这次的PC端初赛整体难度不高,没有涉及到游戏安全的内容,题目就是一个CTF的解题模式,不过这也给了我这个小白完整解出来题目的机会哈哈,下面给出我的解题思路,有问题还请各位大佬指出
看了几眼,发现没有壳,题目就是类似CTF的flag checker类型
sub_1400010D0里起了一个线程,里面有一些常见的反调试

sub_140001000里解密字符串初始化了一个base58的表,调试可以得到
abcdefghijkmnopqrstuvwxyzABCDEFGHJKLMNPQRSTUVWXYZ1234567890!@+/
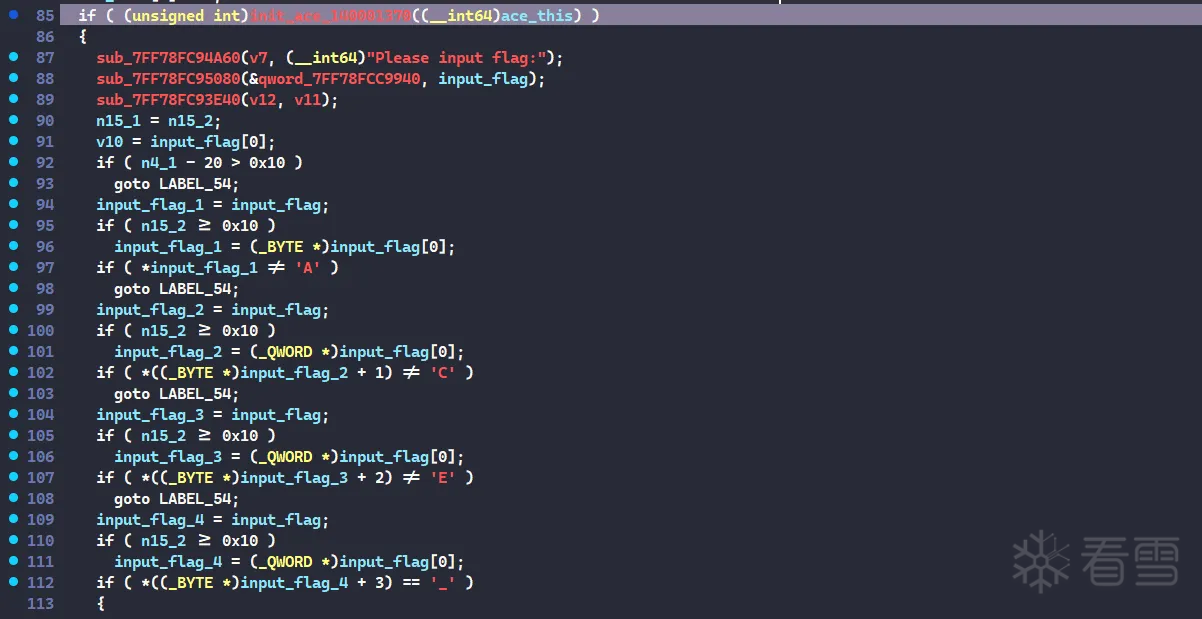
然后main函数里初始化ACE的驱动程序,初始化成功后输入flag进行验证,前4个字符必须为ACE_
解密了一个字符串
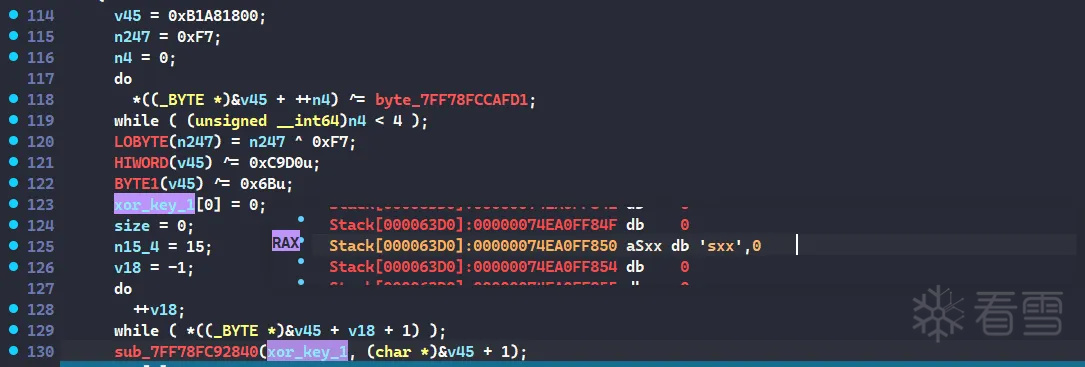
取4个字符后的内容进行base58 encode,里面还会在最后加一个@字符,并逆序字符串

然后和前面解密的sxx进行异或加密
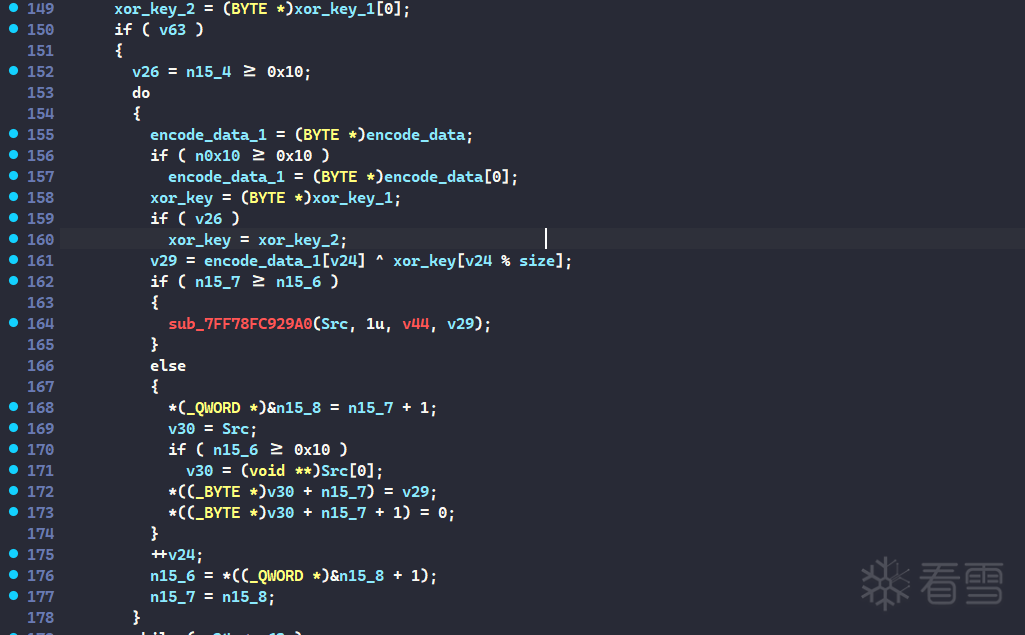
剩下的check都在驱动里

驱动还是上了tvm,我这里没有驱动调试的环境,因此整个做题流程都是静态分析(guessing time!),毕竟出题人应该不会真的让选手日tvm吧,所以check逻辑应该都是没有加虚拟化的
对于这种jmp跳转类的混淆
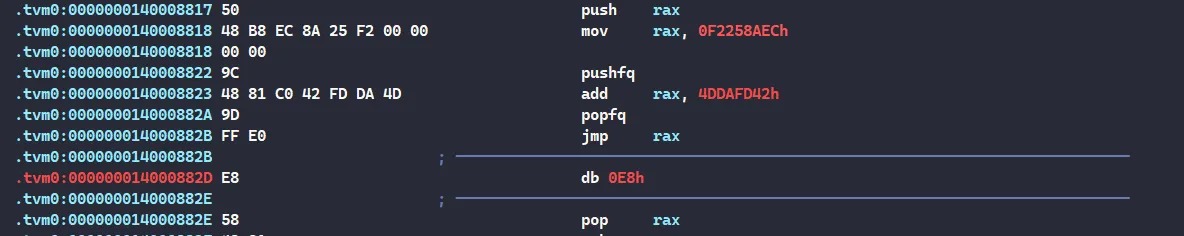
手动计算一下目标跳转地址patch一下即可,不过这种近跳一眼就能看出来目标地址

其他的混淆不影响程序逻辑分析,所以忽略
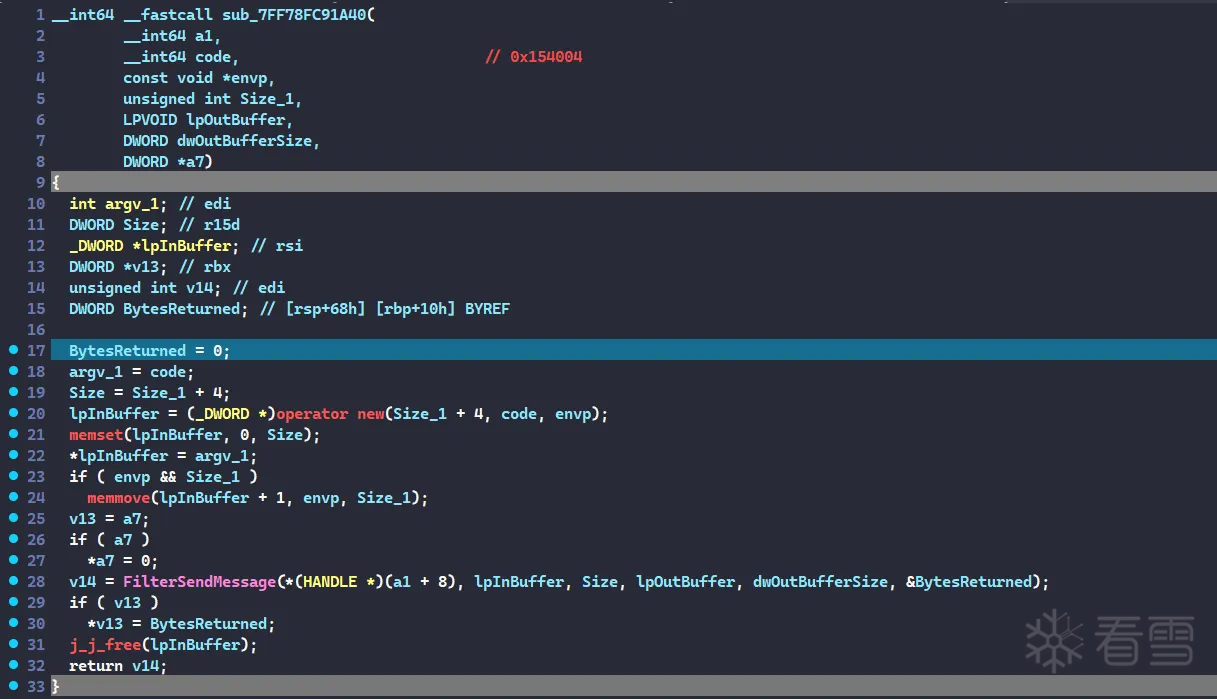
在sub_1400087F1里找到处理0x154004消息码的地方

整个的逻辑就是一个普通的tea加密, key: {'A', 'C', 'E', '6'}

密文提取的时候要注意一下,往前4个字节
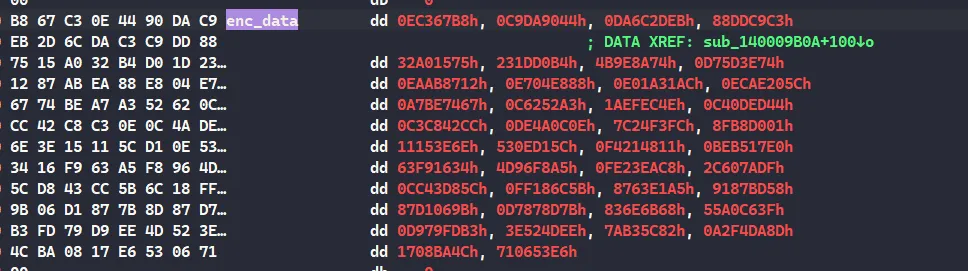
tea
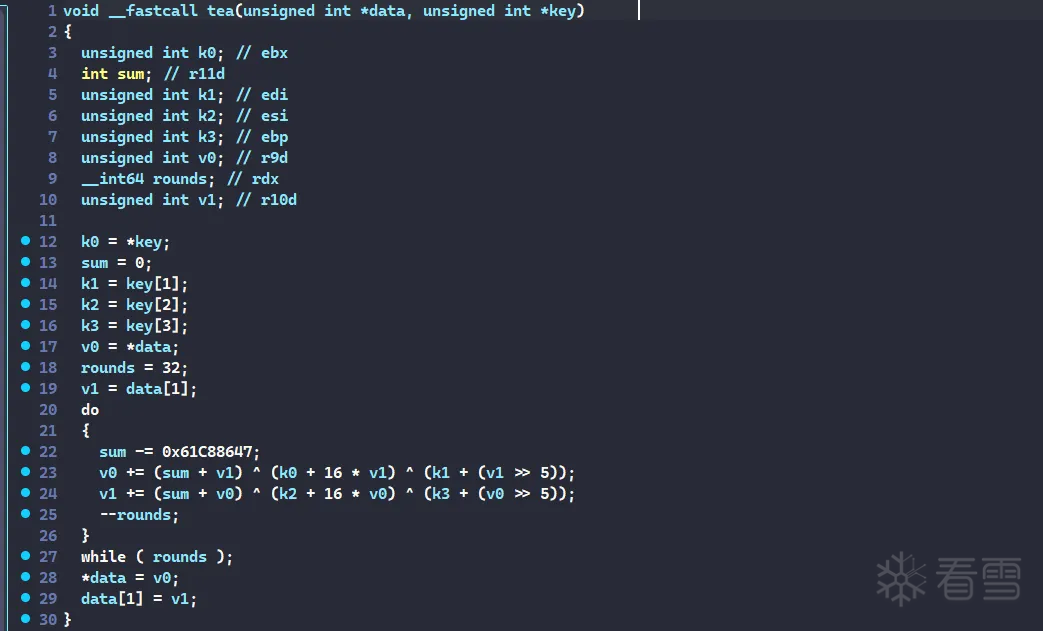
但是如果只看到了这里,那么恭喜你掉进出题人的陷阱里了
找一下交叉引用,发现他还在sub_140009E64里hook了tea

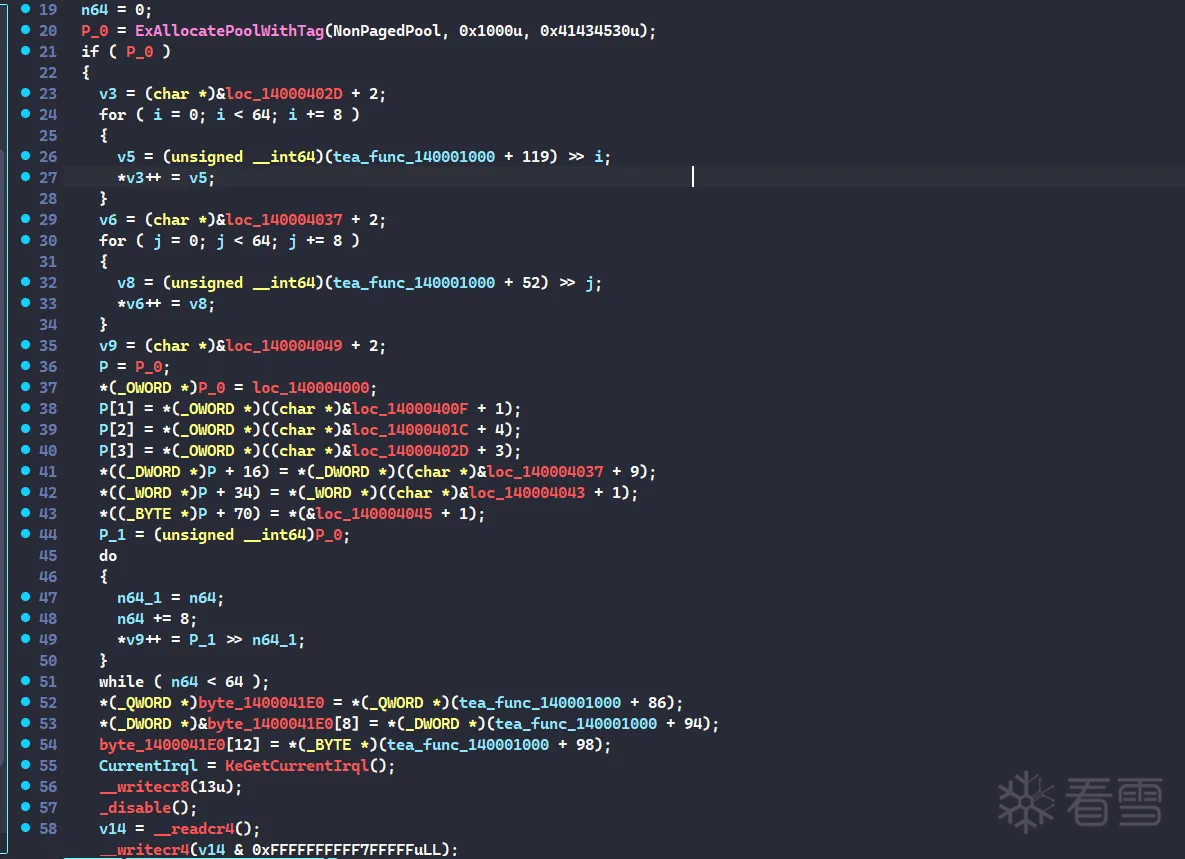
手动模拟一下hook,把代码给填过来,然后修复一下跳转
那么现在逻辑就很清晰了
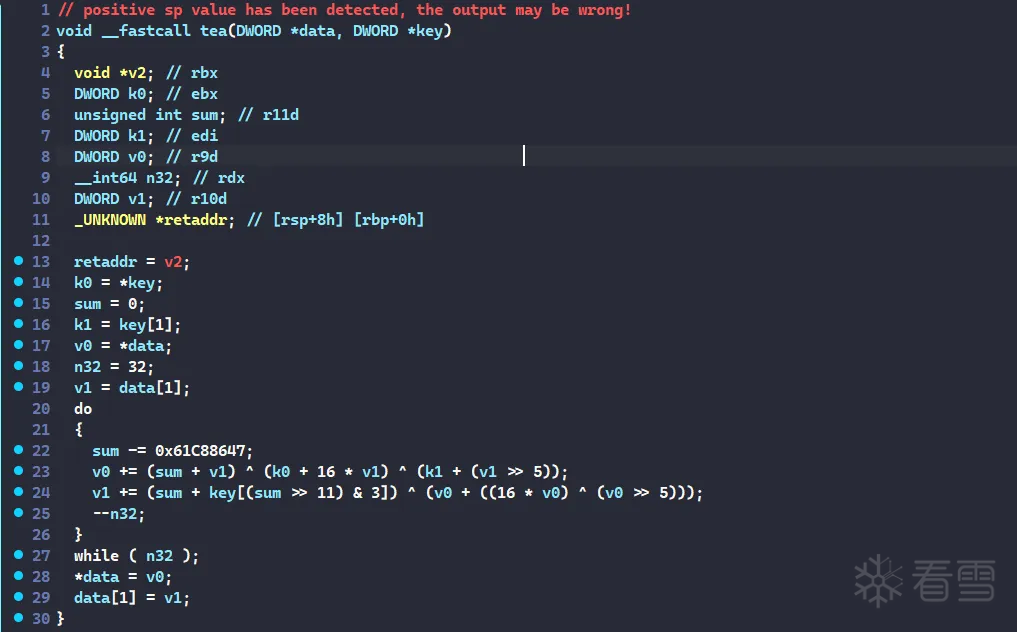
FLAG: flag{ACE_We1C0me!T0Z0Z5GamESecur1t9*CTf}
.text:0000000140001000 48 8B C4 mov rax, rsp
.text:0000000140001003 48 89 58 08 mov [rax+8], rbx
.text:0000000140001007 48 89 68 10 mov [rax+10h], rbp
.text:000000014000100B 48 89 70 18 mov [rax+18h], rsi
.text:000000014000100F 48 89 78 20 mov [rax+20h], rdi
.text:0000000140001013 41 55 push r13
.text:0000000140001015 4C 8B EA mov r13, rdx
.text:0000000140001018 8B 1A mov ebx, [rdx]
.text:000000014000101A 45 33 DB xor r11d, r11d
.text:000000014000101D 8B 7A 04 mov edi, [rdx+4]
.text:0000000140001020 4C 8B C1 mov r8, rcx
.text:0000000140001023 8B 72 08 mov esi, [rdx+8]
.text:0000000140001026 8B 6A 0C mov ebp, [rdx+0Ch]
.text:0000000140001029 44 8B 09 mov r9d, [rcx]
.text:000000014000102C 41 8D 53 20 lea edx, [r11+20h]
.text:0000000140001030 44 8B 51 04 mov r10d, [rcx+4]
.text:0000000140001034
.text:0000000140001034 loc_140001034: ; CODE XREF: tea:loc_140001087↓j
.text:0000000140001034 41 8B CA mov ecx, r10d
.text:0000000140001037 45 8D 9B B9 79 37 9E lea r11d, [r11-61C88647h]
.text:000000014000103E C1 E9 05 shr ecx, 5
.text:0000000140001041 41 8B C2 mov eax, r10d
.text:0000000140001044 03 CF add ecx, edi
.text:0000000140001046 C1 E0 04 shl eax, 4
.text:0000000140001049 03 C3 add eax, ebx
.text:000000014000104B 33 C8 xor ecx, eax
.text:000000014000104D 43 8D 04 13 lea eax, [r11+r10]
.text:0000000140001051 33 C8 xor ecx, eax
.text:0000000140001053 44 03 C9 add r9d, ecx
.text:0000000140001056
.text:0000000140001056 loc_140001056:
.text:0000000140001056 58 pop rax
.text:0000000140001057 41 8B C9 mov ecx, r9d
.text:000000014000105A 41 8B C1 mov eax, r9d
.text:000000014000105D C1 E0 04 shl eax, 4
.text:0000000140001060 C1 E9 05 shr ecx, 5
.text:0000000140001063 33 C8 xor ecx, eax
.text:0000000140001065 41 8B C3 mov eax, r11d
.text:0000000140001068 48 C1 E8 0B shr rax, 0Bh
.text:000000014000106C 41 03 C9 add ecx, r9d
.text:000000014000106F 83 E0 03 and eax, 3
.text:0000000140001072 41 8B 44 85 00 mov eax, [r13+rax*4+0]
.text:0000000140001077 41 03 C3 add eax, r11d
.text:000000014000107A 33 C8 xor ecx, eax
.text:000000014000107C 44 03 D1 add r10d, ecx
.text:000000014000107F 48 83 EA 01 sub rdx, 1
.text:0000000140001083 75 02 jnz short loc_140001087 ; Keypatch modified this from:
.text:0000000140001083 ; nop
.text:0000000140001083 ; nop
.text:0000000140001083 ; Keypatch modified this from:
.text:0000000140001083 ; jnz short loc_14000108B
.text:0000000140001085 EB 02 jmp short loc_140001089 ; Keypatch modified this from:
.text:0000000140001085 ; nop
.text:0000000140001085 ; nop
.text:0000000140001085 ; Keypatch modified this from:
.text:0000000140001085 ; jmp short loc_140001098
.text:0000000140001087 ; ---------------------------------------------------------------------------
.text:0000000140001087
.text:0000000140001087 loc_140001087: ; CODE XREF: tea+83↑j
.text:0000000140001087 EB AB jmp short loc_140001034 ; Keypatch modified this from:
.text:0000000140001087 ; nop
.text:0000000140001087 ; nop
.text:0000000140001089 ; ---------------------------------------------------------------------------
.text:0000000140001089
.text:0000000140001089 loc_140001089: ; CODE XREF: tea+85↑j
.text:0000000140001089 41 5D pop r13
.text:000000014000108B 48 8B 5C 24 08 mov rbx, [rsp-8+arg_8]
.text:0000000140001090 48 8B 6C 24 10 mov rbp, [rsp-8+arg_10]
.text:0000000140001095 48 8B 74 24 18 mov rsi, [rsp-8+arg_18]
.text:000000014000109A 48 8B 7C 24 20 mov rdi, [rsp-8+arg_20]
.text:000000014000109F
.text:000000014000109F loc_14000109F: ; DATA XREF: .rdata:00000001400030EC↓o
.text:000000014000109F ; .rdata:Registration↓o ...
.text:000000014000109F 45 89 08 mov [r8], r9d
.text:00000001400010A2 45 89 50 04 mov [r8+4], r10d
.text:00000001400010A6 C3 retn
.text:0000000140001000 48 8B C4 mov rax, rsp
.text:0000000140001003 48 89 58 08 mov [rax+8], rbx
.text:0000000140001007 48 89 68 10 mov [rax+10h], rbp
.text:000000014000100B 48 89 70 18 mov [rax+18h], rsi
.text:000000014000100F 48 89 78 20 mov [rax+20h], rdi
.text:0000000140001013 41 55 push r13
.text:0000000140001015 4C 8B EA mov r13, rdx
.text:0000000140001018 8B 1A mov ebx, [rdx]
.text:000000014000101A 45 33 DB xor r11d, r11d
.text:000000014000101D 8B 7A 04 mov edi, [rdx+4]
.text:0000000140001020 4C 8B C1 mov r8, rcx
.text:0000000140001023 8B 72 08 mov esi, [rdx+8]
.text:0000000140001026 8B 6A 0C mov ebp, [rdx+0Ch]
.text:0000000140001029 44 8B 09 mov r9d, [rcx]
.text:000000014000102C 41 8D 53 20 lea edx, [r11+20h]
.text:0000000140001030 44 8B 51 04 mov r10d, [rcx+4]
.text:0000000140001034
.text:0000000140001034 loc_140001034: ; CODE XREF: tea:loc_140001087↓j
.text:0000000140001034 41 8B CA mov ecx, r10d
.text:0000000140001037 45 8D 9B B9 79 37 9E lea r11d, [r11-61C88647h]
.text:000000014000103E C1 E9 05 shr ecx, 5
.text:0000000140001041 41 8B C2 mov eax, r10d
.text:0000000140001044 03 CF add ecx, edi
.text:0000000140001046 C1 E0 04 shl eax, 4
.text:0000000140001049 03 C3 add eax, ebx
.text:000000014000104B 33 C8 xor ecx, eax
.text:000000014000104D 43 8D 04 13 lea eax, [r11+r10]
.text:0000000140001051 33 C8 xor ecx, eax
.text:0000000140001053 44 03 C9 add r9d, ecx
.text:0000000140001056
.text:0000000140001056 loc_140001056:
.text:0000000140001056 58 pop rax
.text:0000000140001057 41 8B C9 mov ecx, r9d
.text:000000014000105A 41 8B C1 mov eax, r9d
.text:000000014000105D C1 E0 04 shl eax, 4
.text:0000000140001060 C1 E9 05 shr ecx, 5
.text:0000000140001063 33 C8 xor ecx, eax
.text:0000000140001065 41 8B C3 mov eax, r11d
.text:0000000140001068 48 C1 E8 0B shr rax, 0Bh
.text:000000014000106C 41 03 C9 add ecx, r9d
.text:000000014000106F 83 E0 03 and eax, 3
.text:0000000140001072 41 8B 44 85 00 mov eax, [r13+rax*4+0]
.text:0000000140001077 41 03 C3 add eax, r11d
.text:000000014000107A 33 C8 xor ecx, eax
.text:000000014000107C 44 03 D1 add r10d, ecx
.text:000000014000107F 48 83 EA 01 sub rdx, 1
.text:0000000140001083 75 02 jnz short loc_140001087 ; Keypatch modified this from:
.text:0000000140001083 ; nop
[培训]科锐逆向工程师培训第53期2025年7月8日开班!
最后于 2025-3-31 17:36
被TubituX编辑
,原因: