最近研究了一下这个,实战中还没遇到过,也可能存在只是我没发现,小记!
两个地址的协议域名端口都一样则为同源
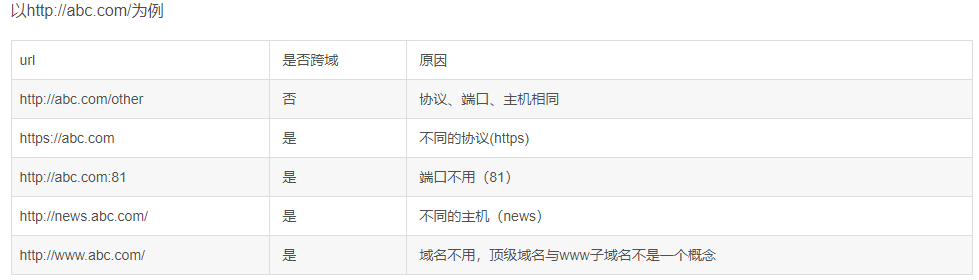

Tips:同源策略是浏览器行为,拦截的是客户端发出去的请求,该请求返回的信息,也就是请求发出去了,服务器响应了,但是无法被浏览器接收。
Tips1:同源策略只存在于浏览器端,服务器访问服务器不存在跨域问题。
不同源的客户端脚本在没有明确授权的情况下,不能读写对方资源。只有同一个源的脚本才可以赋予dom、读写cookie、session、ajax等操作的权限,例如a.com可以随意调用b.com的接口去修改数据
以上三个标签可以允许跨域加载资源
利用标签元素,网页可以得到从其他来源动态产生的JSON资料,而这种模式就是所谓的Jsonp,用Jsonp抓到的资料并不是Json,而是任意的JavaScript。
Jsonp跨域的原理本质就是利用的标签有跨域的属性
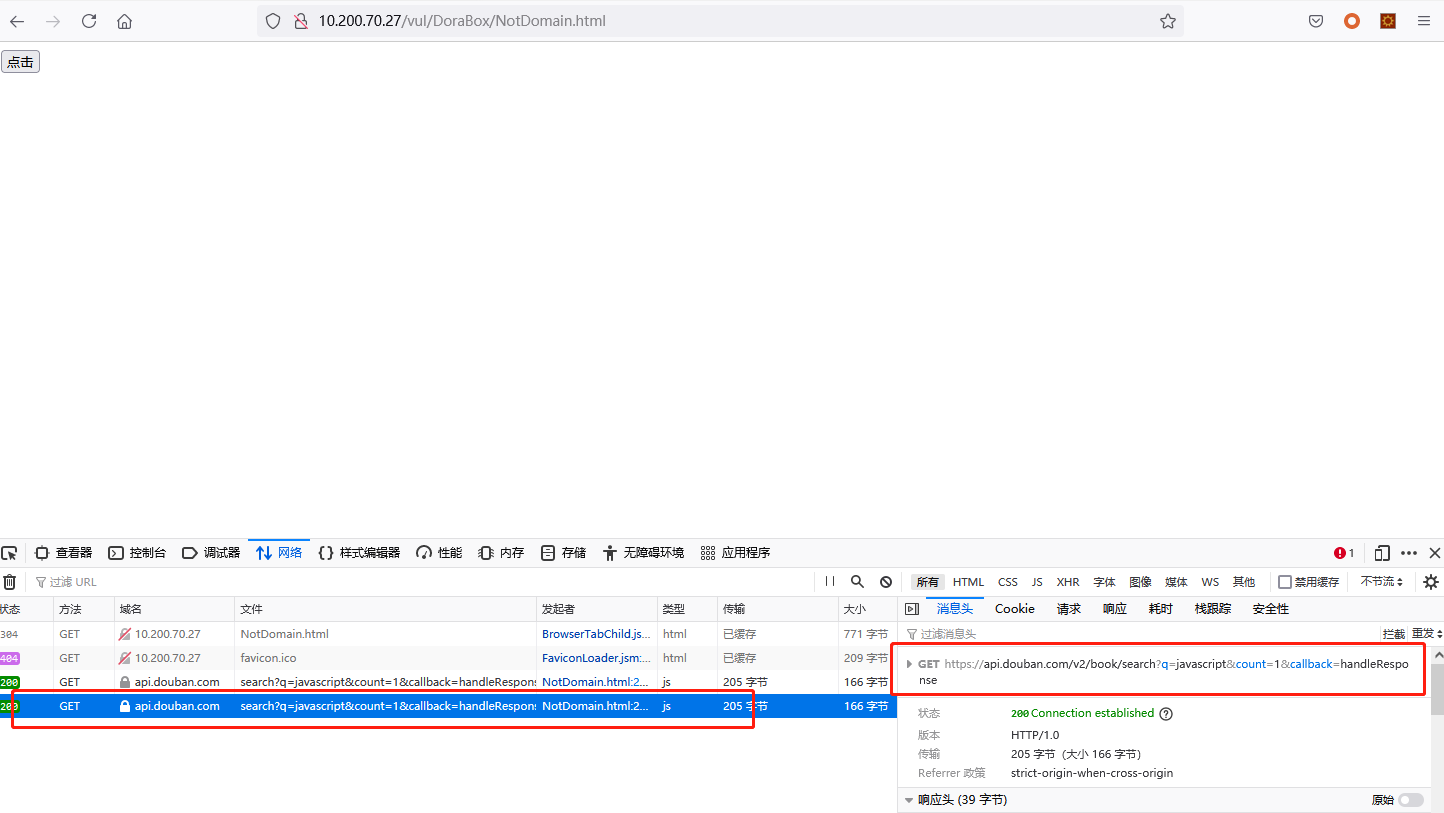
在不同源的情况下
这里没有使用本地搭建两个不同的端口来访问html服务,而是使用douban的网址来测试
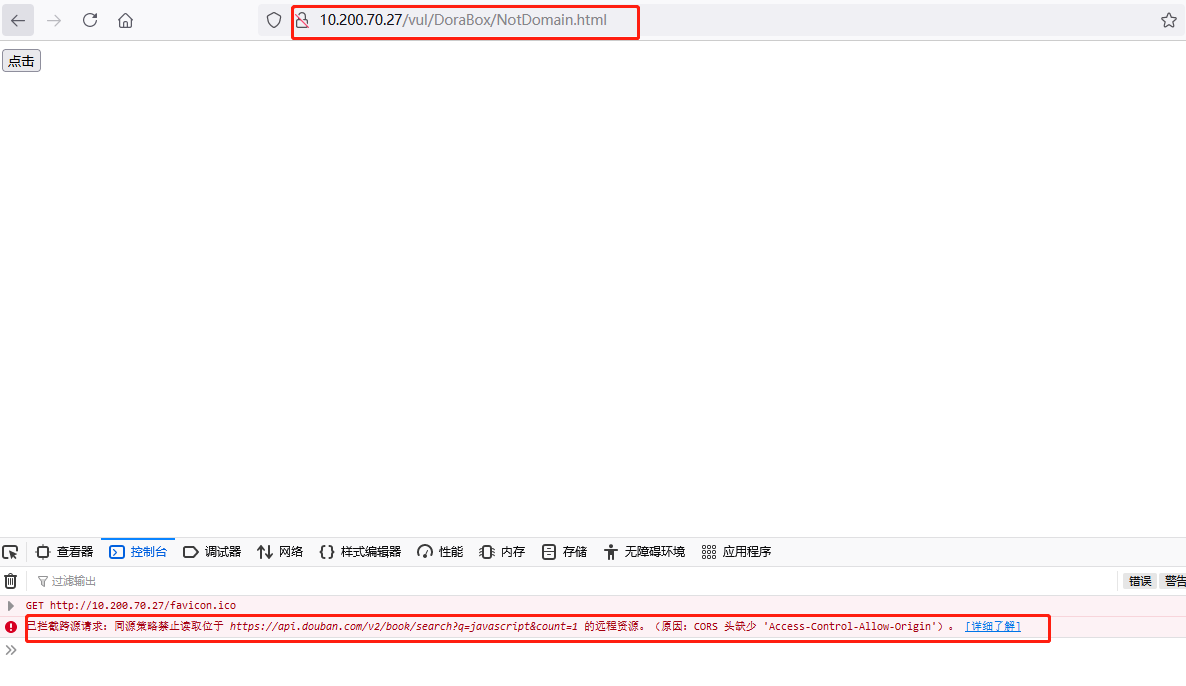
同源的情况下
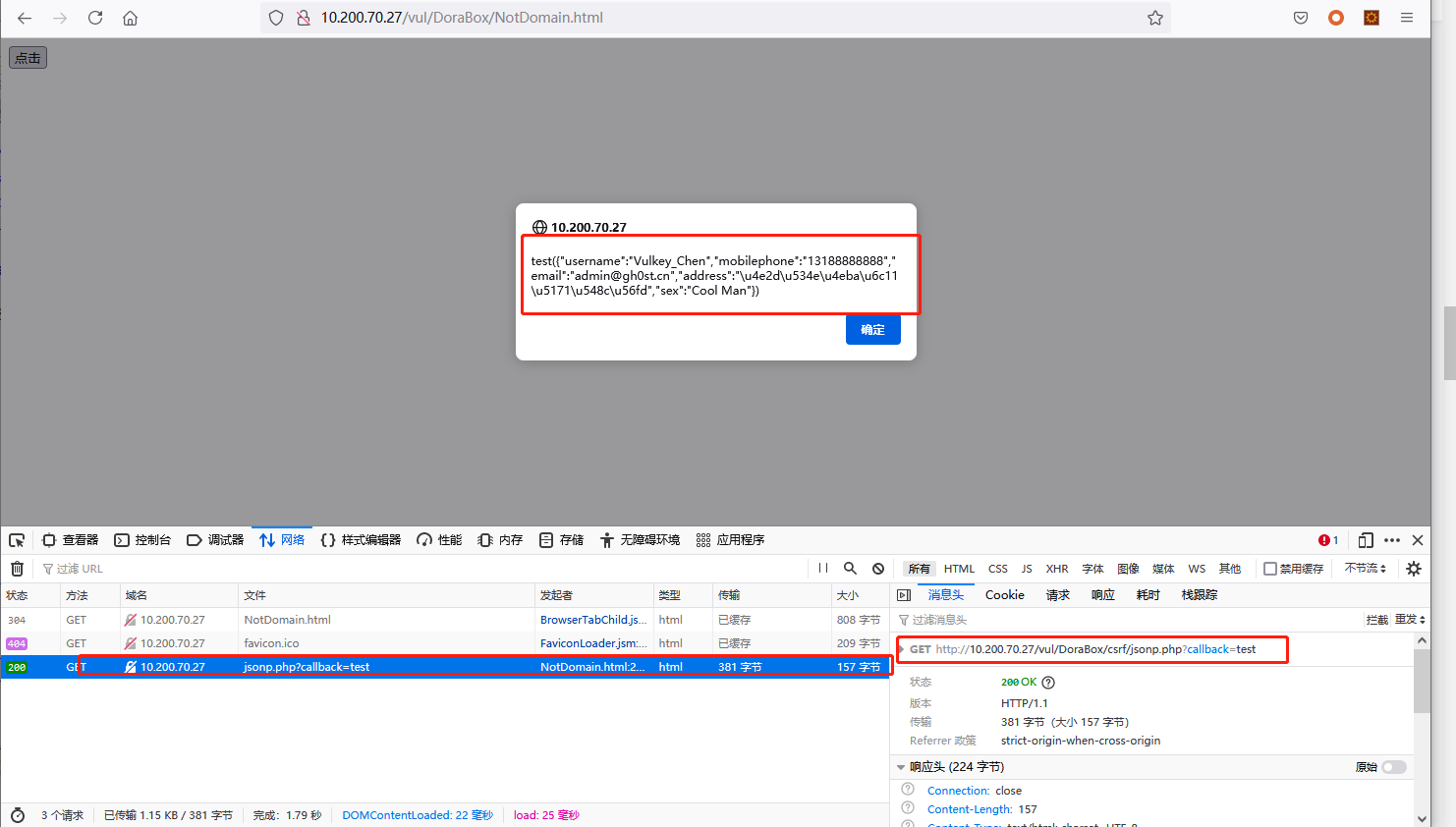
跨域访问
JSONP实现跨域请求的原理简单的说,就是动态创建<script>标签,然后利用<script>的src 不受同源策略约束来跨域获取数据。
JSONP 由两部分组成:回调函数和数据。回调函数是当响应到来时应该在页面中调用的函数。回调函数的名字一般是在请求中指定的。而数据就是传入回调函数中的 JSON 数据。
动态创建<script>标签,设置其src,回调函数在src中设置
在页面中,返回的JSON作为参数传入回调函数中,我们通过回调函数来来操作数据。
完整代码
漏洞页面为
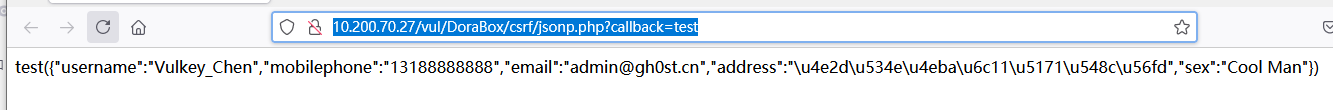
攻击页面
受害者点击页面
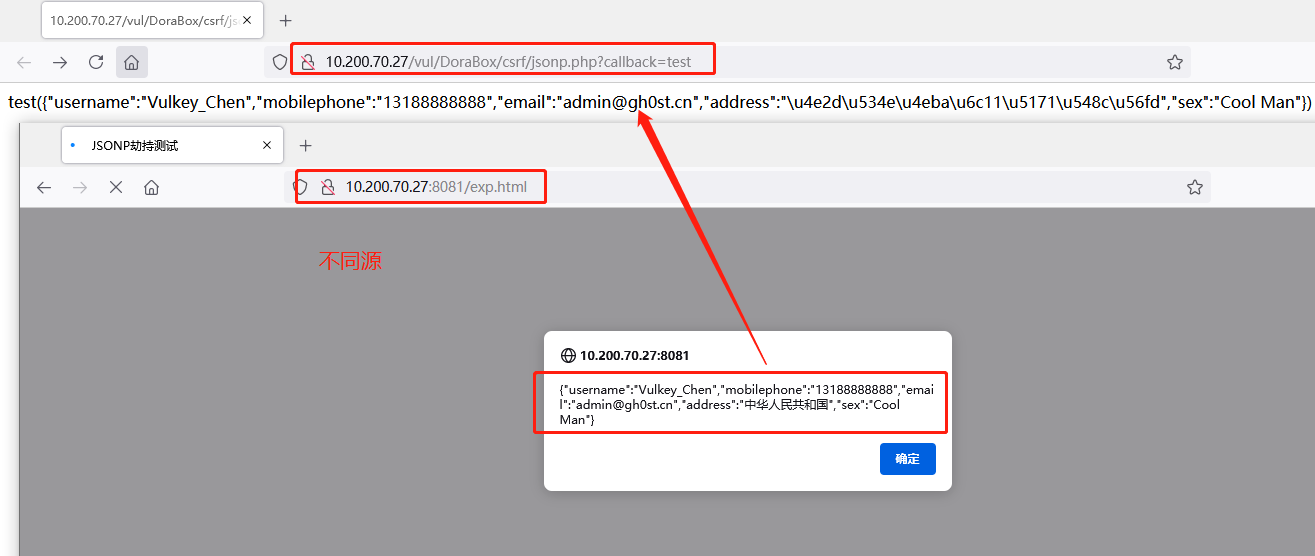
其实网上的文章复现对这里并没有说的很清楚,照着复现演示看上去也比较模糊,大概的意思我理解的是漏洞页面(b31K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5H3i4K6u0W2x3U0l9H3i4K6u0W2y4K6m8Q4x3X3f1J5y4#2)9J5c8Y4k6#2L8q4)9J5c8V1c8G2M7X3q4n7L8%4S2Q4x3V1k6U0M7%4u0X3i4K6u0r3K9Y4y4G2L8Y4m8Q4x3X3g2H3K9s2m8Q4x3@1k6U0j5h3I4D9j5X3q4U0K9#2)9K6c8s2c8W2M7%4c8Q4x3U0W2Q4c8e0S2Q4b7e0k6Q4z5o6q4Q4c8e0S2Q4z5p5g2Q4b7U0N6Q4c8e0g2Q4z5p5k6Q4z5e0k6Q4c8e0S2Q4b7V1k6Q4z5e0W2Q4c8e0c8Q4b7V1q4Q4z5f1u0Q4c8e0k6Q4z5e0g2Q4b7U0m8Q4c8e0k6Q4z5p5c8Q4b7f1g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0k6Q4z5e0S2Q4b7f1k6Q4c8e0W2Q4z5f1y4Q4z5o6m8Q4c8e0S2Q4b7e0k6Q4z5o6q4Q4c8e0N6Q4z5e0W2Q4b7V1u0Q4c8e0g2Q4b7V1c8Q4z5e0g2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5p5k6Q4z5e0N6Q4c8e0g2Q4b7f1g2Q4b7U0y4Q4c8e0S2Q4z5o6m8Q4z5o6g2Q4c8e0N6Q4z5e0W2Q4b7V1u0Q4c8e0g2Q4b7V1c8Q4z5e0g2Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5p5k6Q4z5o6S2Q4c8e0S2Q4b7f1g2Q4b7V1k6Q4c8e0W2Q4z5e0N6Q4b7f1g2Q4c8e0c8Q4b7V1q4Q4z5o6k6Q4c8e0k6Q4z5e0c8Q4b7V1u0Q4c8e0g2Q4z5o6N6Q4b7V1u0Q4c8e0S2Q4z5o6m8Q4z5o6g2Q4c8e0N6Q4b7V1u0Q4z5e0W2Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4b7V1y4Q4z5p5k6Q4c8e0k6Q4b7U0c8Q4z5f1g2Q4c8e0g2Q4z5p5q4Q4b7f1u0Q4c8e0k6Q4z5p5y4Q4z5o6q4Q4c8e0g2Q4b7e0c8Q4z5p5c8Q4c8e0N6Q4z5p5g2Q4b7U0m8Q4c8e0W2Q4z5e0y4Q4b7V1g2Q4c8e0k6Q4z5p5g2Q4b7e0g2Q4x3U0S2Z5N6s2c8H3i4K6y4m8i4K6u0r3i4K6u0r3x3e0m8Q4x3X3f1J5x3o6m8Q4x3X3f1%4x3q4)9J5k6e0t1%4i4K6y4m8z5o6l9^5x3g2)9J5c8X3g2^5M7q4)9J5k6h3S2@1L8h3I4Q4x3U0W2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7U0m8Q4b7U0q4Q4c8e0W2Q4z5o6m8Q4b7e0m8Q4c8e0k6Q4z5o6S2Q4z5e0m8Q4c8e0c8Q4b7V1q4Q4z5o6k6Q4c8e0k6Q4z5e0c8Q4b7V1u0Q4c8e0g2Q4z5o6N6Q4b7V1u0Q4c8e0S2Q4z5o6m8Q4z5o6g2Q4c8e0g2Q4z5p5k6Q4b7f1k6Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0S2Q4z5p5g2Q4b7U0N6Q4c8e0g2Q4z5p5k6Q4z5e0k6Q4c8e0S2Q4b7V1k6Q4z5e0W2Q4c8e0c8Q4b7V1q4Q4z5f1u0Q4c8e0k6Q4z5e0g2Q4b7U0m8Q4c8e0k6Q4z5p5c8Q4b7f1g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4z5e0m8Q4z5p5y4Q4c8e0k6Q4b7V1q4Q4z5e0m8Q4c8e0N6Q4b7f1c8Q4z5e0k6Q4c8e0N6Q4z5e0g2Q4b7e0g2Q4c8e0S2Q4b7e0N6Q4z5o6c8Q4c8e0g2Q4b7f1g2Q4z5f1q4Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7U0S2Q4z5p5c8Q4c8e0g2Q4z5e0m8Q4z5p5y4Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0k6Q4b7V1q4Q4z5e0m8Q4c8e0k6Q4z5e0S2Q4b7f1k6Q4c8e0c8Q4b7U0S2Q4z5p5c8Q4c8e0g2Q4z5p5k6Q4b7f1k6Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0S2Q4z5p5g2Q4b7U0N6Q4c8e0g2Q4z5p5k6Q4z5e0k6U0L8$3!0C8K9h3g2Q4c8e0S2Q4b7V1k6Q4z5e0W2Q4c8e0c8Q4b7V1q4Q4z5f1u0Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0g2Q4b7V1g2Q4z5o6S2Q4c8e0k6Q4z5e0S2Q4b7V1g2Q4c8e0N6Q4z5o6c8Q4b7U0k6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0N6Q4z5e0c8Q4b7e0S2Q4c8e0k6Q4z5o6S2Q4b7U0N6Q4c8e0N6Q4z5e0W2Q4b7V1u0Q4c8e0g2Q4b7V1c8Q4z5e0g2Q4c8e0g2Q4z5e0m8Q4z5p5g2Q4c8e0N6Q4z5f1q4Q4z5o6c8U0L8$3!0C8K9h3g2Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0c8Q4b7U0S2Q4z5p5c8Q4c8e0g2Q4z5e0m8Q4z5p5y4Q4c8e0k6Q4b7V1q4Q4z5e0m8Q4c8e0k6Q4z5e0S2Q4b7f1k6Q4c8e0c8Q4b7U0S2Q4z5p5c8Q4c8e0g2Q4z5p5k6Q4b7f1k6Q4c8e0c8Q4b7V1u0Q4b7e0g2Q4c8e0S2Q4z5p5g2Q4b7U0N6Q4c8e0g2Q4z5p5k6Q4z5e0k6Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0S2Q4b7V1k6Q4z5e0W2Q4c8e0W2Q4z5o6N6Q4z5p5y4Q4c8e0W2Q4z5o6m8Q4z5f1q4Q4c8e0S2Q4b7V1k6Q4z5o6N6Q4c8e0k6Q4b7e0m8Q4z5o6N6Q4c8e0N6Q4b7f1c8Q4b7V1g2Q4c8e0g2Q4b7U0q4Q4z5f1g2Q4c8e0k6Q4z5o6m8Q4b7e0N6Q4c8e0N6Q4z5f1q4Q4z5o6c8Q4c8e0N6Q4z5o6W2Q4b7U0W2Q4c8e0k6Q4z5o6m8Q4b7e0N6Q4c8f1k6Q4b7V1y4Q4z5p5y4Q4c8e0S2Q4z5p5g2Q4b7U0N6Q4c8e0g2Q4z5p5k6Q4z5e0k6Q4c8e0g2Q4z5o6S2Q4b7U0m8Q4c8e0c8Q4b7V1q4Q4z5o6k6Q4c8e0c8Q4b7U0S2Q4z5p5c8Q4c8e0g2Q4z5e0m8Q4z5p5y4Q4c8e0k6Q4b7V1q4Q4z5e0m8Q4c8e0N6Q4z5e0c8Q4b7e0S2Q4c8e0k6Q4z5o6S2Q4b7U0N6Q4c8e0N6Q4z5f1q4Q4z5o6c8o6L8$3!0C8K9h3f1`.
1、验证Referer
2、增加随机的Token进行验证
在phpstudy中开启,删掉前面的#号并在配置文件的最开头配置header然后重启服务
这一步不是必须设置,通过复现测试发现,如果php中写了,这里好像可以不用设置
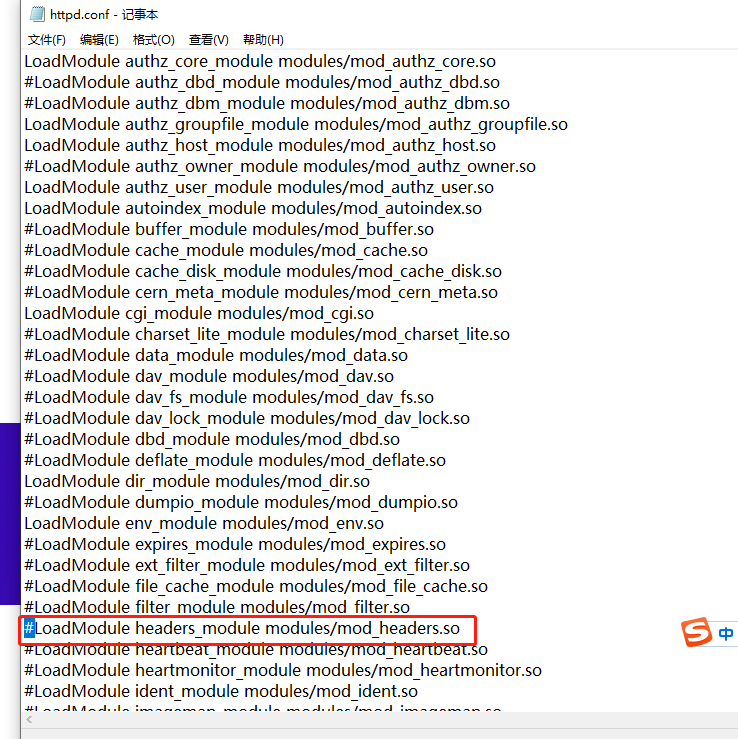

请求头存在origin参数且可控(不存在可自行添加不影响结果)
响应头存在下面两个:
Burp重放

如何判断是否存在跨域攻击,可以在请求头中添加一个源,看看是否可控

模拟受害者点击

首先你判断是否请求头里面是否有Origin如果有,就讲header设置为(Access-Control-Allow-Origin: "传进来的Origin")如果没有就设置为*,在设置不同的header,最后echo json
把这些header删掉,就会触发同源策略,就无法获得想要的json信息

删掉后还是正常输出json内容

但是使用不同域模拟受害者点击的时候就会提示

同源策略不允许其他的源访问,所以如果错误的配置了Access-Control-Allow-Origin,导致攻击者可以控制这个Origin的话,就会导致我只需要指定当前访问地址的源即可。
如果使用Access-Control-Allow-Origin来处理跨域的话,如果没有传入Origin参数,那么就会使用默认的值,这个默认的值浏览器会将当前的host传进去,所以在请求中可以看到返回包里面Origin是当前的host


参考文章
1、badK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8Y4N6W2K9i4S2A6L8W2)9#2k6U0b7I4y4U0M7&6y4o6t1%4i4K6u0r3j5i4u0@1K9h3y4D9k6g2)9J5c8X3c8W2N6r3q4A6L8s2y4Q4x3V1j5I4x3e0l9K6x3e0t1K6z5o6R3`.
2、64bK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2A6L8h3!0G2j5#2)9J5k6h3y4G2L8g2)9J5c8X3q4J5N6r3W2U0L8r3g2Q4x3V1j5J5z5e0p5&6x3K6p5`.
3、3e4K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4u0#2j5h3&6&6K9h3k6W2L8X3N6Q4x3X3g2U0L8$3#2Q4x3V1k6T1L8r3!0Y4i4K6u0r3x3U0l9I4y4W2)9J5c8U0l9@1i4K6u0r3j5$3!0J5M7#2)9J5k6h3S2@1L8h3H3`.
4、f31K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8Y4N6W2K9i4S2A6L8W2)9#2k6U0b7I4y4e0V1^5y4U0j5H3i4K6u0r3j5i4u0@1K9h3y4D9k6g2)9J5c8X3c8W2N6r3q4A6L8s2y4Q4x3V1j5I4x3o6j5H3y4e0l9&6y4e0M7`.
5、4b9K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2U0L8X3u0D9L8$3N6K6i4K6u0W2j5$3!0E0i4K6u0r3j5%4y4F1k6q4)9J5c8Y4m8Q4x3V1j5I4x3e0R3H3y4K6M7H3z5g2)9J5k6h3S2@1L8h3H3`.
<img/>
<link/>
<script/>
<!-- 以上同源与不同源的测试代码 -->
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>ajax</title>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
</head>
<body>
<div id="mydiv">
<button id="btn">点击</button>
</div>
</body>
<script type="text/javascript">
window.onload = function() {
var oBtn = document.getElementById('btn');
oBtn.onclick = function() {
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if (xhr.readyState == 4 && xhr.status == 200) {
alert( xhr.responseText );
}
};
xhr.open('get', '373K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5H3i4K6u0W2x3U0l9H3i4K6u0W2y4K6m8Q4x3X3f1J5y4#2)9J5c8Y4k6#2L8q4)9J5c8V1c8G2M7X3q4n7L8%4S2Q4x3V1k6U0M7%4u0X3i4K6u0r3K9Y4y4G2L8Y4m8Q4x3X3g2H3K9s2m8Q4x3@1k6U0j5h3I4D9j5X3q4U0K9#2)9K6c8s2c8W2M7%4c8Q4x3U0M7`., true);
xhr.send();
};
};
</script>
</html>
<!-- 以上同源与不同源的测试代码 -->
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>ajax</title>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
</head>
<body>
<div id="mydiv">
<button id="btn">点击</button>
</div>
</body>
<script type="text/javascript">
window.onload = function() {
var oBtn = document.getElementById('btn');
oBtn.onclick = function() {
var xhr = new XMLHttpRequest();
xhr.onreadystatechange = function() {
if (xhr.readyState == 4 && xhr.status == 200) {
alert( xhr.responseText );
}
};
xhr.open('get', '373K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5H3i4K6u0W2x3U0l9H3i4K6u0W2y4K6m8Q4x3X3f1J5y4#2)9J5c8Y4k6#2L8q4)9J5c8V1c8G2M7X3q4n7L8%4S2Q4x3V1k6U0M7%4u0X3i4K6u0r3K9Y4y4G2L8Y4m8Q4x3X3g2H3K9s2m8Q4x3@1k6U0j5h3I4D9j5X3q4U0K9#2)9K6c8s2c8W2M7%4c8Q4x3U0M7`., true);
xhr.send();
};
};
</script>
</html>
var script = document.createElement("script");
script.src = "3e9K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6S2M7r3W2Q4x3X3g2V1L8%4g2T1j5h3&6Q4x3X3g2U0L8$3#2Q4x3V1k6$3x3W2)9J5c8X3u0G2L8$3E0Q4x3V1k6K6k6h3q4J5j5$3S2Q4x3@1k6I4i4K6y4p5K9X3q4$3j5i4y4U0M7X3W2H3N6q4)9J5y4X3q4E0M7q4)9K6b7X3y4G2N6h3&6@1i4K6y4p5x3g2)9J5y4X3q4E0M7q4)9K6b7X3y4S2L8r3I4T1j5h3y4C8i4K6y4p5K9r3q4F1k6r3I4W2f1X3g2K6M7r3!0F1M7$3f1`.";
document.body.insertBefore(script, document.body.firstChild);
var script = document.createElement("script");
script.src = "3e9K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6S2M7r3W2Q4x3X3g2V1L8%4g2T1j5h3&6Q4x3X3g2U0L8$3#2Q4x3V1k6$3x3W2)9J5c8X3u0G2L8$3E0Q4x3V1k6K6k6h3q4J5j5$3S2Q4x3@1k6I4i4K6y4p5K9X3q4$3j5i4y4U0M7X3W2H3N6q4)9J5y4X3q4E0M7q4)9K6b7X3y4G2N6h3&6@1i4K6y4p5x3g2)9J5y4X3q4E0M7q4)9K6b7X3y4S2L8r3I4T1j5h3y4C8i4K6y4p5K9r3q4F1k6r3I4W2f1X3g2K6M7r3!0F1M7$3f1`.";
document.body.insertBefore(script, document.body.firstChild);
function handleResponse(response){
// 对response数据进行操作代码
}
function handleResponse(response){
// 对response数据进行操作代码
}
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>JSONP实现跨域2</title>
</head>
<body>
<div id="mydiv">
<button id="btn">点击</button>
</div>
</body>
<script type="text/javascript">
function handleResponse(response){
console.log(response);
}
</script>
<script type="text/javascript">
window.onload = function() {
var oBtn = document.getElementById('btn');
oBtn.onclick = function() {
var script = document.createElement("script");
script.src = "d73K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6S2M7r3W2Q4x3X3g2V1L8%4g2T1j5h3&6Q4x3X3g2U0L8$3#2Q4x3V1k6$3x3W2)9J5c8X3u0G2L8$3E0Q4x3V1k6K6k6h3q4J5j5$3S2Q4x3@1k6I4i4K6y4p5K9X3q4$3j5i4y4U0M7X3W2H3N6q4)9J5y4X3q4E0M7q4)9K6b7X3y4G2N6h3&6@1i4K6y4p5x3g2)9J5y4X3q4E0M7q4)9K6b7X3y4S2L8r3I4T1j5h3y4C8i4K6y4p5K9r3q4F1k6r3I4W2f1X3g2K6M7r3!0F1M7$3f1`.";
document.body.insertBefore(script, document.body.firstChild);
};
};
</script>
</html>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>JSONP实现跨域2</title>
</head>
<body>
<div id="mydiv">
<button id="btn">点击</button>
</div>
</body>
<script type="text/javascript">
function handleResponse(response){
console.log(response);
}
</script>
<script type="text/javascript">
window.onload = function() {
var oBtn = document.getElementById('btn');
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课