-
-
[原创]第四题飞蛾扑火WP
-
发表于: 2022-5-29 20:52 6535
-
网址端口621K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5x3g2)9J5k6e0x3$3i4K6u0W2x3e0b7#2i4K6u0W2x3e0f1%4i4K6y4m8z5o6l9@1y4q4)9J5c8W2!0q4c8W2!0n7b7#2)9^5b7#2!0q4y4W2)9&6c8W2!0m8y4g2!0q4y4#2)9&6b7#2)9^5b7W2!0q4y4W2!0n7b7g2)9&6x3q4!0q4y4q4!0n7b7W2!0m8x3#2!0q4y4#2!0m8x3q4)9^5x3g2!0q4x3#2)9^5x3q4)9^5x3R3`.`.
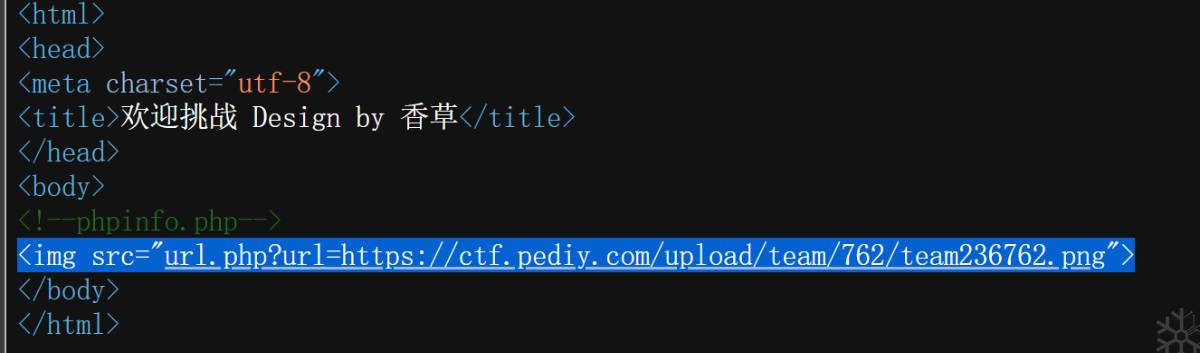
查看url.php的源代码
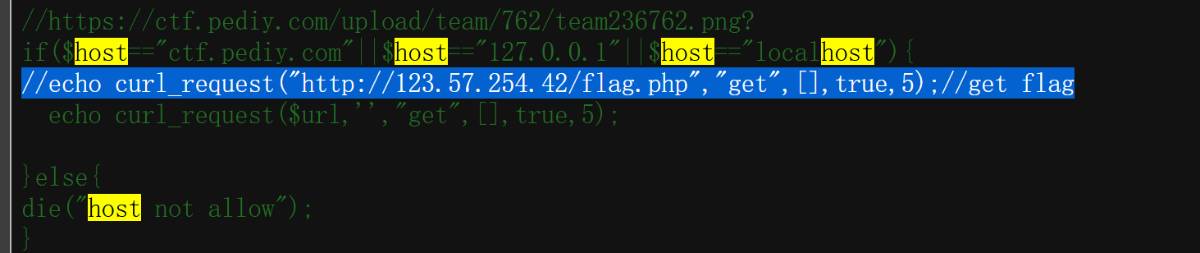
根据注释,flag的位置在123.57.254.42/flag,但是host有限制,需要想办法绕过。
查找资料,在9f9K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8Y4N6W2K9i4S2A6L8W2)9#2k6U0x3&6z5e0f1$3x3e0p5H3i4K6u0r3j5i4u0@1K9h3y4D9k6g2)9J5c8X3c8W2N6r3q4A6L8s2y4Q4x3V1j5I4x3e0p5I4x3U0l9I4z5e0t1`.
发现一个漏洞,URL协议对特殊字符的处理有漏洞。
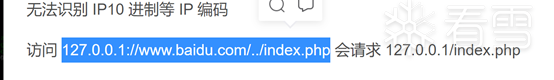
构造请求,
05aK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8U0p5J5x3g2)9J5k6e0x3$3i4K6u0W2x3e0b7#2i4K6u0W2x3e0f1%4i4K6y4m8z5o6l9@1y4q4)9J5c8Y4g2J5L8q4)9J5k6i4m8Z5M7q4)9K6c8Y4g2J5L8q4)9K6c8o6p5J5x3#2)9J5k6e0f1%4i4K6u0W2x3U0f1@1i4K6u0W2y4o6u0Q4x3@1q4Q4x3V1k6Q4x3V1k6U0N6r3k6Q4x3X3g2H3k6h3c8A6P5g2)9J5k6h3y4G2L8g2)9J5c8W2)9J5k6g2)9J5k6g2)9J5c8X3k6D9j5h3N6Q4x3X3g2H3K9s2l9`.
成功绕过,获得flag。
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
赞赏
- [原创]KCTF2022春季赛逆向第2题 末日邀请WP 9105
- [原创]KCTF2022春季赛逆向第七题 一触即发WP 8457
- [原创]KCTF2022春季赛Crypto虫洞末世WP 12605
- [原创]第四题飞蛾扑火WP 6536

