最近工作上让做个app的复测,把apk发我后,开始尝试挂代理抓包,结果发现抓不到
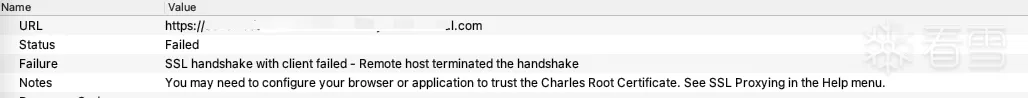

以为是证书没弄好,想着前几天不是刚导入了吗(雾)。又重新导入了下还是不行。然后各种lsp模块,objection都不行,r0capture也没数据。
然后jadx看了下,全是flutter字样,才想起来和flutter有关。

然后就开始各种找。https://bbs.kanxue.com/thread-261941.htm
根据上面文章找到关键函数handshake.cc386行
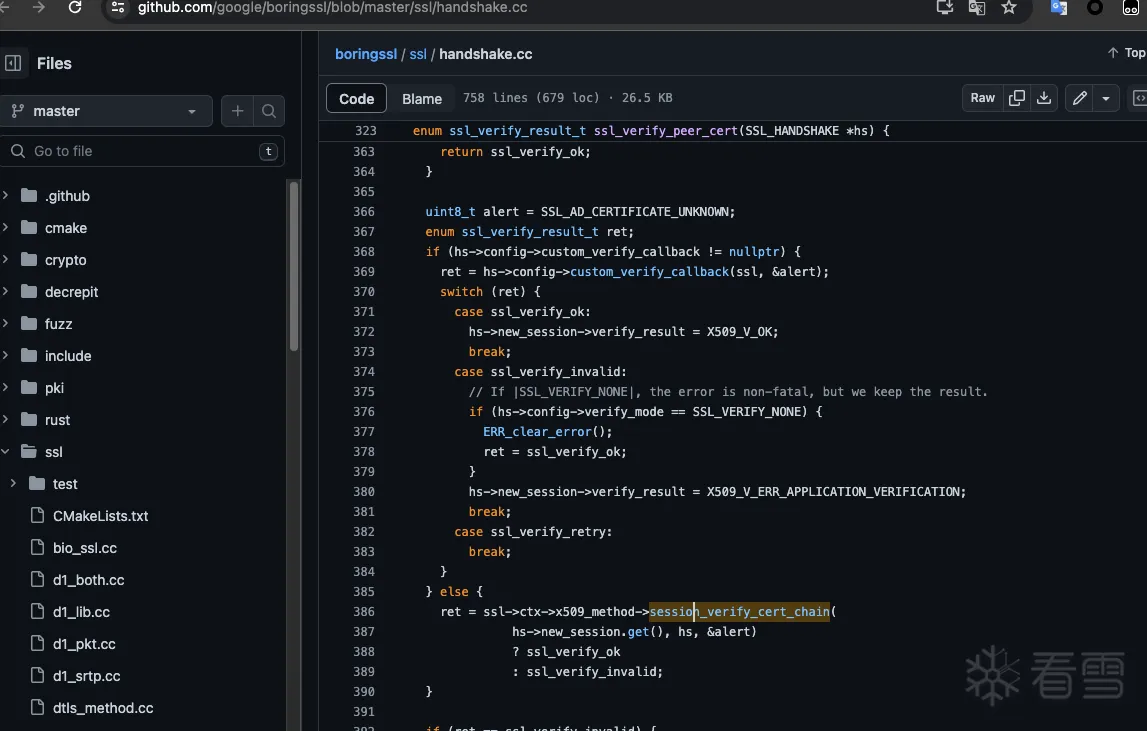
session_verify_cert_chain函数在第356行的ssl_x509.cc中被定义

然后根据https://bbs.kanxue.com/thread-261941.htm 这篇文章特征找,但是这个是32位的,所以在app安装的时候指定32位安装
接下来就是找
往上翻找
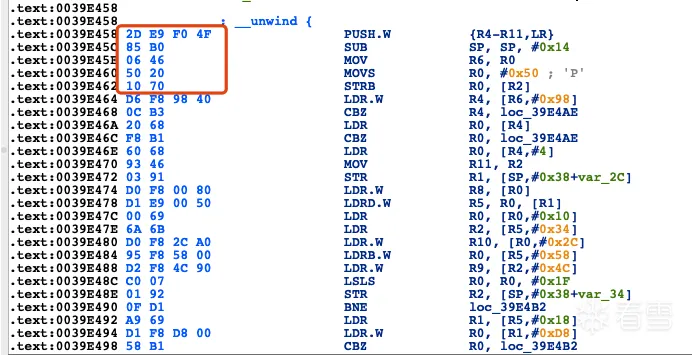
然后启动就可以抓包了

搜索ssl_client
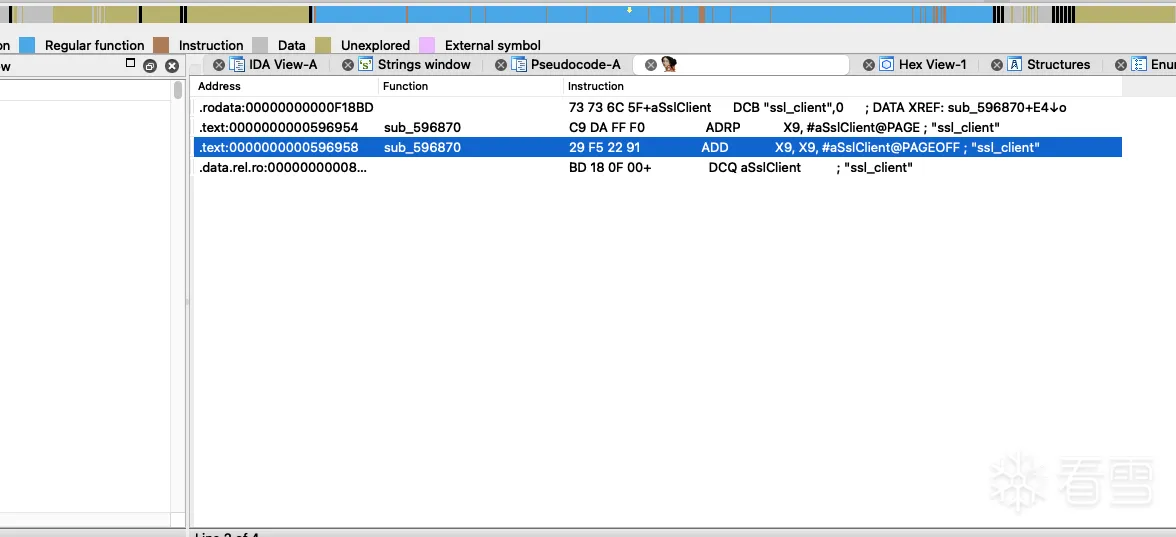
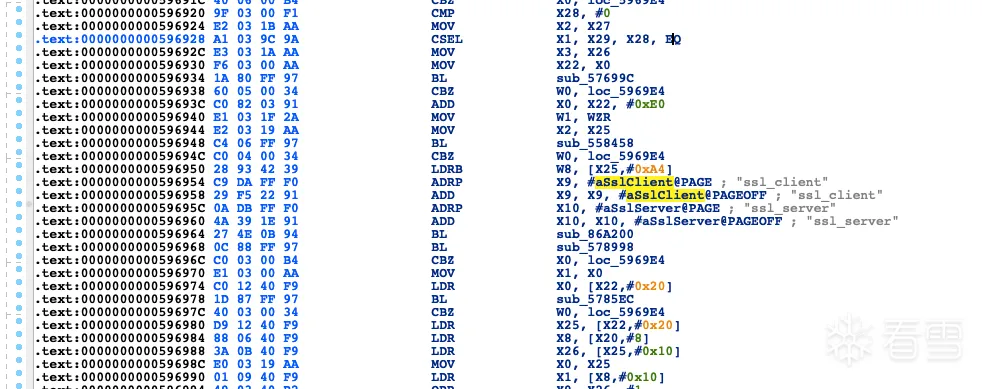
照例往上找

然后就找到了这些
然后写脚本
然后发现报错了
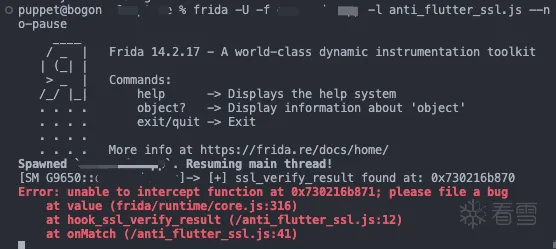
把hook_ssl_verify_result(address.add(0x01))改为hook_ssl_verify_result(address)就可以正常使用了

ee0K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2B7K9h3q4F1M7$3S2#2i4K6u0W2j5$3!0E0i4K6u0r3M7q4)9J5c8X3q4V1j5e0p5H3k6o6t1&6y4K6k6X3x3R3`.`.
a02K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6E0M7q4)9J5k6i4N6W2K9i4S2A6L8W2)9J5k6i4q4I4i4K6u0W2j5$3!0E0i4K6u0r3M7#2)9J5c8Y4m8j5M7r3k6j5d9#2)9J5k6p5g2*7x3r3^5%4x3r3j5K6j5Y4q4r3N6i4g2r3k6H3`.`.
https://bbs.kanxue.com/thread-261941.htm
ce5K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2L8Y4k6A6M7$3!0Q4x3X3g2W2N6g2)9J5c8U0t1H3x3e0W2Q4x3V1j5H3z5q4)9J5c8U0p5K6i4K6u0r3K9h3&6@1k6i4u0U0k6i4m8@1K9h3&6Y4i4K6u0V1N6s2u0S2k6X3k6A6j5#2)9J5k6r3k6J5L8$3#2Q4x3X3c8S2L8X3c8J5L8$3W2V1i4K6u0V1k6X3I4#2N6s2c8W2M7W2)9J5k6r3q4H3M7r3I4A6j5$3q4@1K9h3!0F1M7#2)9J5c8R3`.`.
以上四篇文章均是和flutter证书校验相关
adb install --abi armeabi-v7a <path to apk>
adb install --abi armeabi-v7a <path to apk>
function hook_ssl_verify_result(address) {
Interceptor.attach(address, {
onEnter: function(args) {
console.log("Disabling SSL validation")
},
onLeave: function(retval) {
console.log("Retval: " + retval);
retval.replace(0x1);
}
});
}
function hookFlutter() {
var m = Process.findModuleByName("libflutter.so");
var pattern = "2D E9 F0 4F 85 B0 06 46 50 20 10 70";
var res = Memory.scan(m.base, m.size, pattern, {
onMatch: function(address, size){
console.log('[+] ssl_verify_result found at: ' + address.toString());
// Add 0x01 because it's a THUMB function
// Otherwise, we would get 'Error: unable to intercept function at 0x9906f8ac; please file a bug'
hook_ssl_verify_result(address.add(0x01));
},
onError: function(reason){
console.log('[!] There was an error scanning memory');
},
onComplete: function() {
console.log("All done")
}
});
}
function hook_ssl_verify_result(address) {
Interceptor.attach(address, {
onEnter: function(args) {
console.log("Disabling SSL validation")
},
onLeave: function(retval) {
console.log("Retval: " + retval);
retval.replace(0x1);
}
});
}
function hookFlutter() {
var m = Process.findModuleByName("libflutter.so");
var pattern = "2D E9 F0 4F 85 B0 06 46 50 20 10 70";
var res = Memory.scan(m.base, m.size, pattern, {
onMatch: function(address, size){
console.log('[+] ssl_verify_result found at: ' + address.toString());
// Add 0x01 because it's a THUMB function
// Otherwise, we would get 'Error: unable to intercept function at 0x9906f8ac; please file a bug'
hook_ssl_verify_result(address.add(0x01));
},
onError: function(reason){
console.log('[!] There was an error scanning memory');
},
onComplete: function() {
console.log("All done")
}
});
}
.text:0000000000596870 FF C3 01 D1 SUB SP, SP,
.text:0000000000596874 FD 7B 01 A9 STP X29, X30, [SP,
.text:0000000000596878 FC 6F 02 A9 STP X28, X27, [SP,
.text:000000000059687C FA 67 03 A9 STP X26, X25, [SP,
.text:0000000000596880 F8 5F 04 A9 STP X24, X23, [SP,
.text:0000000000596884 F6 57 05 A9 STP X22, X21, [SP,
.text:0000000000596888 F4 4F 06 A9 STP X20, X19, [SP,
.text:000000000059688C 08 0A 80 52 MOV W8,
.text:0000000000596890 48 00 00 39 STRB W8, [X2]
.text:0000000000596870 FF C3 01 D1 SUB SP, SP,
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课