
能力值:
 ( LV2,RANK:15 )
( LV2,RANK:15 )
|
-
-
2 楼
先按照这个文章脱出easy-dex,63eK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6T1L8r3!0Y4i4K6u0W2j5%4y4V1L8W2)9J5k6h3&6W2N6q4)9J5c8X3q4S2x3U0f1J5z5o6R3%4y4K6V1^5y4#2)9J5c8X3q4J5N6r3W2U0L8r3g2Q4x3V1k6V1k6i4c8S2K9h3I4K6i4K6u0r3x3e0t1J5x3o6V1^5z5e0M7J5i4K6u0o6i4@1f1@1i4@1u0p5i4@1p5H3i4@1f1@1i4@1u0o6i4K6W2m8i4@1f1#2i4K6S2r3i4K6V1I4i4@1f1%4i4K6S2q4i4@1t1H3i4@1f1#2i4K6W2o6i4@1p5^5k6h3q4K6P5g2)9J5k6r3c8W2P5q4!0q4z5g2)9^5y4#2)9^5b7#2!0q4z5g2)9&6c8q4!0m8x3R3`.`.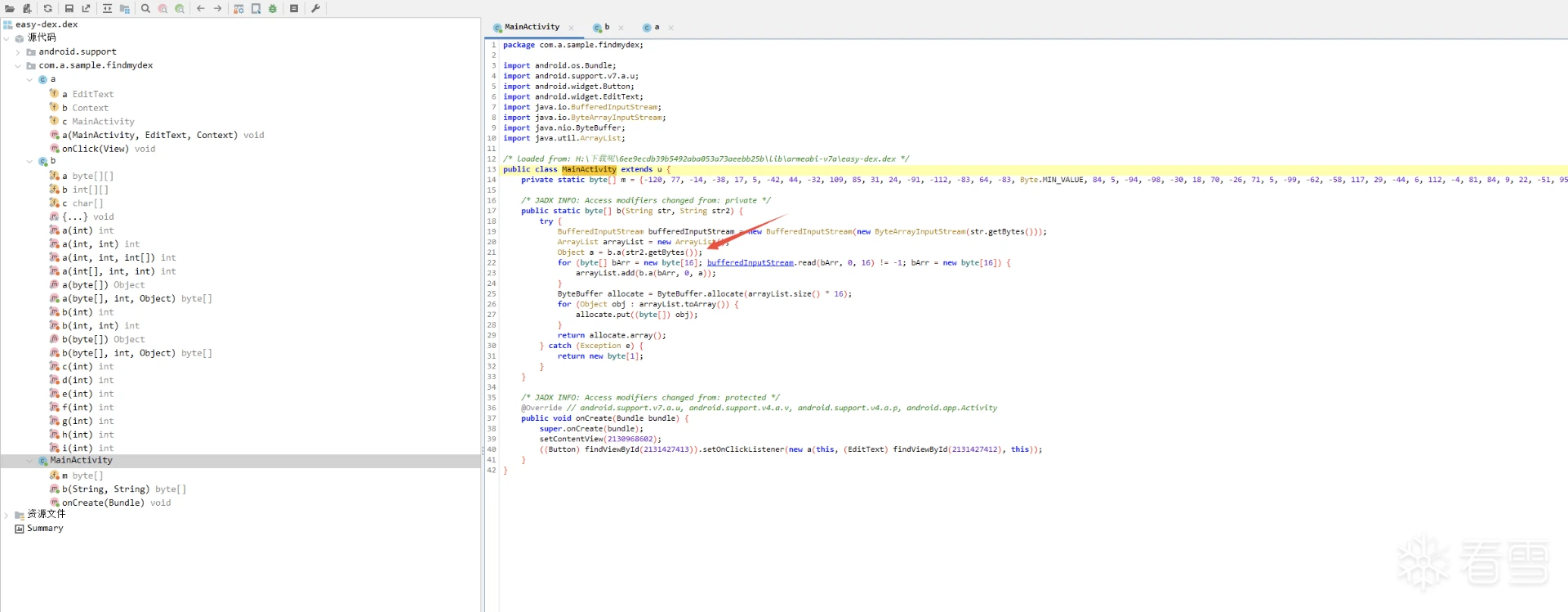 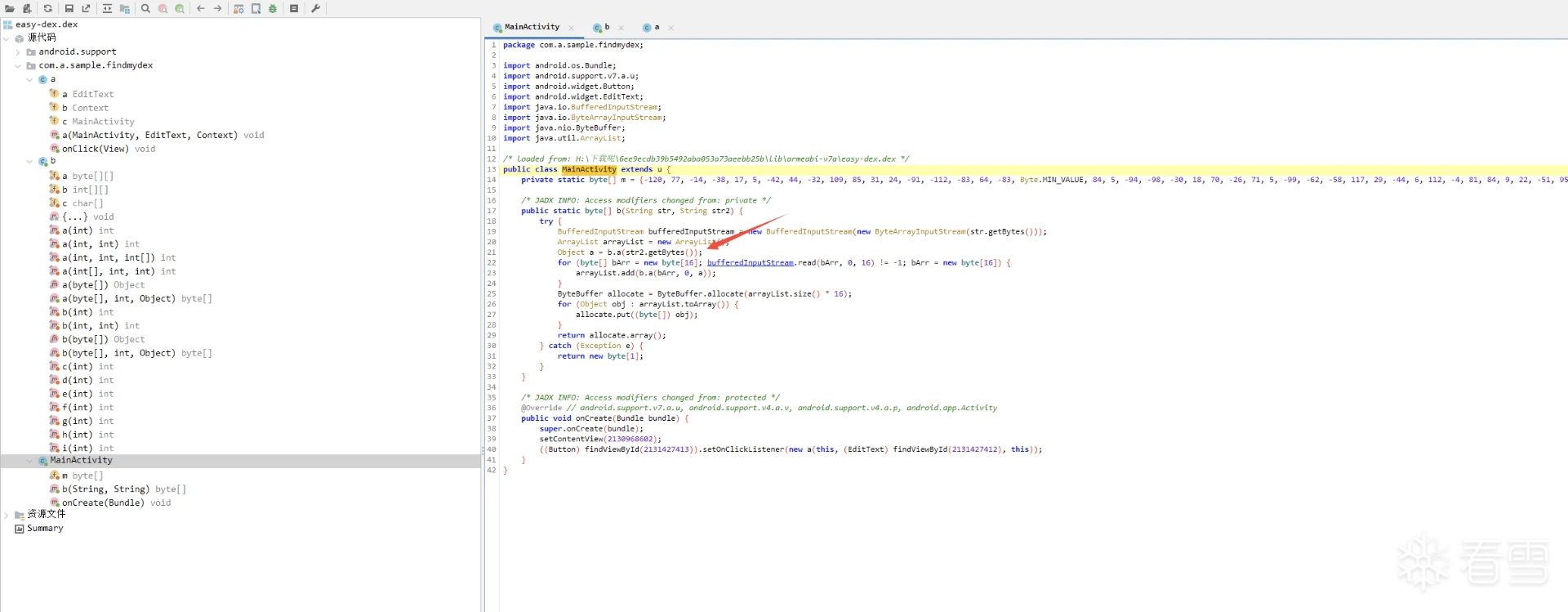 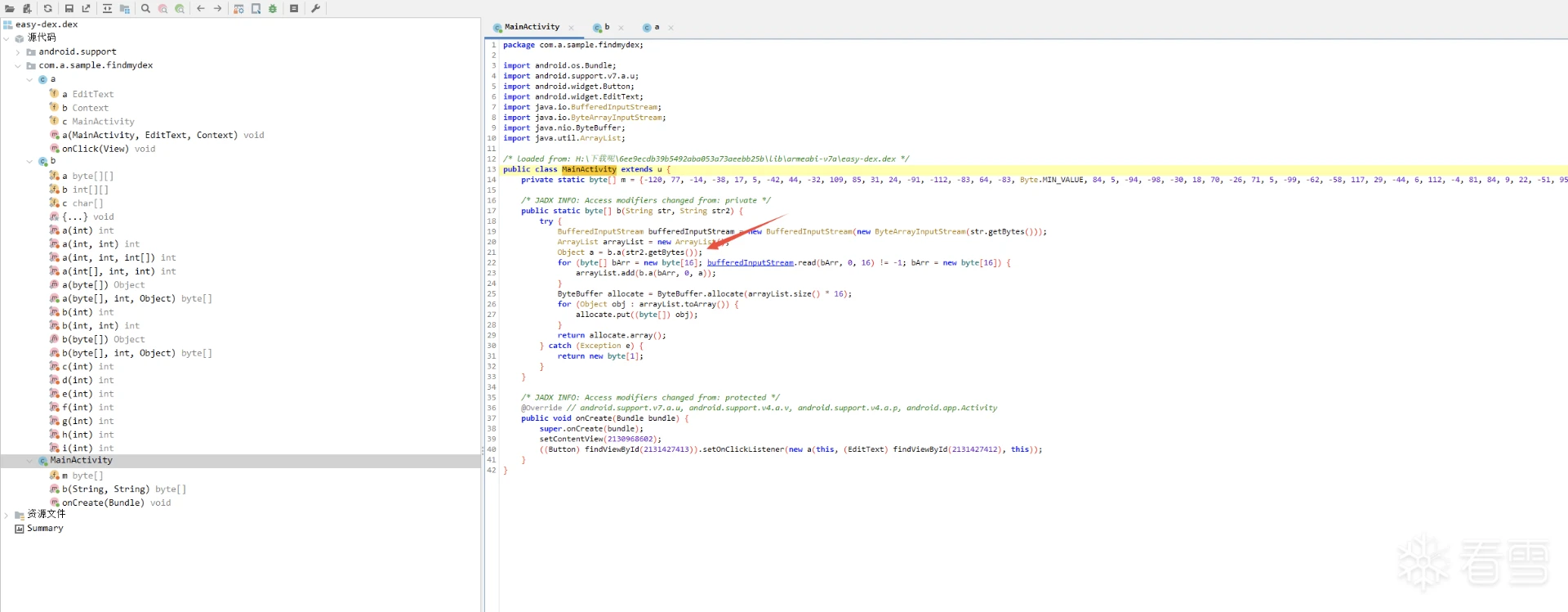 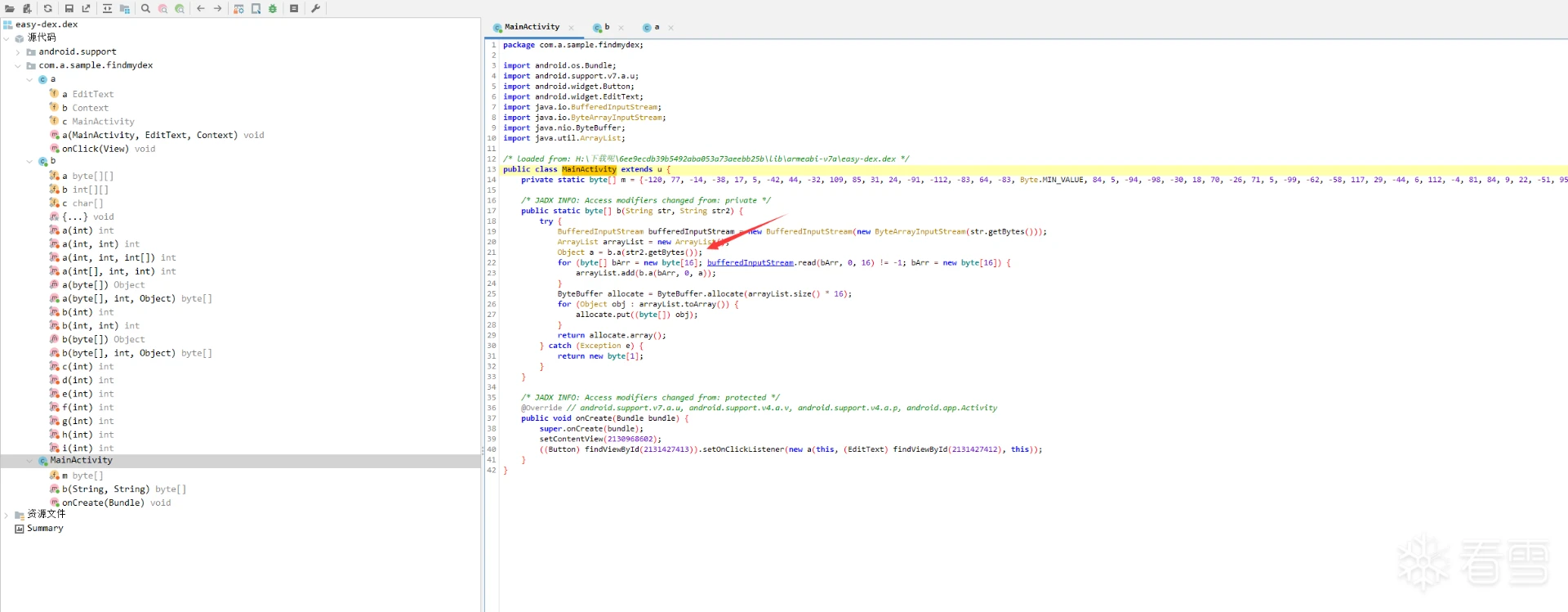 的MainActivity(图一) 