
快速定位log4j新漏洞影响的项目
第一步:将FossEye知识库更新至最新版本
第二步:【项目管理】全量扫描代码仓库
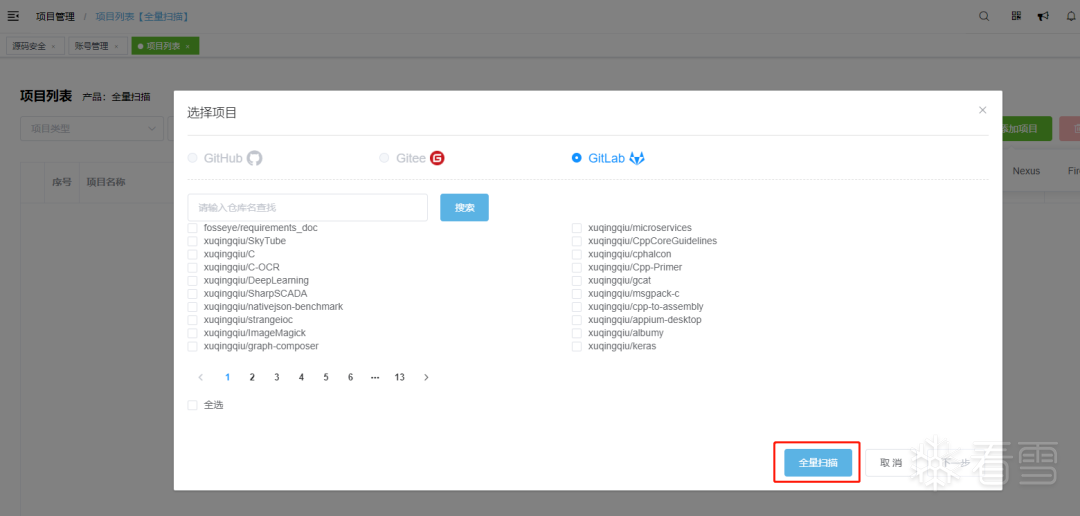
第三步【资产管理-漏洞】根据漏洞id搜索“CVE-2021-44228”,点击查看影响项目数
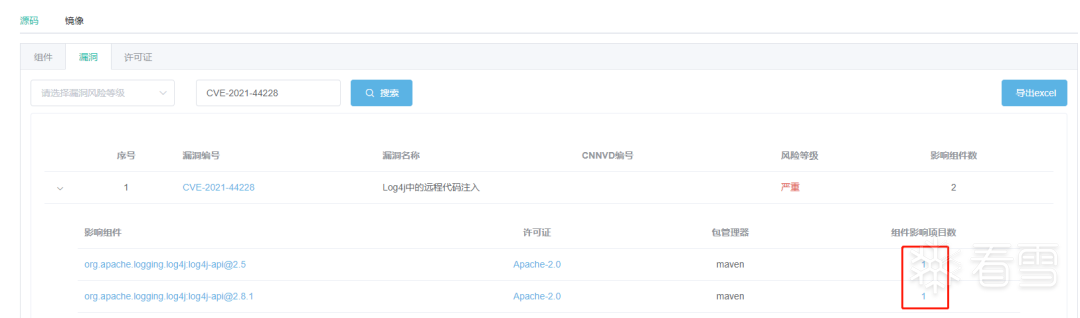
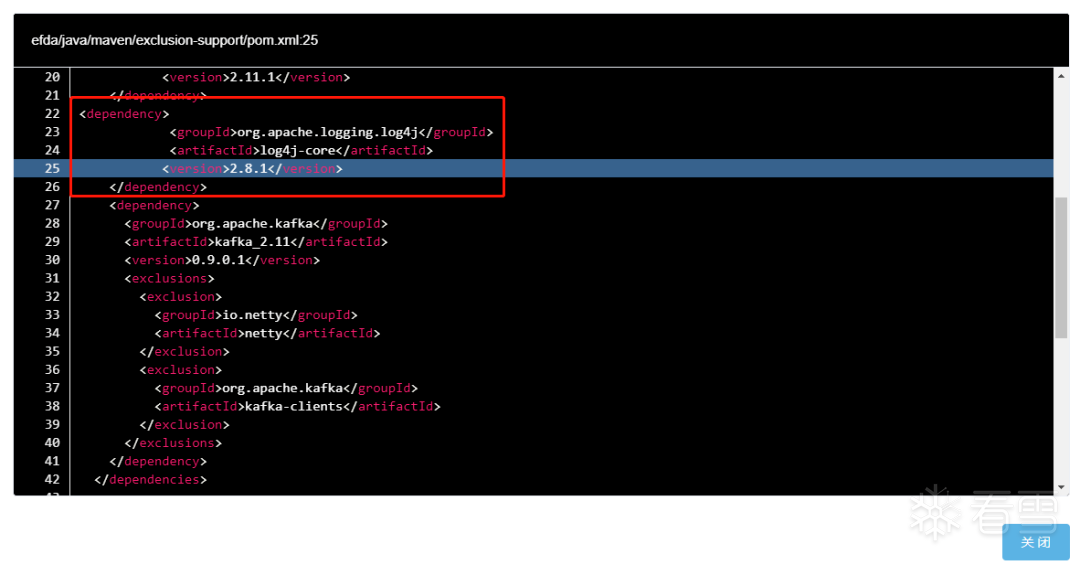
第四步 溯源页面显示出该漏洞影响的所有项目,点击放大镜图标可查看代码具体位置
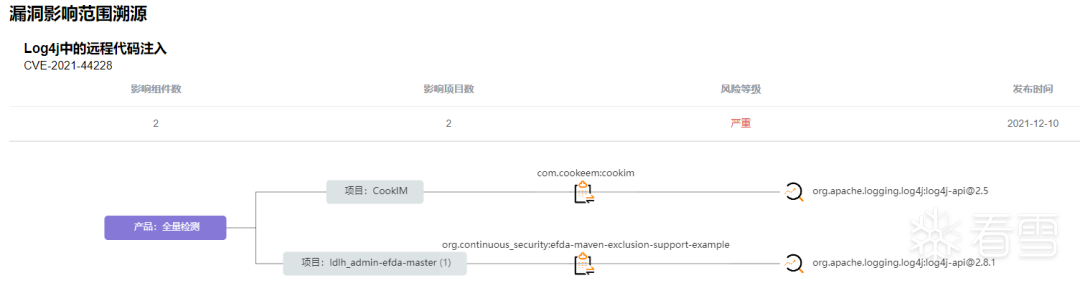
漏洞详情
漏洞概述
此次Apache Log4j2 漏洞是用于 Log4j2 提供的 lookup 功能造成的,该功能允许开发者通过一些协议去读取相应环境中的配置。但在实现的过程中,并未对输入进行严格的判断,从而造成漏洞的发生。恶意攻击者可以利用该漏洞注入恶意class文件从而执行任意命令。
漏洞编号
CVE-2021-44228
漏洞危险等级
严重
影响版本
Apache Log4j <=2.15.0-rc1
可能的受影响应用包括但不限于如下:
Spring-Boot-strater-log4j2
Apache Struts2
Apache Solr
Apache Flink
Apache Druid
ElasticSearch
flume
dubbo
Redis
logstash
kafka
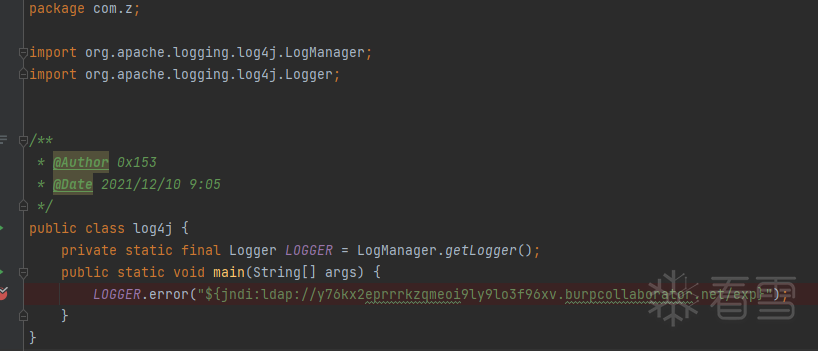
漏洞复现
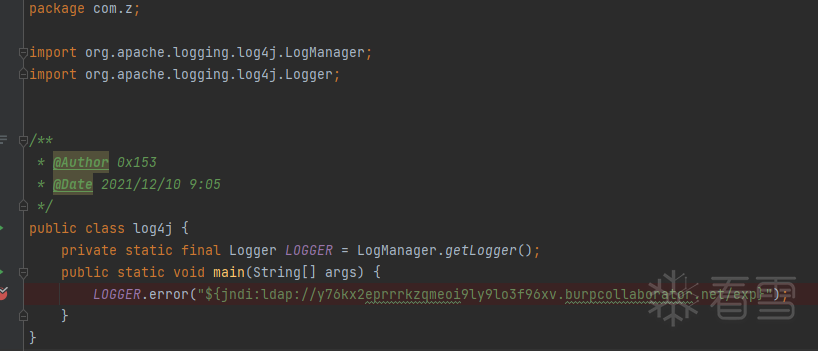
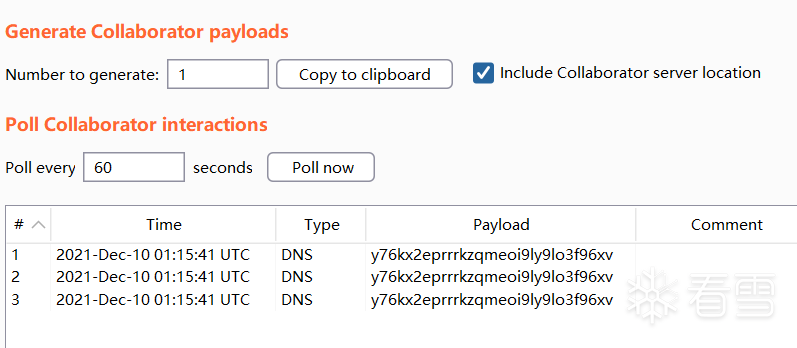
漏洞分析
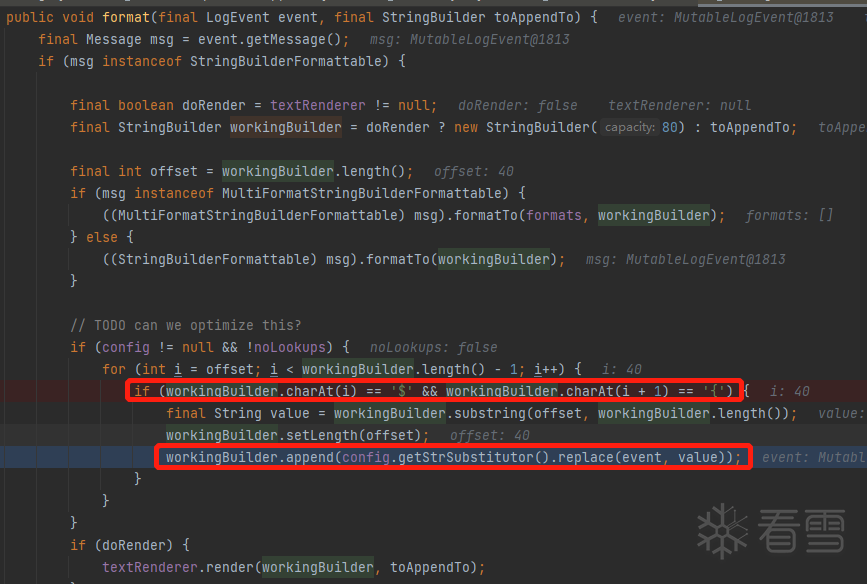
略去一些非关键流程,日志信息最终会进入MessagePatternConverter.java 文件的format方法,如下图,当日志信息中出现 "${"关键字 则通过StrSubstitutor.java的replace方法对其进行替换和解析
最终通过StrSubstitutor.java文件中的substitute方法对传入的日志信息进行替换。这个函数主要作用就是提取出日志信息中的${}信息,并根据内容调用。varName就是提取出来的关键信息,最关键的位置如下:
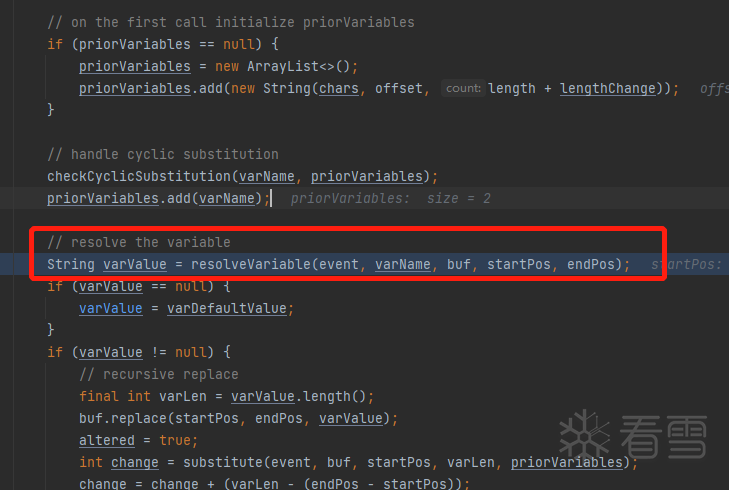
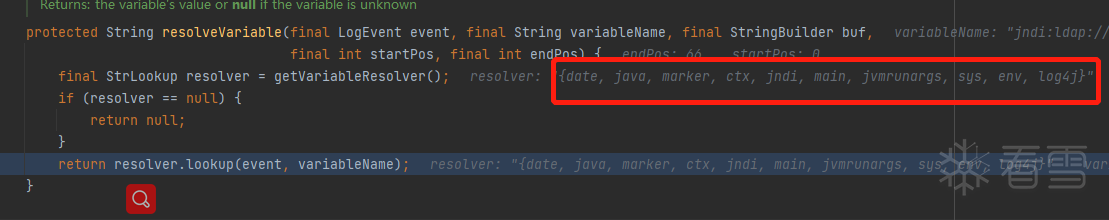
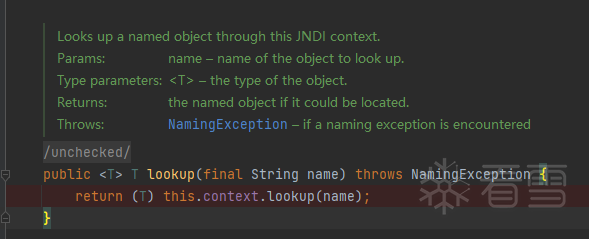
在lookup中,prefix是对应配置类,name是其参数并通过调用对应方法进行解析。
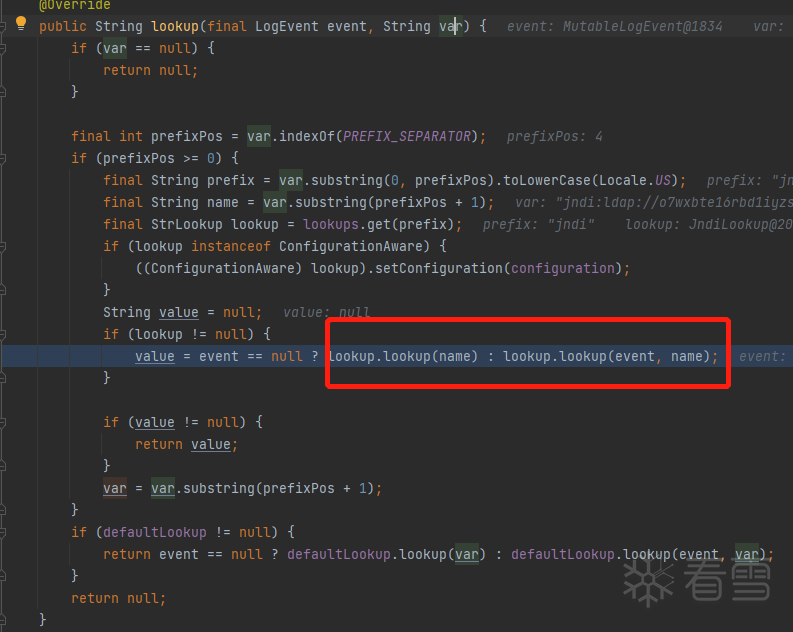
lookup保存有如下解析类:
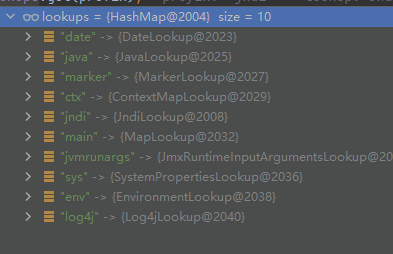
最终在JndiLookup.java中触发漏洞
堆栈:
lookup:172, JndiManager (142K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8X3!0J5k6#2)9J5k6h3q4H3j5h3y4Z5k6g2)9J5k6h3I4G2k6$3N6A6L8X3N6Q4x3X3g2D9L8$3M7@1K9W2)9J5k6h3y4G2M7X3g2Q4x3X3g2F1k6i4c8Q4x3U0V1`.
lookup:56, JndiLookup (org.apache.logging.log4j.core.lookup)
lookup:184, Interpolator (org.apache.logging.log4j.core.lookup)
resolveVariable:1054, StrSubstitutor (org.apache.logging.log4j.core.lookup)
substitute:976, StrSubstitutor (org.apache.logging.log4j.core.lookup)
substitute:872, StrSubstitutor (org.apache.logging.log4j.core.lookup)
replace:427, StrSubstitutor (org.apache.logging.log4j.core.lookup)
format:132, MessagePatternConverter (org.apache.logging.log4j.core.pattern)
format:38, PatternFormatter (org.apache.logging.log4j.core.pattern)
toSerializable:334, PatternLayout$PatternSerializer (org.apache.logging.log4j.core.layout)
toText:233, PatternLayout (org.apache.logging.log4j.core.layout)
encode:218, PatternLayout (org.apache.logging.log4j.core.layout)
encode:58, PatternLayout (org.apache.logging.log4j.core.layout)
directEncodeEvent:177, AbstractOutputStreamAppender (org.apache.logging.log4j.core.appender)
tryAppend:170, AbstractOutputStreamAppender (org.apache.logging.log4j.core.appender)
append:161, AbstractOutputStreamAppender (org.apache.logging.log4j.core.appender)
tryCallAppender:156, AppenderControl (org.apache.logging.log4j.core.config)
callAppender0:129, AppenderControl (org.apache.logging.log4j.core.config)
callAppenderPreventRecursion:120, AppenderControl (org.apache.logging.log4j.core.config)
callAppender:84, AppenderControl (org.apache.logging.log4j.core.config)
callAppenders:448, LoggerConfig (org.apache.logging.log4j.core.config)
processLogEvent:433, LoggerConfig (org.apache.logging.log4j.core.config)
log:417, LoggerConfig (org.apache.logging.log4j.core.config)
log:403, LoggerConfig (org.apache.logging.log4j.core.config)
log:49, DefaultReliabilityStrategy (org.apache.logging.log4j.core.config)
logMessage:146, Logger (org.apache.logging.log4j.core)
log:2117, AbstractLogger (org.apache.logging.log4j.spi)
tryLogMessage:2205, AbstractLogger (org.apache.logging.log4j.spi)
logMessageTrackRecursion:2159, AbstractLogger (org.apache.logging.log4j.spi)
logMessageSafely:2142, AbstractLogger (org.apache.logging.log4j.spi)
logMessage:2017, AbstractLogger (org.apache.logging.log4j.spi)
logIfEnabled:1983, AbstractLogger (org.apache.logging.log4j.spi)
error:740, AbstractLogger (org.apache.logging.log4j.spi)
main:14, log4j (com.z)
修复建议
官方修复链接如下:
c71K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6S2M7r3q4U0K9r3g2Q4x3V1k6D9L8$3N6Y4K9h3&6Y4i4K6u0V1L8r3!0Y4y4r3Z5J5i4K6u0r3M7X3g2D9k6h3q4K6k6i4y4Q4x3V1k6@1j5h3N6Q4x3V1k6D9L8$3M7@1K9W2)9J5k6o6u0Q4x3X3f1I4y4g2)9J5k6e0m8Q4x3X3c8J5j5K6t1`.
临时解决方案(三选一):
(1) 修改jvm参数 -Dlog4j2.formatMsgNoLookups=true
(2) 修改配置log4j2.formatMsgNoLookups=True
(3) 将系统环境变量 FORMAT_MESSAGES_PATTERN_DISABLE_LOOKUPS 设置为 true
参考链接
982K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6F1N6X3c8Q4x3X3g2F1K9i4y4@1i4K6u0W2k6$3!0$3i4K6u0r3N6Y4g2D9L8W2)9J5c8X3c8W2N6r3q4A6L8q4)9J5c8V1y4h3c8g2)9J5k6o6t1H3x3U0q4Q4x3X3b7@1y4o6t1J5z5l9`.`.
e79K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6S2M7r3q4U0K9r3g2Q4x3V1k6D9L8$3N6Y4K9h3&6Y4i4K6u0V1L8r3!0Y4y4r3Z5J5i4K6u0r3M7s2g2D9L8q4)9J5c8U0j5H3z5l9`.`.
6cfK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6@1j5h3&6Y4P5r3W2S2L8$3k6W2L8X3M7%4i4K6u0r3j5i4m8S2j5$3S2W2i4K6u0V1L8r3!0Y4y4r3A6Q4x3X3c8H3L8$3x3`.
06fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6D9L8$3N6Y4K9h3&6Y4i4K6u0W2j5i4m8S2j5$3S2W2i4K6u0W2L8%4u0Y4i4K6u0r3L8r3!0Y4y4r3A6Q4x3V1j5J5i4K6u0W2P5q4)9J5c8X3y4Z5j5h3&6Y4k6i4y4Q4x3X3c8J5k6i4m8G2M7Y4c8Q4x3X3g2Z5N6r3#2D9i4K6t1K6j5e0u0Q4x3X3f1I4y4g2)9J5k6e0l9`.
84aK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6D9L8$3N6Y4K9h3&6Y4i4K6u0W2j5i4m8S2j5$3S2W2i4K6u0W2L8%4u0Y4i4K6u0r3L8r3!0Y4y4r3A6Q4x3V1j5J5i4K6u0W2P5q4)9J5c8X3#2S2L8Y4g2S2L8q4)9J5c8X3I4G2L8$3E0#2M7s2y4Q4x3X3g2Z5N6r3#2D9i4K6t1K6d9X3&6V1K9f1I4G2L8$3E0#2M7l9`.`.
47fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6S2k6s2k6A6M7$3!0J5K9h3g2K6i4K6u0r3c8@1S2e0b7g2)9J5k6r3A6X3K9o6S2Q4x3X3c8U0x3X3A6H3i4K6u0V1y4i4j5K6M7b7`.`.
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课