-
-
[原创]远程桌面无法访问远程电脑上的USB证书
-
发表于:
2023-2-23 14:20
7713
-
最近有个需求,需要把EV签名放到公司本地服务器上面去,这样大家都可以通过远程来使用EV签名.
在服务器(windows 10 x64)上面装上SafeNet,插上USB证书,正常识别到证书.
但是通过远程桌面连接到服务器的时候,SafeNet无法识别到证书.
网上查了资料,问题出在 C:\Windows\System32\WinSCard.dll 的 SCardEstablishContex 函数中.下层调用了 RedirectionContextIsLocal 函数,看名字应该是判断上下文是否是本地:
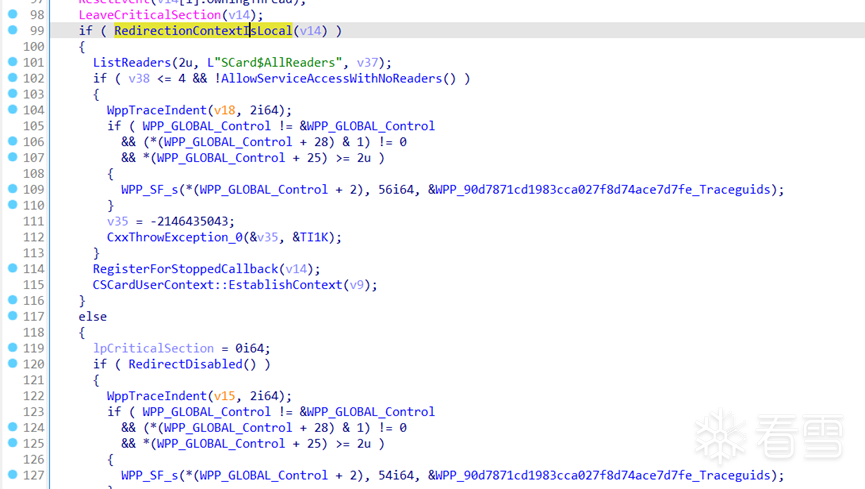
动态跟一下,远程桌面时返回0,本地时返回1.
确定了问题就是这个函数,由于这个函数有多个地方调用,所以patch这个函数的内部,patch方法如下:
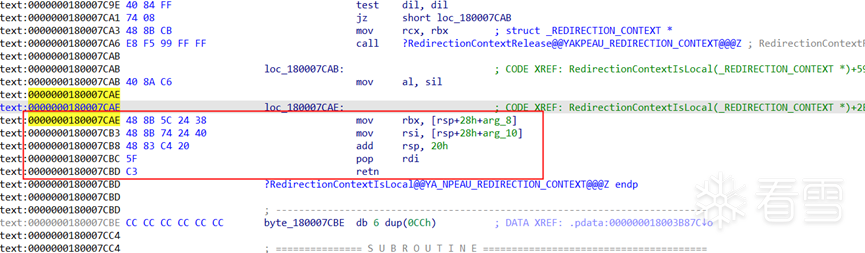
在 0000000180007CAE 这句代码的地方插入add al,1 原本的代码往后面移动2个字节,修改之后如下:
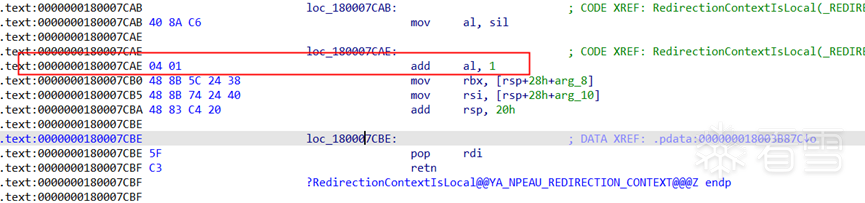
这样修改之后,在任何情况下 RedirectionContextIsLocal 返回的值都是大于0的.
绕过windows的文件保护机制,替换 C:\Windows\System32\WinSCard.dll
管理员权限运行cmd,输入如下指令后就可以替换了.
C:\Windows\system32>takeown /f C:\Windows\System32\WinSCard.dll
C:\Windows\system32>icacls C:\Windows\System32\WinSCard.dll /grant administrators:F
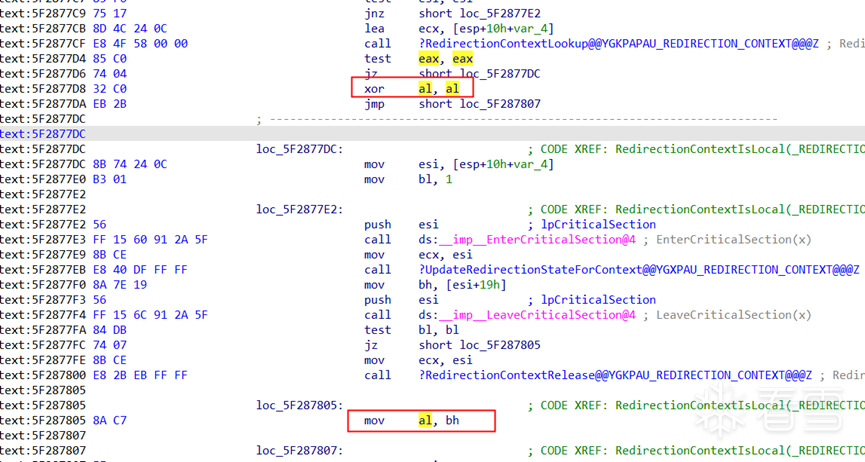
如果你的工具是wow64的,那么相同的操作处理C:\Windows\SysWOW64\WinSCard.dll即可,由于 RedirectionContextIsLocal 后面没有空白空间,所以不能用前面的patch方法,需要将如下两个地方的指令改为add al,1
另外,还有一种解决方案:在服务器上面安装虚拟机,通过远程桌面操作虚拟机是可以识别USB证书的.
参考资料:
d46K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8Y4q4I4i4K6g2X3x3e0j5&6y4e0t1H3x3U0y4Q4x3V1k6S2M7Y4c8A6j5$3I4W2i4K6u0r3k6r3g2@1j5h3W2D9M7#2)9J5c8U0p5J5x3e0x3%4y4U0f1@1z5g2)9K6c8Y4y4H3L8g2)9K6c8o6p5H3x3o6q4Q4x3X3f1J5x3e0l9I4i4K6u0W2x3K6l9H3x3g2)9J5k6e0j5$3y4e0m8Q4x3X3f1I4i4K6t1$3j5h3#2H3i4K6y4n7N6i4c8E0i4K6g2X3L8h3g2V1K9i4g2E0i4K6y4p5k6r3W2K6N6s2u0A6j5Y4g2@1k6g2)9J5k6i4m8U0i4K6g2X3M7X3g2D9k6i4k6S2L8Y4c8Q4x3X3g2F1L8$3&6W2i4K6u0V1N6r3q4K6K9#2)9J5k6r3u0D9L8$3N6Q4x3X3b7J5i4K6t1#2y4@1g2V1k6h3k6S2N6h3I4@1i4K6t1#2y4@1g2o6g2q4u0x3d9g2y4f1i4K6t1#2y4@1g2d9j5i4c8W2i4K6u0V1x3g2)9J5k6o6p5J5x3e0x3%4y4U0f1@1z5g2)9J5k6r3u0D9L8$3N6Q4x3X3b7#2z5o6p5%4x3K6p5^5i4K6u0W2M7r3y4Q4y4h3k6J5k6h3I4W2N6X3q4F1N6q4)9#2k6X3c8W2k6X3q4#2L8s2c8Q4x3U0k6S2L8i4m8Q4x3@1u0V1k6i4m8@1K9q4)9#2k6U0q4Q4x3X3c8#2N6r3#2Q4y4h3k6K6L8%4g2J5j5$3g2Q4x3@1c8V1K9i4y4@1M7X3W2T1N6i4c8W2i4K6u0W2M7r3y4Q4y4h3k6J5k6h3I4W2N6X3q4F1N6q4)9J5k6h3&6G2L8X3g2Q4x3X3c8@1j5i4y4C8i4K6u0V1j5X3I4G2k6#2)9J5k6o6u0Q4x3U0f1%4c8h3c8W2k6X3q4#2L8s2c8Q4x3U0f1%4c8f1y4f1f1V1I4u0f1#2c8Q4x3U0f1%4c8g2u0S2N6r3g2Q4x3X3b7I4i4K6u0V1x3e0t1I4x3K6M7$3y4e0b7&6i4K6u0V1j5X3I4G2k6#2)9J5k6o6f1^5x3e0M7K6x3e0S2Q4x3X3g2H3j5#2)9#2k6Y4u0W2L8r3g2$3j5h3&6@1i4K6g2X3k6r3g2X3j5i4g2D9N6q4)9J5y4X3q4E0M7q4)9K6b7Y4g2@1L8g2)9#2k6Y4u0W2L8r3g2$3j5h3&6@1i4K6g2X3K9h3&6V1k6i4S2Q4x3@1b7J5
c56K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8Y4A6&6i4K6g2X3M7%4c8J5K9i4k6W2i4K6g2X3x3U0l9I4x3W2)9J5c8X3q4J5N6r3W2U0L8r3g2Q4x3V1k6V1k6i4c8S2K9h3I4K6i4K6u0r3y4K6V1@1y4K6l9^5x3U0V1`.
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
最后于 2023-2-23 14:23
被xxyiyi编辑
,原因: