25 个网络安全搜索引擎
不分先后
1/25—Shodan
===========
搜索连接到互联网的设备 2f8K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2K6K9r3!0V1j5h3&6Q4x3X3g2A6L8#2)9J5c8R3`.`.
2/25 — Wigle
==============
无线网络数据库,带有统计信息 Wigle :887K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2%4K9h3N6D9k6g2)9J5k6h3&6W2N6q4)9J5c8R3`.`.。
3/25 — GreyNoise
====================
搜索连接到互联网的设备 GreyNoise e1bK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2Y4M7X3g2&6L8X3!0A6M7$3g2Q4x3X3g2A6L8#2)9J5c8R3`.`.。
4/25 — VirusTotal
=====================
分析可疑文件、域、IP 和 URL 以检测恶意软件 VirusTotal c3dK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2$3K9i4u0#2M7%4c8G2N6r3q4D9i4K6u0W2j5$3!0E0i4K6u0r3k6%4g2A6i4K6u0r3K9r3!0E0k6g2)9J5c8Y4g2H3L8r3!0S2k6l9`.`.

5/25 — URL Scan
=================
扫描和分析网站 e7eK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6#2M7X3I4K6j5$3q4F1i4K6u0W2K9h3!0Q4x3V1j5`.。

6/25 — Vulners
=========
在大型数据库中搜索已知漏洞 c47K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6$3N6h3I4F1k6i4u0K6i4K6u0W2j5$3!0E0i4K6u0r3。
7/25 — WayBackMachine
=====================
查看已删除网站的内容或深入了解某网站历史信息 WayBackMachine 4bcK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4k6h3u0Q4x3X3g2S2M7X3y4Z5K9i4k6W2i4K6u0W2L8%4u0Y4i4K6u0r3
8/25 — Netlas
===========
搜索和监控互联网连接资产 Netlas 6ddK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6F1k6i4c8D9j5i4y4Q4x3X3g2A6L8#2)9J5c8R3`.`.。
9/25 — ONYPHE
=============
收集网络威胁情报数据 ONYPHE 383K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2G2L8Y4W2H3K9r3g2Q4x3X3g2A6L8#2)9J5c8R3`.`.。
10/25 — FullHunt
================
搜索和发现攻击面 FullHunt 07eK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6X3N6h3I4D9K9s2g2F1N6q4)9J5k6h3W2G2i4K6u0r3。
11/25 — GrepApp
===============
搜索 50 万个 git 存储库 GrepApp 382K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4M7X3g2H3i4K6u0W2j5i4m8H3i4K6u0r3。

12/25 — CRT sh
==============
搜索已经收录的证书信息 f82K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6U0M7Y4c8Q4x3X3g2K6K9q4)9J5c8R3`.`. 。
13/25 — GreyHatWarfare
============
搜索公共 S3 buckets 42cK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4M7X3q4&6K9r3q4@1N6$3q4J5k6X3q4J5k6g2)9J5k6h3y4G2L8g2)9J5c8R3`.`.

14/25 — AlienVault
==================
开源威胁情报社区 c9fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6G2N6s2S2Q4x3X3g2S2L8r3W2W2L8Y4k6S2N6h3I4@1i4K6u0W2j5$3!0E0i4K6u0r3。
15/25 — BinaryEdge
==================
扫描互联网以获取威胁情报 BinaryEdge 788K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2T1K9h3&6S2M7Y4W2W2k6r3N6W2i4K6u0W2K9h3!0Q4x3V1j5`.
16/25 — TinEye
==========
逆向图像搜索 TinEye a49K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6@1K9h3&6W2P5h3g2Q4x3X3g2U0L8$3#2Q4x3V1j5`.。
17/25 — OSINT Framework
================
OSINT(开源情报)框架网站,一些链接不再有效,但它仍然是一个不错的网站 OSINT 框架26fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6G2M7$3W2F1N6r3k6J5j5h3#2W2N6$3!0J5K9#2)9J5k6h3y4G2L8g2)9J5c8R3`.`.。
18/25 — Hunter.io
=================
搜索属于该网站或公司的电子邮件地址 f0fK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Z5N6h3&6@1k6i4u0Q4x3X3g2A6L8#2)9J5c8R3`.`.。
19/25 — LeakIX
============
搜索公开泄露索引信息 9a3K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6D9k6h3q4C8K9i4S2Q4x3X3g2F1k6i4c8Q4x3V1j5`.。
20/25 — IntelligenceX
=====================
搜索 Tor、I2P、数据泄漏、域和电子邮件 5e1K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6A6L8Y4c8W2L8s2S2Q4x3X3g2A6L8#2)9J5c8R3`.`.。
21/25 — DNSDumpster
===================
DNS Recon & Research, DNS 记录 34dK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6V1L8Y4y4V1N6h3#2H3M7%4c8W2M7W2)9J5k6h3y4G2L8g2)9J5c8R3`.`.。

22/25 — ExploitDB
=============
各种漏洞的存档 ExploitDB 0e3K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2W2P5s2m8D9L8$3W2@1i4K6u0V1k6r3u0Q4x3X3g2U0L8$3#2Q4x3V1j5`.。
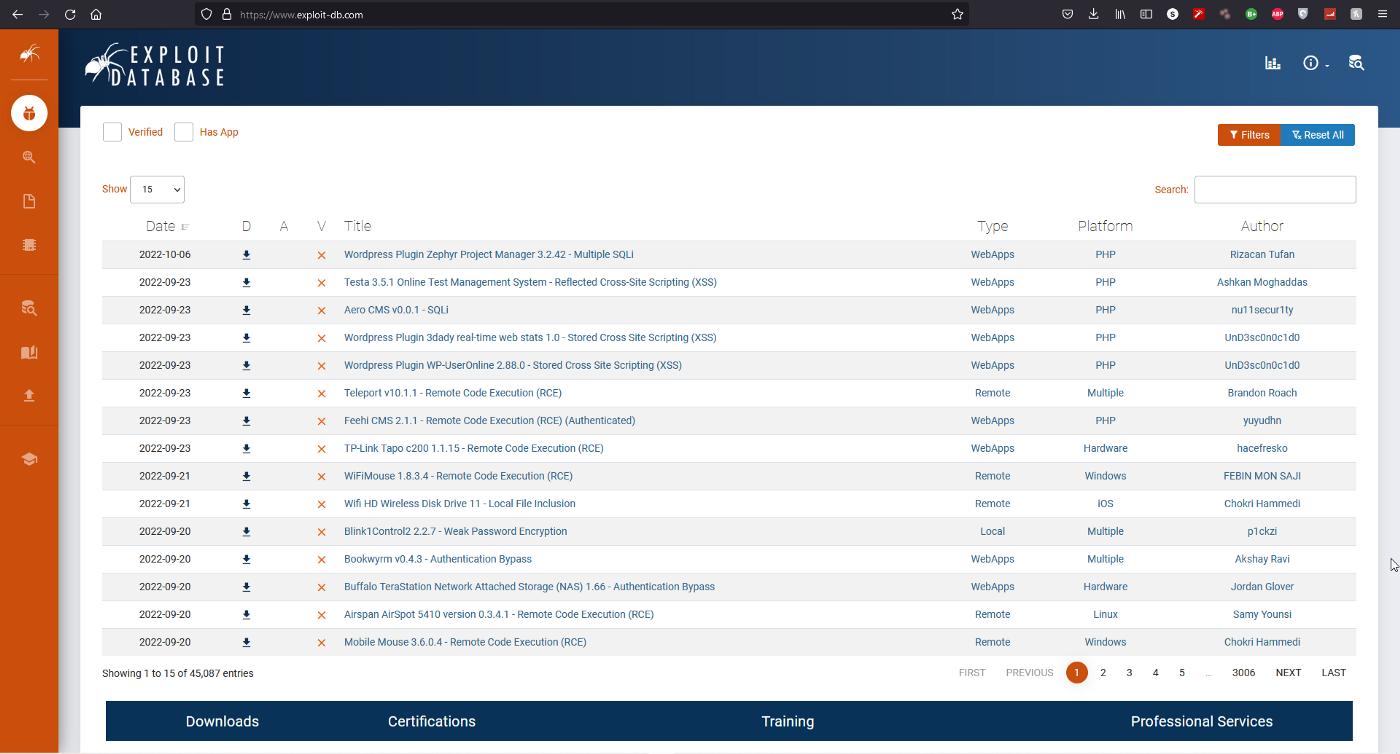
23/25 — CVE
===========
CVE 网站的创建是为了识别、定义和分类公开披露的网络安全漏洞 CVE 269K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6U0N6X3g2Q4x3X3g2E0K9i4c8J5k6g2)9J5k6h3!0J5k6#2)9J5c8R3`.`.。
24/25 — PulseDive
=================
搜索威胁情报(PulseDive 网站链接)。
25/25 — PulseDive
浏览最新的漏洞和漏洞利用 e7bK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6H3j5h3y4C8k6i4c8K6N6r3!0J5L8i4y4W2j5%4g2J5K9i4c8&6i4K6u0W2j5$3!0E0i4K6u0r3。
可gz TIPFactory情报工厂 获取其他内容
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课