-
-
[原创]QQ游戏外挂收集色情文件 火绒提示切勿使用
-
-
[原创]QQ游戏外挂收集色情文件 火绒提示切勿使用
【快讯】
近期,火绒工程师根据用户反馈,发现一款名为“QQ游戏智能机器人”的外挂程序,会针对广大游戏玩家,搜集和回传隐私数据,包括带有色情相关关键字的文件及含密码、账号、通信录、笔记等关键字的文件,被搜集的文件类型包括文档、图片、视频等。火绒用户无需担心,火绒安全软件已对该木马程序进行拦截查杀。
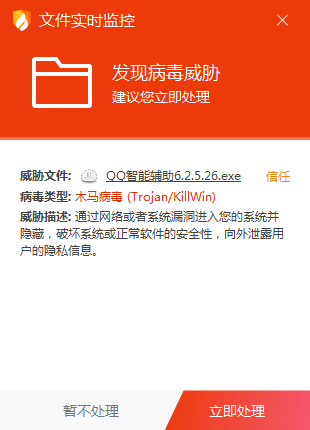
通过分析发现,该木马程序制作者通过云控会将任意QQ号列入黑名单,并删除其大量文件。除此之外,提供该木马程序的下载站,甚至会提醒用户“个别杀软误报本软件,请不要相信,本软件不是病毒木马,运行辅助前请请先退出杀软“。
游戏玩家受众较广,从事网络游戏外挂黑产的团队随之增多,市面上流通的外挂软件种类也不断增加。这类灰色程序软件,通常会携带各类病毒,威胁用户安全。火绒工程师提醒大家,请谨慎下载不明软件,如需下载应用软件请通过正规官网链接,并使用火绒及时查杀;如果必须使用某些不明程序,可以提前开启安全软件进行扫描、查杀,或者前往火绒论坛求助,确保文件、程序安全后再运行,以免遭遇风险。
附:【分析报告】
一、详细报告
近期根据用户反馈,在运行“QQ游戏智能机器人”程序之后,电脑中出现大量文件被删除的现象,恶意程序相关主页hxxp://78cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4q4I4k6Y4A6F1i4K6u0W2j5$3!0E0i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1%4i4@1u0n7i4K6S2r3i4@1f1^5i4@1u0r3i4K6R3%4i4@1f1#2i4K6R3^5i4K6R3$3i4@1f1$3i4K6W2q4i4K6V1H3i4@1f1#2i4K6S2r3i4K6V1I4i4@1f1%4i4K6S2q4i4@1t1H3i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1^5i4@1q4r3i4@1p5#2i4@1f1$3i4@1p5^5i4@1p5I4i4@1f1#2i4K6W2p5i4K6V1%4i4@1f1#2i4K6S2o6i4K6R3#2i4@1f1#2i4K6V1H3i4@1q4n7i4@1f1@1i4@1u0m8i4K6V1I4i4@1f1$3i4K6S2q4i4@1p5%4i4@1f1@1i4@1t1^5i4K6S2m8i4@1f1@1i4@1u0o6i4@1p5H3i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1@1i4@1u0n7i4@1p5#2i4@1f1#2i4K6S2r3i4K6S2m8i4@1f1#2i4K6R3^5i4@1p5H3i4@1f1&6i4K6V1&6i4@1p5@1i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1&6i4K6R3H3i4@1u0n7i4@1f1^5i4@1u0q4i4K6V1I4i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1#2i4@1u0p5i4K6V1K6i4@1f1%4i4K6V1@1i4@1p5^5i4@1f1$3i4K6R3^5i4@1t1%4i4@1f1@1i4@1u0p5i4@1u0r3i4@1f1%4i4K6V1@1i4@1p5^5i4@1f1^5i4@1q4r3i4@1p5#2i4@1f1^5i4@1u0p5i4@1q4r3i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1$3i4K6V1%4i4@1t1$3i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1@1i4@1u0q4i4@1u0r3i4@1f1@1i4@1u0o6i4K6W2m8i4@1f1$3i4@1p5H3i