e0k6Q4z5o6c8Q4z5p5k6Q4c8e0k6Q4z5e0c8Q4b7f1k6Q4c8e0k6Q4z5p5y4Q4z5o6q4Q4c8e0u0Q4z5o6m8Q4z5f1c8Q4c8e0S2Q4b7f1k6Q4b7e0g2Q4c8e0S2Q4b7V1c8Q4b7f1k6Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7V1c8Q4z5o6k6Q4c8e0g2Q4b7e0k6Q4z5o6u0Q4c8e0k6Q4z5f1g2Q4z5f1y4Q4c8e0S2Q4b7V1k6Q4z5e0m8Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0k6Q4z5e0N6Q4b7e0g2Q4c8e0k6Q4z5f1y4Q4z5f1k6Q4c8e0c8Q4b7U0S2Q4z5p5g2Q4c8e0k6Q4b7U0y4Q4b7e0S2Q4c8e0g2Q4z5o6k6Q4z5p5y4Q4c8e0S2Q4b7e0q4Q4b7e0S2Q4c8f1k6Q4b7V1y4Q4z5o6S2t1d9@1g2k6i4K6g2X3b7#2g2d9f1V1g2z5g2q4)9#2k6W2g2e0c8g2u0Q4y4f1y4e0L8$3k6@1N6$3q4J5k6g2)9#2b7@1y4D9j5i4y4K6k6i4y4Q4y4f1y4o6e0q4y4u0c8q4)9#2b7#2)9%4b7U0u0n7y4e0y4r3x3p5p5%4i4K6u0V1x3K6t1K6z5q4)9J5k6o6c8T1y4r3c8Q4x3X3b7^5y4e0R3J5i4K6u0V1c8e0f1K6y4U0p5^5y4K6x3&6b7K6V1H3i4K6N6p5i4K6g2o6e0r3!0U0K9@1c8S2N6r3g2Q4c8f1k6Q4b7V1y4Q4z5o6W2Q4c8e0c8Q4b7U0S2Q4b7f1c8Q4c8e0S2Q4b7f1g2Q4b7U0m8Q4c8e0g2Q4b7V1c8Q4z5e0g2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0W2Q4b7e0k6Q4z5e0k6Q4c8e0k6Q4b7f1y4Q4b7e0q4Q4c8e0S2Q4b7V1k6Q4z5e0m8Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0k6Q4z5e0N6Q4b7e0g2Q4c8e0k6Q4z5f1y4Q4z5f1k6Q4c8e0c8Q4b7U0S2Q4z5p5c8Q4c8e0g2Q4z5e0m8Q4z5p5y4Q4c8e0k6Q4z5e0N6Q4b7U0k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5o6S2Q4z5e0W2Q4c8e0c8Q4b7V1y4Q4z5f1q4Q4c8e0N6Q4z5f1u0Q4b7U0c8Q4c8e0k6Q4z5p5g2Q4b7e0g2Q4c8e0k6Q4z5o6W2Q4b7e0N6Q4c8e0S2Q4b7e0q4Q4z5p5y4Q4c8e0W2Q4b7e0k6Q4z5e0k6Q4c8e0W2Q4b7e0q4Q4b7U0g2Q4c8e0g2Q4z5p5q4Q4b7f1u0Q4c8e0k6Q4z5p5y4Q4z5o6q4Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8e0W2Q4z5o6m8Q4b7V1u0Q4c8e0S2Q4b7V1g2Q4z5e0q4Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0g2Q4b7V1y4Q4b7U0W2Q4c8e0N6Q4b7f1q4Q4z5e0N6Q4c8e0k6Q4z5o6S2Q4b7f1q4Q4c8e0g2Q4z5f1u0Q4b7V1g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7e0k6Q4z5o6u0Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0g2Q4z5f1u0Q4b7V1g2Q4c8e0k6Q4z5o6W2Q4z5o6m8Q4c8e0N6Q4b7e0c8Q4b7V1q4Q4c8f1k6Q4b7V1y4Q4z5f1p5`.
弹窗截图
该病毒运行后还会将同目录下的BosskeyServer.exe注册为系统服务,而且BosskeyServer.exe中也包含有与主程序中相同逻辑,在首次运行的第二天BosskeyServer.exe则会自动劫持浏览器首页。不过在带有相同恶意代码的小工具中,并不是所有小工具都会注册系统服务,对于只有一个病毒模块的小工具来说,则需要依靠用户在首次运行的第二天执行带毒程序,才会在不经过用户允许的情况下劫持浏览器首页。
最终执行的恶意代码会通过检测运行进程、注册表、调试器和运行日期与分析人员进行对抗,只有在运行日期与首次运行日期不同时,才会继续执行恶意代码。被下发病毒模块的主要代码逻辑,如下图所示:
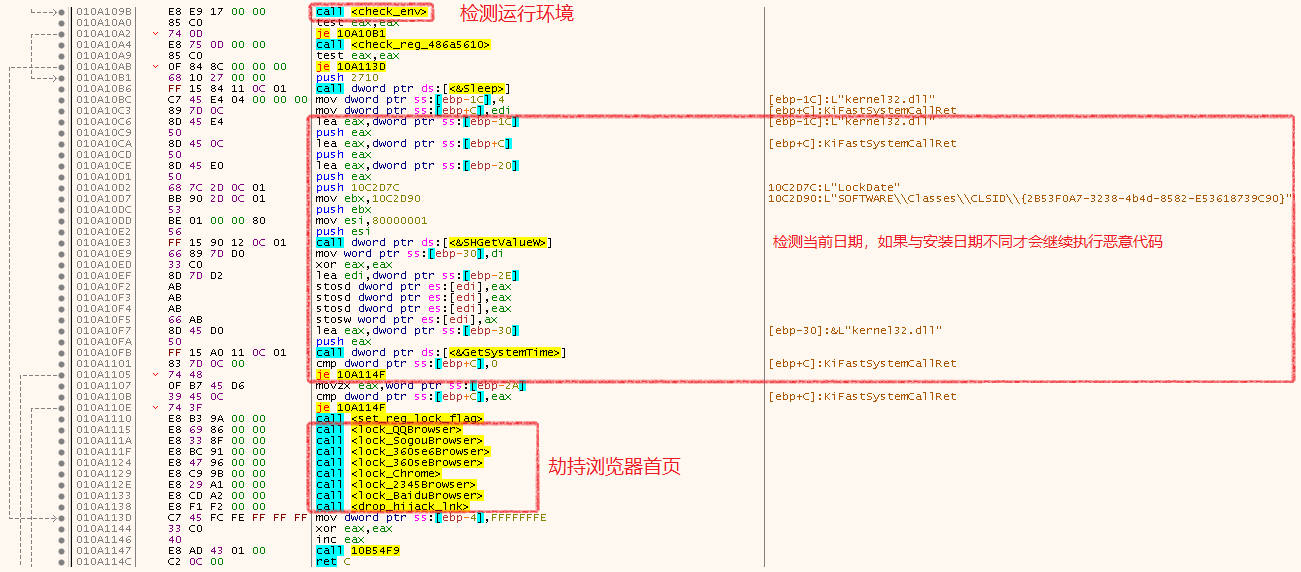
劫持浏览器首页代码逻辑
与代码相关数据,如下图所示:

远程恶意代码数据
恶意代码执行后,恶意代码逻辑会通过修改浏览器配置的方式劫持浏览器首页,并释放带有推广计费号的快捷方式。受影响的浏览器列表,如下图所示:
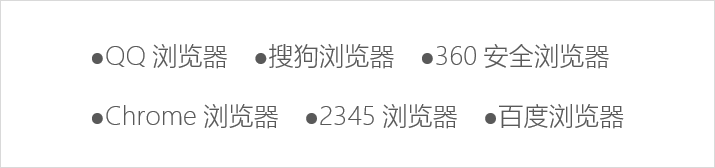
受影响的浏览器列表
恶意代码执行后,被释放的快捷方式。如下图所示:
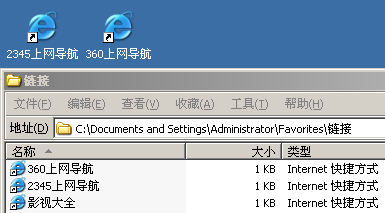
被释放的快捷方式
恶意代码对进程和注册表的检测,主要针对反病毒工具的进程名、注册表项,一旦检测到环境中存在上述进程或注册表,则会直接退出恶意代码执行流程。相关代码逻辑,如下图所示:
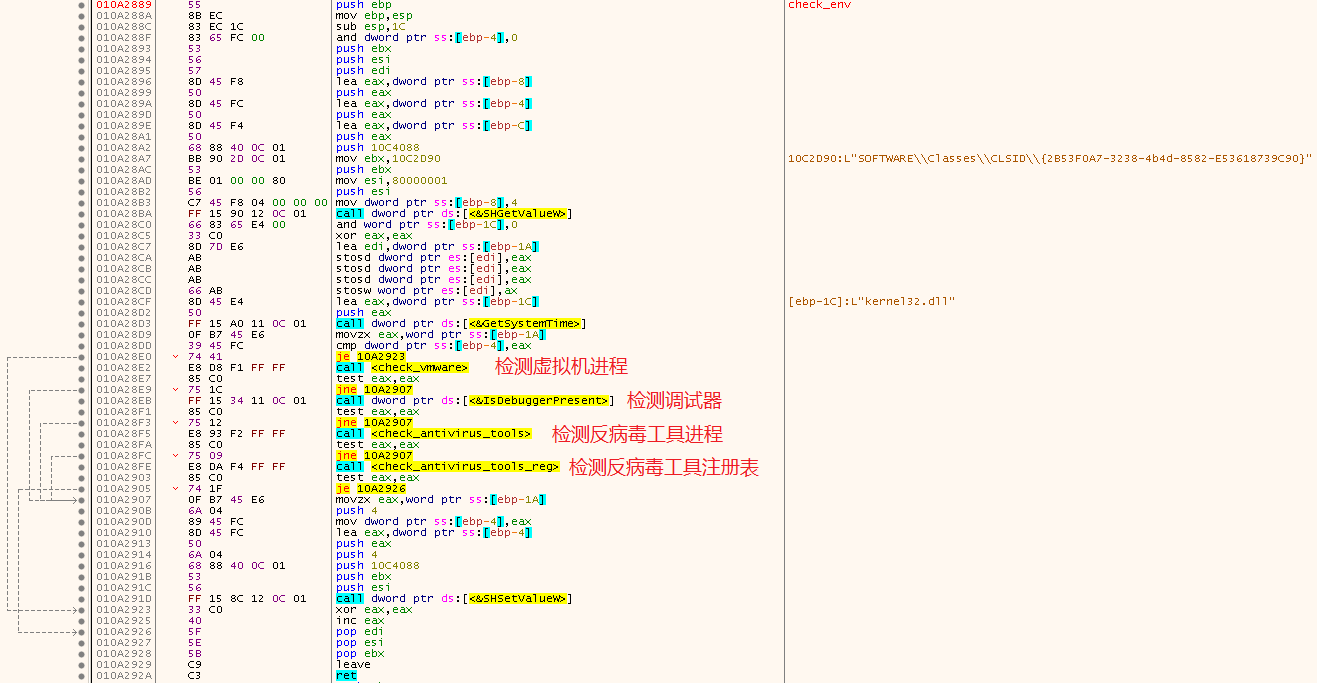
检测代码
被检测的进程名(其中vmware为子串),如下图所示:

被检测的进程名
被检测的注册表项,如下图所示:
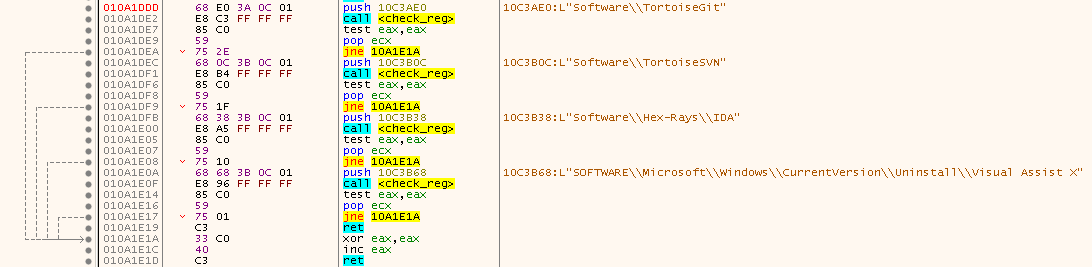
被检测的注册表项
通过我们根据域名hxxp://ee7K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3u0S2K9h3c8#2i4K6u0V1K9r3!0E0k6g2)9J5k6h3y4G2L8g2!0q4z5q4!0n7c8W2)9&6b7W2!0q4z5q4!0m8x3g2)9^5b7#2!0q4y4W2!0n7b7g2!0m8c8W2!0q4y4W2!0n7b7g2)9&6x3q4!0q4y4g2)9^5z5q4)9^5y4W2!0q4y4W2)9&6c8g2)9&6x3q4!0q4c8W2!0n7b7#2)9^5b7#2!0q4y4W2)9^5z5q4)9&6x3g2!0q4y4q4!0n7b7W2!0m8b7#2!0q4y4g2)9^5c8W2)9&6x3g2!0q4y4#2)9^5c8g2!0n7x3q4!0q4y4g2!0n7z5q4!0m8y4W2!0q4y4W2)9&6b7#2)9^5z5g2!0q4y4#2)9&6b7W2!0n7z5q4!0q4y4g2)9&6x3q4)9^5b7#2!0q4y4W2)9^5x3g2!0n7y4W2!0q4y4W2)9^5y4q4)9^5c8W2!0q4y4q4!0n7b7W2!0m8x3#2!0q4y4#2!0m8x3q4)9^5x3g2!0q4z5g2)9^5x3q4!0n7b7W2!0q4z5q4!0n7c8g2)9&6x3g2!0q4y4#2)9&6b7g2)9^5y4q4!0q4z5q4!0n7c8q4!0m8c8W2!0q4y4q4!0n7b7W2!0n7y4W2!0q4y4q4!0n7z5q4)9^5c8q4!0q4y4W2!0m8c8q4!0m8x3W2!0q4y4q4!0n7z5q4)9^5x3q4!0q4y4q4!0n7z5q4!0m8b7g2!0q4x3#2)9^5x3q4)9^5x3W2!0q4y4g2!0n7z5q4!0m8y4W2!0q4y4W2)9&6b7#2)9^5z5g2!0q4y4#2)9&6b7W2!0n7z5q4!0q4y4g2)9&6x3q4)9^5b7#2!0q4y4q4!0n7b7W2!0m8x3#2!0q4y4#2!0m8x3q4)9^5x3g2!0q4z5g2)9^5x3q4!0n7b7W2!0q4z5q4!0n7c8g2)9&6x3g2!0q4z5q4!0n7c8q4!0m8c8W2!0q4y4q4!0n7b7W2!0n7y4W2!0q4c8W2!0n7b7#2)9^5b7#2!0q4y4g2!0m8y4W2)9^5x3W2!0q4y4q4!0n7z5q4)9^5b7W2!0q4y4g2)9&6b7W2!0n7c8g2!0q4y4W2)9^5z5g2)9^5x3q4!0q4y4#2!0m8y4q4!0n7b7g2!0q4c8W2!0n7b7#2)9&6b7b7`.`.

带有相同恶意代码的软件
以PDF转WORD超级转化器为例。同源代码,如下图所示:
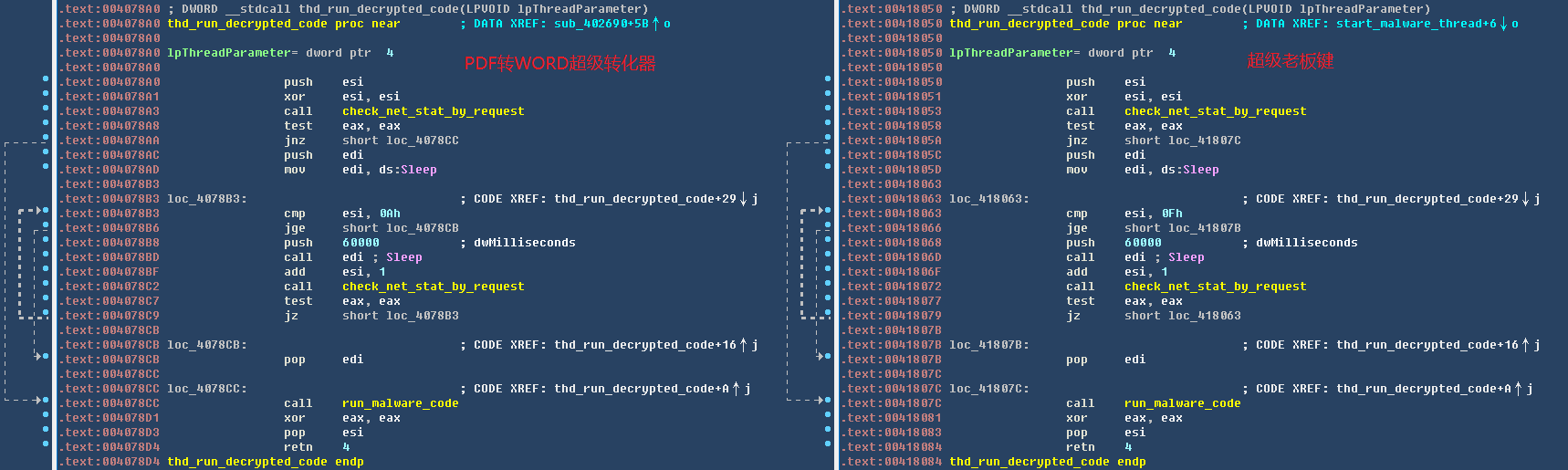
同源性代码
三、 附录
文中涉及样本SHA256:

PDF下载:301K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3c8G2N6$3^5@1i4K6u0W2K9s2g2G2M7X3!0F1k6#2)9J5k6h3y4F1i4K6u0r3k6r3!0U0i4K6u0r3M7X3g2H3L8%4u0@1i4K6u0r3K9s2g2E0M7r3I4W2M7W2)9J5k6i4m8V1k6R3`.`.
[培训]科锐逆向工程师培训第53期2025年7月8日开班!
最后于 2019-6-6 12:48
被tonite编辑
,原因: