-
-
未解决
[求助]如何分析这种NSIS病毒?
50.00雪花
-
-
未解决 [求助]如何分析这种NSIS病毒?
50.00雪花
这是一个修改过的nsis邮箱附件后门恶意文件
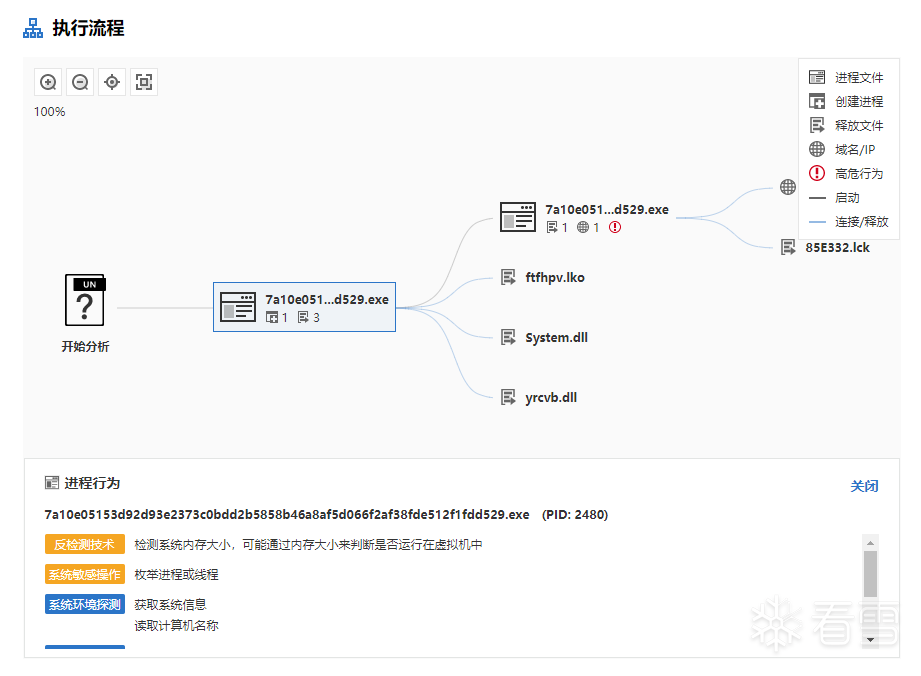

如上图,该病毒第一次启动与自己调用自己时加载了两套不同的dll。
但是在OD与IDA中只有第一次启动的相关dll加载与实现代码,没找到任何与第二个线程相关的代码与调用。。。
请问这种情况该怎么做才能找到第二个线程中恶意行为的代码?
微步沙箱:643K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6K6i4K6u0W2N6r3S2J5k6h3q4@1j5X3!0G2K9#2)9J5k6h3y4F1i4K6u0r3M7X3g2H3L8%4u0@1i4K6u0r3k6X3W2D9k6g2)9J5c8U0N6S2x3e0m8W2x3o6f1I4y4e0y4V1z5e0u0V1z5e0y4W2x3U0x3%4x3$3x3H3j5X3c8V1x3X3t1#2z5o6f1^5j5U0b7$3j5e0S2S2k6U0g2V1x3o6j5$3k6U0u0S2k6U0x3^5k6X3c8W2y4e0p5J5k6U0q4X3k6r3b7#2x3U0W2Q4x3V1k6Q4x3@1k6W2L8Y4k6Q4x3@1c8%4K9h3^5%4i4K6g2X3M7%4l9I4i4K6g2X3k6h3&6^5z5o6k6Q4y4h3k6G2k6X3k6A6j5$3f1J5x3o6p5K6
VT:
0c7K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2$3K9i4u0#2M7%4c8G2N6r3q4D9i4K6u0W2j5$3!0E0i4K6u0r3k6%4g2A6i4K6u0r3k6X3W2D9k6g2)9J5c8U0N6S2x3e0m8W2x3o6f1I4y4e0y4V1z5e0u0V1z5e0y4W2x3U0x3%4x3$3x3H3j5X3c8V1x3X3t1#2z5o6f1^5j5U0b7$3j5e0S2S2k6U0g2V1x3o6j5$3k6U0u0S2k6U0x3^5k6X3c8W2y4e0p5J5k6U0q4X3k6r3b7#2x3U0W2Q4x3V1k6V1k6i4c8W2j5%4c8A6L8$3^5`.
恶意文件已压缩后放在在附件内。无后缀,不会自启动。可用7Z解包
[培训]科锐逆向工程师培训第53期2025年7月8日开班!