4@1t1&6i4@1f1$3i4K6S2p5i4@1q4q4i4@1f1&6i4K6R3#2i4K6S2p5i4@1f1%4i4@1u0p5i4@1q4q4i4@1f1@1i4@1t1^5i4K6S2m8i4@1f1@1i4@1u0o6i4@1p5H3i4@1f1$3i4K6S2o6i4K6R3%4i4@1f1#2i4@1q4q4i4K6W2m8i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1g2r3i4@1u0o6i4K6R3^5i4@1f1@1i4@1t1^5i4K6S2m8i4@1f1@1i4@1u0o6i4@1p5H3i4@1f1#2i4@1u0o6i4K6R3H3i4@1f1#2i4K6R3#2i4@1t1K6i4@1f1$3i4K6W2m8i4K6R3J5i4@1f1$3i4K6W2o6i4@1q4m8i4@1f1#2i4@1u0o6i4K6R3H3i4@1f1#2i4K6V1H3i4@1q4r3i4@1g2r3i4@1u0o6i4K6R3&6i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1#2i4K6V1H3i4K6S2o6i4@1f1$3i4K6V1%4i4@1t1$3i4@1f1#2i4@1u0p5i4K6V1K6i4@1f1%4i4K6V1@1i4@1p5^5i4@1f1$3i4K6R3^5i4@1t1%4f1g2q4Q4c8e0g2Q4z5p5k6Q4b7U0N6Q4c8e0k6Q4z5o6S2Q4z5e0k6Q4c8e0N6Q4z5o6u0Q4b7U0W2Q4c8e0g2Q4z5p5c8Q4b7e0q4Q4c8e0g2Q4z5p5c8Q4b7e0q4Q4c8e0g2Q4z5p5k6Q4b7U0N6Q4c8e0g2Q4z5f1y4Q4b7e0S2Q4c8e0S2Q4b7f1k6Q4b7e0g2Q4c8e0N6Q4z5e0N6Q4z5o6g2Q4c8e0k6Q4b7f1k6Q4z5e0u0Q4c8e0W2Q4z5o6g2Q4z5p5c8Q4c8e0N6Q4b7V1c8Q4b7f1g2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0W2Q4b7V1u0Q4z5e0q4Q4c8e0g2Q4z5e0m8Q4z5p5c8Q4c8e0g2Q4z5p5c8Q4z5e0g2Q4c8e0c8Q4b7U0S2Q4b7f1c8Q4c8e0k6Q4z5e0N6Q4b7U0k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7V1g2Q4b7V1k6Q4c8e0c8Q4b7V1y4Q4z5f1q4Q4c8e0W2Q4z5o6q4Q4z5p5c8Q4c8e0g2Q4z5p5g2Q4z5o6k6Q4c8e0N6Q4b7e0y4Q4z5o6q4Q4c8e0N6Q4z5f1u0Q4z5e0S2Q4c8e0g2Q4z5o6S2Q4b7e0m8Q4c8e0W2Q4z5e0W2Q4b7e0c8Q4c8e0N6Q4z5e0c8Q4b7e0S2Q4c8e0k6Q4z5o6S2Q4b7U0N6Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4z5e0k6Q4z5o6N6Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8e0y4Q4z5o6m8Q4z5o6u0Q4c8e0S2Q4b7V1c8Q4b7f1k6Q4c8e0c8Q4b7V1u0Q4b7U0k6Q4c8e0N6Q4z5e0g2Q4z5p5y4Q4c8e0W2Q4z5f1c8Q4b7e0u0Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7e0k6Q4z5o6u0Q4c8e0c8Q4b7U0S2Q4z5p5u0Q4c8e0g2Q4z5f1u0Q4b7V1g2Q4c8e0k6Q4z5o6W2Q4z5o6m8Q4c8e0N6Q4b7e0c8Q4b7V1q4Q4c8f1k6Q4b7V1y4Q4z5f1p5`.
软件界面
病毒会从C&C服务器(hxxp://9c6K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6h3u0K6k6h3q4K6i4K6u0W2j5$3!0E0i4K6u0r3M7$3#2Q4x3V1k6I4j5U0k6Q4x3V1k6C8i4K6u0W2P5r3#2D9i4@1g2r3i4@1u0o6i4K6R3&6i4@1f1^5i4@1q4r3i4@1t1%4i4@1f1$3i4@1t1I4i4K6R3J5i4@1f1&6i4K6R3#2i4K6S2p5i4@1f1%4i4@1u0p5i4@1q4q4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1&6i4K6R3%4i4K6S2o6i4@1f1&6i4K6W2p5i4@1p5J5i4@1f1#2i4K6S2o6i4K6R3#2i4@1f1#2i4K6V1H3i4@1q4n7i4@1f1#2i4K6S2p5i4K6R3%4i4@1f1%4i4@1u0m8i4@1p5%4i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1&6i4@1u0n7i4K6V1I4i4@1f1#2i4K6V1H3i4K6S2p5i4@1f1#2i4K6S2p5i4K6V1#2i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1@1i4@1t1^5i4K6S2m8i4@1f1@1i4@1u0o6i4@1p5H3i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1&6i4K6R3#2i4K6S2p5i4@1f1%4i4@1u0p5i4@1q4q4i4@1f1%4i4@1q4p5i4K6R3&6i4@1f1@1i4@1u0r3i4@1p5I4i4@1f1$3i4K6R3I4i4@1q4r3i4@1f1K6i4K6R3H3i4K6R3J5i4@1f1&6i4K6R3K6i4@1p5^5i4@1f1#2i4K6R3^5i4K6R3$3i4@1f1&6i4K6R3#2i4K6S2p5i4@1f1%4i4@1u0p5i4@1q4q4i4@1f1$3i4K6V1$3i4K6R3%4i4@1f1@1i4@1u0n7i4@1t1$3i4@1f1#2i4K6R3$3i4K6R3#2i4@1f1#2i4@1q4q4i4@1t1&6i4@1g2r3i4@1u0o6i4K6S2o6i4@1f1#2i4@1p5$3i4K6R3J5i4@1f1@1i4@1t1^5i4K6S2n7i4@1f1#2i4K6W2n7i4@1u0q4i4@1f1$3i4K6R3&6i4K6R3H3i4@1f1%4i4@1p5@1i4@1u0m8i4@1g2r3i4@1u0o6i4K6W2m8
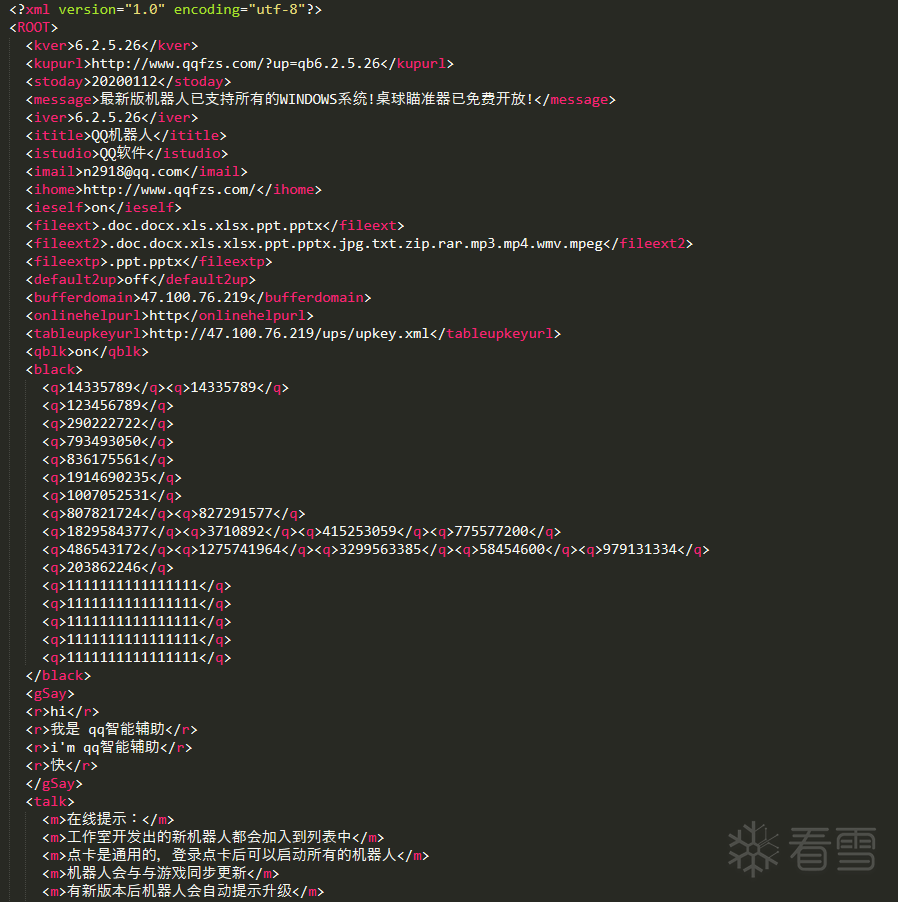
配置文件
病毒通过遍历QQ UserDataSavePath目录的方式获得用户机器上登录过的QQ号,如果用户QQ账号或点卡卡号在黑名单中,那么病毒便会遍历磁盘,删除除了后缀名为.exe、.dll、.sys、.ini、.txt、.db、.lnk、.log以及配置文件中fileextp字段后缀名以外的文件。相关代码,如下图所示:
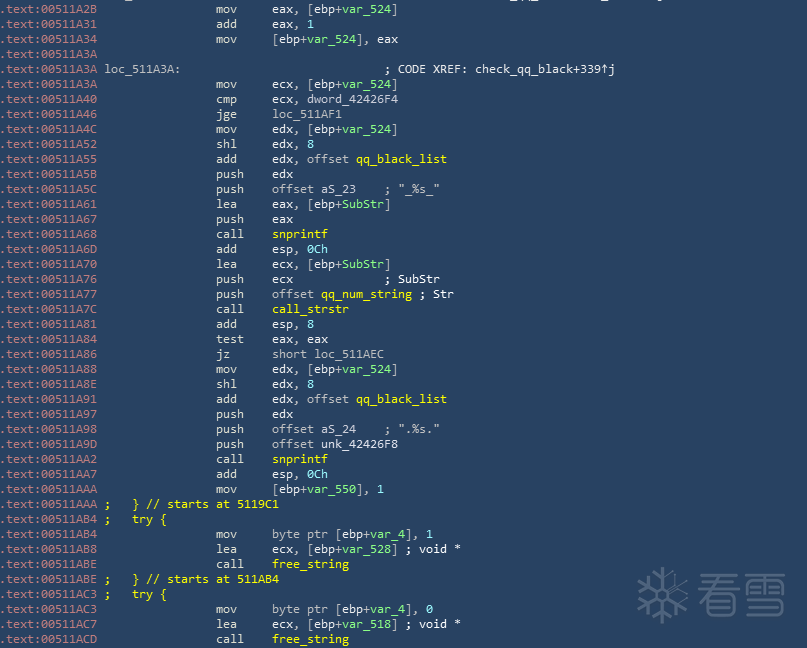
检查用户QQ是否在黑名单中
除此之外,恶意程序还会根据上传配置中fileext和fileext2字段,遍历上传扩展名为.doc、.docx、.xls、.xlsx、.ppt、.pptx、.jpg、.txt、.zip、.rar、.mp4、.wmv、.mpeg的文件(且上传文件大小需小于16M)。tryflag字段为尝试上传用户文件的开关,根据火绒现阶段请求结果,该开关暂为关闭状态。相关逻辑代码如下图所示:
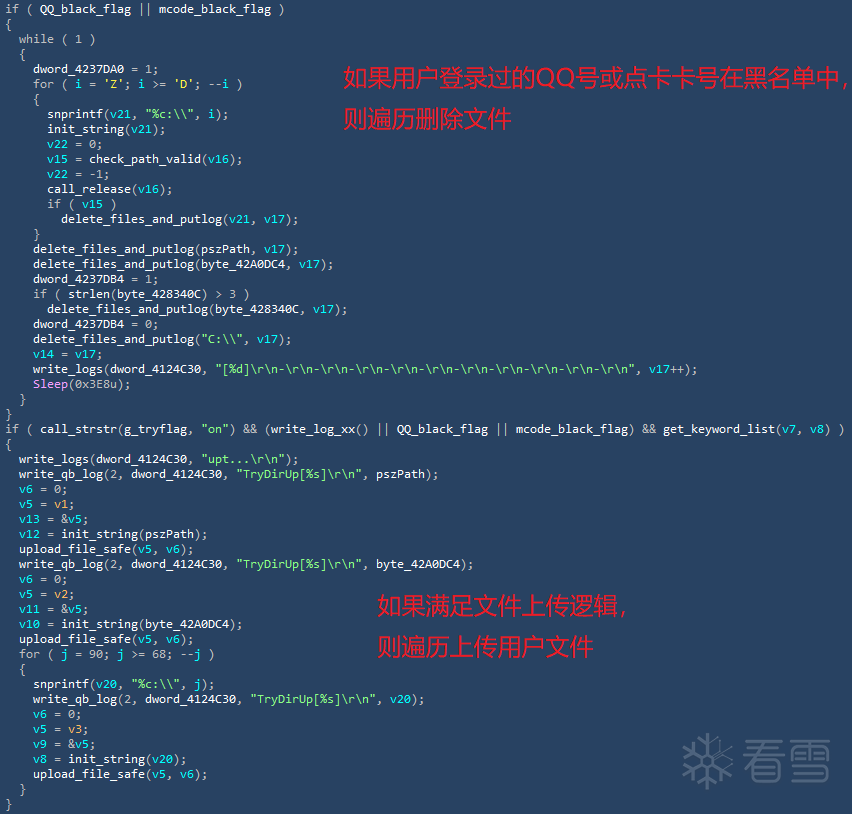
遍历磁盘删除文件及上传指定后缀名文件相关逻辑
文件上传时,恶意代码会判断文件名中是否带有指定的关键字(yeskey上传文件关键、nokey为禁止上传的关键字)。上传文件控制关键字列表,如下图所示:
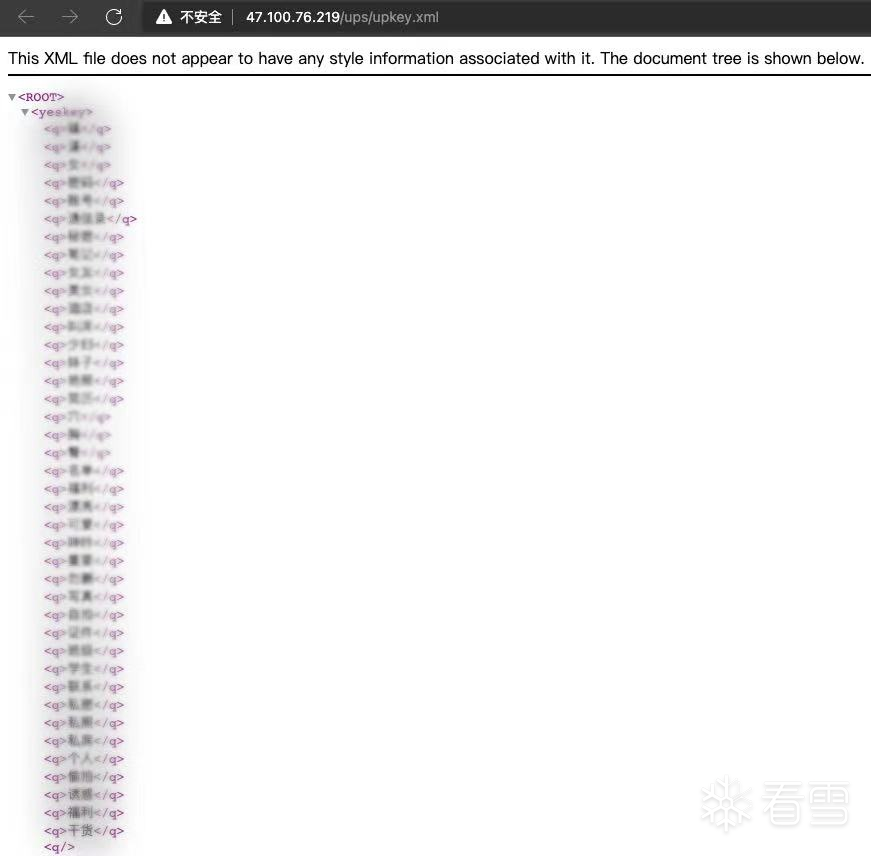
上传文件控制关键字列表
禁止上传的控制关键字列表,如下图所示:
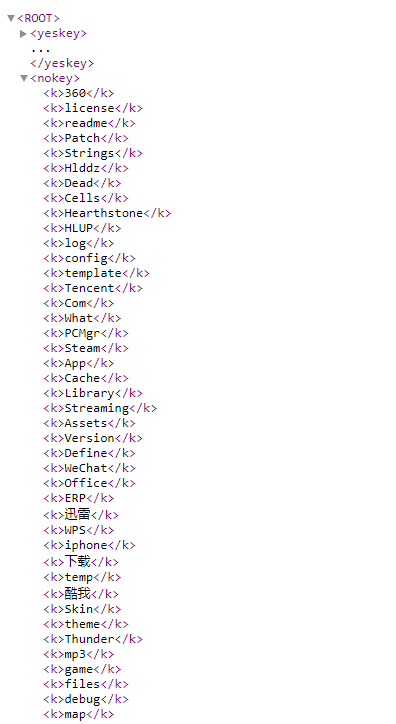
禁止上传的控制关键字列表
文件上传相关代码逻辑,如下图所示:
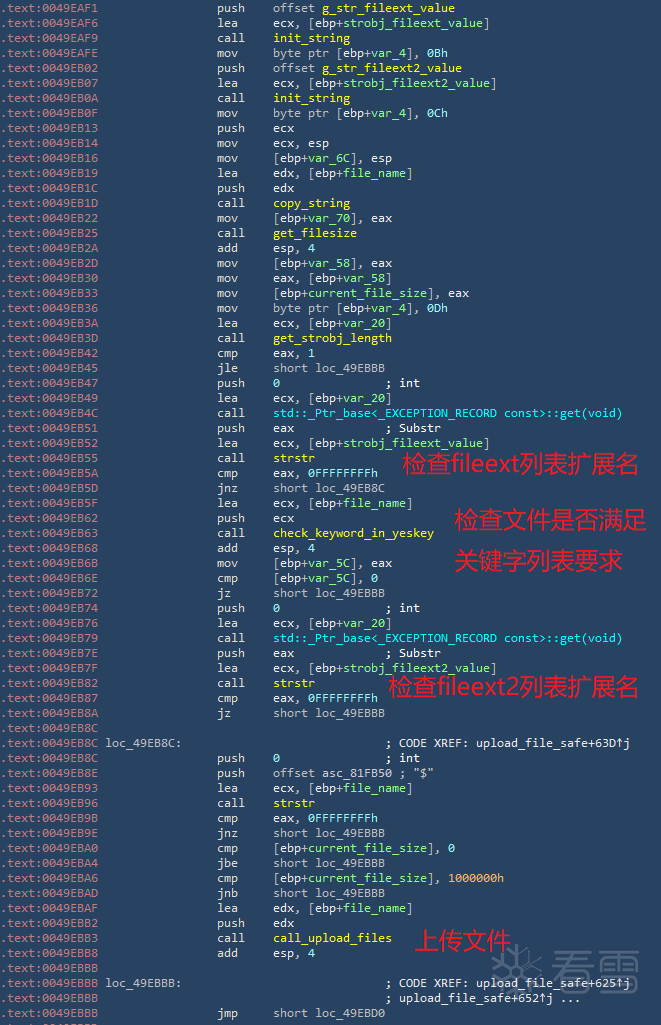
文件上传相关代码逻辑
二、附录
病毒hash
[培训]科锐逆向工程师培训第53期2025年7月8日开班!