-
-
[原创]实战分析43XX的HTTPS协议
-
发表于:
2020-12-8 17:36
3585
-
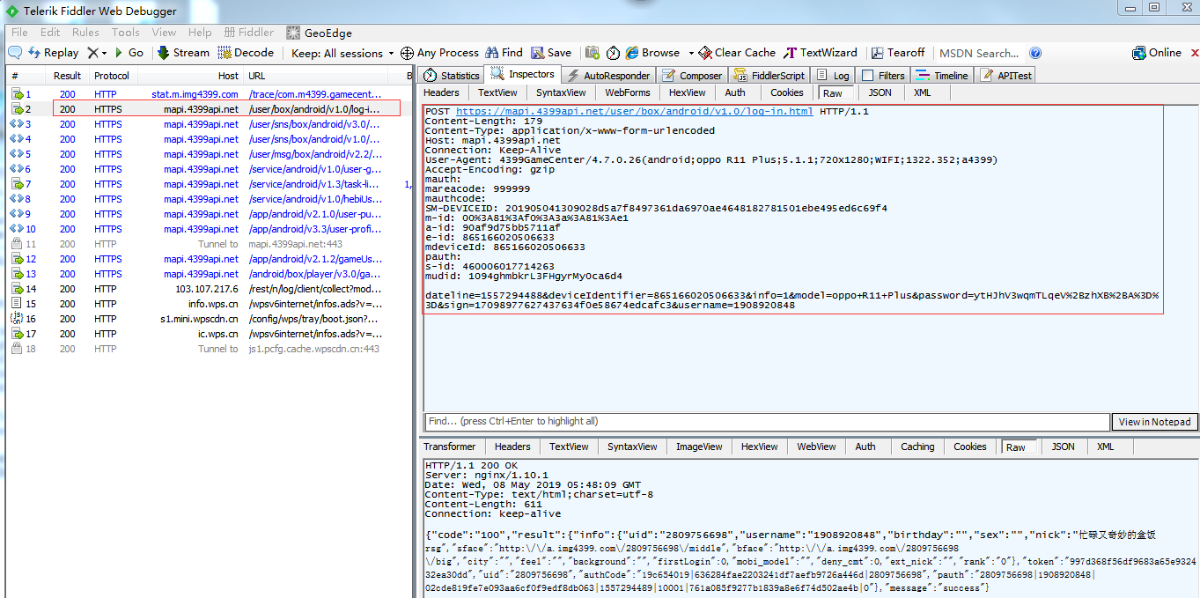
第一次抓包:
POST 649K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0j5i4m8A6i4K6u0W2y4o6x3&6z5h3q4H3K9g2)9J5k6h3&6W2N6q4)9J5c8Y4g2K6k6i4u0Q4x3V1k6T1L8%4S2Q4x3V1k6S2L8X3c8J5L8$3W2V1i4K6u0r3N6U0q4Q4x3X3f1H3i4K6u0r3L8r3!0Y4i4K6u0V1K9h3&6Q4x3X3g2Z5N6r3#2D9 HTTP/1.1
Content-Length: 179
Content-Type: application/x-www-form-urlencoded
Host: mapi.4399api.net
Connection: Keep-Alive
User-Agent: 4399GameCenter/4.7.0.26(android;oppo R11
Plus;5.1.1;720x1280;WIFI;1322.352;a4399)
Accept-Encoding: gzip
mauth:
mareacode: 999999
mauthcode:
SM-DEVICEID: 201905041309028d5a7f8497361da6970ae4648182
781501ebe495ed6c69f4
m-id: 00%3A81%3Af0%3A3a%3A81%3Ae1
a-id: 90af9d75bb5711af
e-id: 865166020506633
mdeviceId: 865166020506633
pauth:
s-id: 460006017714263
mudid: 1094ghmbkrL3FHgyrMy0ca6d4
dateline=1557294373&deviceIdentifier=865166020506633&info=1&
model=oppo+R11+Plus&password=ytHJhV3wqmTLqeV%2BzhXB%2BA%3D%3D&
sign=8d86292d44242171706dbb86878c5fef&username=1908920848
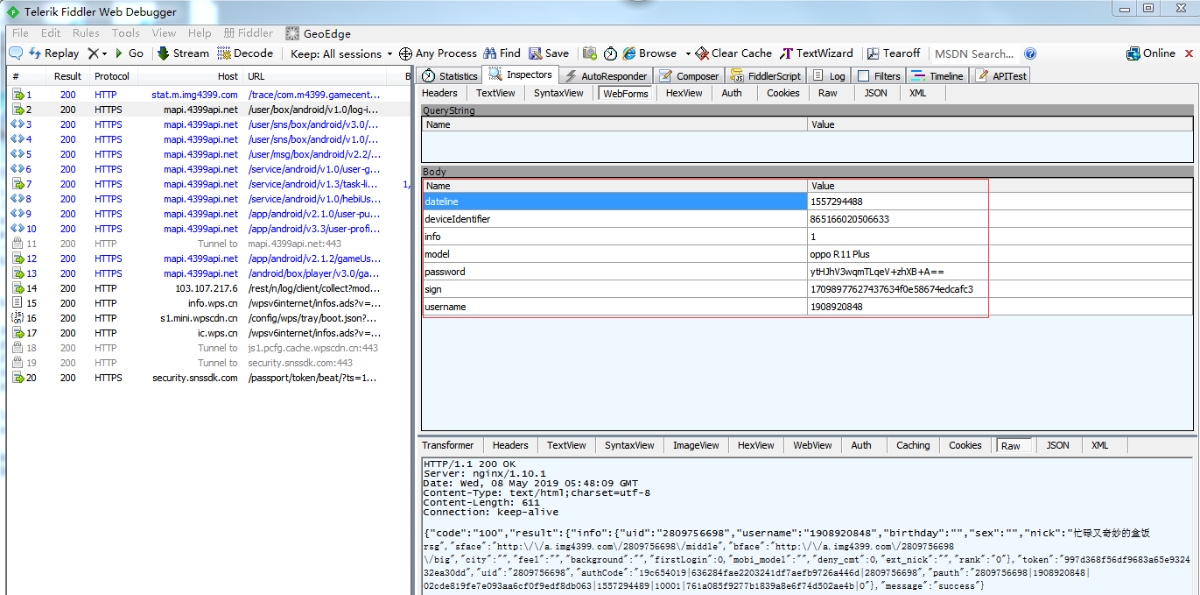
第二次抓包:
POST f5fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0j5i4m8A6i4K6u0W2y4o6x3&6z5h3q4H3K9g2)9J5k6h3&6W2N6q4)9J5c8Y4g2K6k6i4u0Q4x3V1k6T1L8%4S2Q4x3V1k6S2L8X3c8J5L8$3W2V1i4K6u0r3N6U0q4Q4x3X3f1H3i4K6u0r3L8r3!0Y4i4K6u0V1K9h3&6Q4x3X3g2Z5N6r3#2D9 HTTP/1.1
Content-Length: 179
Content-Type: application/x-www-form-urlencoded
Host: mapi.4399api.net
Connection: Keep-Alive
User-Agent: 4399GameCenter/4.7.0.26(android;oppo R11
Plus;5.1.1;720x1280;WIFI;1322.352;a4399)
Accept-Encoding: gzip
mauth:
mareacode: 999999
mauthcode:
SM-DEVICEID: 201905041309028d5a7f8497361da6970ae464818278
1501ebe495ed6c69f4
m-id: 00%3A81%3Af0%3A3a%3A81%3Ae1
a-id: 90af9d75bb5711af
e-id: 865166020506633
mdeviceId: 865166020506633
pauth:
s-id: 460006017714263
mudid: 1094ghmbkrL3FHgyrMy0ca6d4
dateline=1557294488&deviceIdentifier=865166020506633&info=1&
model=oppo+R11+Plus&password=ytHJhV3wqmTLqeV%2BzhXB%2BA%3D%3D&
sign=17098977627437634f0e58674edcafc3&username=1908920848
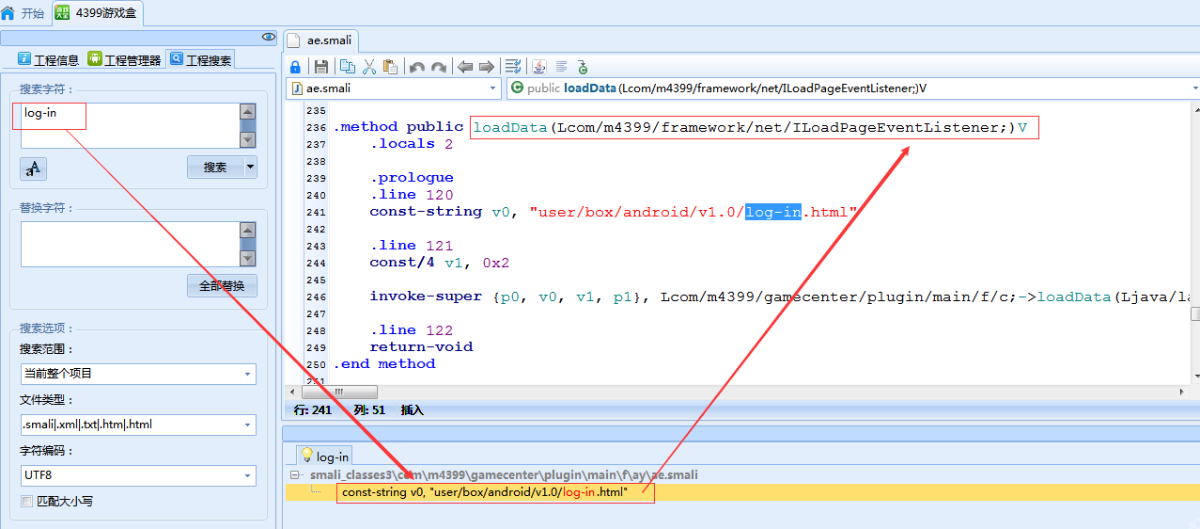
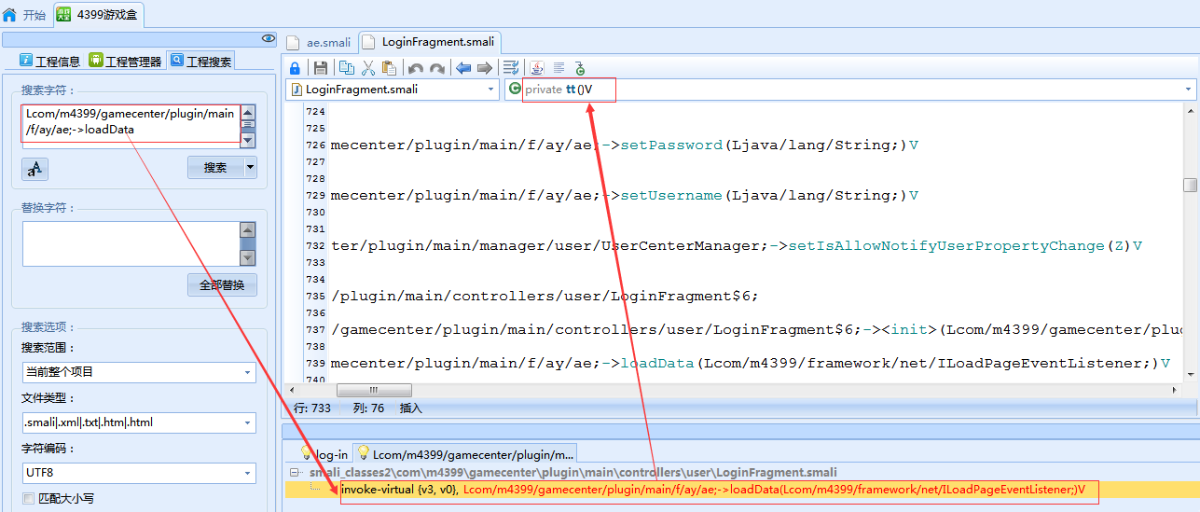
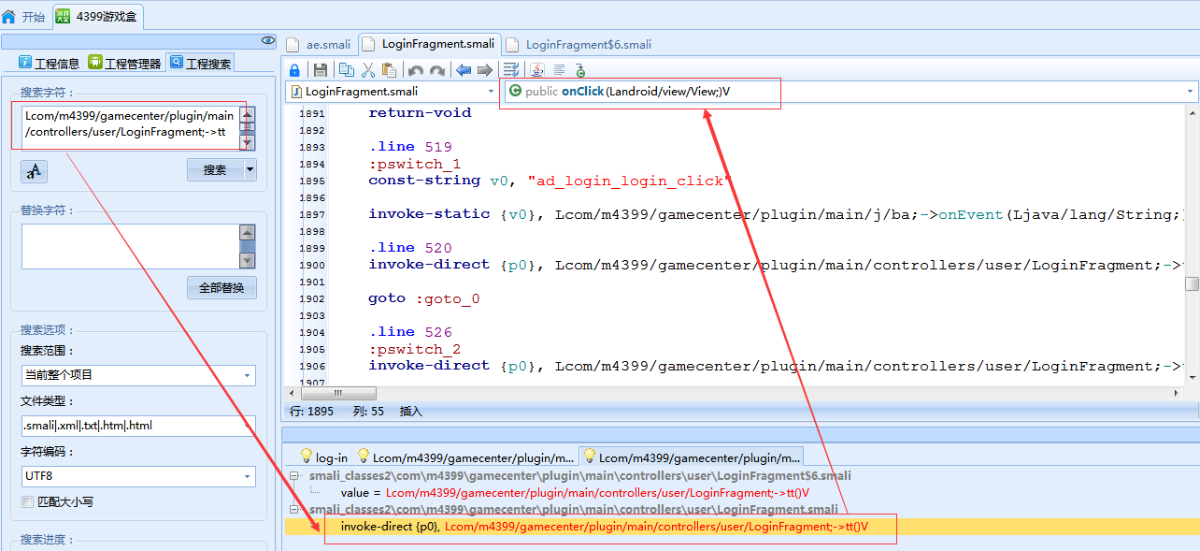
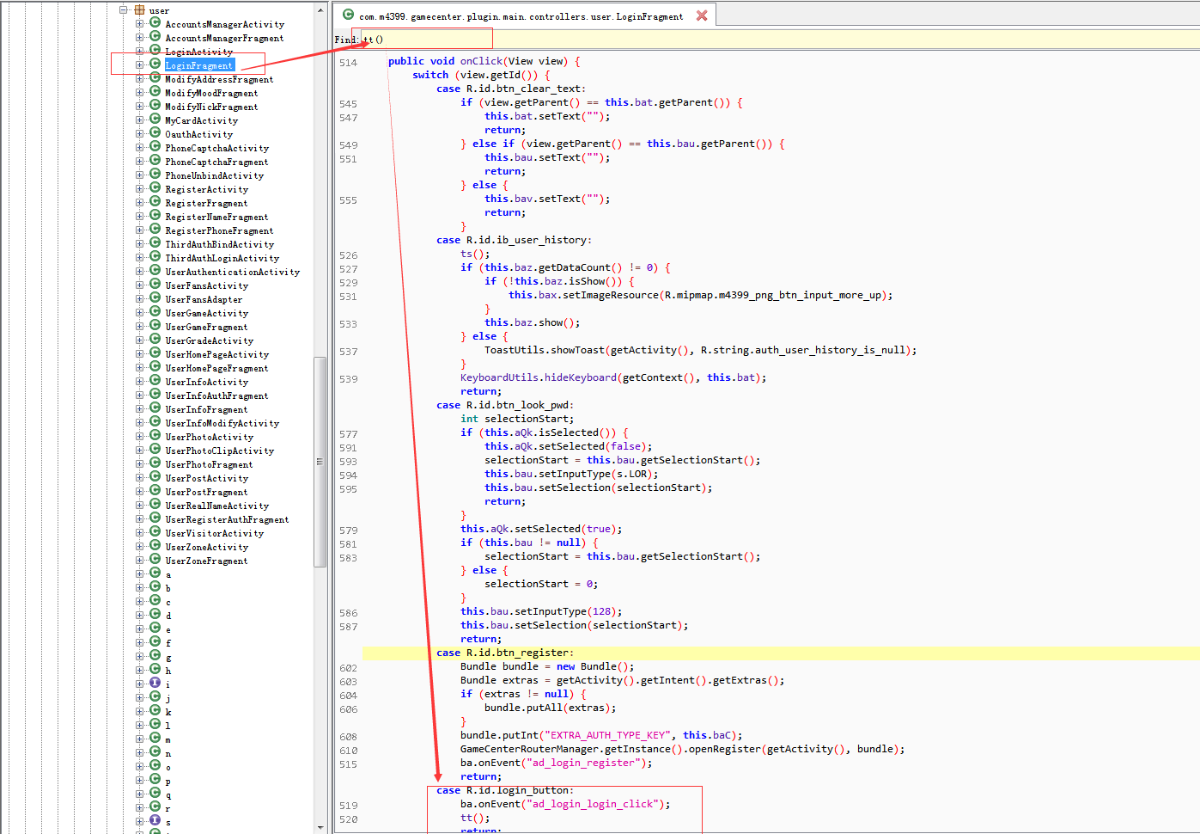
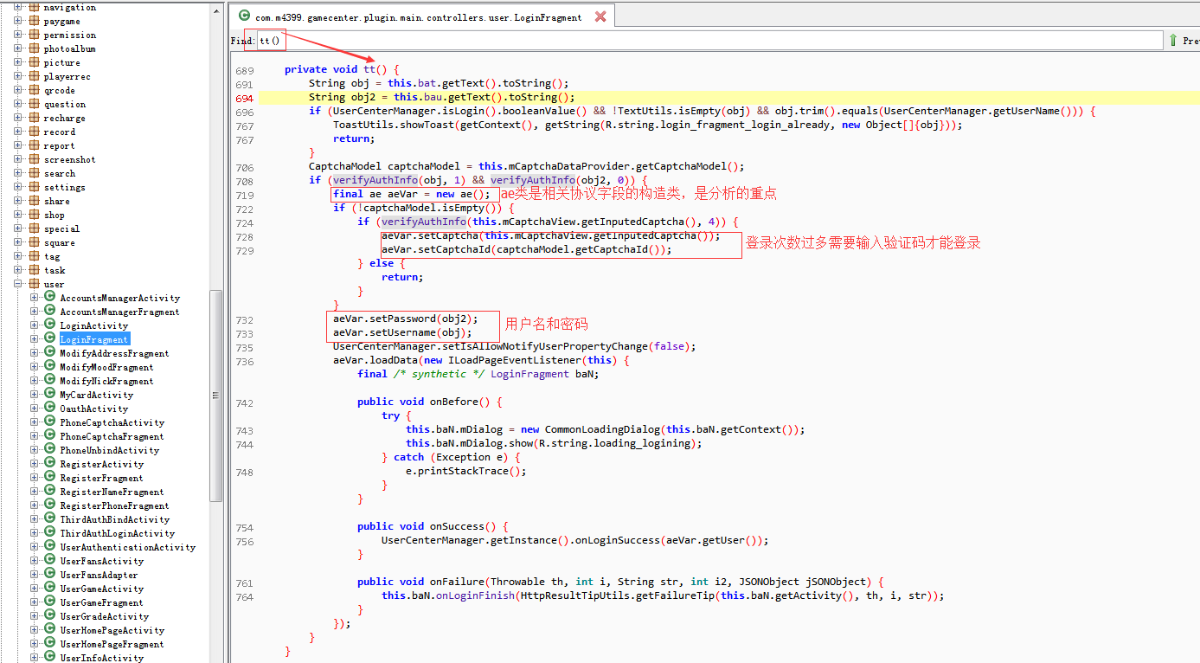
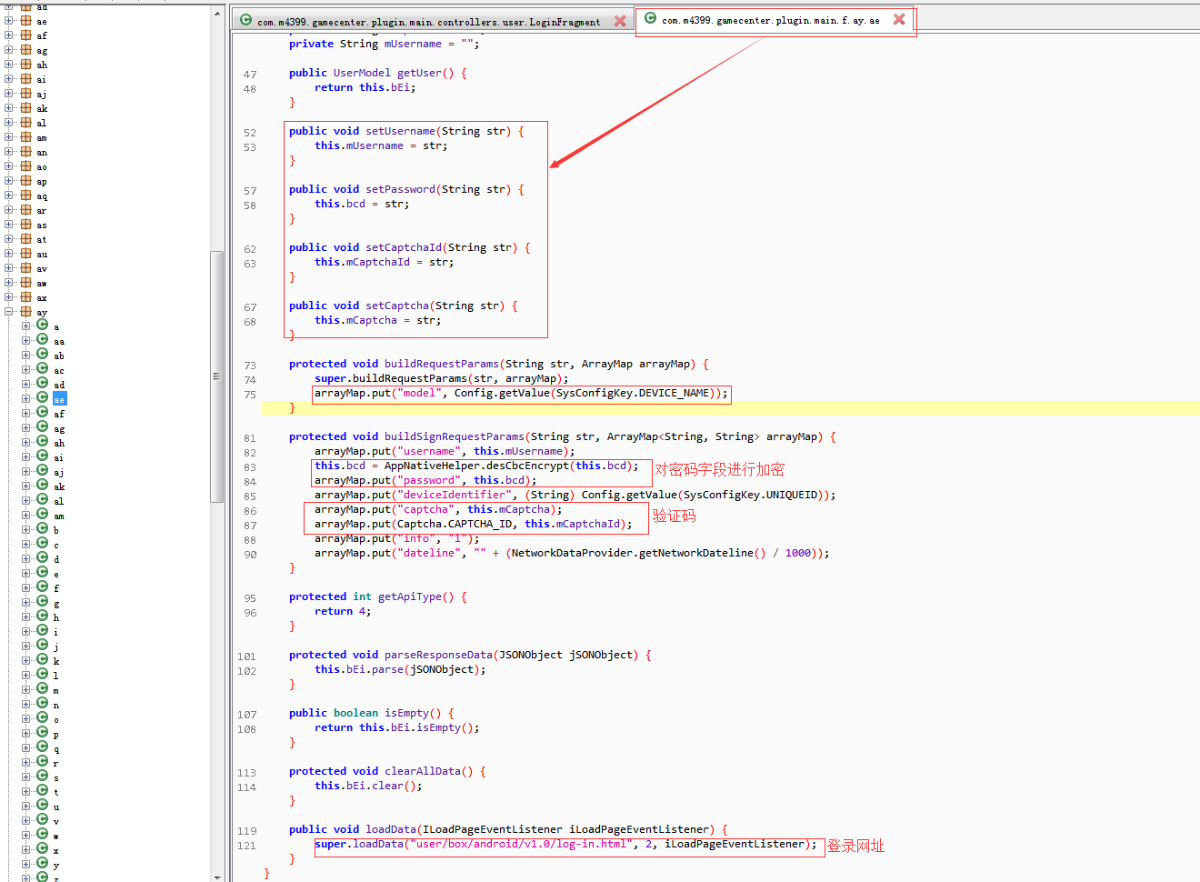
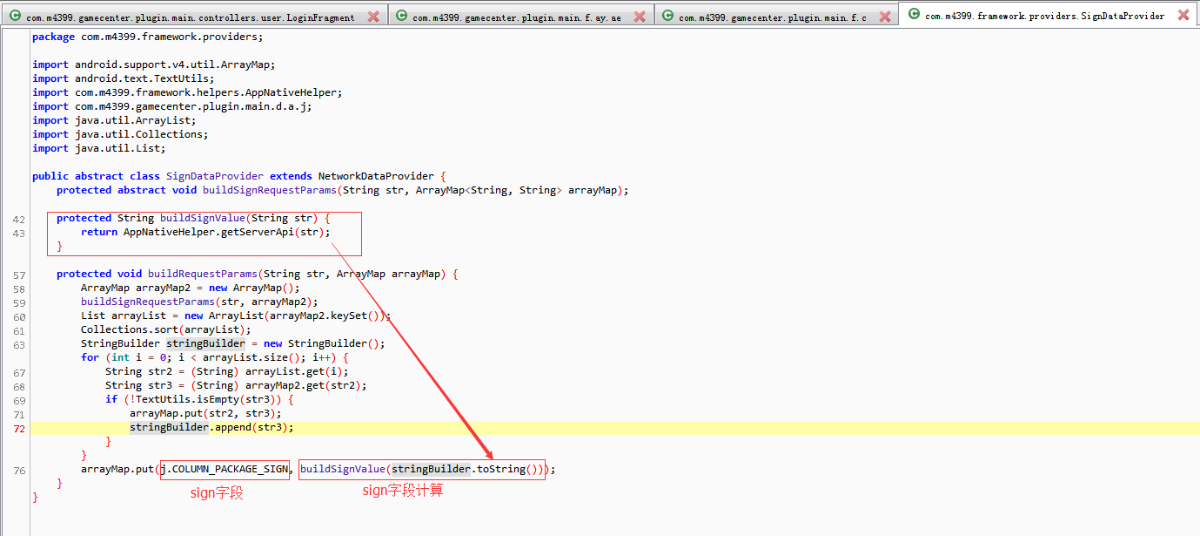
除了”sign”这个字段,其他字段都找到了。”sign”字段就在当前类的附近,通过com.m4399.gamecenter.plugin.main.f.ay.ae类的基类(com.m4399.gamecenter.plugin.main.f.c)发现一个非常可疑的类(com.m4399.framework.providers.SignDataProvider),点击进去发现该类有一个方法(buildRequestParams)正是计算”sign”字段的值。
调试模启动式
adb shell am start -D -n com.m4399.gamecenter/.controllers.splash.SplashActivity
端口转发
adb forward tcp:8700 jdwp:2561
出现这个错误说明8700端口被占用
error: cannot bind listener: cannot bind to 127.0.0.1:8700: 通 常每个套接字地址(协议/网络地址/端口)只允许使用一次。 (10048)
解决办法
netstat -nao | findstr "8700"
根据PID找到该进程,结束进程
打开任务管理器—>查看—>选项列(S)—>勾选 PID,确定—>进程按钮栏
1、抓包分析43XX的登录协议,两次抓包,对比哪些字段发生了变化,重点分析变化字段。
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课