的MainActivity(图一) Object a = b.a(str2.getBytes()); 实际上你输入的是在这个b.a方法加密的,随后到b.a方法里面查看,想要识别出来常规算法就得知道算法的特征,类似于常量表之类的,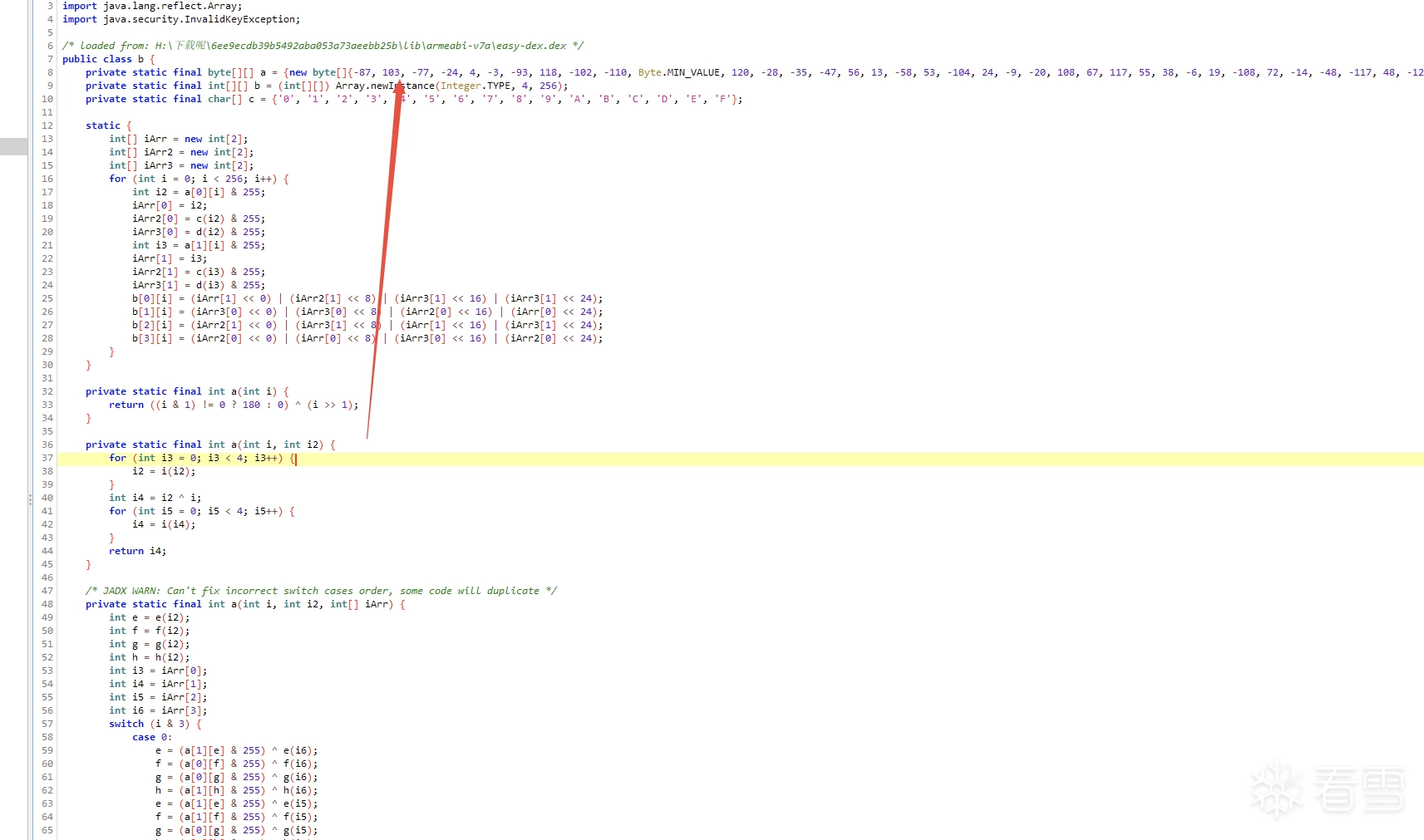 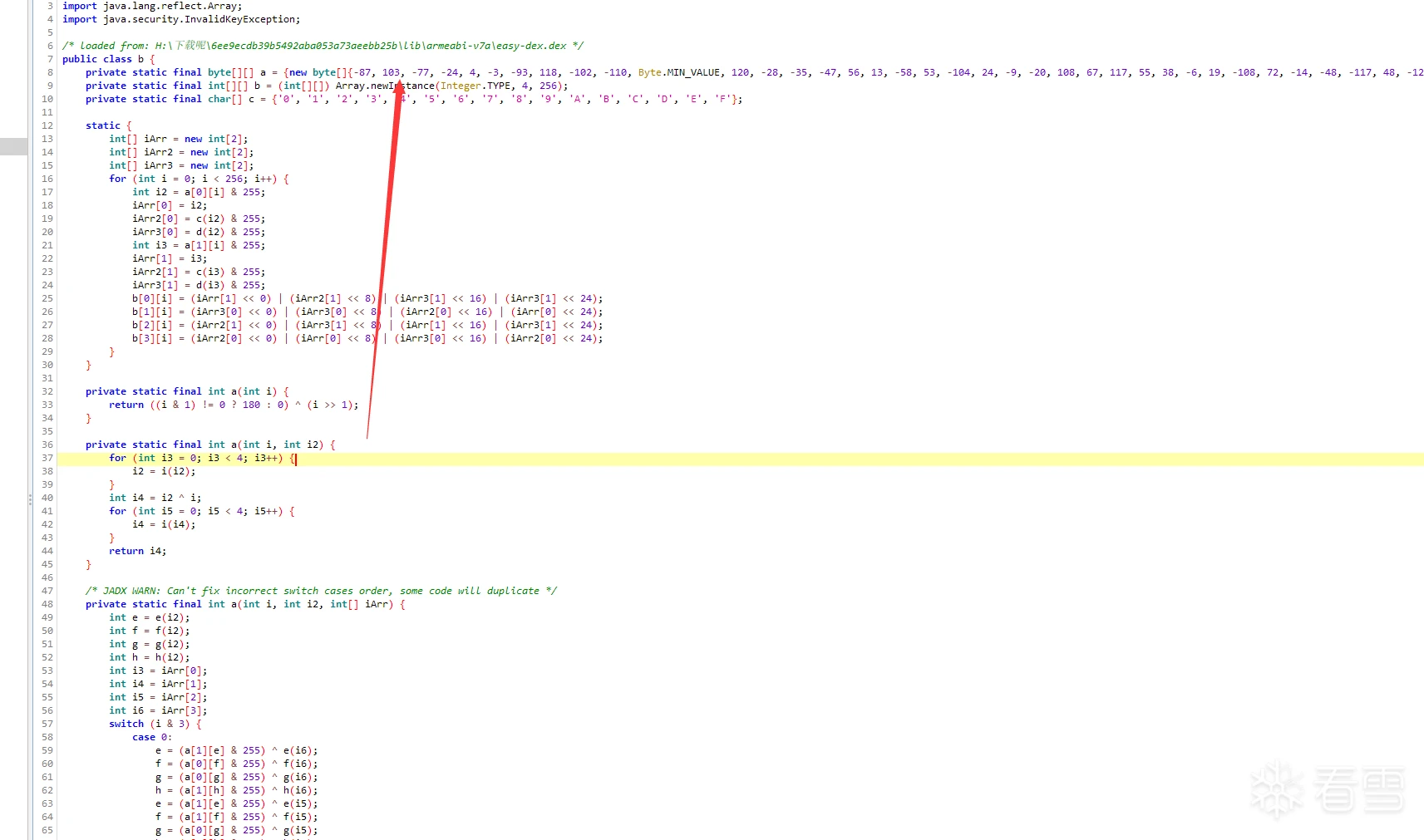 b方法的算法表特征就在第一行(图二) b方法的算法表特征就在第一行(图二) private static final byte[][] a = {new byte[]{-87, 103, -77, -24, 4, -3, -93, 118, -102, -110, By上网查询可知道他是twofish的加密表84cK9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6%4N6%4N6Q4x3X3g2G2M7Y4W2^5i4K6u0V1k6h3#2T1k6h3c8V1k6h3c8Q4x3X3g2U0L8$3#2Q4x3V1k6V1L8$3y4Q4x3V1k6@1N6$3!0X3K9i4y4Z5i4K6g2X3z5r3y4Q4y4h3k6K6L8%4g2J5j5$3g2Q4x3X3g2Z5N6r3#2D9i4K6u0o6K9X3q4$3j5g2!0q4y4g2)9^5c8q4)9^5x3g2!0q4z5q4!0n7c8W2)9&6b7W2!0q4y4g2)9^5z5q4!0n7y4W2!0q4z5q4!0n7c8q4!0m8b7#2!0q4y4q4!0n7z5q4!0n7b7g2!0q4y4g2)9^5c8q4)9^5x3g2!0q4y4g2)9^5y4g2!0m8c8q4!0q4z5q4!0n7c8W2)9&6b7W2!0q4y4g2)9^5z5q4!0n7y4W2!0q4y4g2!0n7x3q4!0n7x3g2!0q4y4W2)9&6z5q4!0m8c8W2!0q4z5q4!0n7c8W2)9&6z5g2!0q4z5g2)9^5y4#2)9^5b7#2!0q4z5g2)9&6c8q4!0m8x3W2!0q4y4#2)9&6b7g2)9^5y4s2g2A6L8Y4b7^5i4K6g2X3N6l9`.`. q0还有uint8_t q1,具体的加密代码肯定也不是出题者自己写的,搜索github Incorrect key length twofish(对应着easy-dex的这一部分,直接搜这一部分的也行 synchronized (b.class) {
if (bArr == null) {
throw new InvalidKeyException("Empty key");
}
int length = bArr.length;
if (length != 8 && length != 16 && length != 24 && length != 32) {
throw new InvalidKeyException("Incorrect key length");
}),可以找到原有算法,接下来就是先一一比较大体相似之处,随后确定这个是twofish算法了
|

|
|