#wangdeifa Shaeld算法Chomper黑盒调用
文章仅用来展示Chomper的能力,请勿用于非法用途
从安卓还原算法过程得知需要初始化设置一个Token
这里也不需要其他多余的部环境操作。
chomper 地址:b98K9s2c8@1M7s2y4Q4x3@1q4Q4x3V1k6Q4x3V1k6Y4K9i4c8Z5N6h3u0Q4x3X3g2U0L8$3#2Q4x3V1k6K6L8r3g2V1k6$3g2Z5y4s2N6Q4x3V1k6U0K9r3!0E0M7r3g2J5
从frida-trace无法得知初始化做了什么,只能看到具体的算法调用逻辑。
无法从frida-trace得知初始化的值,只能在dlopen 之后做
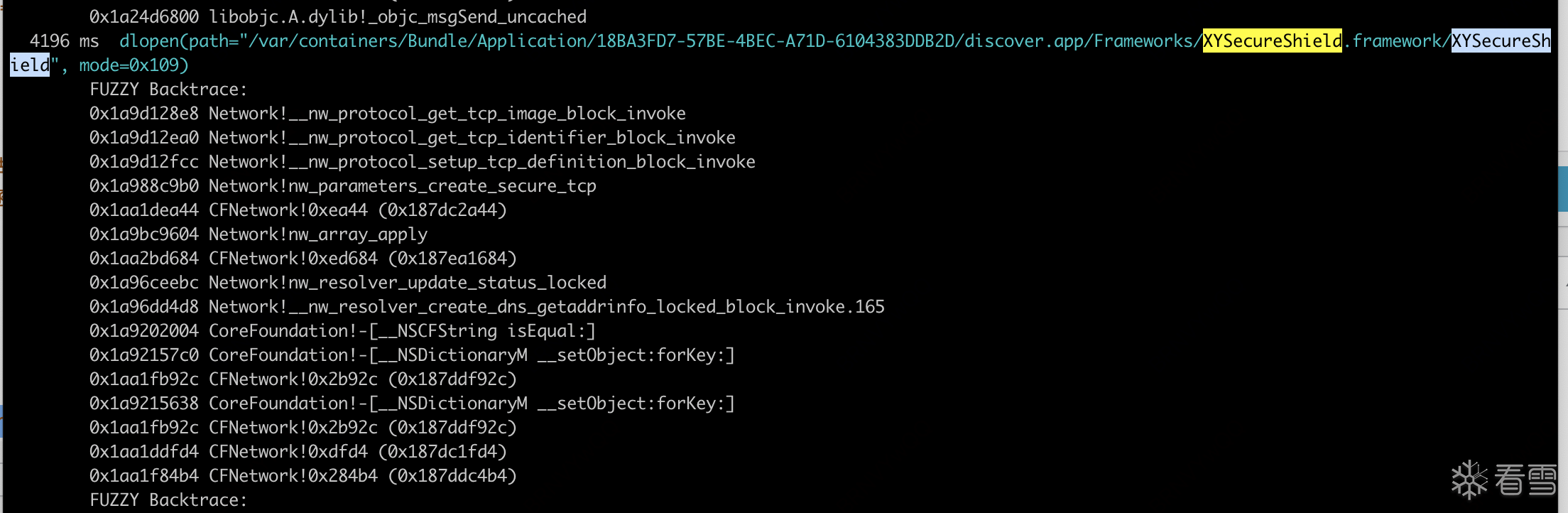
代码如下:从frida-trace得知wangdeifa的相关初始化函数。
基础框架请看上一篇文章 某王得发sig13-ios算法Chomper黑盒调用
如下代码就初始化完成
##主动调用
这里还是比较复杂一点,根据frida-trace的代码得知,需要传入一个NSMutableURLRequest对象,需要构造。问下ai
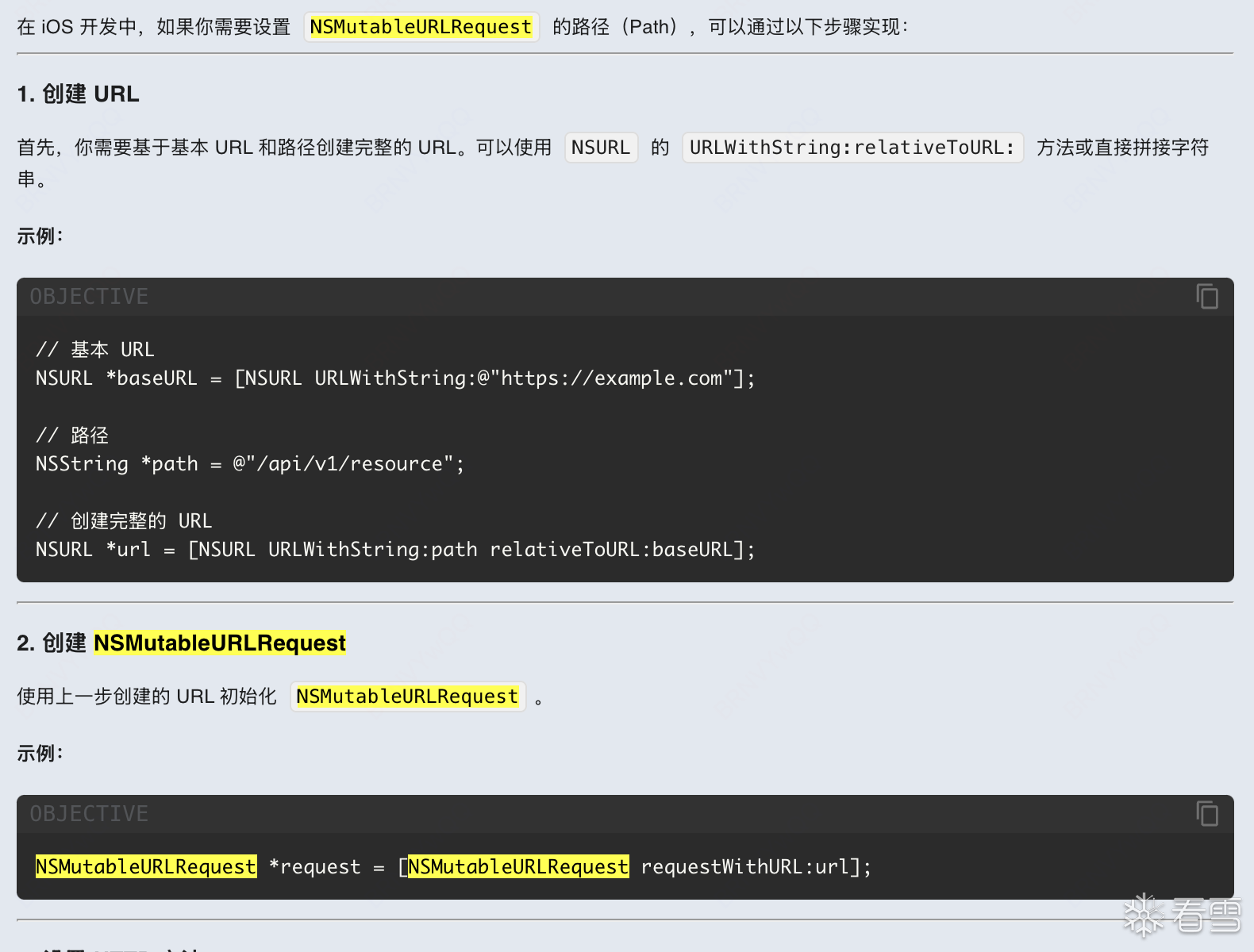
如下代码就构造好req对象。
直接使用作者的pyobj2nsobj,如下代码就是将py的dict转为oc里面的dic
下面就是算法入参
上边的构造传入,并主动调用之后就会得出结果。
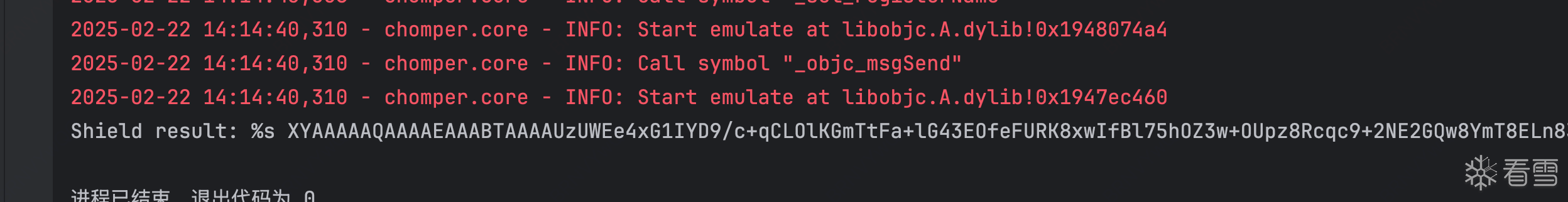
/* TID 0x103 */
863 ms +[wangdeifa reqAuthorityWithHeaders:<CFBasicHash 0x283b31740 [0x201426858]>{type = mutable dict, count = 10,
entries =>
0 : Accept-Language = zh-Hans;q=1, en;q=0.9
1 : X-B3-TraceId = a4e86b06fbe691f3
2 : Connection = Keep-Alive
3 : Mode = rawIp
4 : X-raw-ptr = 0
7 : Host = edith.wangdeifa.com
9 : User-Agent = wangdeifa/7.1 (iPhone; iOS 16.7.10; Scale/2.00) Resolution/750*1334 Version/7.1 Build/7010202 Device/(Apple Inc.;iPhone10,1) NetType/WiFi
10 : wangdeifa-platform-info = platform=iOS&version=7.1&build=7010202&deviceId=C53A986E-875F-4FE2-9C49-BC1DD280E337&bundle=com.xingin.discover
11 : Accept-Encoding = br;q=1.0, gzip;q=1.0, compress;q=0.5
12 : wangdeifa-common-params = app_id=ECFAAF02&build=7010202&deviceId=C53A986E-875F-4FE2-9C49-BC1DD280E337&device_fingerprint=2025022115160335e8c03be20ba5b6b300c149f76fc3f50123d7e2b8cb1cf6&device_fingerprint1=2025022115160335e8c03be20ba5b6b300c149f76fc3f50123d7e2b8cb1cf6&fid=1740122163-0-0-970427ae7226e33071bdefb4866c668a&identifier_flag=0&lang=zh-Hans&launch_id=761816146&platform=iOS&project_id=ECFAAF&sid=session.1740122519639795203705&t=1740123589&tz=Asia/Shanghai&uis=light&version=7.1
}
request:0x282c35e00 bodyData:nil]
/* TID 0x103 */
863 ms +[wangdeifa reqAuthorityWithHeaders:<CFBasicHash 0x283b31740 [0x201426858]>{type = mutable dict, count = 10,
entries =>
0 : Accept-Language = zh-Hans;q=1, en;q=0.9
1 : X-B3-TraceId = a4e86b06fbe691f3
2 : Connection = Keep-Alive
3 : Mode = rawIp
4 : X-raw-ptr = 0
7 : Host = edith.wangdeifa.com
9 : User-Agent = wangdeifa/7.1 (iPhone; iOS 16.7.10; Scale/2.00) Resolution/750*1334 Version/7.1 Build/7010202 Device/(Apple Inc.;iPhone10,1) NetType/WiFi
10 : wangdeifa-platform-info = platform=iOS&version=7.1&build=7010202&deviceId=C53A986E-875F-4FE2-9C49-BC1DD280E337&bundle=com.xingin.discover
11 : Accept-Encoding = br;q=1.0, gzip;q=1.0, compress;q=0.5
12 : wangdeifa-common-params = app_id=ECFAAF02&build=7010202&deviceId=C53A986E-875F-4FE2-9C49-BC1DD280E337&device_fingerprint=2025022115160335e8c03be20ba5b6b300c149f76fc3f50123d7e2b8cb1cf6&device_fingerprint1=2025022115160335e8c03be20ba5b6b300c149f76fc3f50123d7e2b8cb1cf6&fid=1740122163-0-0-970427ae7226e33071bdefb4866c668a&identifier_flag=0&lang=zh-Hans&launch_id=761816146&platform=iOS&project_id=ECFAAF&sid=session.1740122519639795203705&t=1740123589&tz=Asia/Shanghai&uis=light&version=7.1
}
request:0x282c35e00 bodyData:nil]
let dlopen = Module.findExportByName(null, "dlopen");
Interceptor.attach(dlopen, {
onEnter: function (args) {
this.hook = false
if ((args[0].readUtf8String() + '').indexOf("XYSecureShield") > -1) {
this.hook = true;
}
}, onLeave: function (retval) {
if (this.hook) {
var methodName = "+ setup:build:key:";
var hooking = ObjC.classes["wangdeifa"][methodName];
// console.log(hooking, 'hooking')
Interceptor.attach(hooking.implementation, {
onEnter: function (args) {
console.log(ObjC.Object(args[2]), ObjC.Object(args[3]), ObjC.Object(args[4]))
}, onLeave: function (returnValues) {
}
});
var methodName = "+ setToken:";
var hooking = ObjC.classes["wangdeifa"][methodName];
// console.log(hooking, 'hooking')
Interceptor.attach(hooking.implementation, {
onEnter: function (args) {
console.log("setToken", ObjC.Object(args[2]))
}, onLeave: function (returnValues) {
}
});
let module_name = "XYSecureShield"
var base_addr = Module.findBaseAddress(module_name);
// console.log(hooking, 'hooking')
Interceptor.attach(base_addr.add(0x969C), {
onEnter: function (args) {
console.log("0x969C")
}, onLeave: function (returnValues) {
}
});
}
}
});
let dlopen = Module.findExportByName(null, "dlopen");
Interceptor.attach(dlopen, {
onEnter: function (args) {
this.hook = false
if ((args[0].readUtf8String() + '').indexOf("XYSecureShield") > -1) {
this.hook = true;
}
}, onLeave: function (retval) {
if (this.hook) {
var methodName = "+ setup:build:key:";
var hooking = ObjC.classes["wangdeifa"][methodName];
// console.log(hooking, 'hooking')
Interceptor.attach(hooking.implementation, {
onEnter: function (args) {
console.log(ObjC.Object(args[2]), ObjC.Object(args[3]), ObjC.Object(args[4]))
}, onLeave: function (returnValues) {
}
});
var methodName = "+ setToken:";
var hooking = ObjC.classes["wangdeifa"][methodName];
// console.log(hooking, 'hooking')
Interceptor.attach(hooking.implementation, {
onEnter: function (args) {
console.log("setToken", ObjC.Object(args[2]))
}, onLeave: function (returnValues) {
[培训]内核驱动高级班,冲击BAT一流互联网大厂工作,每周日13:00-18:00直播授课
最后于 2025-4-1 09:01
被mb_aoooaosd编辑
,原因: