-
-
[原创]关于NSPACK 3.7的通用脱壳分析及相关
-
发表于: 2007-7-2 11:49 7943
-
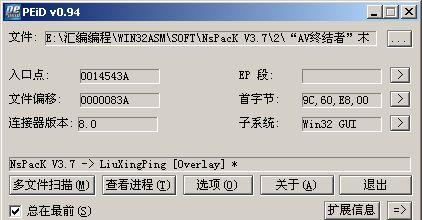
加壳方式,和检测结果,已如上图所示
按照基本习惯,隐藏OD,忽略所有异常,后载入WIN32测试程序,显示如下:
004051A1 > 9C pushfd 004051A2 60 pushad 004051A3 E8 00000000 call 004051A8 004051A8 5D pop ebp ;重定位 004051A9 83ED 07 sub ebp, 7 ;ebp=壳入口真实地址 004051AC 8D8D DBFEFFFF lea ecx, dword ptr [ebp-125] 004051B2 8039 01 cmp byte ptr [ecx], 1 004051B5 0F84 42020000 je 004053FD 004051BB C601 01 mov byte ptr [ecx], 1 004051BE 8BC5 mov eax, ebp 004051C0 2B85 6FFEFFFF sub eax, dword ptr [ebp-191] 004051C6 8985 6FFEFFFF mov dword ptr [ebp-191], eax 004051CC 0185 9FFEFFFF add dword ptr [ebp-161], eax 004051D2 8DB5 E3FEFFFF lea esi, dword ptr [ebp-11D] 004051D8 0106 add dword ptr [esi], eax 004051DA 55 push ebp 004051DB 56 push esi 004051DC 6A 40 push 40 ; Protect = PAGE_EXECUTE_READWRITE 004051DE 68 00100000 push 1000 ; AllocationType = MEM_COMMIT 004051E3 68 00100000 push 1000 ; Size = 1000 (4096.) 004051E8 6A 00 push 0 ; Address = NULL 004051EA FF95 07FFFFFF call dword ptr [ebp-F9] ; KERNEL32.VirtualAlloc 004051F0 85C0 test eax, eax 004051F2 0F84 69030000 je 00405561 004051F8 8985 97FEFFFF mov dword ptr [ebp-169], eax ;保存申请内存的地址 004051FE E8 00000000 call 00405203 00405203 5B pop ebx ;重定位 00405204 B9 67030000 mov ecx, 367 00405209 03D9 add ebx, ecx 0040520B 50 push eax ;eax=申请内存的地址 0040520C 53 push ebx ;ebx=ebx+367h 0040520D E8 B0020000 call 004054C2 ;========================================================================================== 004054C2 55 push ebp ; win32.<模块入口点> 004054C3 8BEC mov ebp, esp 004054C5 8B75 08 mov esi, dword ptr [ebp+8] ;获取第一个参数:ebx 004054C8 8B7D 0C mov edi, dword ptr [ebp+C] ;获取第二个参数:eax 004054CB FC cld 004054CC B2 80 mov dl, 80 ;使下面DL第一次清零 004054CE A4 movs byte ptr es:[edi], byte ptr [esi] 004054CF E8 6D000000 call 00405541 ;---------------------------- 00405541 02D2 add dl, dl ;累加dl=dl×2 00405543 75 05 jnz short 0040554A ;不等于零就转 00405545 8A16 mov dl, byte ptr [esi] 00405547 46 inc esi ;跳过一个字节 00405548 12D2 adc dl, dl ;ADC带进位加发 0040554A C3 retn ;---------------------------- 004054D4 ^ 73 F8 jnb short 004054CE ;没有进位就转回 004054D6 33C9 xor ecx, ecx ;将ECX清零,再执行以上操作 004054D8 E8 64000000 call 00405541 004054DD 73 19 jnb short 004054F8 004054DF 33C0 xor eax, eax ;将EAX清零,再执行以上操作 004054E1 E8 5B000000 call 00405541 004054E6 73 21 jnb short 00405509 ;以上简短的分析一下,后略。 004054E8 B0 10 mov al, 10 004054EA E8 52000000 call 00405541 004054EF 12C0 adc al, al 004054F1 ^ 73 F7 jnb short 004054EA 004054F3 75 41 jnz short 00405536 004054F5 AA stos byte ptr es:[edi] 004054F6 ^ EB D7 jmp short 004054CF 004054F8 E8 50000000 call 0040554D 004054FD 49 dec ecx 004054FE E2 15 loopd short 00405515 00405500 8BC5 mov eax, ebp 00405502 E8 44000000 call 0040554B 00405507 EB 2E jmp short 00405537 00405509 AC lods byte ptr [esi] 0040550A D1E8 shr eax, 1 0040550C 74 4F je short 0040555D 0040550E 83D1 02 adc ecx, 2 00405511 8BE8 mov ebp, eax 00405513 EB 22 jmp short 00405537 00405515 91 xchg eax, ecx 00405516 48 dec eax 00405517 C1E0 08 shl eax, 8 0040551A AC lods byte ptr [esi] 0040551B 8BE8 mov ebp, eax 0040551D E8 29000000 call 0040554B ........ ;========================================================================================== 00405212 5E pop esi 00405213 5D pop ebp 00405214 8B36 mov esi, dword ptr [esi] 00405216 8BFD mov edi, ebp 00405218 03BD 5FFEFFF>add edi, dword ptr [ebp-1A1] 0040521E 8BDF mov ebx, edi 00405220 833F 00 cmp dword ptr [edi], 0 00405223 75 0A jnz short 0040522F 00405225 83C7 04 add edi, 4 00405228 B9 00000000 mov ecx, 0 0040522D EB 16 jmp short 00405245 0040522F B9 01000000 mov ecx, 1 00405234 033B add edi, dword ptr [ebx] 00405236 83C3 04 add ebx, 4 00405239 833B 00 cmp dword ptr [ebx], 0 0040523C 74 34 je short 00405272 0040523E 0113 add dword ptr [ebx], edx 00405240 8B33 mov esi, dword ptr [ebx] 00405242 037B 04 add edi, dword ptr [ebx+4] 00405245 57 push edi 00405246 51 push ecx 00405247 53 push ebx 00405248 FFB5 0BFFFFF>push dword ptr [ebp-F5] 0040524E FFB5 07FFFFF>push dword ptr [ebp-F9] 00405254 8BD6 mov edx, esi 00405256 8BCF mov ecx, edi 00405258 8B85 97FEFFF>mov eax, dword ptr [ebp-169] 0040525E 05 AA050000 add eax, 5AA 00405263 FFD0 call eax 00405265 5B pop ebx 00405266 59 pop ecx 00405267 5F pop edi 00405268 83F9 00 cmp ecx, 0 0040526B 74 05 je short 00405272 0040526D 83C3 08 add ebx, 8 00405270 ^ EB C7 jmp short 00405239 00405272 68 00800000 push 8000 00405277 6A 00 push 0 00405279 FFB5 97FEFFF>push dword ptr [ebp-169] 0040527F FF95 0BFFFFF>call dword ptr [ebp-F5] ; KERNEL32.VirtualFree 00405285 8DB5 9FFEFFF>lea esi, dword ptr [ebp-161] 0040528B 8B4E 08 mov ecx, dword ptr [esi+8] 0040528E 8D56 10 lea edx, dword ptr [esi+10] 00405291 8B36 mov esi, dword ptr [esi] 00405293 8BFE mov edi, esi 00405295 83F9 00 cmp ecx, 0 00405298 74 3F je short 004052D9 0040529A 8A07 mov al, byte ptr [edi] 0040529C 47 inc edi 0040529D 2C E8 sub al, 0E8 0040529F 3C 01 cmp al, 1 004052A1 ^ 77 F7 ja short 0040529A 004052A3 8B07 mov eax, dword ptr [edi] 004052A5 807A 01 00 cmp byte ptr [edx+1], 0 004052A9 74 14 je short 004052BF 004052AB 8A1A mov bl, byte ptr [edx] 004052AD 381F cmp byte ptr [edi], bl 004052AF ^ 75 E9 jnz short 0040529A 004052B1 8A5F 04 mov bl, byte ptr [edi+4] 004052B4 66:C1E8 08 shr ax, 8 004052B8 C1C0 10 rol eax, 10 004052BB 86C4 xchg ah, al 004052BD EB 0A jmp short 004052C9 004052BF 8A5F 04 mov bl, byte ptr [edi+4] 004052C2 86C4 xchg ah, al 004052C4 C1C0 10 rol eax, 10 004052C7 86C4 xchg ah, al 004052C9 2BC7 sub eax, edi 004052CB 03C6 add eax, esi 004052CD 8907 mov dword ptr [edi], eax 004052CF 83C7 05 add edi, 5 004052D2 80EB E8 sub bl, 0E8 004052D5 8BC3 mov eax, ebx 004052D7 ^ E2 C6 loopd short 0040529F 004052D9 E8 3A010000 call 00405418 004052DE 8D8D B3FEFFF>lea ecx, dword ptr [ebp-14D] 004052E4 8B41 08 mov eax, dword ptr [ecx+8] 004052E7 83F8 00 cmp eax, 0 004052EA 0F84 8100000>je 00405371 004052F0 8BF2 mov esi, edx 004052F2 2B71 10 sub esi, dword ptr [ecx+10] 004052F5 74 7A je short 00405371 004052F7 8971 10 mov dword ptr [ecx+10], esi 004052FA 8DB5 E3FEFFF>lea esi, dword ptr [ebp-11D] 00405300 8B36 mov esi, dword ptr [esi] 00405302 8D5E FC lea ebx, dword ptr [esi-4] 00405305 8B01 mov eax, dword ptr [ecx] 00405307 83F8 01 cmp eax, 1 0040530A 74 0A je short 00405316 0040530C 8BFA mov edi, edx 0040530E 0379 08 add edi, dword ptr [ecx+8] 00405311 8B49 10 mov ecx, dword ptr [ecx+10] 00405314 EB 08 jmp short 0040531E 00405316 8BFE mov edi, esi 00405318 0379 08 add edi, dword ptr [ecx+8] 0040531B 8B49 10 mov ecx, dword ptr [ecx+10] 0040531E 33C0 xor eax, eax 00405320 8A07 mov al, byte ptr [edi] 00405322 47 inc edi 00405323 0BC0 or eax, eax 00405325 74 20 je short 00405347 00405327 3C EF cmp al, 0EF 00405329 77 06 ja short 00405331 0040532B 03D8 add ebx, eax 0040532D 010B add dword ptr [ebx], ecx 0040532F ^ EB ED jmp short 0040531E 00405331 24 0F and al, 0F 00405333 C1E0 10 shl eax, 10 00405336 66:8B07 mov ax, word ptr [edi] 00405339 83C7 02 add edi, 2 0040533C 0BC0 or eax, eax 0040533E ^ 75 EB jnz short 0040532B 00405340 8B07 mov eax, dword ptr [edi] 00405342 83C7 04 add edi, 4 00405345 ^ EB E4 jmp short 0040532B 00405347 33DB xor ebx, ebx 00405349 87FE xchg esi, edi 0040534B 8B06 mov eax, dword ptr [esi] 0040534D 83F8 00 cmp eax, 0 00405350 74 1F je short 00405371 00405352 AD lods dword ptr [esi] 00405353 0BC0 or eax, eax 00405355 74 08 je short 0040535F 00405357 03D8 add ebx, eax 00405359 66:010C1F add word ptr [edi+ebx], cx 0040535D ^ EB F3 jmp short 00405352 0040535F 33DB xor ebx, ebx 00405361 C1E9 10 shr ecx, 10 00405364 AD lods dword ptr [esi] 00405365 0BC0 or eax, eax 00405367 74 08 je short 00405371 00405369 03D8 add ebx, eax 0040536B 66:010C1F add word ptr [edi+ebx], cx 0040536F ^ EB F3 jmp short 00405364 00405371 8DB5 6FFEFFF>lea esi, dword ptr [ebp-191] 00405377 8B16 mov edx, dword ptr [esi] 00405379 8DB5 CBFEFFF>lea esi, dword ptr [ebp-135] 0040537F 8A06 mov al, byte ptr [esi] 00405381 3C 01 cmp al, 1 00405383 75 3F jnz short 004053C4 00405385 0356 04 add edx, dword ptr [esi+4] 00405388 56 push esi 00405389 52 push edx 0040538A 56 push esi 0040538B 6A 04 push 4 0040538D 68 00010000 push 100 00405392 52 push edx 00405393 FF95 03FFFFF>call dword ptr [ebp-FD] 00405399 5F pop edi 0040539A 5E pop esi 0040539B 83F8 01 cmp eax, 1 0040539E 0F85 BD01000>jnz 00405561 004053A4 83C6 08 add esi, 8 004053A7 B9 08000000 mov ecx, 8 004053AC F3:A4 rep movs byte ptr es:[edi], byte ptr [esi] 004053AE 83EE 0C sub esi, 0C 004053B1 83EF 08 sub edi, 8 004053B4 56 push esi 004053B5 FF76 FC push dword ptr [esi-4] 004053B8 68 00010000 push 100 004053BD 57 push edi 004053BE FF95 03FFFFF>call dword ptr [ebp-FD] 004053C4 55 push ebp 004053C5 5B pop ebx 004053C6 81EB 2100000>sub ebx, 21 004053CC 33C9 xor ecx, ecx 004053CE 8A0B mov cl, byte ptr [ebx] 004053D0 80F9 00 cmp cl, 0 004053D3 74 28 je short 004053FD 004053D5 43 inc ebx 004053D6 8DB5 6FFEFFF>lea esi, dword ptr [ebp-191] 004053DC 8B16 mov edx, dword ptr [esi] 004053DE 56 push esi ;经Nspack3.7加壳后基本类似代码 004053DF 51 push ecx 004053E0 53 push ebx 004053E1 52 push edx 004053E2 56 push esi 004053E3 FF33 push dword ptr [ebx] 004053E5 FF73 04 push dword ptr [ebx+4] 004053E8 8B43 08 mov eax, dword ptr [ebx+8] 004053EB 03C2 add eax, edx 004053ED 50 push eax 004053EE FF95 03FFFFF>call dword ptr [ebp-FD] 004053F4 5A pop edx 004053F5 5B pop ebx 004053F6 59 pop ecx 004053F7 5E pop esi 004053F8 83C3 0C add ebx, 0C 004053FB ^ E2 E1 loopd short 004053DE 004053FD B8 00000000 mov eax, 0 00405402 83F8 00 cmp eax, 0 00405405 74 0A je short 00405411 00405407 61 popad 00405408 9D popfd 00405409 B8 01000000 mov eax, 1 0040540E C2 0C00 retn 0C 00405411 61 popad 00405412 9D popfd 00405413 - E9 E8BBFFFF jmp 00401000 ;跳转EPO
在程序入口处,向下翻找形如以下的代码
004053FD B8 00000000 mov eax, 0 ;可以在此处F2,然后F8跟到JMP 00405402 83F8 00 cmp eax, 0 00405405 74 0A je short 00405411 00405407 61 popad 00405408 9D popfd 00405409 B8 01000000 mov eax, 1 0040540E C2 0C00 retn 0C 00405411 61 popad 00405412 9D popfd 00405413 - E9 E8BBFFFF jmp 00401000 ;跳转EPO,亦可直接在此F2
在最后一个长距离JMP,F2后,再F9,完整的PE数据就都释放完毕,再GO就要执行真正的EPO入口代码
暂时别忙着关OD,停在那,别理它. 剩下的就是常规步骤了,先用LordPE->DUMPFULL,再用ImportREC修复IAT后,直
接转储,就OK了.
从以上情况看来,对于使用NsPacK V3.7加过压缩壳的,脱起来应该是机械化的,毫无难度可言.可我在分析KV
终结者时,经检测也是加有此壳.用OD载的确有相同的特征,在JMP处F2,却无法用ImportREC修复转储.还望个位高
手,解惑.
附件中,有详细文档及甲壳样本,其中tubjsoe(KV终结者病毒),解压码为1;想试试的请先关闭杀毒软件,
万一脱壳过程中,不小心中毒了,可以用2中的专杀工具搞定它.请一定要将脱壳后的tubjsoe文件,给我一份
,E-mail:sdf2003@126.com,同时也更期望能提下是如何脱掉壳的.
赞赏
|
|
|---|---|
|
|
厉害啊!!!!!!!!!!!!!!!!!!
|
|
|
壳加了多少层 不知道 Delphi的程序。 直接用ODDump的 至于可以用不 就看人品加运气了。
Unpacked.rar OEP在这儿 你也可以自己想办法Dump 0040BDF8 /. 55 push ebp 0040BDF9 |. 8BEC mov ebp,esp 0040BDFB |. B9 17000000 mov ecx,17 0040BE00 |> 6A 00 /push 0 0040BE02 |. 6A 00 |push 0 0040BE04 |. 49 |dec ecx 0040BE05 |.^ 75 F9 \jnz short tubjsoe.0040BE00 0040BE07 |. 51 push ecx 0040BE08 |. 53 push ebx 0040BE09 |. 56 push esi 0040BE0A |. 57 push edi 0040BE0B |. B8 90BD4000 mov eax,tubjsoe.0040BD90 0040BE10 |. E8 1785FFFF call tubjsoe.0040432C 0040BE15 |. 8B3D C4D44000 mov edi,dword ptr ds:[40D4C4] ; tubjsoe.0040F0A4 0040BE1B |. 33C0 xor eax,eax 0040BE1D |. 55 push ebp 0040BE1E |. 68 90C64000 push tubjsoe.0040C690 0040BE23 |. 64:FF30 push dword ptr fs:[eax] 0040BE26 |. 64:8920 mov dword ptr fs:[eax],esp 0040BE29 |. 8BC7 mov eax,edi 0040BE2B |. BA 04010000 mov edx,104 0040BE30 |. E8 FB7FFFFF call tubjsoe.00403E30 0040BE35 |. 68 04010000 push 104 0040BE3A |. 8B07 mov eax,dword ptr ds:[edi] 0040BE3C |. E8 C77EFFFF call tubjsoe.00403D08 0040BE41 |. 50 push eax ; |PathBuffer 0040BE42 |. A1 00E74000 mov eax,dword ptr ds:[40E700] ; | 0040BE47 |. 50 push eax ; |hModule => NULL 0040BE48 |. E8 9386FFFF call tubjsoe.004044E0 ; \GetModuleFileNameA 0040BE4D |. 8BD0 mov edx,eax 0040BE4F |. 8BC7 mov eax,edi 0040BE51 |. E8 DA7FFFFF call tubjsoe.00403E30 0040BE56 |. E8 29BBFFFF call tubjsoe.00407984 0040BE5B |. BE 17000000 mov esi,17 0040BE60 |. 8B1D 1CD44000 mov ebx,dword ptr ds:[40D41C] ; tubjsoe.0040D0C4 0040BE66 |> A1 F0D44000 /mov eax,dword ptr ds:[40D4F0] 0040BE6B |. 8B13 |mov edx,dword ptr ds:[ebx] 0040BE6D |. E8 6E7BFFFF |call tubjsoe.004039E0 0040BE72 |. 8D55 EC |lea edx,[local.5] 0040BE75 |. 8B07 |mov eax,dword ptr ds:[edi] 0040BE77 |. E8 DC9DFFFF |call tubjsoe.00405C58 0040BE7C |. 8B45 EC |mov eax,[local.5] 0040BE7F |. 50 |push eax 0040BE80 |. A1 F0D44000 |mov eax,dword ptr ds:[40D4F0] 0040BE85 |. FF30 |push dword ptr ds:[eax] 0040BE87 |. A1 E8D44000 |mov eax,dword ptr ds:[40D4E8] 0040BE8C |. FF30 |push dword ptr ds:[eax] 0040BE8E |. A1 F8D34000 |mov eax,dword ptr ds:[40D3F8] 0040BE93 |. FF30 |push dword ptr ds:[eax] 0040BE95 |. 8D45 E4 |lea eax,[local.7] 0040BE98 |. BA 03000000 |mov edx,3 0040BE9D |. E8 2E7DFFFF |call tubjsoe.00403BD0 0040BEA2 |. 8B45 E4 |mov eax,[local.7] 0040BEA5 |. 8D55 E8 |lea edx,[local.6] 0040BEA8 |. E8 AB9DFFFF |call tubjsoe.00405C58 0040BEAD |. 8B55 E8 |mov edx,[local.6] 0040BEB0 |. 58 |pop eax 0040BEB1 |. E8 9E7DFFFF |call tubjsoe.00403C54 0040BEB6 |. 0F85 5B010000 |jnz tubjsoe.0040C017 0040BEBC |. 6A 01 |push 1 0040BEBE |. 8B0D F0D44000 |mov ecx,dword ptr ds:[40D4F0] ; tubjsoe.0040F1B0 补充一句,,现在的病毒真是面向大众了。 真是用C语言写病毒我都还稍微想的通点。。。。。。Delphi。。。晕倒哈 |
|
|
|
他的文章
谁下载
fly
kanxue
forgot
jxx_gt
binliao
周二两
骨灰C
xiluoyou
yyjpcx
qfejj
lfsx
mudropmu
wangcl
情狼
LOCKLOSE
piaoxue184
inr
xyzjhe
深海游侠
zzsx
you8107
天天快乐
wer412
yushiro
9494
波导终结者
Xacs
swlepus
phoenixkiller
whyIII
dhtfish
liuyuer
pmma
yzzfzd
不古龙
option
zjzxj
71190838
qc2t
black1hero
ShSc
xbeggar
unlocker
nba2005
lhglhg
kingjia
晓兵
stan52
azrael1987
一夕渔樵话
mmqiang
tomenzi
fdltc
ttds
军营绿花
virtual
hrbx
hbqjxhw
fob
locket
foria
yjd
HSQ
完美
laserfox
yxg
zhonghuam
foxabu
tqfs
wancb
duwenqing
jting陈
skylly
9521
盘中鸟
ffzy
ddrmsdos
summax
sunsjw
newice
whypro
瘦雨雨
jiaxing徐
RuShi
Lancia
三根火柴
erguo
wan
yzm
yzjsdn
M酷酷
chenbao
fhsyj
luckyfish
openworld
mrghost
vgacard
无心释途
poll
谁下载
fly
kanxue
forgot
jxx_gt
binliao
周二两
骨灰C
xiluoyou
yyjpcx
qfejj
lfsx
mudropmu
wangcl
情狼
LOCKLOSE
piaoxue184
inr
xyzjhe
深海游侠
zzsx
you8107
天天快乐
wer412
yushiro
9494
波导终结者
Xacs
swlepus
TeLeMan
phoenixkiller
whyIII
dhtfish
liuyuer
pmma
yzzfzd
不古龙
option
zjzxj
71190838
qc2t
black1hero
ShSc
xbeggar
unlocker
nba2005
lhglhg
kingjia
晓兵
stan52
azrael1987
一夕渔樵话
mmqiang
tomenzi
fdltc
ttds
军营绿花
virtual
hrbx
hbqjxhw
fob
locket
foria
yjd
HSQ
完美
laserfox
yxg
zhonghuam
foxabu
tqfs
wancb
duwenqing
jting陈
skylly
9521
盘中鸟
ffzy
ddrmsdos
summax
sunsjw
newice
whypro
瘦雨雨
jiaxing徐
RuShi
Lancia
三根火柴
erguo
wan
yzm
yzjsdn
M酷酷
chenbao
fhsyj
luckyfish
openworld
mrghost
vgacard
无心释途
赞赏
雪币:
留言:


